HOW TO SECURE COMPUTER'S HARD DISK DATA

INTRODUCTION
There are millions of bugs, worms, viruses and malware swimming through the Internet and an infection to your PC is more a question of when rather than if. The average user is sure to have an antivirus program installed, but there are other steps you need to take to ensure that your data is completely protected. The forever changing and improving nature of PC viruses means that even the most reliable antivirus might not be able to detect an infection. In some dire cases, the viruses can even start from a malicious antivirus installation itself.
Apart from protecting your data from malware or viruses, you should also take steps to prevent data loss due to file corruption and hardware or physical problems. While such incidents occur mostly by accident, having certain file handling practices in place will ensure that you never have to fret when an important document is accidentally deleted, or if it gets corrupted or stolen.
WHAT IS THE THREAT
Your local drive is like a library of everything important, both professionally and stuff that is close to your heart. If you are tech-savvy, you will have annals of photos and videos from all your vacations, a huge collection of music and movies, and important documents like scans of your passport and other sensitive documents. Along with this, you will probably have pen drives and external drives, where you store similar files, most of which is irreplaceable and the kind you wouldn’t want in the wrong hands. Viruses and malware can corrupt these drives and render all your data useless. Your data can also be stolen from an unattended PC or from stolen external storage devices so it is important to ensure that files stored on such drives aren’t easily accessible even if you have misplaced them.
HOW IT'S DONE?
Your data is relatively safer from infection when using your machine in offline mode and the main threat would come from external storage devices that contain infected files. Exchanging files with a friend or colleague whose machine isn’t well protected could lead to infection of your own machine. Files can also get corrupted, although this is fairly rare. File corruption occurs generally when a file isn't saved correctly or if a program crashes while using the file. You can also do damage to running files if your PC is powered off or is restarted manually when it hangs. File corruption also sometimes occurs when you remove an external storage device without ejecting it correctly.
Files can also be stolen from public access machines or your own local machine by an unauthorized user. A file deleted from Windows Explorer is still present in the recycle bin and some software also create regular backups of files that are being used. An unauthorized user can restore files from the recycle bin or even search for backups or temporary stored files if they are trying to steal your data.
HOW TO PREVENT IT?
The general safety rules to ensure your data is safe are something that any computer user would be aware of. Never leave your PC unattended or unlocked to allow unauthorized users from accessing it. Always ensure that you have saved your work and save multiple copies of the file on different drives or devices to make sure you can still use it from one source if another is corrupted.
PROTECT WITH PASSWORD
Preventing unauthorized users from accessing data means creating a password for everything. You can create a password lock from the very instance your PC starts up by setting a BIOS password.
The next step is the operating system for which you can create different user accounts, each with its own password. You can even lock and hide specific folders and files so that they cannot be run, copied or transferred without a password.
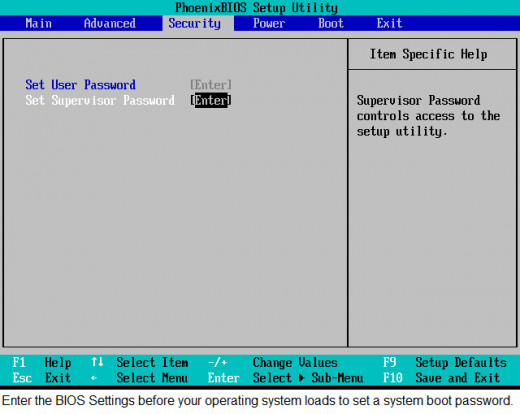
To create a BIOS password, you must enter the BIOS setup before your OS can load. When you boot your machine, the screen will display a series of diagnostics along with which there is an instruction to enter the BIOS setup. This is most commonly done by pressing [Del] or [F2]. In the BIOS setup, there is a security tab, which gives you the option to set a user password. Here, you can set a user password so that your system requests for password authentication before loading your operating system. After setting the password, remember to change the BIOS settings to prompt for a password every time the machine is started. You will find this in the BIOS features setup menu. You can also use security software that enables you to lock specific files and folders, which gives you more features like locking files, folders or entire drives.
CREATE BACKUPS
There is no telling when or how your files might get corrupted; either due to a software malfunction or physical damage to your hardware, so it is best to take safety measures by creating backups of your data. You can either use the ever growing space on cloud servers for your backups or simply save multiple copies of files on different drives. For creating backups of large amounts of data, however, you might need to use certain backup software. PCs from established manufacturers like Lenovo, HP or Dell often come with their own security suites with a backup feature. If you do not have such a suite, you can use any other software, which come with options for creating backups of specified folders or entire drives. Some backup software also give you options to encrypt data and compress files to reduce the size of your backup drive or folder.
GET A GOOD SECURITY SUITE
The best form of protection from viruses or malware is a reliable antivirus application. Most security suites these days come with a variety of services bundled into one; from virus protection to spam blockers, so good security software can help you protect your PC in many ways. It is also wise to invest in the full, paid version as the free ones sometimes come as a limited time trial version or have some features blocked. It is also important to make sure your software is up-to-date. Antivirus programs are regularly updated with the latest virus database and fixes for loopholes, so configuring regular updates is very useful.

ENCRYPT YOUR DATA
If you are going to transfer or exchange valuable or sensitive data from your machine either over the Internet or via external storage, you want to ensure that it cannot be accessed by third party users. In such cases, you should use encryption software to protect your data.
Microsoft bundles BitLocker to Go with certain versions of Windows 7 and can be used to encrypt data on your PC and removable drives. Although the software is available only with Windows 7 Ultimate or Enterprise, the encrypted files can be read even on Windows Vista or Windows XP operating systems.You can use any other encryption software also that will have many other features also.
KEEP YOUR HARDWARE SAFE
To keep your data safe, you must ensure that your storage hardware is safe. Hard disk drives are vulnerable to physical damage, so external storage drives should be kept secure and safe from shock. You should also get a voltage stabilizer or a UPS for your machine to ensure that no damage is done due to fluctuating power supply. These two hazards are the primary causes of damage to hard drives due to which your local data can be lost.



