- HubPages»
- Technology»
- Internet & the Web»
- Viruses, Spyware & Internet Security
Infected With Trojan.ADH.2? - How to Remove It?
“I keep hearing what sounds to be ads in my speakers/headset so I run a scan with Malwarebytes. In the end, it says that it has quarantined the file C:\Windows\System32\rpcss.dll which has been infected with Trojan.ADH.2. However, this doesn't stop the ads from coming up. I still hear the annoying audio ads in the background. Malwarebytes also keeps popping up that it has blocked the threat about once every 40 seconds to a minute. How can I get rid of the threat? “
Learn more about Trojan.ADH.2:
Trojan.ADH.2 is identified as a malicious Trojan horse that can damage the computer severely. It is often found to infect scvhost.exe on the computer. However, many antivirus applications just can help stop and quarantine this threat, but fail to completely delete it. This Trojan can reoccur over and over again after it has been quarantined. In fact, this Trojan is designed by cyber criminals to corrupt target computers terribly and then steal information from the target users. It has the capability to play audio ads in the background once it gets into the compromised PC. You may feel strange to hear such unexpected advertisements when surfing the Internet without opening any media programs.
Screenshot of the threat detected by Symantec Antivirus:
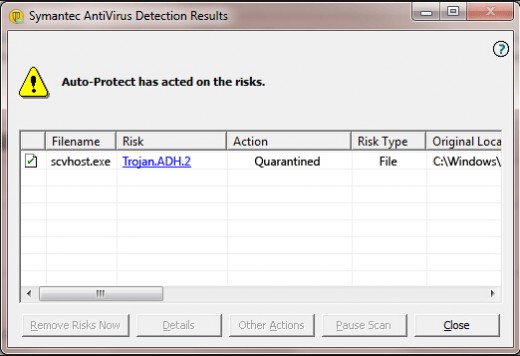
Once installed on your computer, this Trojan can affect your computer performance obviously by modifying the infected rpcss.dll. Since rpcss.dll is a system process it should not be altered easily. The process is required for your PC to work properly. If it is changed by the threat, many computer issues may occur. On the one hand, the Trojan is able to run automatically every time Windows starts. Whenever you start up PC, this threat can be triggered at startup. Then it will start to perform a list of harmful tasks. On the other hand, it may connect to remote servers and download other malicious files or programs on the infected computer, further damaging and compromising the PC. In this way, the data that stored on your PC may be uploaded randomly, which can lead to your personal private information leak. Third parties may get and make use of the data to make illegal profits. Moreover, it may even open a backdoor for remote hackers to access the PC without permission. Then attackers can your trace system records and browser histories to steal your confidential information and compromise the system security aggressively. As a consequence, your log-in passwords, ID number, online credit card passwords or other personal information could be recorded and stolen.
The Trojan is not only a threat to your personal privacy, but also a time bomb to your infected computer. It can endanger your computer security seriously by modifying some vital settings. Some functions of the security tools that installed on your PC may be disabled or turned off by this malware, which makes the infected PC vulnerable for other cyber threats. Under the circumstances, many other malware like ransomware, rogue programs, spyware and so on can take the opportunity to invade the same machine.
Therefore, in order to protect your computer from further damages, please remove Trojan.ADH.2 from the computer as quickly as you can.
Attention: Usually, the Trojan is distributed through harmful websites, suspicious links and free downloads, etc. It may slip into your computer as a harmless application when you visit unsafe web pages or download free items from infected website without letting you know. Therefore, you need to be more careful when surfing the Internet. NEVER visit the malicious websites or click on unknown attachments or links in junk emails.
Symptoms of getting infected by Trojan.ADH.2:
1) Some audio advertisements appear on your computer without rhyme or reason.
2) Some application errors or system errors may pop up when you run programs.
3) The computer speed becomes very slow and it takes you a long time to wait a program to respond.
4) The computer may freeze or crash frequently or encounter blue screen of death error.
5) Some unwanted or strange programs and files may be found on your PC without your permission.
How to get rid of Trojan.ADH.2 and repair the infected PC manually?
Currently, many antivirus applications may fail to thoroughly clear this Trojan from the infected computer. To eradicate the threat, you can follow the instructions below and effectively delete all components of the Trojan.
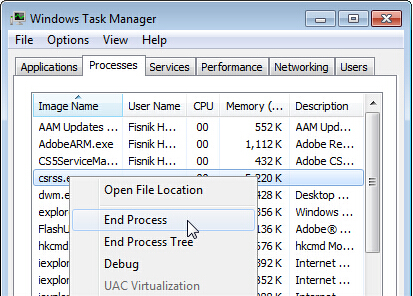
Step 1: Open Windows Task Manager to end process associated with this Trojan. To do that, press Ctrl + Alt + Delete keys at the same time to open Window Task Manager.

Go to Processes tab on top and scroll down the list to find the suspicious process then right click on it and select End Process.
[random].exe
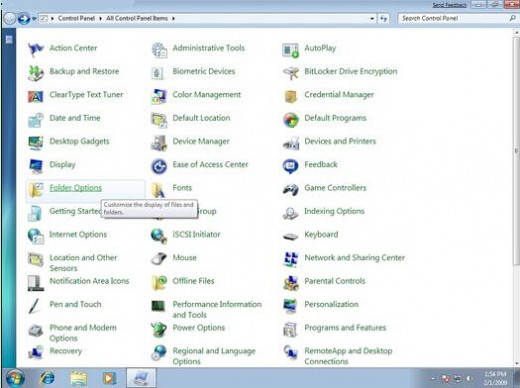
Step 2: Show hidden folders and files and delete malicious files. Open Folder Options by clicking Control Panel, clicking Appearance and Personalization and clicking Folder Options.
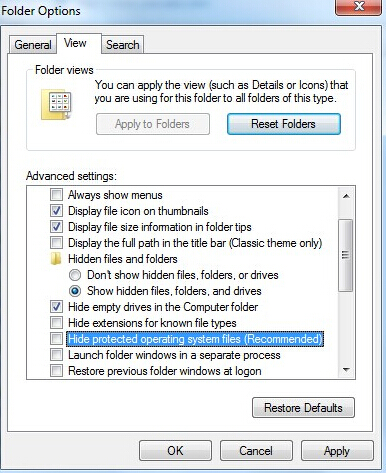
Under View tab, tick Show hidden files, folders and drivers and uncheck Hide protected operating system files (Recommended) and then click OK.
Search for the following folders and delete files created by Trojan.ADH.2.
C:\windows\winstart.bat
C:\windows\wininit.ini
C:\windows\Autoexec.bat
C:\Windows\System32
Step 3: Modify the registry entries that changed by the Trojan. Press Windows key + R key to start Run box.

Then type in regedit and click OK to open Registry Editor.
In the registry entries, locate the following registry keys and alter them.
Change the value of the below entry to “NT AUTHORITY\NetworkService”.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet \Services\rpcss\ObjectName
Change the value of the below entry to “%SystemRoot%\system32 \rpcss.dll”.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\rpcss\Parameters\ServiceDll
Warning: It is risky to modify the Windows registry because any wrong modification may lead to serious consequence to your computer. You are not suggested to modify this part of PC until you are confident about it.
Step4: Download a compatible version of rpcss.dll to replace the old one. You can go to a reputable dll file download website and download a version of rpcss.dll that works on your system. Save it on your PC and right click on it to select the option to decompress the file. Then drag the file to the right location to replace the infected one. Then reboot your PC.
Recommended method:
In addition to the manual steps above, there is another easy way to remove Trojan.ADH.2 completely. We highly recommend you to use a professional and powerful removal tool to delete the Trojan as well as its leftovers once for all within minutes. For those computer beginners, it’s too hard and sophisticated to make modifications on program files and system registry. If you are not familiar with computer, please download and install a reliable and powerful removal tool to help eliminate the Trojan instead.
Download a professional removal tool on your PC.
Perform a scan of your infected PC with the tool.
Delete all infected files and registry entries of the Trojan.
With a few simple steps and you will be able to protect your machine from the malicious Trojan attack. Therefore, use a professional removal to get rid of Trojan.ADH.2 if you are not good at delete it manually.
© 2014 Joan White








