The Criminal's Guide to Bitcoin - The Basics on Striking It Rich
So you want to be a criminal?
Make no mistake; the life of a criminal is not an easy one. You’ll be dealing with shady people, some of which are incredibly dangerous. There’s also a very good chance you’ll be fighting to avoid federal agents and the like, with a risk of a hefty fine and jail time if you’re caught. But if you truly want to venture down this road, if you do things correctly, then there’s a possibility you can make quite the fortune…
In the modern day, criminals actually have the ability to set up their own store “a la eBay” and sell products that some may consider illegal (stupid government). By following the steps here, you too can own your very own online shop filled to the brim with AK-47s and Cocaine!
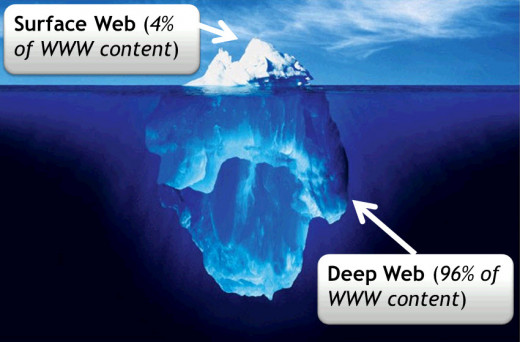
But just where are these stores? Why have I never seen them before? What does a guy have to do to purchase some credit card details and a bazooka? Well, strangely enough, selling these things on the regular internet will probably get you imprisoned and your website nicked. Fortunately for you and I, there exists a large portion of the internet dedicated to this sort of thing… The Deep Web.
WARNING! THE FOLLOWING GUIDE IS FOR EDUCATIONAL PURPOSES ONLY! I AM IN NO WAY RESPONSIBLE SHOULD YOU CAUGHT BREAKING THE LAW!
With that out of the way, let’s get started!
The Three Steps
Before we start making some cash, there are a few things we need to do first if you don’t want to look like a common meth dealer. I like to call them The Three Steps:
- Acquiring Bitcoin – Where we’re going, credit cards and PayPal accounts are useless. Think flying to another country and forgetting the savages take lamb heads over US dollars. To that end, we need Bitcoin.
- Setting up – Once we have our virtual currency, we need to make sure we have the necessary tools to not only access the Deep Web, but to make sure the feds can’t trace us.
- Enter the Deep Web – Finally, with everything in place, we can make our into the Deep Web and start making some cash!
Acquiring Bitcoin
So before we assemble our criminal empire, we do need a start-up investment of sorts. This will be used to set up our store, acquire merchandise and to hire hitmen to kill off the competition. We need Bitcoin.
Why Bitcoin?
Judging by the fact you clicked on the article, I assume you have a basic understanding of Bitcoin. In case you don’t however, Bitcoin is a cryptocurrency, meaning it’s an actual form of money we can use to buy stuff. Except instead of being papery or metal, it’s virtual. Hence the term, cryptocurrency. What make Bitcoin so appealing are the fast transactions and the anonymity behind it.
Where Can I Get Bitcoin?
There are various ways of getting Bitcoin. By far the most common and efficient way is to simply buy the things. At the time of writing, an entire Bitcoin costs around $580. The great thing about Bitcoins though is that they can be broken down, like converting a dollar to cents. You can buy a half, a quarter, an eighth, or even a thousandth!
If you don’t want to buy it, there are ways you can earn it. If you have a fast PC (and I mean very fast, preferably with a good graphics card), you can ‘mine’ Bitcoin, but don’t expect much of a yield here. You could also complete offers and surveys to earn it, but again, don’t expect to have enough to purchase a French villa.
Of course, there are illegal ways of earning Bitcoin, notably stealing it, and I’d be happy to cover this complex subject in the future. For now though, I recommend you buy the stuff so we can get a move on.
Setting Up
Now that you have some Bitcoin to use, we need to prepare our computer for entry into the Deep Web. As a diver needs a submarine to enter the darkest depths of the ocean, we need our own vessel to reach the wondrous world of drugs and guns. But as a submarine must be well protected from pressure, we need to install our own protection methods so we don’t get caught. This would be bad.
The Onion Network
The Onion Network is used by a large portion of people. From the military to journalists to politicians, anyone who uses TOR will be granted an excellent level of privacy from the prying eyes of the government and other peeping toms. However, whilst it does indeed give us a starting point to conceal ourselves, we also need it to access the Deep Web.
Download the Onion Network Browser Bundle here!
Proxy
You know at school how most websites were blocked? How on earth could you get through your day without checking your emails and watching a funny cat video on YouTube? You couldn’t, which is why you used a proxy! Proxies are useful for hiding from both school IT inspectors and the NSA.
A VPN coupled with a Proxy can certainly provide an incredibly decent protection package, so I’d certainly recommend using one.
You can find a list of Proxies at the end of this Hub.
VPN
VPNs (or Virtual Private Networks) are a must if you’re planning becoming the new Al Capone. I won’t go into the technical details, but it will assure that data sent to and from your computer is encrypted, making it incredibly useful.
When looking for a VPN, you’ll want to choose a paid one. This will guarantee a premium service that won’t sell you out, unlike some of the free options. Furthermore, you’ll need to find one that takes Bitcoin.
You can find a list of VPNs at the end of this Hub.
Other Stuff
If you’re paranoid, then you might want to further decrease your chances of receiving a visit from the FBI. And that’s good! Paranoia is excellent! Whilst I’m no true expert in this field, I would highly recommend you check out the ‘Anonymous Security Handbook’. Written by the leading hackers of the new world, following the advice here practically guarantees your safety for years to come.
Download the handbook here!
Search Engine
If you’re using the TOR bundle, then you’ll be using the Firefox search engine by default. For that extra layer of privacy however, I recommend you use DuckDuckGo when you go surfing. This leaves no records of your browsing whatsoever, making it a highly effective tool. Even if you don’t want to become an online gangster, I’d recommend using it in your day-to-day life.
You can find the DuckDuckGo search engine here!
Entering the Deep Web
When you’re certain all the preparations have been made, load up the TOR Browser Bundle. If installed correctly, you should be brought to a Firefox style browser with a few modifications and the TOR Browsing Homepage. If you click the links provided, you can take a look at a few more ways to ensure your privacy online. Once you’re ready, copy and paste the link below to be taken to the TOR Directory.
Link: eqt5g4fuenphqinx.onion
Creating Your Business
The easiest way of creating a business is to buy a storefront within the Deep Web. An excellent website which offers this service is [INSERT NAME HERE], where you too can own your own black market for a measly $100 dollars (about 0.18 in Bitcoin at the time of writing). It functions like a regular e-store, with the ability to add products, special offers and referral programs. For some extra dosh, you can have your own custom design and even a forum for your store.
Use the link below to buy your own store: http://shopsat2dotfotbs.onion/?ref=Shadow
Your other option, albeit more complicated but more professional, is to design the website yourself and have it hosted by one of the many Deep Web hosting companies. As I know absolutely nothing about website creation, you may want to look at another tutorial on Hubpages. Otherwise, probably best to buy the pre-made store.
Black Markets
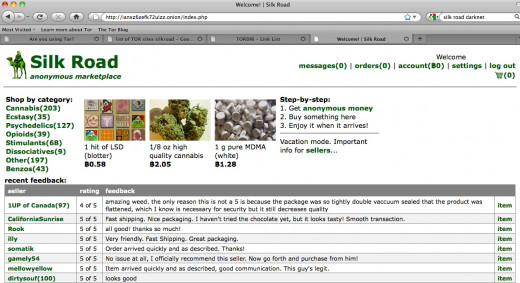
Last year, Silk Road, the biggest criminal marketplace in the history of the internet, was shut down by federal agents. During its lifespan, approximately ONE BILLION DOLLARS worth of transactions were made. Since the fall of Silk Road, several other stores have opened up across the Deep Web.
If you’re serious about selling goods but don’t have the means to acquire them in the real world, the next best thing is to buy items from other websites and sell them at a higher price. This can be time consuming, but profitable. Also, be sure to use the marketplaces I’ve provided at the end of this Hub, as some stores can and will rip you off.
For those of you who do want to sell their own ‘homemade’ products, the Deep Web has several guides on drug manufacture. I recommend checking out the recipe for Methamphetamines. If you aren’t very good with your hands but excellent with computers, hackers can always try to get a hold of credit card info and account details.
Laundering
Laundering money is the act of transforming the illegally obtained proceeds of your criminal business into ‘clean’ and legitimate cash, removing any trace of how you came to own it in the first place. Whilst Bitcoins offer a decent level of anonymity, it is incredibly easy to see the address to which the currency was sent.
There are numerous websites which will launder your ill-gotten gains for a small fee. By using these launderers, you can assure yourself that no one will be able to trace the 50 Bitcoins you earned selling PayPal account details.
Services
Aside from Laundromats, there are also other services you and your business can benefit from. There are hackers for hire, capable of stealing information and files from other websites. Private email accounts, some of which will even send messages that delete upon being sent. And of course, hitmen. Yes, if you have a few hundred grand, you too can help control the planet’s population. Once again however, make sure you’re careful in where you spend your money, as some of these places are nothing more than scams. And to think you actually paid good money to have someone blown up with C4!

Conclusion
And so, we reach the end of the guide. I hope that I have provided you with some useful information (hopefully for educational purposes only) in the art of making money as a criminal. If you enjoyed, check out some of my friendlier guides and essays. I’m not called the Philosophical Brit for nothing you know! Thanks again and I hope to see you soon!
Useful Links
VPNs:
Free:
- http://proxpn.com
- https://anonymityonline.org
- http://www.bestfreevpn.com
- http://www.your-freedom.net
- http://www.ultravpn.fr
Paid:
- http://www.swissvpn.net
- http://perfect-privacy.com
- https://www.ipredator.se
- http://www.anonine.se
- https://www.vpntunnel.se
- http://www.relakks.com
- http://www.steganos.com
Proxies:
- http://www.freeproxies.org
- http://www.socks24.org
- http://www.samair.ru/proxy
.onion Websites:
- http://3g2upl4pq6kufc4m.onion/ - DuckDuckGo Search Engine, Onion Edition
- http://3fyb44wdhnd2ghhl.onion/wiki/index.php?title=Main_Page - Safe version of the Hidden Wiki, the best source of information in the Deep Web
- http://fogcore5n3ov3tui.onion/ - Bitcoin Laundering