How to Apply Risk Based Process Management
Product Control - Check if the Door is Closed
When we leave home and I lock the door with the key, my wife always asks to "feel if the door is closed".
But that is not necessary, because I verified when I turn the key twice to the right until it cannot go further, the door is locked. Why should I feel if the door is closed then?
What my wife wants me to do, is a product control to feel if the door is locked after locking it. But this is a redundant step. Because I know that by turning the key the door is closed.
When a process delivers a 100% verified product, the product doesn't need to be checked anymore.
Turning the key of a door to the right (in my case) delivers a locked door. Turning it to the left delivers an open door. It's not necessary to verify this system every time. This is a very simple example of Risk Based Process Management.
- How high is the risk that I leave the door unlocked when I feel if the door is locked? 0%. But this is a product control, that will keep me forever on this non-systematic level.
- How high is the risk that I leave the door unlocked when I verifiable turned the key? 0%. But this is a process control (= higher = better)
- How high is the risk that I leave the door unlocked when I pull out the key without verifying that I turned the key? 50%. Turned vs. not turned similar with flipping a coin.
You can now determine which risk level is acceptable for you.
Did you ever used Risk Based Process Management?
Trust
It is important to understand the example of the locked door. If you also have the trait to check things that were already verified, you'll have troubles using Risk Based Process Management.
After verification you have to trust that contractors are doing a fine job according to their system. If something is wrong in their system, trust on the fact the auditors will find this out and trust on the fact the penalties have enough force to correct the processes and partly reorganize the system.
It is of course allowed to look on products, but your opinion about a product has no status anymore once systems and processes are audited and verified to be good. Failed products are a sign of a failing process and a failing system that should control the process, this is where you should be and forget the product.
Your Clients' Risks
When you want to control projects using risk based techniques, the risks of your client must be determined first. For this you need your client, because you cannot determine for your client what his/her risks are. Of course you must help to brainstorm and think about events and consequences. Help your client on his way to determine the major risks and how to control them.
This process must be done before you start designing, tendering and constructing.
What Is a High Risk Here?

Risk Table for Construction Projects
Class number
| Probabliity (P)
| Consequences time (T)
| Consequences money (M) relative to budget
| Consequences quality (Q)
|
|---|---|---|---|---|
0.
| Not applicable 0%
| Not applicable 0%
| Not applicable 0%
| Not applicable
|
1.
| Very small <0.1%
| Very small (few days)
| Very small 0.1%
| Not according to directive: functional
|
2.
| Small 0.1-1.0%
| Small (1-2 weeks)
| Small 1.0%
| Not according to contract: functional
|
3.
| Average 1-10%
| Average (< month)
| Average 2.5%
| Functional loss of not important part
|
4.
| Large 10-25%
| Large (1-3 months)
| Large 5.0%
| Functional loss, repairable essential part
|
5.
| Very large >25%
| Very large (>3 months)
| Very large 10%
| Functional loss, unrepairable essential part
|
Probability (P) can be estimated by using the technique of: the amount of ways it can happen / the total amount of outcomes.
Risk Management and Audit Threshold
The matrix above is multifunctional and can be used for every construction project. According to the matrix above the highest risk can be: 54= 625.
The often made mistake is that chances larger then 50% are incorporated in the risk database, they must be determined as an occurring event and should be covered in the contract. For example: How high is the chance you'll lack money if you have no budget for unprovided costs? This is 100% - it cannot be part of your risk management, you must have a budget for unprovided costs. But the height of your budget unprovided can be part of your risk management.
Before you start to determine your risk matrix, you must determine your risk threshold, for example 34= 81 or for example 2*3*4*3=72. Every risk above 81 resp. 72 becomes part of the audit plan. It is always allowed to change the threshold. Don't forget to incorporate this freedom in the contract.
All risks beneath the threshold are accepted during the coming audit cycle. If this risks occur nothing in the processes or system has to be corrected.
Safety Risks
In all projects safety and environment is (or should be) the number one priority. The goal should be: zero accidents. The number of accidents on construction sites are still very high. Safety risks are mostly on top of the list.
A serious safety accident has direct impact on all management aspects of your project: money, time, human resources, organization and communication.
Preventing accidents should your top priority.
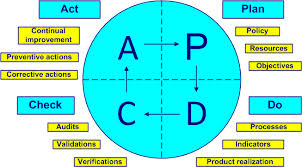
Deming Cycle
Quantifying Safety - An Example
Quantifying risks is the most difficult part of all, because it requires fuzzy science.
Example: How big are the risks on a safety incident on a construction site of a high rise project of 50 million dollar? You should ask yourself then: What kind of safety incident? A worker losing the ability to function after the incident.
The cause can be carelessness of a worker, but the deeper cause is a failing system that gave the worker too much freedom (or improvisation) to 'play' with the safety rules. The effects are: the injury of a worker, a nerve-racking investigation, possible trauma of other workers, delay of your project, extra money, negative impact and perhaps even negative quality of the project. This event can be expressed in a cold figure: Risk = P x T x M x Q.
- The chance on a severe safety incident on a high rise construction project of 50 million dollar is statistical around 2% (P = 3).
- Due to investigations and upgrade of the system you'll have a delay of a few months (T=4), the authorities won't let you continue until the safety system is watertight.
- The salaries of the team will continue longer on the same project, perhaps there are penalties to pay. There might be legal discussions with the main constructor. On a large project the impact won't be so big, around $500,000, which is in this case 1% of the budget (M=2).
- The safety incident of a worker must be defined as a functional loss of an essential part (Q=5).
In this case the risk of a mortal incident will be: 3 x 4 x 2 x 5 = 120. The smaller the project the higher this risk becomes, it can derail your whole project.
Passive Risk Control
Many contractors work with subcontractors. The main contractor is responsible for abidance of the safety rules on the construction site. Abidance of the safety rules costs a subcontractor more time, so it costs indirect money. Subcontractors can try to avoid time consuming safety rules. Safety risks can jump from this way of organizing. You can demand the main contractor to pay a bonus for every subcontractor that finished the work with ZERO accidents. It is a passive process control that appears to work very well.
You can add to this simple method all kind of features, like an abatement for every registered accident on the site.
How to Start?
When you're looking at a blanc page of your project, with a new team, the question immediately starts - how to begin?
Once you composed the right team for your project, you can drain all knowledge of your team members. Let your team members mention what they see as risks, write this down and organize this in logical groups.
Divide your risks in the following groups:
- Geologic
- Economic
- Social
- Juridical (includes Safety)
- Financial
- Political
- Technical
Keep your system as simple as possible. Write down all the motivations of the choices, the scores that are given to risks, and keep a good administration of your risk session.
Make an inventory of the probability and the impact of every risk that is mentioned. Most important of all what your team suggests how to prevent and control the risks. Start with the highest risks first and go down.
Risk management is dynamic. Especially in the beginning the risk sessions must be updated at least every two weeks.
Corrective Measures
Ideally you should prevent all risks to occur, unfortunately you cannot. In case risks occur, it means something in the concerned processes is wrongly organized.
According to the Deming Cycle the 'act' must be used to determine, to administrate and to change where it went wrong. These parts of the process must be reorganized to prevent the same events to occur the next time.
Risks beneath the audit threshold are usually not corrected. It is in this case up to the contractor to correct this or not.
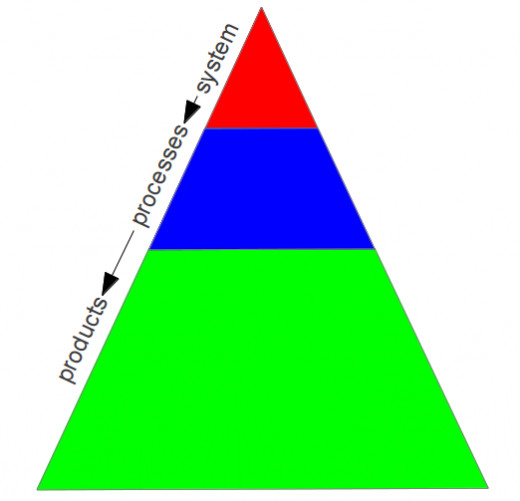
Next Steps
The next steps you can take after finishing your risk sessions is to determine which risks are already present in your team and how to control them. The auditors have to make an audit plan to monitor the risks.
Explain the Deming cycle - the plan-do-check-act cycle. You must manage the system and the administration.
The Role of the Contractor
The contractor that is going to build your project must have a certified system, for example ISO 9001. This system is verified by the issuer, your auditors must audit this too, in order to verify the system is suitable for your project before you contract the contractor.
All the processes concerning your project must be described, what the risks are on failure, how it is maintained, how it is controlled and what products are delivered using this process.
All products must be described in detail and what the concerned processes are to deliver this product without failures. This, of course must all be done by the contractor.
The risks your team determined must be present in the system of the contractor. If some risks are not present they need to be added by the contractor and the contractor has to control these risks.
What to do With Audit Findings
After you have determined the risks that are above the audit threshold, the auditors will make an audit plan based upon this risks. The contractor will be audited periodically. From every audit the auditors make a report.
In the case the auditors have findings, these findings are written down and during the audit communicated with the interviewed employees. A finding is a failure in one ore more of the processes and/or system, which means the quality of the delivered products that depend of these processes are not constant.
The contract must be divided in payment cycles. The next payment cycle will be withheld until the involved processes are revised and re-audited by your auditors. If the necessary updates are made the withheld payment(s) can be paid.
Product Samples
If the system and the processes are perfect, all products must be perfect too. If not, the processes and the system have failures and must be adjusted on all interfaces according to the Deming Cycle.
To find out if products are failing, you can go rarely with members of your team on a "inspection round" to take samples of products. Every product that is not according to specifications is a sign of a failing system. You don't have to go deeper into the matter of the product. It's the contractors task to improve these specific processes.
The auditors must re-audit after the adjustments the system and all concerned processes.
Conclusion
Working with Risk Based Process Management is not as difficult as it looks. Bear in mind the Deming Cycle always works on all aspects of a project. Use it constantly to improve the way of working.
Trust is the basis of Risk Based Process Management. Trust on the system, trust on verified processes, trust the auditors, trust that the team members are doing a fine job, and trust the contractor is delivering products without failure.
If something is wrong, the audits will reveal this and you must take preventive measures. The system will correct everything afterwards, as long as the financial penalties are strong enough to correct the systematic procedures of the main contractor.
© 2013 by Buildreps