When Security Becomes a Trojan Horse

I think Security is
What is Security?
Security can be related to several subjects:
- protection of a person(s) / population,
- protection of a building(s) / organization(s),
- protection of information,
- protection of a country.
Primarily is security meant to prevent harm to, or robbery and damage of the above subjects.
Secondly, is security increasingly used as a mean to identify suspects after they've committed an offense by looking back recorded video.
There seems not much wrong with this at first hand.
From Wikipedia
A Trojan horse, or Trojan, in computing is any malicious computer program which misrepresents itself to appear useful, routine, or interesting in order to persuade a victim to install it. The term is derived from the Ancient Greek story of the wooden horse that was used to help Greek troops invade the city of Troy by stealth

About Private Security Contractors
Private Security Contractors, shortly PSCs, is booming business. Part of this business became PMCs, Private Military Contractors. It's one of the most steadily growing businesses, showing a constant annual growth of 7 to 8% over the last 30 years. In many countries PSCs employ more personnel than the police.
The PSCs business accounts annually for nearly 300 billion US$ (2014), and employs worldwide 25 million security guards.
Some of these companies can be classified as extremely militant, like Triple Canopy and ACADEMI that are involved in violent military operations.
The global trend towards downsizing of governments, including public security institutions, has contributed to the growth of the private security sector.
Who is holding the most guns? The monopoly on violence is shifting from government to businesses. Democracy is becoming increasingly a Corporatocracy.

Most Used KPI's in Security Industry
KPI stands for Key Performance Indicator. Every professional industry uses KPI's to monitor targets.
The main goal of any security company is to decrease responsive actions and to increase proactive actions. Proactiveness cuts costs and prevents the related negative events to occur.
We see two things happening at the moment:
- the monopoly on violence is shifting from government to businesses,
- the actions are shifting from responsive to proactive.
What are the consequences? That businesses, based upon automated algorithms, will determine who in the public arena is showing suspicious behaviour.
PSC'ers in Warzones in Relation to Soldiers
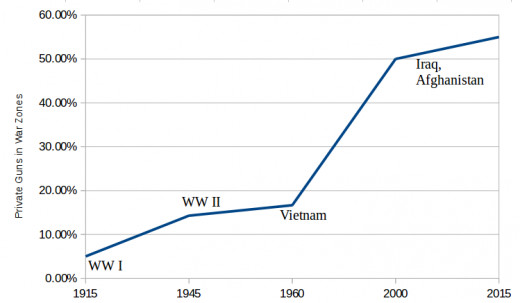
more than 50 per cent of all contracts are not subject to any monitoring to ensure the performance of suppliers with contract terms
— David Isenberg - author of Shadow ForceSuspicious Behaviour
Rapid developments of video analysis techniques give increasingly the ability to identify suspicious behaviour pro-actively, and give the ability to act before any negative event occurred.
The video analysis technology is still in its infancy. The current algorithms are capable to:
- recognize suspicious behaviour,
- count persons and vehicles,
- recognize left luggage or packages,
- recognize faces.
Is there something wrong with this? Well, that depends what you define with suspicious behaviour.
The definition of suspicious behaviour depends on the ones who are in power. And that is something that is not chiselled in granite.
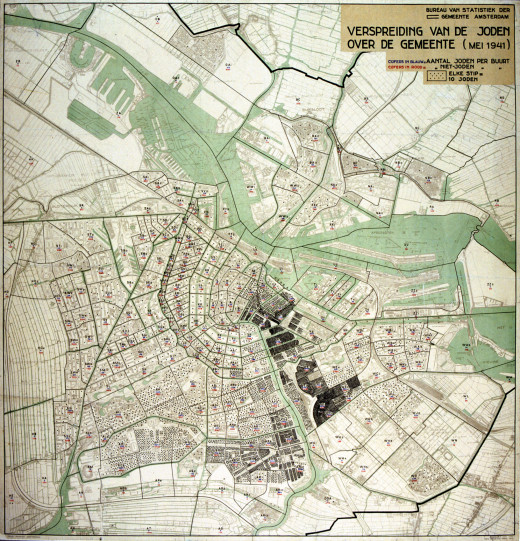
History Always Repeats Itself
Can you recall what happened during the Nazi oppression? Jews, Gypsies, Jehovah's Witnesses, homosexuals and mentally handicapped were systematically traced and exterminated.
Let's look at the Jews. The Jews were nota bene themselves responsible for the purchase and distribution of badges - the Star of David. When a Jew was caught not wearing a star, then he/she ended up in jail or shot dead on the spot.
So, this distribution of stars seemed to be a social action. But they didn't knew the other consequence of wearing the Star of David at that time. Or did they?
A Jew was a suspect. The crime during the Nazi regime was being a Jew. That is in our Democracy no crime anymore. Crimes are only related to current ruling power.
Over-active officials were also good in registering Jews in the town archives, which made the job of the Nazi's much easier. Registration was the only way to separate the wheat from the chaff.
Do you see?
Top 10 countries with the Highest PSCs rates
Rank
| Country
| Percentage
| PSCs Employees
| Inhabitants
|
|---|---|---|---|---|
#1
| Hungary
| 1.05%
| 105,121
| 10,013,628
|
#2
| Guatemala
| 0.94%
| 120,000
| 12,710,000
|
#3
| Panama
| 0.93%
| 30,000
| 3,232,000
|
#4
| Honduras
| 0.87%
| 60,000
| 6,893,000
|
#5
| South Africa
| 0.81%
| 387,273
| 48,073,000
|
#6
| Brazil
| 0.75%
| 56,486
| 7,576,751
|
#7
| United States
| 0.66%
| 2,000,000
| 302,741,000
|
#8
| India
| 0.62%
| 7,000,000
| 1,130,618,000
|
#9
| Jamaica
| 0.56%
| 15,000
| 2,668,000
|
#10
| Australia
| 0.56%
| 114,600
| 20,395,000
|
Source: smallarmssurvey.org most figures are of 2011.
The Use of Firearms by PSCs
Just a few countries prohibit the use of firearms by PSCs on their territory - including Denmark, Japan, Kenya, the Netherlands, Nigeria, Norway, and the UK.
In some countries PSCs are allowed to use fire-arms only for specific operations. In China and France, for instance, PSCs may legally carry firearms when escorting money to and from banks.
Countries that legalized for PSC's to carry a gun, have no official information on what percentage of personnel normally carry a gun. Based upon the fact that guards may share firearms between shifts, it is estimated that two million of the PSC's in the US have access to a gun.
Worldwide have PSCs access to 3 million legal firearms, and since firearms can be shared between shifts, with a ratio of 1:4, 12 million PSC's have access to a gun. The heaviest weapons that PSC's are usually able to use is the legendary AK-47.
Gathered Information in the Public Domain
The second largest private employer in the world behind WalMart is G4S, which for example, acquired recently Armorgroup that runs a 10,000 men strong army. This is not just an average neat company. It is even paid with tax money.
It is astonishing to see that just a handful very large companies control our 'security' worldwide. The 6 largest PSCs gather about 70% of all the video data around the world.
These 6 big ones operate more than 200 million cameras of the total estimated 300 million surveillance cameras worldwide (2014). There is not one cosmopolitan who is not catched on one of the cameras of these companies, meaning that your data is stored many times in datacenters.
It will be such a disadvantage not to have the implant that it will essentially not be optional
— Dr. Mark Gasson (cybernetics scientist)
How Safety Becomes a Trojan Horse
You will probably say - and so what? Can you recall what you did on just a random day a month ago? Or the day before that? No, you cannot, but these cameras can.
Within a few years cameras will be equipped with chip scanners. Once people, like animals (which we are now used to), have a RFID microchip implanted, there's no escape from the systems behind these cameras identifying you everywhere. If you feel OK with this, you're nothing more than cattle.
Around 2020 will be most people used to the idea of many new smart technologies, and start to have a chip implanted. Ignorance obtains for ease at customs control, or any other convenience that comes with this chip implant, maybe in connection with their 'smart' devices.
The cameras that have become behaviour/tracking devices are then able to distinguish you including your behaviour. You will not be able to walk freely on this planet anymore. Do you see? Or not?
By that time, the corporatocracy has the
- information,
- guns,
- monopoly on force.
Remember what happened in WWII, with the difference that the target groups are yet unknown to us.
Beware of Trojan Horses!
© 2015 by Buildreps



