The Best Computer Virus Protection for the Home User
Cyber attacks and malicious software that we knew a decade ago are a bit of a joke today because of what we now face. In what has become the epitome of cybercrime, perpetrators have upped their game by getting faster, crafty and take advantage of embarrassing user ignorance. This calls for a smarter computer virus protection strategies
To compound, this is the increasing installation of domestic digital equipment such as smart TVs, routers, satellite receivers, spy cams etc, which cybercriminals have embraced with relish.
Online computer crimes and malware are thus becoming costly to governments, corporations and home users alike while increasingly getting harder to detect and protect against with the use of only the basic security software.
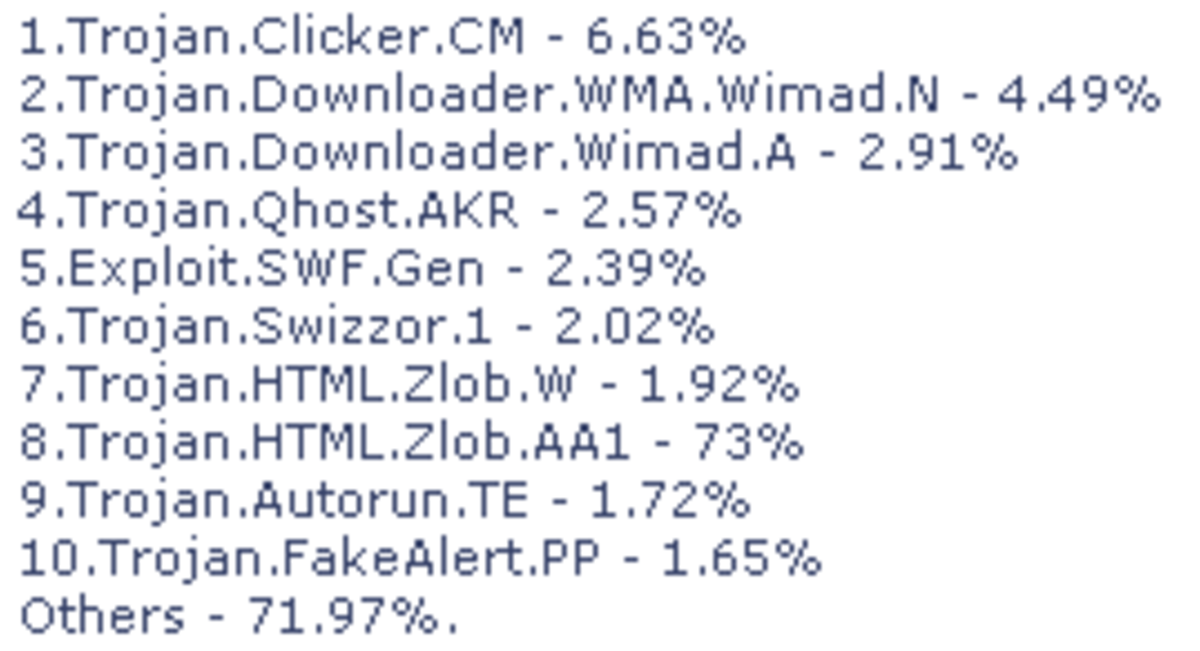
According to Kaspersky, there was an upward trend of targeted computer crimes towards government institutions and private firms in 2014 via Trojans. This was championed by an espionage campaign called Careto, which hacked into communication networks worldwide to collect all kinds of data.
It has become more than necessary for every user to know that no threat to the computer is too small and no internet security software is exhaustive enough to deliver the ultimate firewall from remote attacks.
For those that are already proactive, well and good, otherwise, start by making a few changes to the manner in which you interact with your computer.
Below is a brief look at 11 proactive practices to protect you and your digital equipment at home.
1. Educate Yourself About Cyber Security
This cannot be overemphasized!
Stay on top of the game in order to keep online and offline computer crimes at bay in order to implement the best computer virus protection. There is no better way of doing this than equipping yourself with relevant cybersecurity news regarding most forms of attacks and malware.
Read wide, and keep reading…
Just to jog your memory for example,
- do you know over 300 million viruses were released in 2014 alone?
- do you know the old belief that Mac computers don’t get infected is a fallacy?
- do you know no security software is 100% perfect?
- Have you implemented 2 Factor Authentication?
Your ability to stay informed about changing trends and statistics will help you make informed decisions.
Suffice to write, educate yourself,
- about forms of cybercrime
- how to safely protect your system at the local level
A Trojan or Trojan horse is a seemingly harmless program or file which you install or run on your computer after you have been duped by a hacker. Following installation or use, a Trojan will activate a backdoor exploit tool through which a hacker can monitor your computer remotely.A Trojan usually attaches itself to your favorite computer software or mobile phone app that has been cracked, or it may come with mail attachments and other file types. It may also get access to your computer when
A very fundamental fact you need to know is that most malware will involve some kind of remote installation of code using a Trojan.
Most Trojans will get access to your computer through,
- hacked software installations
- mail attachments
- infected links
The remote hacker will successfully install a Trojan onto your computer depending on how fertile the ground is on your digital equipment.
Fertile ground may mean you,
- running old software in your computer
- using pirated software
- having a merry clicking habit
- installing random software without much thought
Now that you know the remote access strategy, you can work on blocking likely loopholes that can be used by hackers.
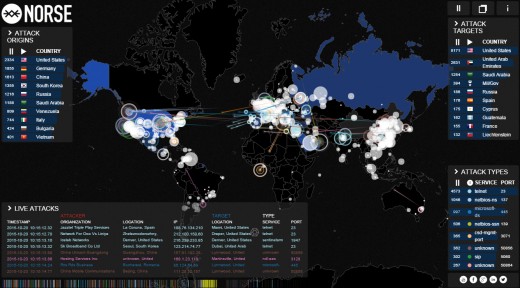
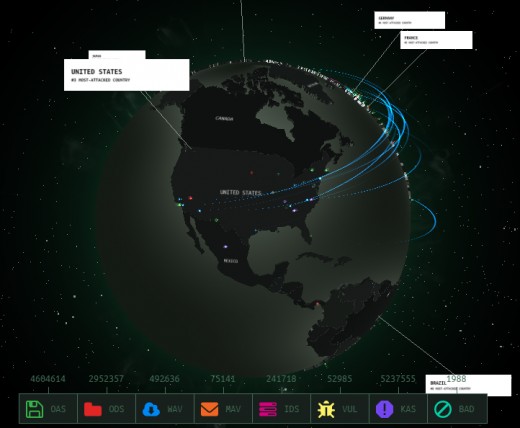
You may actually want to visit the site below to get an insight into real-time cyber security activity:
Realtime cyber attacks from Norse and Kaspersky
2. Install and Update Trusted Security Software
Trusted anti-virus and anti-malware software should always be the preferred course of defense when fighting off malware attacks. Get a good antivirus and antimalware app to start protecting your devices.
NOTE: As a rule of thumb, never browse the internet without updated security software. Your computer will be vulnerable to threats instantly it goes online. The next attack could just turn your beautiful system into the next botnet!
Most antivirus packages are designed to identify malicious files before they settle on your computer.
Usually, standard security software should offer the following protection:
- Real-time protection against viruses, spyware, Trojans, worms, adware, ransomware
- Password protection against snooping
- Web protection from harmful sites, downloads and key-loggers
- Identity protection
- Malicious URL blocking
- Phishing detection
- Privacy protection
- Email scan to detect harmful attachments
- Anti-spam protection
- Protection against rootkits
- Heuristics scanning of unknown but suspected threats
What antivirus you choose to run on your device is a matter of choice, but care must be taken not to trust software solution whose performance has not been proven.
You can start by seeking recommendations from friends and experts alike, whose suggestions should help you get started.
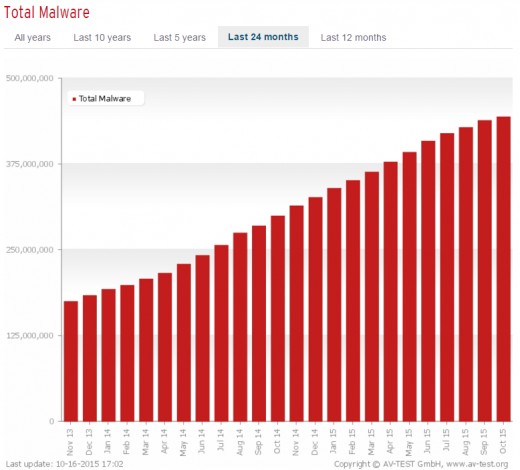
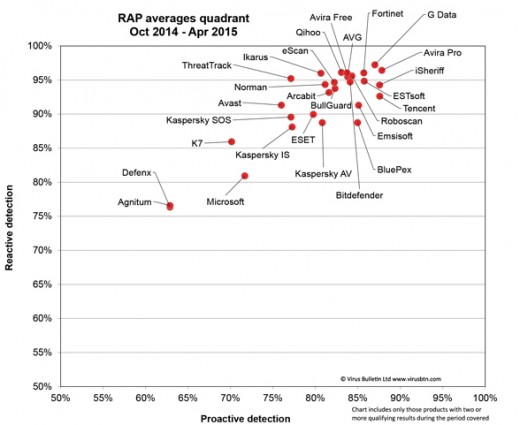
Two very important websites to visit are AV-test and Virus bulletin where arrays of antivirus tests are done and displayed online.
Besides your security package, make sure to download and install one functional antimalware package.
A good starting point for most users is Malwarebytes which is famed for effectively dealing with emerging multi-faced malware and those delivered by zero-day exploits.
Finally, ensure you are running the latest definition updates at all times. By default, most security software will install daily definition updates automatically, but you may want to check this out periodically just to be sure.
3. Only Install and Update Legitimate Software
We live in an era where pirated software seems to be the way to go, but at what cost? According to Arxan’s State of Application Security Report 2015, there was 22% overall increase in download and use of pirated digital media between 2014 - 2015, and that corporations spent astronomical $500 billion to counter the costs and effects of malware associated with pirated software.
In the research, over 30,000 of mobile apps and desktop software titles were pirated between 2012 and 2015, with Android mobile games and desktop computer software the biggest losers!
At the local level, the effects of pirated software, especially those laden with patches and keygens can be manifested in malware infested computer.
If for some reasons your computer is never stable, always showing popups and your security software is always at war with infected files and installations, then you may be having serious problems with one or two installations.
Only run legitimate software and when prompted, update it to the very latest version.
If you are really, really security conscious, stay away from old software and operating systems in particular. As of now, you should not be running Windows XP or Vista anywhere on your computers.
As a rule of thumb,
- run software that is u to date
- update your Windows, Mac, Android, IOS operating systems
- don’t install software and apps from untrusted sources
- keygens and patches will always install Trojans and other malware
- don’t give away confidential information to online strangers
- stay away from pirated software
- don’t install pirated security software with keygens and patches!
Finally, listen to your security software when it spots malware, and let it do its stuff! The interaction you have with installed security software will make or break the computer. A working and updated software is good enough only if allowed to do its work well.
4. Use Strong and Secure Passwords
It is a fact that use of secure passwords is the first line of defense when it comes to protecting mobiles, desktops, apps and logins from hackers.
The rules on password strength don't really change by getting softer. Stronger passwords are now recommended more than ever.
A secure password should not be
- used across accounts
- written on papers or anywhere carelessly
- stored in your phone if the phone is not password protected
- dictionary words even if spelled backwards
- used in series i.e. abc, 123
- character substitutions i.e. P@$$W0RD
- pet, child, hubby or recognized name by people around you
- shared online for whatever reasons
- searchable on the browser
- be stored on the browser
A good password should have at least a number, (e.g 7) a special character, (e.g. <) a capital letter, (e.g H) at least 8 letters i.g. 7<>XstnR
If you feel incapable of storing your mounting number of passwords, download and install password management software like LastPass and Roboform.
5. Implement 2 Step Verification
2 Step Verification or 2 Factor Authentication gives added layer of security in a world where traditional passwords are getting compromised by the day.
It works just like a token which you have physically with you and is next to impossible for remote hackers to access.
Other forms of 2-factor authentication exist but the most common in the digital world is tied down to your mobile phone. Every time you log-in to your account in a new device, a special code will be sent to you via SMS message which must be typed into the login page.
The remote user will not be able to receive this SMS message since he or she does not have access to your mobile.
While this type of authentication seems reliant enough, it can also get compromised especially if you choose to create backup codes and store them carelessly. Someone with access to your account password can also make use of these codes to break into your account.
Further still, if you tick ‘Don’t ask for codes again on this computer’ especially when in a public computer your account will remain open for hacking. Never tick that option when using a computer which does not belong to you.
Ultimately, combined use of strong passwords and 2 Step Verification will avail you the best possible protection, at least for now.
2 Factor Verification is supported by most online services like Gmail, Outlook, Yahoo, Facebook e.t.c.
But now that passwords are getting increasingly compromised for one reason or another, the 2 Step Verification or 2 Factor authentication implementation has been thrown in as added firewall to boost your overall security.
Have you implemented 2 Factor Authentication?
6. Watch the Apps You Install
For one reason or another, there are loads of free apps in stores belonging to Apple, Google and Microsoft, which apps somehow, are used without much thought.
As you are probably aware, free ‘things’ online are not necessarily free, with developers and proprietors of these apps using them to market themselves or/and install malware.
Every so often you are tempted to install apps, especially in Android devices, you probably do not read the Terms and Conditions that accompany app installation. These apps actually alert you that personal data and information may be accessed, but because you are somehow in a hurry and don’t usually read stuff, you happily click away. Hackers will then steal your personal details and sell them to the highest bidder.
Upon installation, some of these apps will bombard you with ads and annoying redirects.
To be on the safe side:
- always read the Terms and Conditions before app installation
- do not share your personal data with any one
- watch every app you install, comprehend what it does and what questions it asks
- check out the integrity of apps and related sites before installing them
- make a habit to review installed apps, and uninstall what you never use
7. Install Ad Blockers or Turn Off Javascript
They may appear innocent most of the time, which actually is true, but ads have become means through which marketers and publishers collect data from internet users. The run towards ads has been the feasible one for marketers since everything is being closed off by security software and browsers.
Ad publishers employ cookies and once allowed to run, are capable of anything beyond basic online behavior. Cybercriminal however, will make use of loopholes in ads to install malware.
Since most ads use Adobe Flash embedded content and yet Flash as we know has always been susceptible to arrays of compromise, cybercriminals will always find a way to trigger or install malware on your computer through them
According to Edwin Snowden, in an interview with Intercept, "Everyone should be running ad block software, if only from a safety perspective…”
Of course, ads are not bad in themselves because many content publishers out there depend on them to raise money, and they surely deserve returns for work well done. For this reason, you may want to consider Ad Blockers that whitelists genuine against creepy ads.
Besides Ad Blockers, you want to have a go at Javascript, but at a cost of course. Disabling Javascript will mess up the operations of plenty of software i.e Google Docs, YouTube, but again will make life better by disabling all unnecessary scripts, ads included.
Disabling Javascript even speeds up browsing!
8. Assess Your Online Presence
The dawn of social media was life changing for internet users since it simplified communication between family and friends hailing in different corners of the world.
Right from the innocent days of MySpace and chatrooms, to present day Instagram and Snapchat, most users have become dependent on social media to help them pass information across. In so doing, we have gradually forgotten the difference between what is private and what is not.
When Edward Snowden first raised alarm bells in regards to governments snooping of personal data, there was the usual trepidation about what should be done and undone in regards to digital privacy.
Online digital privacy has become so complex that some users don’t really understand who between government and marketers is in charge, or who is to blame for misuse of their personal data.
Even closer to home, be aware that your online activity is being watched by the local network administrator (if there is one), the Internet Service Provider (ISP) – usually the cellular network provider, and of course, a geeky neighbor (if there is one around you).
On the other hand, users don’t realize they are fueling the situation by publishing and sharing personal data on social media platforms. To some extent, users are giving up and believing that digital privacy battle is a lost cause.
Ultimately, the user has become the willing accomplice in abetting cybercrimes and spreading malicious software.
A simple illustration of the dilemma users face is explained by the Guardian and Jsoeph Turow e.t.c
Besides Ad Blockers, you want to have a go at Javascript, but at a cost of course. Disabling Javascript will mess up the operations of plenty of software i.e Google Docs, YouTube, but again will make life better by disabling all unnecessary scripts, ads included.
Disabling Javascript even speeds up browsing!
9. Implement a Trusted VPN Solution
In a lay man’s language, Virtual Private Network (VPN) is a kind of network implementation that provides secure online activity for a subscriber.
When you purchase and install a VPN solution, your activities online are disguised by the service provider to ensure you remain discreet.
VPNs basically disguise your computer IP address and geolocation at all times and this will leave the remote hacker at a loss about your exact whereabouts.
A VPN service will protect you even when connected to insecure Wi-Fi hotspots, ensuring you remain anonymous. Public Wi-Fi’s are popular for cyber criminals who prowl for insecure computers where they can steal sensitive data through wireless sniffers.
Here are just some of the popular VPNs:
- Cyberghost
- Private Internet Access
- IP Vanish
- Pure VPN
- HideMyAss
- Nord VPN
- TorGuard VPN
The above believe that marketers are to blame for driving users into divulging information even when the know should not. This in the end, avail hackers part of data they have been seeking for years.
Despite the rather sobering reality, we can still go out of our way to make online life better than it actually is:
- watch and assess the apps, mails on social media closely
- watch out for Like-jacking spam: so, don’t click on strange links
- don’t over share: sharing much is stupid, sharing less is wiser, sharing too little is brilliant
- watch out for social spam: especially enticing video links, friends e.t.c.
- read before signing up for services using other services e.g. signing up for one service using your Facebook account details
- remember that once you post info online, it is no longer private
- delete accounts you no longer use
- make websites you visit use the SSL security protocol
- watch out for link-jacking : don’t just click, check them out
- read Terms of use
- don’t open mails from strangers
- avoid online multitasking: a spammy tab may be at remotely
- watch out for those re directs
- watch out on public Wi-Fi’s: avoid auto connecting, use public profile
- use secure websites: they should have the Lock icon for encrypted or verified address
- also ensure the web address starts with https:// with the letter S for secure socket layer
- use TOR if know how if you are comfortable with it
- use a private browsing: your surf history will not be stored
10. Backup Your Data Regularly
Data is the very reason you own a computer, and so is the main reason you will shed tears when your laptop fails with everything in it.
It is important to know you are not the only one who knows this fact: the remote guy knows it and will want to teach you a lesson especially if he found out you value your data so much.
Many solutions exist about how best to back up your data: Go with what suits you most but remember to also protect your computer from petty thieves. If you opt for local backup, make sure your storage is quite secure, otherwise you may want to entrust your data with cloud services.
11. Use Your Computer Alone!
It may not be much, but using a laptop alone can save you from a lot of trouble most of the time.
Just a few reasons why your laptop is safer only with you:
- It is 80% safer from theft
- You will be safe from a snooping friend
And as added layer of security make sure your laptop is password protected, even when someone turns it on from Sleep and Hibernation.
Make sure to also set up a Screen Saver which requires a password on resume. Set the waiting time to a minute.
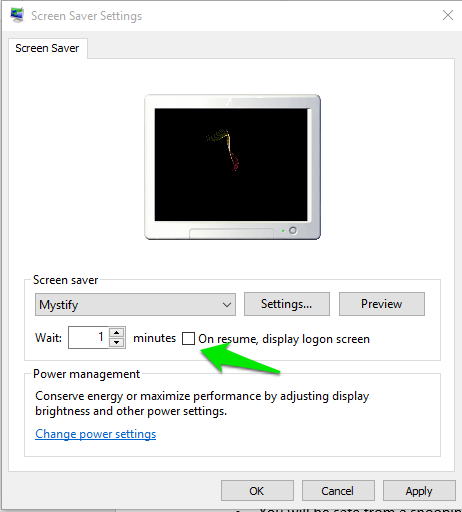
Do you share your computer with sensitive computer with everyone?
A Final Note
Suffice to mention, not every solution above will work to the dot, but again, you are better off implementing them than sitting back and waiting for disaster to strike. Try them and you will surely notice what works and what does not. It is a learning process.
© 2015 Alfred Amuno