How Safe Are Your "Electronic Medical Records" From Hackers?
Your Electronic Healthcare Records

What is HIPAA?
HIPAA is an abbreviation for the "Health Insurance Portability and Accountability Act of 1996."
What does it do for you?
HIPAA protects any AND all your personal identifying health information which is either held in a file or transmitted in any form of media, whether electronically, paper, or orally.
What does "personal identifying health information" cover?
This is information that contains your past, present or future mental or physical health condition, the type of health care you receive, the payments you make for it or receive regarding your health care provider, your demographics which is your name, age, social security number, address, phone number, birth date and any other information which can directly lead back to you personally.
Who has to abide by HIPAA rules?
Anyone who requests your personal identifying information is required to safeguard it and provide you with written HIPAA rules (usually requiring your signature) which they are required to provide at every instance or transaction. These entities may include but not limited to:
- Your physicians and specialists, includes any healthcare provider under their supervision such as Nurse Practitioners and Physician Assistants, his/her office and medical personnel,
- Hospitals and nursing homes and their employees, also includes maintenance and housekeeping employees
- Your healthcare insurance plan and their employees (no exceptions)
- Healthcare clearinghouses (companies who are transcribers or interpreters of healthcare data, charts and reports including laboratory and imaging tests which is transcribed from either dictation, from handwritten notes or from laboratory printout) and their employees (no exceptions)
- Pharmacies and their employees (no exceptions)
- Medical supply houses and their employees (companies who provide you with durable goods and medical supplies such as diabetic supplies)
- Many but not all medical research facilities who conduct research using humans and their data
Linked story of another hack

Your Medical Privacy At Risk
As previously stated in my hub Spotlight On: Doctors Office Visits - Do You Get Your Money's Worth? , all health care providers are required to transfer patient medical records from paper to electronic health records (EHRs). This is because in July 2010, the CMS (Centers for Medicare and Medicaid Services) created the Medicare and Medicaid Electronic Health Record Incentive Program, which was written as part of the HITECH Act of 2009 (Health Information Technology for Economic and Clinical Health).
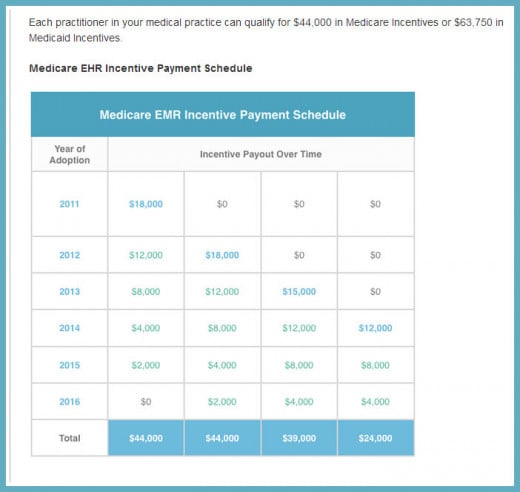
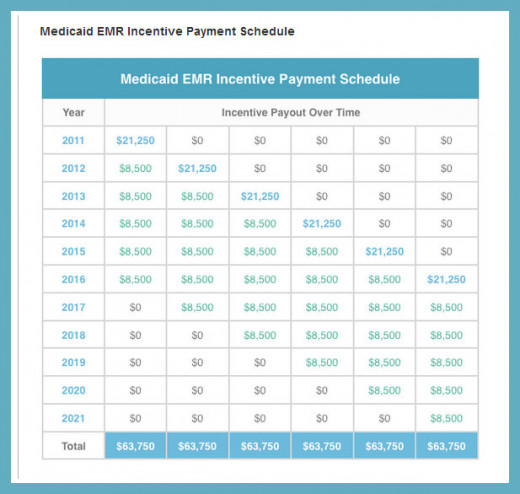
There are even some very attractive monetary incentives to get physicians to do it. These incentives pay them up to the end in the year 2021, at the latest. (see graphics below)
The financial program payouts will be received only if
- the healthcare provider can show "meaningful use," which in essence means that as long as each healthcare provider shows he has mastered each step of the EHR program in how to use the program, and
- who falls under the 30% rule for Medicare and the 20% rule for Medicaid, will receive the bonuses when they come into compliance on each step of the program, as outlined in my other hub.
As much as everyone was concerned about HIPAA in the 1980s, which became a law in 1996, and required more revisions in 2005, very little thought and emphasis went into implementing HIPAA protection into this program.
As new events come to light, it seems that protecting your medical privacy was not as important and getting this program under way ASAP. I guess they wanted to make sure the money incentives didn't run out before they put too many rules into the program.
A Hacker's Dream
Requiring medical practices to be on all EHR (electronic health records) systems puts us all at risk of cyber criminals. Since we've had to protect our credit card and bank information so fiercely, how will we ever protect our medical information when we have to trust it in the hands of otherwise incompetent, inexperienced, non-computer savvy people, like our doctors? Most know medicine, not computers.
Some practices have done away with paper charts altogether which in my opinion is silly. Even the most inexperienced computer person knows to keep paper copies of important documents after entering them into a computer.
Unfortunately, having "live online" patient information has provided a wonderful environment for cyber-criminals to exploit patients, mostly because this new EHR program did not safeguard your personal information as you yourself would do on your own personal computer with virus protectors, firewalls, malware scanners and other programs to deter invaders.
The firewalls and other technology safety measures were not in place to protect the records at the same time the mandate was issued to health care providers to get on the ball with the transfer of paper records to enter into their own computers.
Many computer savvy professionals predicted long in advance that criminals will see electronic patient records as a great opportunity for hacking and theft, even to the point of selling records for profit.
Well, it came to pass.
Referring to a SANS Healthcare CyberThreat Report dated February 20, 2014, the FBI's Cyber Division issued a memo confirming that three vulnerable information technology companies were hacked by cyber criminals, who sold each patient record to parties who normally would have no business knowing a patient's personal medical history.
The report did NOT mention accessing Obama's healthcare.gov website and I find that really interesting since, to me, that is the site which would be the hacker's dream, given the supposed high numbers of people who flooded the website so it crashed several times due to overuse.
Regarding the links in the above paragraph: Because in my past experience, the FBI has routinely re-classified documents after de-classifying or issuing them as un-classified, I took a screenshot of the above referenced FBI memo to have for posterity. Screenshot follows this paragraph.
FBI report 4 8 2014, two pages - links are disabled to clicking


FYI only from other hub: Incentives paid to healthcare providers to convert over to electronic recordkeeping

Qualifying For Incentives for Electronic Health Recording
If you read this in the other hub, skip to next section.
The qualification schedule was written into law as such:
80 percent of physician practices or medical institutions (see chart below for qualifying entities) providing services or treatment in practices
- whose income comes from at least 30% of their patients on MEDICARE or
- whose income comes from at least 20% of their patients on MEDICAID
must convert over to all electronic charting by the end of 2013 and the remainder 20 percent to come into compliance by the end of 2014. While doing this, they must still maintain paper charting for up to ten years or until 2021.
There are exceptions. Of Course! After all, this is government we are talking about here.
Updated info:
- A healthcare provider, practice or health center can include "other needy individuals" even if they don't have Medicaid or Medicare to be able to qualify for the incentives you see in the chart below.
- This includes patients who get free care from a healthcare provider, or reduced costs based on a sliding scale determined by the person's ability to pay per income brackets or medical assistance from Medicaid or other government program, including Children's Health Insurance Program.
EHR has "gaping holes in security"

So ... what was the extent of the hack?
According to a Forbes report dated February 20, 2014, NORSE (a threat intelligence vendor who identifies threats for governments and private industry) issued their report which was analyzed by Barbara Filkins who works for SANS as an analyst and healthcare specialist. It states:
"The data analyzed was alarming. It not only confirmed how vulnerable the industry had become, it also revealed how far behind industry-related cybersecurity strategies and controls have fallen.
During the sample one year period [09/2012 to 10/2013], the Norse threat intelligence infrastructure – a global network of sensors and honeypots that process and analyze over 100 terabytes of data daily – gathered data. The intelligence data collected for this sample included:
49,917 Unique Malicious Events
723 Unique Malicious Source IP addresses
375 U.S.-based health-care related organizations were compromised
A SANS examination of cyberthreat intelligence provided by Norse supports these statistics and conclusions, revealing exploited medical devices, conferencing systems, web servers, printers and edge security technologies all sending out malicious traffic from medical organizations. Some of these devices and applications were openly exploitable (such as default admin passwords) for many months before the breached organization recognized or repaired the breach. -- Barbara Filkins – SANS Analyst and Healthcare Specialist"
I don't know about you, but that should have been a fireworks in the sky, all out red alert, super blast to all the news stations in order to get the word out to warn people that their medical records have been infiltrated and are no longer safe.
The public should have been told to be on the alert for unusual changes in their everyday use of credit cards, PIN numbers, online banking and other online accounts that act suspiciously as if maybe they were being used by someone else, or someone else was speaking for or as them, or possibly impersonating them in different venues.
I don't like the words "malicious" or "compromised." Those two words alone in any report regarding people's personal data should have been made public in a big way, not buried in with the Evening News the way so many other things get buried these days.
The only report I saw was at the following link on April 19, 2014, which was 10 days after the hub I wrote warning of the Heartbleed bug.
Obamacare Enrollees Urged to Change Passwords Over Heartbleed Bug A little bit offered, a little bit too late.

So......how much do hackers get paid for YOUR information?
According to the FBI's information regarding records hacked from one hospital website and a stolen physician laptop, the hackers' going rate right now is $50 per chart. However, the bigger the chart, the higher the payout rate. The more well known the patient, the higher the payout rate too. Who says it doesn't pay to be famous? Unfortunately, the wrong people are getting paid in this instance.
Dr. Steven Waldren, an information technology expert and a physician strategist with the American Academy of Family Physicians said that organizations that are the most attractive to hackers are small community hospitals and small physician offices. He cites that they really don't hve the money to make investments in securing patient data like larger hospitals do.
Referring to the charts below (which were also featured in my last hub on this subject) I wholeheartedly take issue with that statement since the high incentives paid to practices with 30% Medicare patients from 2001 to 2016 and for 20% Medicaid patients until 2021 more than amply provides funds that can be used toward protecting their medical records against invasion by viruses and cyber criminals.
I think what is lacking here is pure and simple. Health provider education. It is another case of government dictating what we have to do to keep up with the times, paying large amounts of tax dollars to implement it and basically throwing people into the system without educating them on the how and wherefores to do the actual work.
It is akin to government assuming that healthcare providers already have basic computer knowledge, assuming they already know how to protect their personal computer from invasion - so why waste time on the education process and just whisk them all into the mandated "everyone has to be on electronic recordkeeping by the end of 2014?"
It is ridiculous and it is totally irresponsible of the government mandating them to comply and of healthcare providers not even taking simple precautions to safeguard your personal information.
When HIPAA came into effect, people actually lost their jobs for violating patient confidentiality if even one little piece of your personal information escaped their lips, for example, your diagnosis or your medication list.
Computer safety programs were installed in hospitals who were already using electronically generated reports (Faxed or emailed) which were heavily laden with the HIPAA statement either at the beginning, end or a full page of HIPAA mumbo jumbo that patients are still required to sign today when they go to the doctor's office, a testing facility or enter as inpatient to a hospital. Do they read it? No, because it has become acceptable practice to assume our personal information is safeguarded by HIPAA and we have the opportunity to seek retribution if they violate the HIPAA laws.
So what will happen when a hospital gets hacked or another physician's laptop is stolen?
The same thing that has happened ever since lawyers became popular ... lawsuits.
On April 25, 2014, there was a financial settlement of $1,975,200 in the case of stolen laptop computers which resulted in a breach of HIPAA guidelines. At fault were Concentra Health Services in Springfield, Missouri and from QCA Health Plan in Arkansas.
So....what do the hackers do with your information?
On Wednesday, April 23, 2014, the FBI warned healthcare providers (the report does not say exactly WHO or HOW they warned them) that their cyber-security systems are vulnerable to attacks by hackers who are searching for personal medical records and insurance data.
They went on to cite that health data is more valuable to hackers on the black market - even more than credit card numbers - because the details can be used to access anyone's bank account and even get prescriptions for controlled substances ....drugs. They do this by impersonating people with diseases in order to get prescriptions.
Other hackers are solely interested in medical information for financial gain - to submit claims to insurance companies on behalf of a patient for payment of treatment and ongoing care. Insurance companies find this feasible because the billed claims are not questioned because the patient diagnosis and information matches the treatment.
And there are still other hackers who are interested in a patient's information to make it easier to get away with Identity Theft so they can open new accounts, which may or may not hold ill gotten gains from financial payments from insurance claims as mentioned in the previous paragraph.
Health information is organized into packages called "fullz" or "kitz" on underground rings where they can get as much as $1000 if the "package" contains a complete set of documents regarding a victim's personal information, all of which are counterfeited over and over again.
FBI spokeswoman Jenny Shearer said that a breach of healthcare information takes a long time for victims to figure out that someone accessed it and even longer to figure out HOW it was accessed because the information is used in so many different ways.
A group surgeons practice had their internal client network hacked, medical records were held for ransom

What your healthcare provider can do to protect you
As much as these articles featured in the links let you think that you are at the mercy of your physician (in more ways than one), there are some things they can do to protect you.
The hard part is getting them to do it.
Copy and paste this next section to a Word Document, and DO NOT be afraid to hand it to EACH of your doctors and their Office Managers. These are measures that your healthcare provider can do - even if he is a private practitioner with no other healthcare providers in his offices. Each statement addresses your provider directly.
1. Keep software up to date with "patches" that are offered by the vendors of the software EVERYONE IN YOUR OFFICE uses. It will plug up the holes that hackers use to access your computer, laptops, smartphones, faxes and other electronic systems (internet and interoffice email, databases, online accounts).
2. Only install the applications you need to use to store and update patient data, and for transcription and billing practices on your office computers (including any laptops and Smartphones that travel out of the office or between offices). There is no need for recreational programs which most likely have to be downloaded from an external website.
3. DO NOT allow employees to use any type of "instant message" program or inter-office email system on YOUR equipment which has to travel over internet lines.
4. DO NOT allow employees to visit websites or access personal email using any of YOUR office computers, smartphones or laptops. Emails disguised as professional can turn out to be Paypal scams, Nigerian scams, Password update scams, and other sites engineered to coerce the user to enter personal information to access what looks like professional or company website.
5. DO NOT allow any employee to copy patient data to a "take home laptop" or any laptop which "travels between your office locations."
6. Invest in a program that encrypts data on your computers, laptops, smartphones and other mobile devices.
7.Talk to your billing software vendors and your EHR (Electronic Health Records) vendor about whether there are periodic updates to your present equipment and programs.
8. Make rules and stick to them for yourself and all your employees for "physically securing" mobile devices and laptops while they are in a vehicle. Encourage safe care practices, like using the trunk or keeping the device with them at all times.
9. For a wireless network in your office which is needed to transmit documents and files electronically, ask your software vendor (ask several) about the best programs they can offer to keep your patient data safe.
10. If you have an EHR system that runs on a client-server network IN your office, consider changing to a Cloud system and put a password on it. If you choose not to use an outside vendor to maintain and protect the Cloud server, change the password weekly to keep data safe.
An "in office client-server network" is very difficult for your business to keep patient data secure because you can't be observant 24/7. While a Cloud based system may look tempting for hackers because of the volume of information stored on it, especially if the information is from multiple offices or healthcare practices, it is easier for the vendor you use to protect that system because he has more personnel and resources to keep it safe.
This link will lead to a site which offers free training materials for healthcare providers to safeguard patient information, especially on mobile devices.
On April 25, 2014, there was a financial settlement of $1,975,200 in the case of stolen laptop computers which resulted in a breach of HIPAA guidelines. At fault were Concentra Health Services in Springfield, Missouri and from QCA Health Plan in Arkansas. You could be next if you don't have at least minimal safeguards in place to protect your patient records.
Opinion Poll
Do you get frustrated when you hear about security breaches of personal information?
Final thoughts
Your social security number has become your identifying number to locate you and your records anywhere in the world.
And it is not even a secret anymore.
Update: 4/30/2014 - 4PM PDT
Most efforts to protect it will be in vain. Here's what I do to help do my part and I offer it as a suggestion to readers.
Use index cards to keep certain personal information on, so when you have eyes over your shoulder or have a queue behind you waiting their turn, you can hand the index card to the person you want to provide certain information and make sure you get it back when they are done with it.
Try not to repeat any of your identifying information out loud so it is overheard.
Keep several index cards - one with healthcare info and one with social security number, date of birth and one credit card.
If you pay for healthcare visits with credit card, try to keep one credit card for those payments and list it on your healthcare index card so you don't have to jockey credit cards around to change the info on your index cards.
Remember: All anyone needs is your social security number, your phone number or your insurance company name to identify you when similar names to yours shows up in online searches.
Thank you for reading my article. Your opinions are welcomed and your sharing of this article is appreciated so others can be made aware.
"Must See" Shocking (really) Video on Identity Theft Expert by Expert Robert Siciliano
© 2014 Rachael O'Halloran








