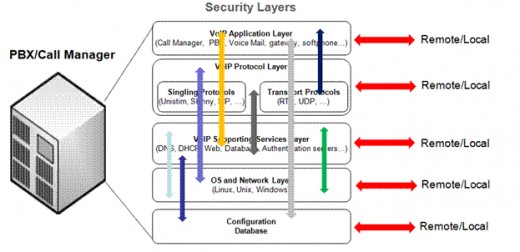
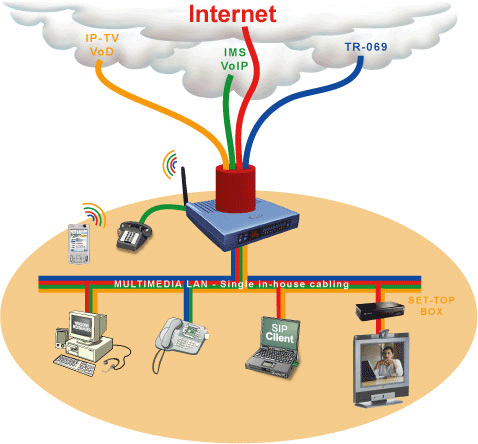
VoIP phone security solutions for confidential business information
This article is meant for people into serious business; it is for those who are looking to secure their VoIP connection because via this article, I am going to show you how one can secure his/her organization’s VoIP connection in a safe and sound manner. As you already know, Internet is unreliable a lot of times for sending and receiving high-quality confidential business information because the currently available IP/TCP protocols do not provide a sure-shot bandwidth reservation or guarantee of the quality of service and for that reason, the overall call quality over voice over IP gets adversely affected due to power failure or network congestion causing loss or late receiving of voice call packets. Public Internet network creates an environment that is marked by a dramatic fluctuation of uncontrollable load, which cannot guarantee acceptable voice connections therefore it can cause leakage of your confidential business information.
VoIP security solution #1: Encryption is a common method of preventing a hacker’s attack on your VoIP network.
I agree that encryption is a way to prevent a VoIP attack, but unfortunately I have to say that it consumes a lot of bandwidth at the same time. If you are looking for encrypting your network system, there are many ways available for encryption and some of them are virtual private networking (VPN) and SRTP (Secure Real-Time Transport Protocol), but the most important key in any form of encryption is to choose an encryption algorithm which is very efficient, fast, and devotes a dedicated encryption processor. Another option for encryption would be to quality of service or QoS. Quality of service is required to make sure that the voice call is always handled in a timely manner thereby reducing the loss of quality.

VoIP security or in simple terms securing voice over internet services can be solved by some new protocols which are able to provide different types of priority services or packages and have some ability to reserve a bandwidth via the network for a certain duration of call, so for making your VoIP protocol much more secure, new technologies are providing the ability not only to allocate bandwidth with priority of packets, but they are also giving them preference to process themselves within the router in order to make sure that high-priority voice packets are processed first and less-priority voice packets are processed after that. These types of improvements in communication technology to the protocols and algorithms in the switches and routers are decreasing packet loss problems and time taken by the packets to go to a specified location thereby ensuring better service quality. Fortunately, these new developments have enabled VoIP service providers to meet the standards required for voice services.
Secure VOIP communication with ZRTP - Linux Journal Presents: Phil Zimmermann comes to the rescue again with ZRTP, a protocol for securely transfering keys acro
For securing our whole VoIP system, some things which should taken into account is making sure all elements of your VoIP network are secure which are mobile workplace, call server, switches, and routers. A person needs to configure each of these devices to make sure that they are in line with demands in terms of overall VoIP security. For instance, the servers should have small work functions and should only open the ports that are actually required. Switches and Routers must be properly configured at all times with access control filters and lists. All these devices must be updated on a regular basis plus same types of precautions must be taken into account when adding new elements or modifying old elements to data network keeping in mind that we only have to extend this process to a portion which belongs to our VoIP network.
Building VoIP Clusters with Asterisk (1 of 6)
VoIP security solution #2: Use of firewalls and intrusion detection systems for securing VoIP systems
Two other main things we can do for securing our VoIP connection is to use a firewall and an intrusion detection system or IDS in order to protect our voice network but it is not really easy to do that because Voice over IP firewalls are complicated to use and have multi requirements. If we talk about call servers which constantly open and close ports for new connections, this dynamic element makes its own management much more complicated, but the cost of security our VoIP network with addition of firewall and IDS is comparable with the amount of benefits. A system manager trying to secure VoIP system must give special care to improve access controls. An intrusion detection system monitors the network for detecting any abnormalities in service or potential abuse of the system. The warning serves as a key to prevent further intruding or hacking attacks.
Although IP based private networks provide high quality voice services, in addition to using their network capabilities, activities, and plans to avoid congestion, these networks can take advantage of improvements made to the TCP/IP, which allows us to assign high priority to real time traffic or voice data as opposed to the traditional ones.
Packet switching networks are able to carry voice calls efficiently using high quality 8 kbps bandwidth compared to traditional circuit-switched networks, which use 64 kbps bandwidth which much more than what packet-switching networks use. In addition to that, infrastructure cost that is associated with implementation of packet-switching networks is much more lower and cheaper than traditional circuit-switched networks. Because of this, new phone service providers are increasingly using packet-switching network type of systems.