The Internet Bentham’s Panopticon on Steroids
Figure 1
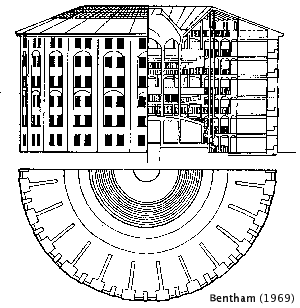
In 1791, the British Philosopher and Social Reformer Jeremy Bentham, in a bid for a contact with the British government, introduced a radical new prison design called the Panopticon (Figure 1). He believed the layout would improve the effectiveness of prisons by maximizing security with minimal staff, while maintaining a level of humanity for the inmates. His design was simple; the facility consisted of two structures. The outer building contained the prison cells. Each cell had an exterior window and a gated door. This setup allowed the natural light to illuminate the inmates’ living quarters. The second building was a tower at the center of the facility, which housed the guards (Bentham referred them as inspectors). The design effectively kept the inmates under the constant watchful gaze of the guards. Blinds concealed the guards’ station so the prisoners could not tell if they were being observed or not. “The essence of it consists, then, in the centrality of the inspector's situation, combined with the well-known and most effectual contrivances for seeing without being seen.” (Bentham)
The central feature in the design was the guards were now able to maintain surveillance over a multitude of inmates, yet the inmates could not tell if someone was there or not. It allowed the staff to react immediately to any misconduct and the perception of being constantly observed by the guards served as an incentive for prisoners to follow the rules. Bentham also believed this design would work for other institutions. “AFTER applying the inspection principle first to prisons, and through mad-houses bringing it down to hospitals, will the parental feeling endure my applying it at last to schools?” (Bentham) He theorized that the system of constant observation could be utilized to exercise control in facilities that services multiple clients.
In 1979, the French philosopher, Michel Foucault, looked at Bentham’s plans and saw something different. Foucault say a concept, “the Panopticon must not be understood as a dream building: it is the diagram of a mechanism of power reduced to its ideal form; its functioning, abstract from any obstacle, resistance or friction, must be represented as a pure architectural and optical system: it is in fact a figure of political technology that may and must be detached from any particular use.” (Foucault Discipline & Punish Page 205) Foucault theorized that this principle of being under constant surveillance is instrumental in maintaining authority and exerting power. To Foucault, Bentham had, “invented a technology of power designed to solve the problem of surveillance.” (Foucault Power/Knowledge page 148) Like Bentham, he could see the exercise of this principle applied in institutions beyond the prison system. However, the available technology when Foucault and Bentham were writing placed limits on the amount of inspection a society as a whole faced.
At Work
Today the internet takes this notion of continuous observation to the extreme. The book, The Tyranny of E-Mail: The Four-Thousand-Year Journey to Your Inbox, by John Freeman, describes the extent surveillance exists on the internet.
“With all these threats to privacy, the message is clear: “You have zero privacy,” Scot McNealy, CEO of Sun Microsystems, once said about life on the Internet. “Get over it.” Web sites you visit send tracking “cookies” to your browser, tiny parcels of text that go back and forth between a server and a client like your browser, allowing the Web site to store information about your preferences and the Web sites you have visited. Retailers mine your computer any time you purchase something online—and then turn around and sell it to the highest bidder. And it doesn’t stop there. E-mail, which, it’s important to remember, is stored on servers most of us don’t own, is constantly monitored. Especially at Work.” (Freeman Page 125)
With the internet, it is possible to keep a person under observation at work, play, or rest.
In the business world every E-mail, internet search, or internet/intranet transaction by employees can be tracked and recorded. These designed actions are for solid business reasoning; employers are paying wages for production and they have the right to ensure that employees are not doing anything that would place the organization at risk. That is why many companies have a written internet and E-mail acceptable use polices in place. However even legitimate actions can be taken to the extreme. In addition to E-mail and internet monitoring, many companies are now keeping the electronic gaze upon their employees all day long. They can track when an employee enters the facility, how long it takes them to log on to the system, the number of keystrokes performed in a day, and the time between them logging off and leaving the facility. Being under the constant electronic gaze at work has changed the dynamics of the environment.
For many employees the gaze has moved beyond the physical work location and has infiltrated their private time. With hand-held devices, at home and mobile high speed internet access, and remote business E-mail access the work place has now become 24/7, even though the pay is still based on an 8-hour day. To be considered a team player, instant responses to all inquiries is the expectation. It is not unusual for employees to receive emails from co-workers or supervisors at 1 or 2 o’clock in the morning. As Freeman points out, “We log on during the drive to work, download a few messages on the train ride home; we look at it in the bath and in between sermons at church. Sixty-two percent of Americans check their e-mail on vacation and respond to work queries, at a time when they’re supposed to be relaxing.” (Freeman Page 140) Freeman gives one explanation of why workers try to keep this insane pace, “If we’re this busy, clearly we’re needed; we have a purpose.” (Freeman Page 140) While this behavior may be expected and even sometimes admired, it is not necessarily rewarded. The personal cost for this practice comes in the form of uncompensated lost personal time, less time for relaxing and increased stress on the body. According to a recent British study, “which followed 2,123 British civil servants for six years, found that workers who put in an average of at least 11 hours per day at the office had roughly two and a half times higher odds of developing depression than their colleagues who clocked out after seven or eight hours.” (McMillen)
A new trend is to initiate the electronic gaze prior to the start of employment. In 2012 the job site CareerBuilder commissioned a survey[1] of 2,000 hiring managers and Human Resources professionals that showed that 37% of them used social media to screen candidates. Some the information the survey found:
What are hiring managers looking for on social media?
Hiring managers are using social media to evaluate candidates’ character and personality outside the confines of the traditional interview process. When asked why they use social networks to conduct background research, hiring managers stated the following:
· To see if the candidate presents himself/herself professionally – 65 percent
· To see if the candidate is a good fit for the company culture – 51 percent
· To learn more about the candidate’s qualifications – 45 percent
· To see if the candidate is well-rounded – 35 percent
· To look for reasons not to hire the candidate – 12 percent (CareerBuilder)
This part of the panoptic gaze forces the individual to create a false persona on the chance a potential employer will search for them online. The gaze at work has created an environment which can be detrimental to the employee’s health and often paints a false picture of the employee’s worth. While the consistent gaze is designed to increase productivity, it often has the opposite effect creating an environment of mistrust and increased costs.
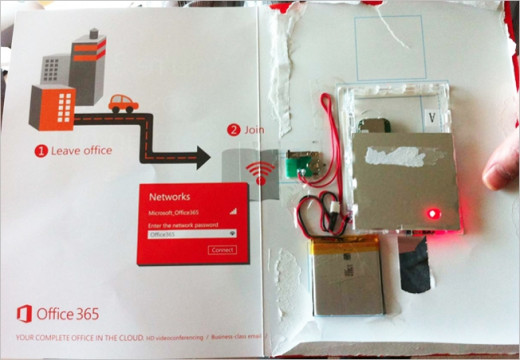
Figure 2
MARKETING
Outside of work, there is little control a person can do to limit the amount of surveillance they are subjected to through the internet. For many, Google’s 2012, change of their securities policies was an expansion of their ability to look into the personal data of their users. The change allow Google to share client data between its many services without the consent of its clients. “When you sign up for a Google Account, we ask you for personal information. We may combine the information you submit under your account with information from other Google services or third parties in order to provide you with a better experience and to improve the quality of our services.” (Google) Before the revision, each service provided by Google had its own security policy and Google needed permission to share the data. One could easily make the argument that all Google is trying to do is basic commercial practice. It is taking the client information for all its services, centralizing the data so it is easier for them to analyze the information, in an attempt to increase their market share. The gaze is not physically on you; however, your data is being observed and analyzed.
Another way the internet is keeping a gaze upon people is in the May 6, 2013 issue of Forbes magazine. (Figure 2) “Many subscribers will be in for a surprise when the latest issue of Forbes Magazine arrives on doorsteps and newsstands. Microsoft has embedded a Wi-Fi router in select copies of the May 6th print edition of the magazine, which gives users 15 days of free Wi-Fi through T-Mobile. The free Wi-Fi is part of Microsoft’s latest campaign to promote its subscription-based Office 365 service.” (Graziano) While the free service is limited for 15-days there is no report on how long the system could remain active. The move was done in an effort to promote a new product.
Researching the needs of current and potential clients is one of the oldest of business practices. An old college textbook definition of marketing is still relevant today. “Marketing Research is the process of identifying and defining a marketing problem or opportunity specifying and collecting data required to address these issues, analyzing the results, and communicating information to decision makers.”(Schoell Page 120) Companies have been conducting client research since the beginning of commerce based economics. The seller has to determine who wants to purchase their goods if they want to stay in business. If the practice of information farming is well established then what is the problem? First of all the speed and depth of information gathered is unprecedented. Internet searches reveal a great deal of information about the user, who may not want the information to be exposed. Never before in the course of human history have we been able to gather vast amounts of information about people and with the speed of a computer’s ability to correlate the data into discernable patterns.
The power exerted with the practice of farming information for business is multi-fold. First is the manipulation of reality to convince the public what is “needed.” The power that is exerted is through the misrepresentation or misuse of the information. In the book, Handbook of Social Economics, Volume 1A, the authors outline some of the problems of these marketing schemes.
“Exploiting their monopoly power, firms manipulate the preferences of consumers through advertising in order to create new (false) needs. Therefore, profits increase and consumer spending rises, to the point where consumers enter a “work and spend cycle.” They reduce the time devoted to leisure activities, or at least they curtail the increase in leisure that would have accompanied productivity and wage increases. Leisure itself is “commodified,” and transformed into a form of consumption (e.g., in exotic vacations, eating out, etc.). Not only, it is argued, is the time devoted to leisure reduced because of advertising, but the mere distinction of consumption and leisure is blurred, as our preferences are “manipulated” to choose forms of leisure that are complementary to consumption. Such patterns of behavior, characterized as the “work and spend cycle” and the “commodification of leisure,” reduces consumers’ overall welfare when welfare is evaluated according to the consumers’ ex-ante preferences, that is before advertising takes place.[2”(Benhabib Page 203)
A problem with mining all this information comes from the accidental or intentional misuse/mishandling of data. Using Google’s policy as an example, the potential for abuse is so great that the Attorney Generals from 36 states have formally expressed their concern over Google’s purposed practice. “Google’s new privacy policy is troubling for a number of reasons. On a fundamental level, the policy appears to invade consumer privacy by automatically sharing personal information consumers input into one Google product with all Google products.[3]” This has become a political issue; President Obama wants safe guards to protect consumer information. "Even though we live in a world in which we share personal information more freely than in the past, we must reject the conclusion that privacy is an outmoded value," President Barack Obama said in a letter accompanying the report. "It has been at the heart of our democracy from its inception, and we need it now more than ever." (Newton) The concerns over protecting personal information appear to cross over standard political party[4] lines. “On Tuesday, April 12, 2011, Senators John Kerry (D-MA) and John McCain (R-AZ) formally introduced the Commercial Privacy Bill of Rights Act of 2011. If enacted by Congress in its current form, the Act will require companies to provide greater transparency to consumers regarding what personal information companies are collecting and how it will be used.” (Salow) However, this bill never made it out of committee and with no real activity to move it forward.
There is good reason for people to be concerned about the security of personal information stored on “secure” websites. According to an April 4, 2011 report by Security Week (Lennon) a data breach at Epsilon[5] exposed the personal data of 2,500 clients. A small sampling of their client list includes, Kroger, TiVo, US Bank, JPMorgan Chase, Capital One, Citi, Home Shopping Network (HSN), Ameriprise Financial, LL Bean Visa Card, Lacoste, AbeBooks, Hilton Honors Program, TD Ameritrade, and Verizon to name just a few. This one security mishap exposed the personal data of millions of people. The cultivated data can be used to steal a person’s identity, commit industrial sabotage or a number of other illegal activities. Increasingly our private information is being accessed and used in ways we have not authorized.
At the same time many people today are voluntarily subjecting themselves to the all seeing eye of the internet. Social media sites provide the world with an intimate view of an individual’s life. For example, in 2011Facebook and Netflicks announced that they were planning to integrate their services. However, existing law that protected consumer video rental information blocked the move. In January 2013, Congress amended the law to allow the merger of the two online services. The way this works is a consumer has to be register first with both Netflicks and Facebook and they can elect for Netflicks to tag the show they watch and post the information so their friends on Facebook can see it. Participation in this activity is voluntary and generally appears to be a harmless disclosure of information. But becomes another public and commercial value judgment that is based solely on the movies you watch.
The exposure to the gaze sometimes comes from unexpected or unwelcome sources. I have often said that I am happy that I grew up when I did. When I screwed up (all kids do) the scope of those who could view my transgression was limited to a few friends, maybe to an extended circle of family members or in my case the whole town (all 2,000 of them). Now if a kid/adult does something stupid/embarrassing the event is memorialized with a posting online where the humiliation can take on a global scale through various different websites. A new term has entered into the lexicon “cyber bullying”. The State of New York describes this phenomenon as, “the repeated use of information technology, including e-mail, instant messaging, blogs, chat rooms, pagers, cell phones, and gaming systems, to deliberately harass, threaten or intimidate others. Unlike physical bullying, where the victim can walk away, technology now allows for continuous harassment, from any distance, in a variety of ways.” (New York State Division of Criminal Justice) Cyber bullying is an action of the gaze Bentham was talking about with a twist. It is putting the information out for public display, and it does not matter if it is fact based or not. The gaze drives action, in some cases suicide, yet we are learning to become numb to the effect.
At Home
Another method of compelling consumers into giving up their privacy is by the selling of fear. Companies such as ADT and Comcast create profits by convincing people that the only way to be safe is to be monitored. The invasion is not sold as intrusive or restrictive, but it presented as protective, that we must be constantly on guard against “them”. From ADT’s home page it says of its home video surveillance, “You work hard to provide your family with the safety and home security they deserve. But your busy life sometimes takes you away from them.”(ADT) Now the Panopticon is complete the surveillance happens at work, play and home. “There is no need for arms, physical violence, material constraints. Just a gaze. An inspecting gaze, a gaze which each individual under its weight will end by interiorizing to the point that he is his own over seer, each individual thus exercising this surveillance over, and against, himself.” (Foucault Power/Knowledge Page 155)
Foucault describes the situation, “In each of its applications, it makes it possible to perfect the exercise of power. It does this in several ways: because it can reduce the number of those who exercise it, while increasing the number of those on whom it is exercised. Because it is possible to intervene at any moment and because the constant pressure acts even before the offences, mistakes or crimes have been committed. …..Because, without any physical instrument other than architecture and geometry, it acts directly on individuals; it gives ‘power of the mind over the mind’. The panoptic schema makes any apparatus of power more intense.” (Foucault Discipline & Punishment Page 206)
Azar Nafisi explains in her book, Reading Lolita in Tehran that fiction should never be mistaken for real life; instead it gives us an insight to the reality around us, “do not, under any circumstance, belittle a work of fiction by trying to turn it into a carbon copy of real life; what we search for in fiction is not so much reality but the epiphany of truth.” (Nafisi Page 4) So while George Orwell’s novel 1984, is not a representation of reality it gives us an understanding of what a future abuse and continuous monitoring of people by the government/business could look like. “The telescreen received and transmitted simultaneously. Any sound that Winston made, above a whisper, would be picked up by it; moreover, so long as he remained within the field of vision which the metal plaque commanded, he could be seen as well as heard. There was, of course no way of knowing whether you were being watched at any given moment. …in the assumption that every sound you made was overheard, and except in darkness, every movement scrutinized.” (Orwell Page 6) We are fast approaching a technological state which can obtain the same level of observation as Orwell predicted. A person would be foolish to believe that the government, businesses, or individuals are not capable of routinely monitoring internet and E-mail activity.
There are several laws on the books that require the cooperation of the telecommunications industry with law enforcement agencies. One such law is the Communications Assistance for Law Enforcement Act of 1994, which states that it is, “To amend title 18, United States Code, to make clear a telecommunications carrier's duty to cooperate in the interception of communications for law enforcement purposes, and for other purposes.” (Communications Assistance for Law Enforcement Act of 1994) The disturbing line to many people is “for other purposes,” which is not clearly defined. Also under Title 18 sections 2511 and 2518 are situations where law enforcement agencies do not need a court order or a warrant to have access to the data. The reason that the government and law enforcement were given these powers is in reaction to the changing technologies and the new crimes that came along with them. Along with the capabilities comes the probability of abuse, the accessing of data for reasons not originally intended by the drafters of the law. “The USA PATRIOT Act (P.L. 107-56) authorizes the FBI to use National Security Letters to obtain a range of information including data pertaining to e-mail and Internet use. It appears that U.S. law enforcement has effectively exploited the Internet—which radicalizing individuals can mine for information and violent jihadists use while plotting—in its pursuit of terrorists.” (Bjelopera Page 3) Each of these laws were not intentionally designed to violate an individual’s privacy. However, when they are used outside the scope of their original design they become a vehicle to do so.
Figure 3
The Impact
The French revolution saw Bentham’s design as something special. “The new aspect of the problem of justice, for the Revolution, was not so much to punish wrongdoers as to prevent even the possibility of wrongdoing, by immersing people in a field of total visibility where the opinion, observation and discourse of others would restrain them from harmful acts.” (Foucault Power/Knowledge Page 153) Part of the justification for the implementation of monitoring government is the prevention of future unlawful actions and to catch/punish those who would commit violent acts prior to them being committed.
While there are people who are willing and able to manipulate the data and power for their own pleasure or profit, there is no single government agency or corporation behind all the surveillance that exists. There is no one evil conspiracy that has designed the current system of surveillance. It is the evolution of the technologies in relation to the governmental and business models that we have adopted. As such it is possible for an individual to be under an electronic gaze 24 hours a day. Foucault explains the effect constant surveillance has on the individual, "An inspecting gaze, a gaze which each individual under its weight will end by interiorizing this surveillance to the point that he is his own overseer, each individual thus exercising this surveillance over, and against, himself.” (Foucault Power/Knowledge page 152) People internalize the process to the point that they believe it is the natural way of living, thus exerting a power over themselves. The surveillance is creating an environment where mistakes are not tolerated and every move captured in a specific moment in time analyzed and paints a picture of the individual that the painter wants to see, not who they necessarily are.
This all is not to say that there is no value to having surveillance. One can look at the speed in which the bombers of the Boston Marathon were identified and apprehended to appreciate the speed in which the information was put together. There is no doubt that all the security, cellphone, news and personal recording devices, which captured every angle of the event, were helpful in the resolution. However, that same technology can and has been used for other purpose besides legitimate law enforcement.
With all the surveillance, it is easy to forget how little privacy there is. To be observed has become the natural state of being in many industrialized countries. The constant gaze that is being applied is used to make decision in the manipulation of personal movements, credit, buying, government policy, social status, and thinking. The point of this article is not to have everyone become a Luddite and stop using the internet, rather to understand the risks. You need to have a strategy of how you want to be represented online presence. Out of this constant level of observation a new industry has risen, designed specifically to protect or do damage control to an individual’s or a business’s online presence. But even companies like Reputation.com state, “In a nutshell, online reputation management, or ORM as it’s known, is the practice of making people and businesses look their best on the Internet. To accomplish that, people need to control their online search results because they frequently contain inaccurate, misleading or outdated material which can adversely influence how web searchers view them.” (Reputation.com) You need to determine how much are you willing to put out there for the world to see. Remember that anytime you agree to the privacy policies on a website you are being observed. When you sign up for a credit card, a store discount card, or get an oil change you are leaving a trail of actions that can be observed and analyzed. The internet is a tool; it can be a very useful in communications, research, etc. As you can tell in the writing of this article internet access was utilized. However, with any tool there are inherent dangers. As with all tools, there is a price to be paid, in the case of E-mail and the internet the price is privacy.
Footnote
[1] The survey was conducted by Harris Interactive© February 9, 2012 to March 2, 2012.
[2] Another factor often cited, as a cause of the “work-spend” cycles is a preference for status and/or for conspicuous consumption. We do not discuss this literature here as Frank (2010) takes it up, in these same volumes. In Benhabib-Bisin (2002), we provide a model of the effect of advertising on status which casts some doubts on the ability of this factor to support the Postmodernist Critique.
[3] A copy of the letter can be found at http://epic.org/privacy/google/20120222-Google-Privacy-Policy-Final.pdf. (accessed February 26, 2012)
[4] Democrat, Republican, or Non-Denominational
[5] From Epsilon’s home page “Epsilon provides strategic consulting, marketing analytics, database, email and loyalty marketing technology, proprietary data, direct and digital marketing services, including creative and interactive services, media services, web design and development, email marketing and direct mail production.”
Figures
Figure 1: Bentham’s Panopticon. Source: http://outreach.lib.uic.edu/www/issues/issue9_9/rajagopal/index.html. (Accessed February 27, 2012)
Figure 2: Microsoft adverting WiFi hotspot. Source: http://news.yahoo.com/microsoft-promo-turns-forbes-magazine-free-wi-fi-182539880.html. (Accessed May 3, 2013)
Figure 3: When are you being watched? Source: Self
Bibliography
ADT Home page. http://www.adt.com/. (Accessed March 19, 2012)
Benhabib, Jess and Alberto Bisin. Handbook of Social Economics, Volume 1A. Chapter 6 Social Construction of Preferences: Advertising . Elsevier B.V. 2011. http://www.econ.nyu.edu/user/bisina/sdarticle%20social%20construction.pdf. (Accessed March 27, 2012)
Bentham,Jeremy. Panopticon; Or The Inspection-House: Containing The Idea Of A New Principle Of Construction Applicable To Any Sort Of Establishment, In Which Persons Of Any Description Are To Be Kept Under Inspection; And In Particular To Penitentiary-Houses, Prisons, Houses Of Industry, Work-Houses, Poor-Houses, Lazarettos, Manufactories, Hospitals, Mad-Houses, And Schools: With A Plan Of Management Adapted To The Principle: In A Series Of Letters, Written In The Year 1787, From Crecheff In White Russia. To A Friend In England. http://cartome.org/panopticon2.htm (accessed February 22, 2012)
Bjelopera, Jerome P. Congressional Research Service. American Jihadist Terrorism: Combating a Complex Threat. November 15, 2011
CareerBuilder. Thirty-seven percent of companies use social networks to research potential job candidates, according to new CareerBuilder Survey. http://www.careerbuilder.com/share/aboutus/pressreleasesdetail.aspx?id=pr691&sd=4%2F18%2F2012&ed=4%2F18%2F2099. April 18, 2012. (Accessed April 13, 2013)
Foucault, Michel. Power/Knowledge. Pantheon Books. 1980
Foucault, Michel, Translated by Alan Sheridan. Discipline and Punishment: The Birth of the Prison. Vintage Books. 1979, translation copyright 1977
Freeman, John. The Tyranny of E-Mail: The Four-Thousand-Year Journey to Your Inbox. Scribner. 2009
Google. Google Privacy Policy. http://www.google.com/policies/privacy/ google/20120222-Google-Privacy-Policy-Final.pdf.. (Accessed February 26, 2012)
Graziano, Dan. Microsoft promo turns Forbes Magazine into a free Wi-Fi hotspot. BRG NEWS. http://news.yahoo.com/microsoft-promo-turns-forbes-magazine-free-wi-fi-182539880.html. April 30, 3013. (Accessed May 3, 2013)
Lennon, Mike. Massive Breach at Epsilon Compromises Customer Lists of Major Brands. Security Week. http://www.securityweek.com/massive-breach-epsilon-compromises-customer-lists-major-brands. April 4, 2011 (accessed February 26, 2012)
McMillen Matt. Health.com. Working long hours doubles depression odds. http://www.cnn.com/2012/01/25/health/working-overtime-doubles-depression/index.html. updated 5:31 AM EST, Thu January 26, 2012. (Accessed March 19, 2012)
Monroe, Mark. The Metaphysics of Discrimination. UMI Dissertation Services. 2001
Nafisi, Azar. Reading Lolita in Tehran: A Memoir in Books. Random House. 2003 (paperback 2004)
Newton, Casey. Google follows privacy trend on tracking. http://www.chron.com/business/article/Google-follows-privacy-trend-on-tracking-3357534.php. Hearst Communications Inc. Published 10:06 p.m., Thursday, February 23, 2012 (accessed February 25, 2012)
New York State Division of Criminal Justice. Cyber Bullying. http://www.criminaljustice.ny.gov/missing/i_safety/cyberbullying.htm. (Accessed March 30, 2013)
One Hundred Third Congress of the United States of America. At The Second Session. Communications Assistance for Law Enforcement Act of 1994. Pub. L. No. 103-414, 108 Stat. 4279.
Orwell, George. 1984. Signett Classic . Penguin Books. 1981 (original Copyright 1949)
Repetuation.com homepage. Reputation.com. (Accessed May 1, 2013)
Salow, Heidi, Alan Sutin and David A. Wheeler. United States: Proposed Federal Privacy Legislation:Summary Of Kerry-Mccain Bill. http://www.mondaq.com/unitedstates/x/140374/Data+Protection+Privacy/Proposed+Federal+Privacy+LegislationSummary+Of+KerryMccain+Bill. 05 September 2011. (Accessed March 20, 2012)
Schoell, William and Joseph Guiltinan. Marketing: Contemporary Concepts and Practices. Allyn and Bacon. 1990
The American Institute of Stress. Job Stress. http://www.stress.org/job.htm. (Accessed February 27, 2012)
Do you believe that your movements on the internet are private?
© 2013 Mark Monroe









