The History of the Computer Viruses

Computer Viruses
Computer viruses are huge problem in modern society. A virus can harm computers system in various way. They steal data, delete information, harm operating systems and so on. Off course, each new virus that infects your system reveals the vulnerability. But the negative effect of the virus can cost millions of dollars if important information is lost during the infection.
The most known viruses that caused huge harm to various systems are Mydoom (2004), Melissa (1999), ILOVEYOU (2000), Storm (2007). These viruses infected millions of computers. For example, Melissa forced Microsoft to shut down their mailing system temporarily. I bet, that those, who do not like Windows OS were pretty happy. I LOVE YOU virus infected over 50 million of computers. Pretty big number, don't you think so?
If you are afraid of computer viruses, try sit down and relax. Explore the wonderful world of malicious programs and you will be afraid much more than you were before. I am kidding. Or maybe I am not. The idea is that you must explore the history of computer viruses to know their origins and targets. This is the only way to find the best cure for your computer.
Which malware is the most dangerous?
Classification of Malicious Programs
It is hard to speak only about viruses. Viruses were the first malicious programs. But later, when internet appeared, many other malicious programs were created. here are several types of malicious programs, that are widely spread. All these types of malware act in completely different way. But their aim is similar.
Virus. A computer virus is a computer program that can replicate itself. Another property of virus is that it spread from one computer to another. The virus attach itself to a computer program or application. Every time the user runs a program, the virus is launched too. It replicates itself and attach the code to other programs. When the user downloads the infected program or file and launches it, the system becomes infected. If infected files are copied to other system, it becomes infected too. This is how the virus spread. The viruses do do spread themselves. The user is needed to copy infected files. The virus can do various harm to a computer or system. The virus can make undesirable changes to the system. It can delete files, damage operating system and so on.
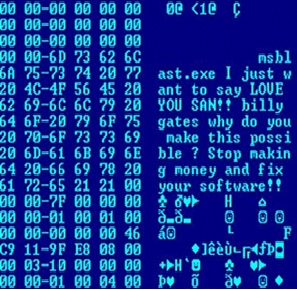
E-Mail Virus. E-mail virus is the same virus as written above. The only difference between a virus and e-mail virus is the way how these two kind of programs spread. E-mail virus spread as an attachments to e-mail letters. Once the system is infected, the virus sends automatic copies of itself to all the addresses that are found in an address book. In mostly cases to infect the system attachment with virus must be opened. But there are some cases, when virus replicates itself when the user is reading letter. Famous Skype viruses spread the similar way.
Trojan horse. Do you remember the story about Trojan horse from Greek mythology? This term is associated with ruse. In computer science a Trojan horse is a program, that looks like a normal computer program. The only problem is that the Trojan horse is a program that is stated to do certain things, but instead of that it does another ones. The Trojan horse pretends to be a useful program, but actually it is a malicious program. Let say you have downloaded a game. If it is a Trojan horse, the program may send all you data to somebody. Also it may defect your operating system, open some ports for worms and so on. Trojan horses do not spread automatically too. The user is needed to download or copy it.
Worm. Worms are malicious programs that spread over the network. Worms usually use security holes in computer networks to spread. The worm search the network until find the computer with specific security hole. Once the hole is found, a worm copies itself to a new computer and start new search for other computers to infect. Computer worms are quite nasty thing. The holes they find can be used as backdoor and private data can be stolen. Remember, that the most secured computer in the one, which is not connected to the internet.
Date
| Virus
| Target or Type
|
|---|---|---|
1970
| Creeper
| DEC PDP-10 computers
|
1974
| ANIMAL
| UNIVAC 1108
|
1981
| Elk Cloner
| Apple II
|
1986
| Brain
| IBM PC
|
1989
| Ghostball
| multipartite virus
|
1992
| Michelangelo
| DOS systems
|
1994
| OneHalf
| DOS based polymorphic virus
|
1999
| Happy99
| Worm
|
2000
| ILOVEYOU
| Computers with Windows OS
|
2004
| MyDoom
| Mass mailer worm
|
2006
| Nyxem
| MS Word files, worm
|
2008
| Koobface
| Facebook, Myspace users, worm
|
2010
| Kanzero
| P2P sites, virus
|
2011
| Zeus
| mobile phone banking information
|
2012
| Flame
| Windows systems, computer espionage
|
History of computer viruses timeline
History of Computer Viruses
The computer viruses appeared since the first computers were created. The theory about self replicated computer programs was developed in 1949. The firs self replicating program was created. This may be considered as the first computer virus ever made, but it was created for scientific purposes. The first computer virus as we know them now appeared in 1970-1972. The Creeper was found on ARPANET network. Later more computer viruses has appeared. They spread via pirated computer games written in 3.5" floppy disks.
The history of computer viruses is very rich. There are viruses that made huge harm to computers, while others were created for fun. The history of computer viruses timeline is shown in the table. It is impossible to talk about every virus ever created, because there are thousands of them. Computer security companies that create antivirus software update their databases for viruses almost every day. It is good to know, that somebody is keeping us save. Off course, there are many conspiracy theories about security companies. It is said, that most of the viruses are created by computer security companies. Personally, I would not believe that. But who knows.
The aims of computer viruses are different. At the moment, most of them are targeted to steal personal data. Personal data is used to make money. This is a crime. There are viruses that are created by geek programmers to check their skills. There are viruses that are made to harm operating system. Check the table for most popular viruses and their targets.
- The History of the Computer Generations
Imagine, that the firs computers filled the whole room. Now we have computers such small that they can be put in our pocket. Explore the evolution of computers and find out what technological achievements allowed computers to become as powerful as we
The Creeper - first computer virus
The Creeper virus is considered to be the first computer virus ever. It appeared in 1970-1971. The Creeper was created by Bob Thomas as experimental self replicating program. The name for the virus came from Scooby Doo cartoons. The episode Jeepers, It's the Creeper was aired in 1970. The Creeper spread through the ARPANET and infected DEC PDP-10 computers. This virus displayed the message: "I'm the Creeper, catch me if you can". Also it messed printers. This was experimental program, and it replicated itself. After the replication Creeper deleted the old version of itself. The Creeper was caught by a program called Reaper. This may be considered as the first antivirus program, but the term "virus" was not used at those days until 1983. So the first official antivirus programs came later.

![Kaspersky Anti-Virus 2015 3 User, 1 Year [Online Code]](https://m.media-amazon.com/images/I/41y6dYFamDL._SL160_.jpg)
How to Avoid Computer Viruses
The history of computer viruses is very rich. Viruses and other malicious programs evolved as new computer technologies were implemented. The antivirus programs also evolved. Where there is a virus, it must have its cure. There are debates going which was the first antivirus program. G Data and UVK 2000 both were developed in 1987. Now you can find many antivirus products to buy.
There are several things your should/shouldn't do to avoid computer virus infections. You should never click mail attachment or link, if you are not sure about the sender. Avoid files with double extensions, such as filename.jpeg.exe. Check all external storage devices for viruses before using them. Avoid visiting suspicious websites and pop up banners: use filters that are integrated in web browsers. Use antivirus and antispyware program. Update your operating system regularly, because there may be some serious security updates. Use your brains while browsing. The last one is the most important tip I suppose.
It is very hard to choose the best antivirus program, but at the moment these products are worth your attention: BitDefender Antivirus, Norton Antivirus, Kaspersky Antivirus, AVG Antivirus and other. When choosing antivirus program you should be very careful, because there are many suspicious and malicious programs that pretend to be antivirus or antispyware products. Choose the know software.