How to Make Secret Codes
Secret Code Messages
Whether you are pretending to be a secret agent or are just a kid trying to pass a coded note in school, if you know a few different options for how to make secret codes, you can create your own super-secret communication method all on your own.
There are a number of ways to construct secret codes, but the most common alternatives that people of all ages can figure out how to use are the classic cipher, date cipher, or a keyword cipher. All of these are very simple to use but won't be cracked by a common person who doesn't understand what a cipher is.
Let's take a look at exactly how to use these methods to create a secret message.

How to Make a Classic Cipher
The traditional replacement cipher is one of the most popular because it is completely customizable. This makes it one of the most fun to use, and a super option for kids. The idea behind this simple cipher is that every letter of the alphabet is replaced by another character or symbol.
Where To Start
First, a key is needed. This is simply a decoding chart that shows the value of each letter in the alphabet. To complete this step, simply write out the alphabet and the numbers 0-9 and, just next to them, create a symbol that will be used to represent them. This is where a person can be very imaginative. Will your secret codes be pictures, dot configurations, lines, or different letters? The possibilities are unlimited. Here is an example where the symbol behind each letter will be the secret code used to replace the letter. For this demo, I am intentionally excluding 0-9 but you should include them when you create they key if you want to be able to use numbers without spelling them out.
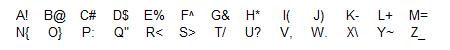
Creating The Message
To create a secret message using a simple cipher, simply replace the letters with the symbols that represent them. For example, if I wanted to create a message that said "I feel great", I would use the symbol just to the right of each letter in my cheat sheet. The resulting message would be "(^%%+&<%!/". It will be much easier to break this code if spaces are added where the words end, so including the code in one continuous string is better for privacy.
How to Break the Replacement Cipher
When you are on the receiving end of the message, you simply refer to your key and translate the symbols back into letters. Then, you have to use your brain to figure out where the word breaks are.
Practice Decoding a Replacement Cipher
Are you ready to break this code? Here is a coded message using the same key from above. Use the key to break the code. The answer is at the bottom of this webpage.
$<}:/*%=}{%~?{$%</*%/!@+%

How to Make a Date Cipher
A date cipher requires the use of a date to break the code. You can determine any number of ways to come up with the date. For example, early in the message you can refer to a historical event that is the hint to the date, the note could contain a date, or you and your decoder could just have previously agreed on a date. Any regular number will actually work with this cipher too, as along as it is a number that can be determined by the person reading the message. For example, you could use pi with this cipher.
Where to Start
Start with the message and the date. Simply write the message out on paper and figure out what you will use as your date. Let's say you want to use the date that Apollo 11 landed on the moon - July 20, 1969. In this case you would include some text on the message that includes "Apollo 11" in it so that the person reading the message can pick up on that date. This hidden message in the note can be as plain or as difficult as you like.
Creating The Message
For our example, let's use "break this secret code" as our message. First, use the date to convert each of the letters into a number based on the date. Our date of July 20, 1969 would be converted to 072069. Next, replace each letter in the secret message with these numbers, repeating the numbers in order. That would transform "break this secret code" into "07206 9072 069072 0690". Finally, use the number to replace the original letter with a new one this many positions away from the original letter in the alphabet. For example, the "b" would move 0 places and still be "b". The "r" would move 7 places and become "y" (7 letters later than "r"). Continue this until you have coded the message. Our coded message would be "bygaq chpu sklrlv cume". For added difficulty you can remove the spaces and make the recipient break the words up or group letters in groups of 5 letters each.
How to Break the Date Cipher
First of all you need the date. Without it this will be tough. Once you have the date, simply figure out the numeric values of the scrambled letters that you see, and count the letters backwards to unscramble the message.
Practice Decoding a Date Cipher
Here is a sample date cipher. See if you can break it. The answer is at the bottom of this webpage.
It's cool how characters in The Matrix can see code as images. I wish I could figure out what in the world "sdifrbbhkjwmplfudae" meant.
How to Make a Keyword Cipher
A keyword cipher is one of the easiest ciphers to use and adjust since it is based on a single keyword. All that is needed to code and decode a message using this method is a single keyword or phrase. The trick is to figure out what that keyword is. Much like the date cipher where the message often contains the date needed to break the code, in a keyword cipher the word that is used to decode the message is often indicated within the message itself. Sometimes this can be fairly simple, while at other times it is quite difficult.
Where to Start
Begin by deciding what the keyword will be. It is a very good idea to have the keyword include at least one letter from the end of the alphabet so that the replacement alphabet will not too closely resemble the original. Once you have the keyword, create a replacement alphabet by replacing "A" with the first letter in your keyword, "B" with the next, and so on. Do not repeat any letter in your keyword. This means that if your keyword is "kitty", you would replace "A" with "K", "B" with "I", "C" with "T", and "D" with "Y". Notice we skipped the second "T" in the word kitty. Next, just continue with the next letter in the alphabet that was not coded and complete the replacement alphabet. Here is an example. Let's use the keyword "geography". The original alphabet and replacement alphabet would be as follows:

Creating the Message
Let's assume that our secret message to be coded is "look out below". In this case, we would simply substitute each letter in the original text with the replacement alphabet letter that is under the original alphabet letter. So, we would replace "L" with "F", "O" with "K", and so on. The fully coded message would read "FKKD KTS EAFKV". As with other codes, it will be more difficult for others to break if you remove the spaces or space the letters out evenly, such as in groups of 3 or 5 letters each.
How to Break the Keyword Cipher
To decode this variation of a secret code, the keyword is needed. Then, you must create the replacement alphabet and back into the original letters.
Practice Decoding a Keyword Cipher
Here is a sample keyword cipher. Let's see if you can figure it out and break the code. The answer is at the bottom of this webpage.
This message is a Mystery - "RCITH EMPPB ESJRR EE OBJK"
Secret Codes Are Simple to Make
With a bit of effort and a willing accomplice, you can easily use these popular secret coding methods to send encrypted messages back and forth and have a lot of fun at the same time.