- HubPages»
- Technology»
- Internet & the Web»
- Viruses, Spyware & Internet Security
How to Stay Safe from Hacking
You may think that your usernames and passwords are safe, but hackers have ways of gaining access to your supposedly “secret” information. For example, your PC could have spyware with a key logger installed that provides the hacker with info about everything you enter using your keyboard, including your login information.
Or, hackers can use a brute-force style of attack using password-cracking software that will attempt to log in using various combinations of words and numbers. These programs can try thousands of different combinations in seconds. And once the hackers break into a single account, such as your webmail, they can take a guess at your other login and password pairings to break into your other online accounts— or even steal your identity. We’ll examine what you’ll need to protect your digital life from intrusion.
Security Starts at Home
How you can protect yourself from hacking. The first step is to install security software on all of your devices, including your PCs, Macs, and mobile devices. Security software is often the first defense against online threats and can detect and block most threats before they appear on your device. It’s also important to ensure that your security software is active and has access to the Internet to download the latest virus definitions. Thousands of new malware variants are discovered every day, so falling behind on virus definitions updates for even a day or two can put your system at risk.
Note that to protect your PC, Mac, smartphones, and tablets; you’ll want a security application designed specifically for use on both desktop and mobile devices. For example, Norton 360 Multi-Device provides protection for up to five devices running Windows (XP, Vista, 7 & 8), Mac (OS X 10.7 or 10.8), Android smartphones and tablets, and iPhones and iPads. Ensure that all of the applications on your computers and mobile devices are up-to-date, because software developers routinely fix bugs and vulnerabilities that hackers can use to infiltrate your PC. It’s most important that you keep the operating system up-to-date, because it’s the most common target for hackers.
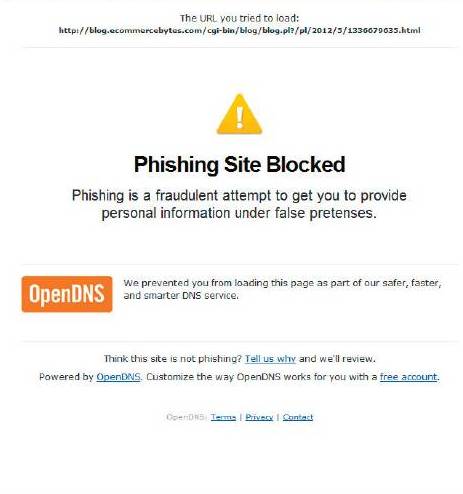
Avoid Pop-Ups & Email Links
It may seem obvious, but be sure to avoid clicking on website pop-ups and also on links in emails from unknown entities—and even in emails that purport to be from someone you know. Malicious software is commonly installed when users inadvertently install a program sent to them in an email.
To prevent identity theft, it’s best to limit the amount of information you make public on social networking websites.
Why You Want a Suite
Modern security suites offer more than just traditional antivirus protection; that’s because today’s threats require a more robust, all-around defense. For example, most security suites provide you with a firewall, a piece of software that determines which network traffic is allowed to enter and leave your PC, as well as providing protection against some forms of spyware and viruses. When comparing security software, check out the extras added by the software provider. Norton Internet Security offers Vulnerability and IPS (Intrusion Protection) to look for signs of malicious activity deep within the network traffic entering and leaving your computer to ensure that attackers are blocked from exploiting weaknesses in your computer’s operating system and the software running on it. This defense technique is particularly effective at blocking web-based attacks, which have increasingly become the attack vector of choice.
Another technology found in Norton Internet Security is Symantec’s SONAR technology, which monitors the regular execution of software applications on your computer by looking for signs of trouble that typically indicate the presence of malware. To avoid phishing scams, many security suites, including Norton Internet Security, offer the ability to block known dangerous websites and emails by scanning content before you open it. For instance, anti-phishing tools will look through links in emails to assure that they aren’t taking you to malware-filled websites. One up-and-coming threat is ransom ware, an attack in which cybercriminals use malicious software to lock your computer and then demand a fine in order to unlock it.
A strong security suite can prevent this locking software from ever installing itself on your computer, whereas a basic antivirus program would not.”

Tips to stay safe online from hackers
Why You Shouldn’t Repeat Passwords
Do you use the same password for all of your online accounts? Many do, but it’s not a good practice. Even if the password is very complex, once a hacker steals one password, he can use it on the rest of your accounts. Everyone is aware that it can be disastrous if cybercriminals gain access to your banking accounts, but it can be equally harmful if email and social networking accounts are left poorly protected, since they can be used to verify other accounts and to reset passwords. You should make sure the passwords for those accounts are complex and that they are changed every few months.
The problem is that it’s tough for us to remember the all the different passwords we need, or even which passwords correlate with a given Web sites. And storing the passwords somewhere—is not advisable.. Consider using a password manager, such as Norton Identity Safe, which will save you the hassle of remembering the password for each site. It’s also a good idea to log out when you’re finished accessing sensitive accounts.
Once the password manager has your usernames and passwords stored, the software will automatically and securely log on to the sites you enter by automatically filling in the open fields. Besides reducing the burden of remembering the credentials, this method also helps to defeat hackers who use keyloggers to monitor the keys you press. Some password managers also feature a random password generator, which is a great tool for creating highly secure passwords. After a password is generated, the software will save the password and associate it with the website and username you prefer, so you’ll never need to remember the complex sequence.
A Final Check
In addition to changing your password and examining your account recovery, check back through your email account settings to make sure nothing has been changed. It’s possible that the hacker configured your account with a forwarding rule, so he can continue to monitor your email account.
Once you’re changed the password and examined your account settings, you should be able to return to your online accounts with relative confidence in the new security.
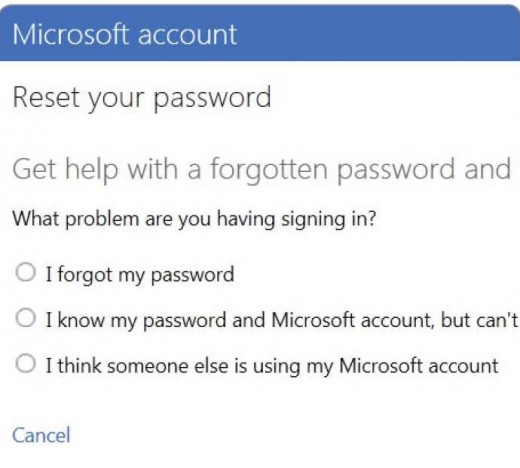
What To Do If You’re Hacked
If you suspect that your accounts have been hacked, take action immediately by shutting down or changing the password for any affected accounts, Notify your account provider and give as many details as possible. Let your friends and family know you’ve been hacked and that they shouldn’t click on links in suspicious emails from you or posts on social networks. Also, run a security scan on your computer to make sure no malicious programs have been installed. Most websites that require a login, including Outlook. com, Gmail, and Facebook, include detailed instructions about what you should do if your account has been compromised.
Most online services offer some form of account recovery options, so you’ll be able to reset the password or gain access to the account through an alternate email or mobile phone number if the hackers has changed the password. Some websites also have an account history, so you may be able to determine when your account was logged into. Check regularly to see if hackers are logging into your account. If your account has access to your financial details, like your credit cards, check your banking and credit reports carefully. The sooner you catch fraudulent behavior, the easier it will be to refute.



![How to Remove Kaspersky Password Protection? [Easily Recover] How to Remove Kaspersky Password Protection? [Easily Recover]](https://images.saymedia-content.com/.image/t_share/MTc2Mjk3NDcwOTAzNTkyMTI2/how-to-remove-kaspersky-password-protected-easily-recover.png)