How To Remove WinFixer

What is WinFixer
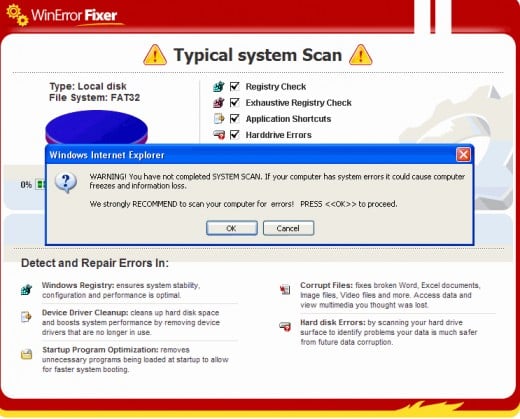
Winfixer is a type of rogue security program that is mostly being spread by trojans. While certain security assessment labs consider WinFixer to be merely a potentially unwanted program, it acts in a very annoying way by displaying misleading pop-ups, ads, and urging PC users to pay for the license key.
Winfixer is distributed as a "free version" with scan-only function. That is, it displays a number of severe risks in a particular system, and alarms the user into paying for a "full version" to stop reminders.
The detected system problems are of questionnable nature. Mostly suspicious or infected items are completely safe Microsoft Windows system files. WinFixer put fake descriptions to those files, trying to scare the user into purchasing a full-featured version of the software to allow the removal of those false and erroneous detections.
Winfixer features same interface as a number of other rogue security programs which clearly indicates it is a fake product made by same team of web scammers.
NOTE: Although the images presented below show WinFixer 2005, there exist versions of 2006 and probably other years. Please don't be confused with "outdated" releases since this malware is still present on the Web, and surfers fall victims to WinFixer, paying for fake software with no chance to get refunds.
WinFixer Advertisement
How To Get Infected with WinFixer
Unlike the relatively harmless nature of WinFixer, its distribution is carrued through nastiest breeches ever used by web criminals.
Thus, WinFixer is known to get installed without user consent. No banner clicks are needed because this malware exploits Internet Explorer vulnerabilties.
But this is not the only way it gets spread via Internet-connected PC's. In addition to brutal attacks through IE, WinFixer is promoted via social networks and bookmarking sites. It seems that a team of aggressive posters, equipped with bot programs and spam tools, are engaged into pushing WinFixer to unsuspicious surfers.
WinFixer is not tight down to any particular Second Level Domain Name (mainly in .com zone) and its web presence is established through a chain of related websites. Besides, it is spread by popular software download resources (softlow, fbmsoftware, etc being examples of such).
The executable installation file of WinFixer may be of less than 100 KB in size, which should make any more or less savvy PC user suspicious enough not to double click on it. Every legitimate program meant to perform some system maintenance tasks is at least several Megabytes in size (this is due to antivirus or antispyware signature databases, patterns of registry scanning, graphics, animation parts, etc.)

How to Remove Winfixer and its Traces Manually
It is possible to remove WinFixer manually. Upon successful installation, this fake program puts its files into the following directories:
- Windows (or WINNT if you're using Windows NT/2000)
- Windows/System32 or WINNT/System32
- Program Files (where it creates a subfolder Winfixer 2005)
- System32/Drivers
- Documents and Settings\All Users\Start menu\Programs\Winfixer 2005
- Documents and Settings\(username)\Local Settings\Temp
Search your hard drive for the following files and remove them using SHIFT+DEL key combination (this bypasses the Recycle Bin).
- WinFixerScannerInstall.exe
- WinFixer2005ScannerSetup.exe
- mfc71.dll
- dfe1.exe
- atl71.dll
- df_u42.sys
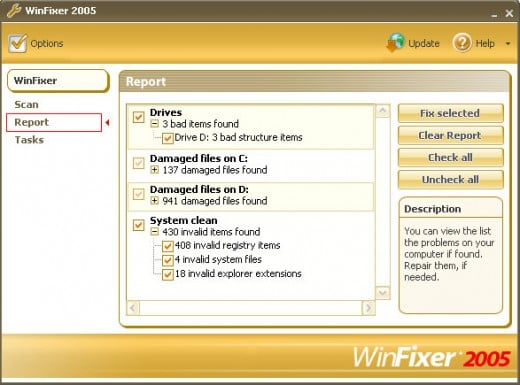
WinFixer Report
Tools and Software to Remove WinFixer
However, manual removal of WinFixer may turn to be quite a complicated task. This malware installs and creates well over a hundred of files and registry entries. Not every computer-savvy user can afford to spend that much time finding the remnants of WinFixer and its associated entries.
Furthermore, files are of different levels of danger to Windows system, some of them may require rather sophisticated approach to remove from the hard drive.
That is why it is recommended not to reinvent the wheel and go the easier route which promises a 100% positive result.
If you're comfortable with command-line scanners (like TrendMicro Sysclean or a-squared scanner), you may use this malware removal guide.
If you're afraid of black windows and the need to type in special commands, or simply prefer something with graphics and mouse support, then you may use HiJackThis (again, created by TrendMicro team and distributed at no cost). This non-installable program allows to run a system scan and identify the files and registry entries WinFixer consists of. However, you definitely need a solid level of competence to interpret the scan results properly. HiJackThis is very popular because of its detection power and removal capabilities, but unless you really know what you're doing, I advise that you consult someone savvy. I've seen quite a lot miserable PC users who used this powerful utility without proper guidance and preparation which ended in non-bootable Windows.
You can download HiJackThis here, but make sure you know what to do with it. I personally like this program a lot.
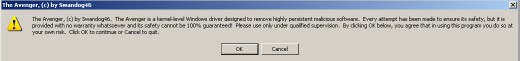
Another tiny tool to remove WinFixer is called Avenger. It works on Windows kernel level and requires pre-made script to execute. This script can be done manually, using the information provided by some scanning program (say, HiJackThis, which was mentioned earlier in this guide).
WARNING 1: Avenger operates on system kernel level (the lowest possible in Windows, and most critical part of the system), so wrong instructions may end in complete system failure. You've been warned, so use it at your own risk. No guarantees are provided whatsoever, and in case of removing anything else instead of WinFixer infection, there's no-one to blame for the unexpected ending.
WARNING 2: WinFixer is capable of creating random filenames, and total number of registry entries / installed files may be different depending on infection case, Windows version, etc. Therefore there's no a "universal" script to use with Avenger to remove winfixer infection. Most likely your particular case needs a specific set of commands to process.
Remove WinFixer Automatically
I'm a big fan of free tools, some of which are listed above. There is, however, a certain risk involved in using software specifically developed to target a particular range of threats. Programmers certainly know what they create and how to use it for best results, but many PC users may find it time-consuming to learn how to operate these tools properly. In some cases, when critical computers are infected and it is not possible to backup important data, software from 3d party manufacturers may suit your needs better. Some of them provide fully functional trials, or versions with scan/removal options, but with advanced features inactive.
NOTE: Every program listed below is safe to use, contains no adware/spyware or malicious code embedded, and has been awarded with top Web magazines. Download options are provided directly from software manufacturers, with full support and warranties pertained to each program.

Max Spyware Detector: 100% WinFixer Removal
- MAX Secure Spyware Detector
A complete solution for individuals, professionals and home users to scan, detect and delete spyware to get rid of the malware, adware popup, Keylogger and trojans instantly. Smart Scan Technology and Max Shields keep you protected all the time.


EMSI Software a-squared anti-malware
- a-squared anti-malware v5.1
a-squared is a Malware scanner and remover of the latest generation which is specialized in Trojans, Dialers and Spyware. Background guard and Intrusion Detection System (IDS). Detects MORE THAN 700,000 types of malware. Available in 11 languages!
a-squared anti-malware screenshot
After Removing WinFixer
I hope you have successfully removed the Winfixer and its variants. Hopefully you have installed an antispyware protection as well to eliminante the infection options in the future.
Still, please follow these simple steps to help your antispyware software protect you at best rate possible.
- Consider switching from Internet Explorer to some other browser (e.g. Mozilla FireFox or Opera). Because of IE popularity and native integration in Windows, this browser is the first to be attacked by all types of malware. Avoid the unnecessary troubles.
- Create a new habit: do antispyware and antivirus scans on a regular basis (e.g. once in a week). Instruct your security software to run scheduled scans (just about every decent program has this feature active by default, though free software may miss sheduling). Alternatively, you can create a Windows scheduled task to launch appropriate software at specified time/date.
- Stick to safe browsing. Avoid visiting websites which are potentially harmful to your computer. When in doubt, check Google or other search engine for reviews or lists of dangerous websites.
- Finally, make sure your PC security program is kept updated to latest definitions. Most antispyware and antivirus programs do it automatically. Some of them (very rare to come across these days, though) go still further and allow manual updates for offline computers. MAX Secure Spyware Detector is an example of such software.
Finally, if you found this guide helpful, please spread the word. You may bookmark it by using Share It button below, or your browser toolbar. Take part in fighting WinFixer!