- HubPages»
- Technology»
- Computers & Software»
- Computer Software
Really Free Malware Removal Software Programs Overview, Tricks and Scan Setup Instructions
No-cost Command-line Malicious Software Removal Tool
At first I intended to write about one free malware remover - EMSISOFT anti-malware command-line scanner. It is available as a free downloadable archive which is kept always up-to-date with latest malware definitions. Freeware anti-malware are in rising demand right now, and short instructions on how to properly use this free malware remover are needed by lots of victims of computer infections.
But then I thought: who would search for a command-line scanner? I bet most PC users are unaware of black DOS-like looking windows, and even among those who know about command line console, the majority would prefer traditional GUI-based software. In the world of 3D graphics DOS environment is looked upon as a remnant of the past. Command line scanners are mostly used by IT pros or Unix enthusiasts, so I risked creating a hub that would never attract its audience.
Therefore I decided to slightly broaden the theoretical part of free malware removal options, while still concentrating on the EMSISOFT command line scanner.
What is Malware
As time goes by and we move in the next decennary of the XXIst century, the pests that aim attacking our computers never stop mutating. Their nature and activity patterns change, and so does the approach to naming the threats. In addition to computer viruses which appeared in the last millennium, a number of new types of PC infections appeared. Consider this list:
- adware;
- spyware;
- threatware;
- badware;
- rogueware;
- scam extortion.
Not speaking about the sub-divisions of the malicious programs, it is clearly seen that almost every PC user simply gets confused. How to know what type of infection bypassed my antivirus protection?
That's why it is common to unite the whole range of threats into a single term: malware.
So what is malware?
In short, it's all included in the list above, plus keyloggers, phishing, process injection, browser hijacks, etc. These are most widely known types of malware. Malware is something that should never be allowed to penetrate into a PC because no-one knows what purpose it prosecutes. Malware can display innocent pop-ups, but also steal identity and transmit sensitive private data to remote servers for later use by web criminals. Malware is used for achieving all kinds of goals, none of which you wish to be achieved.
There's one more question often asked by inquisitive PC users:
What is the difference between malware and spyware?
Spyware is limited to drawing money out of the victim's finances. Opposite to viruses which may use infected computers silently for certain activity (like sending spam or redirecting traffic), spyware is created to make money. It may deliver ads (forced to desktop or browser), collect information about surfing habits and transmit it to companies engaged in Internet marketing, keep a log of keyboard activity, etc. Generally speaking, virus and spyware together constitute the most widely known type of malware. A new spyware function is distribution of scams - rogue security software. This is when people are fooled into buying fake antivirus or antispyware porgram.
Malware is a broader term to refer to spyware, backdoors, trojan viruses, worms, etc. However, in most cases anti-spyware programs deal with all those types of malware in addition to common spyware infections. So if you have a solid antispyware protection this most likely means your computer is secured against not only spyware, but also other parasites. It's just been common to use the "antispyware" term for several years, and only recently it started yielding to a broader "anti malware" software which cover a wide range of PC threats. So basically you can't tell what particular anti malware or anti spyware program covers more types of malware unless you read through specs. But even detailed information doesn't give the full overview, that's why the difference between malware and spyware is many cases is little or non-existent.
Free Malware Removal
Removing malware consists of the following steps:
- identifying the presense of infections in the system;
- locating the exact places where parts of the malware reside;
- finding a proper tool for removing malware;
- creating conditions for removing malicious software;
- completing the malware cleaning process.
So, free malware removers are not the main concern - it's far more important to find out what needs to be deleted from the system. When you have information about the types of malware and their exact locations, it's much easier to find proper free malware removing software.
A free malware removal software can be:
- a single executable file (like McAfee stinger); major PC security software vendors offer such tools whenever a certain type of malware takes the Web by storm. For example, such malware removers were released when Nimda worm infected millions of computers worldwide.
- a batch file executed in the command line console;
- a feature-limited version of commercial anti-malware tools. Sometimes trials allow to remove malware for an evaluation period of two weeks or a month.
- Free online virus scan. Such services are provided by industry-leading anti-malware software manufacturers, as well as IT security-related websited which sometimes combine the power of several online virus scanners. Usually companies provide free online malware scan services as a way to attract new customers.
Advantages of a Command-line Anti-Malware Removal Software
Somebody would inevitably ask what advantages a plain-looking black window may have over convenient, pleasant-looking unfolding menus with keyboard shortcuts and mouse support? And that's not to mention the need to type in commands with switches, where every little error results in necessity to start typing all from scratch.
However, let's look at strong points of free malware removers anyway.
- They never expire, never stop removing malware, never require subscription renewal;
- Being command console applications, anti-malware tools use very little system resources, unlike desktop software with fancy graphics and transparency effects;
- They do not require installation and can be removed simply by deleting a folder;
- They remove malware even in Safe Mode and when desktop programs are disabled by smart viruses. In fact, command-line scanners perform best in Safe Mode.
- They are easy to automate by creating simple .bat files. Double-click one to update definitions, initiate a scan and remove detected malware;
- They are easy to transfer to portable devices.
I'd add that command-line based free malware removal programs help users to discover the hidden part of the system where certain tasks are performed faster than in GUI environment.
EMSISOFT a-squared
A-squared offers a cool command-line scanner that saved lots of users in frustration after their computers underwent malware attacks.
Diverse scams circulating on the Web are smart enough to get onto PC's protected by popular security software. Unfortunately, resident monitoring is often helpless when trojans bring SmitFraud infections with them. And once pop-ups appear on the desktop screaming about spyware infections detected, users feel at loss. How to remove malware?
There are essentially two ways to recover the PC:
- Burn a bootable CD with antivirus and antispyware, providing latest signature files.
- Run a command-line scanner which works both in Normal and Safe Mode.
a-squared anti-malware is exactly of this type of scanners. The manufacturer offers it for download with no strings attached (no need to enter email, confirm, subscribe to newsletter, etc.), conveniently storing the archived file with latest anti malware definitions.
a-squared makes removing malware a no sweat task. Just a few command switches are needed to instruct the scanner:
- to scan memory;
- to use heuristics;
- to clean the infected files;
- to remove those files when cleaning fails.
It is worth noting that a-squared by EMSISOFT is better at removing malware than most antivirus tools because it incorporates the detection mechanism not limited to common virus infections. Its scanning engine is designed to fight a broader range of types of malware, that's why it may perform at a higher efficiency rate than already installed desktop security software.
In particular, free malware remover from a-squared is capable of fighting:
- spyware;
- adware;
- trojans;
- worms;
- keyloggers;
- rootkits;
- dialers.
a-squared malware remover is capable of scanning Alternate Data Streams (ADS) on NTFS file systems and archives.
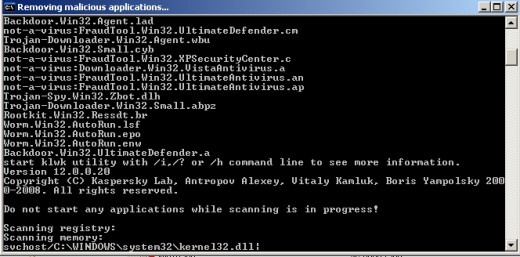
A typical command to instruct a-squared to start scan and deletion process looks like on the screenshot below.
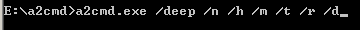
The legend is iterpreted the following way:
E:\a2cmd\ shows the location of a-squared program files. In my case Windows is installed on E:\ drive, therefore I unpacked the files to the root.
/deep is one of the three scanning modes: quick, smart, deep. For an infected computer, I suggest using the deep mode to maximize the chances of successful malware deletion.
/n instructs the malware remover to scan the NTFS file system for Alternate Data Streams.
/h turns on the heuristics scan mode. It is used to identify unknown malware by suspicious behavior patterns.
/m stands for "memory scanning". I see no reason why it shouldn't be used.
/t scans for malware traces.
/r reveals Riskware - not yet defined occurrences or types of malware, yet suspicious in the digital eyes of the a-squared scanning engine.
/d is the most expected command. Every owner of a malware-infected computer would want this ON because it stands for MALWARE REMOVAL ;)
Below is the screenshot to show what happens when ENTER is pressed with the above described command parameters. The figure [404] in square brackets shows the number of scanned files.
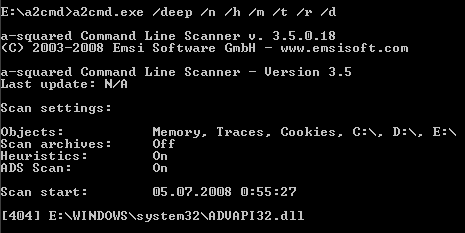
Some more words about a-squared free antimalware
EMSISOFT free malware remover is a perfect tool for on-demand anti-malware scans. It needs no installation, doesn't add any files into Windows system directories, and makes no changes to the registry. About 26 megabytes of space is all that this malware remover needs.
a-squared designed its command-line scanner to remove malware an easy way with no special knowledge needed.
This malware remover is capable of deleting a number of rogue security programs like XP antivirus, and other types of malware.
P.S. If you find this information useful, please feel free to share it with your friends and those in need of removing malware.
Kaspersky(R) Virus Removal Tools
Kaspersky Labs released a command-line tool to remove a number of malware infections. It is a 120KB in size so even those with dial-up connection can use it.
The .com file can be executed straight from within Windows Explorer - just double-click on the tool to start scanning the whole system.
Kaspersky tool supports the following switches:
- /s[n] - to force scanning of hard drives.
- /n - to force scanning of mapped network drives.
- /path <path to scan> - to force scanning specified path.
- /rd - to force restoring registry values.
- /y - do not request key press (to automate the scan).
- /nr - do not reboot system automatically in any cases.
There are five return codes that explain the results of the scan.
- 0 - nothing to clean (good!)
- 1 - system was infected.
- 2 - to finalize removal of infection you should reboot system.
- 3 - to finalize removal of infection you should reboot system and start this program the second time.
- 4 - program error.
If you know what type of virus hit your Windows station and all other remedies didn't work, look through the list of supported infections. If yours is listed among others, download Kaspersky's removal tool.
www.kaspersky.com/virus-removal-tools
Kaspersky Command-line Scanner
MBAM v1.50
- Malwarebyte's v1.50 Anti-Malware
Malwarebyte's can detect and remove malware that even the most well known anti-virus and anti-malware applications fail to detect.
Malware bytes antimalware
Malware bytes is increasing in popularity at a fast pace. This little program with minimalistic interface has saved countless hours of struggle for victims of Virtumonde trojan virus. Since the release of version 1.31 I noticed that visitors of my Virtumonde hub got to praise this malware removal tool for its efficacy in fighting the dread presence of Virtumonde variants. The number of positive comments is so impressive that I believe I can recommend this program to all PC owners who can't kick the malware out of their computers.
Malware bytes anti malware features intuitive interface that's easy to use no matter what your PC experience is. There are two types of scan to choose from: quick and full. If you run Malwarebytes for the first time, do a full scan to make sure there's not a single dark corner in your system where Malwarebytes hasn't inspected every byte of the data. Be sure to update the program with latest definitions before scanning as you want it to have the fresh footprints of digital parasites.
Malwarebyte's in its basic edition is not just a scanner (unlike many other similar products on the market) but a fully-functional free malware remover. It really removes what it finds, and it finds a lot of types of malware!
Malwarebyte's peacefully resides in the system with antivirus software installed, so normally there's no need to worry about compatibility problems.
Malwarebyte's Anti-malware

For those who are afraid of command-line scanners :-)
- EMSISOFT anti-malware v5.1 Just Released!
Remove Trojans, Dialers, Keyloggers, Worms, Spyware. Prevent future infections and stay protected against 1.2 million threats!