- HubPages»
- Technology»
- Computers & Software»
- Operating Systems
How To Retrieve Windows XP Administrator Password
You are a network administrator in a small business environment where there's no domain controller or Active Directory in place -- and one of your users (or managing director!) comes running to you one morning asking you to ‘do something immediately' as he has forgotten his Windows XP administrator password and can't log on anymore!
Your job and reputation are at stake - what would you do? One option is to simply refuse the request saying this is a no-way-out situation which can be solved only through re-installing Windows. But you are provided with an option of giving a positive answer through this guide.
Forgetting Windows XP administrator password can be a big nag especially if there's some important data held up in the system which is required on short notice. While there are no definitive guides on how to retrieve or re-set Windows XP administrator password, there are techniques and third party tools available that claim to put you back in control of your system. But before attempting a solution like this, make sure all other arenas are exhausted - perhaps there's another admin user, or try re-starting the system in Safe Mode and login without a password, i.e. the default admin of Windows XP. In the end, if all other measures fail, here's what you can count on: a Linux based free bootable CD that lets you recover from the loss of Windows XP admin password.
Download the bootable disk's image, an ISO file from here. Burn the image on a new CD and set the computer BIOS to boot with CD drive as first boot device. This is more than just a password resetting utility. Since it's a bootable disk, you land outside the installed OS and get complete offline working environment which is not dependent on Windows, and then NTFS and FAT32 file systems can be read as well.
Second, it offers to either change the password to a new one or removing it - for all the users, not just admin ones. Third, it allows unblocking of existing blocked accounts - so if there's a blocked admin already present, one can simply enable it. And lastly, it has got an ‘almost fully functional registry editor' too.
After booting from the CD, the instructions are provided on-screen and are self explanatory. Initially, the hard disk device drivers are to be loaded, once this is done, path of Windows installation folder has to be provided. This is how the programme gets the list of current users. A list of users along with their hex IDs is shown. Select the one that need to be changed, and select password resetting option. Use asterisk to specify a blank password. Press ‘yes' at confirmation prompt. Exit from the operations menu and select the option to write changes to the disk. Once this is done, remove the CD and re-boot the system and don't forget to change the password when back in Windows. Note that num-pad of keyboard might not work in some cases with this Linux CD.
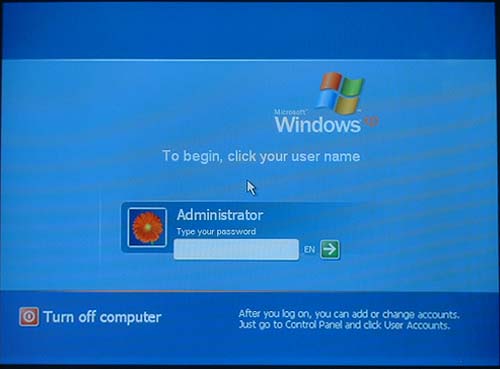
How it works and what can go wrong?
The utility works by accessing the part of registry that is not accessible in normal operation environment - and that's why it is presented as bootable CD. The registry it reads resides at system32\config under Windows directory that contains SAM - Security Account Manager data. This data is susceptible to LM hash weakness, and the tool attempts at altering the registry responsible for managing user authentication.
Doing something that's not standard has its pitfalls nevertheless. The developers warn that at times, there might be some errors like in case when the system was not shutdown properly. In this case, user must re-boot the system and let the disk-check activity complete its work before attempting password re-set.
Secondly, the methodology of updating the registry may not work if user has provided a custom password because its exact jumbled-up form has to be put in exact place, that's why it is recommended to set the new password as blank password instead of re-setting it to a new one.
Another thing to keep in mind is the availability of encrypted files and folders - these won't be retrieved after applying this fix. This happens because in an encrypted file system, the actual password is used as part of encryption algorithm and that is now not accessible to the OS. The utility can be used for standalone PCs only, not for Active Directory passwords, and all the laptops are not supported either.
Countering this mechanism
If for some reason, you believe this mechanism can be a security threat, simply remove the CD/USB from the list of bootable devices and password-protect the BIOS.