Mainframe Security

Mainframe security is as important to an organization's success as it is complex.
For organizations utilizing the z/OS mainframe, keeping the mainframe safe and secure is an absolute necessity. Never mind the potential for catastrophic data loss, but to simply stay in line with the many regulatory agencies, securing the mainframe must be at the forefront of all business practices.
There are many aspects of mainframe security that must be tended to in order to both achieve compliance and secure data. Securing access to the network, securing the network itself and data encryption all need to be done in the name of mainframe security.
We will provide information on all aspects of mainframe security along with sources that provide the information needed to get an understanding of this complicated topic.
Encryption
Data can never be truly protected without the use of good encryption software
Encryption is a vital component of any mainframe security plan. Mainframe encryption used to be a luxury but now is an absolute necessity for compliance and data security. The goal of encryption is to allow only authorized parties the power to view data in its readable state while all others, if they're able to gain access to the data somehow, won't be able to do anything with the ciphertext (data in its encrypted, unreadable state is called ciphertext). Encryption software is needed to encrypt data, decrypt data and perform other auxiliary tasks throughout the encryption process. Random key creation and key management are examples of supporting tasks done with software and depending on how comprehensive the encryption software is, everything may be done within the same product.
PGP Encryption
PGP encryption provides excellent data security and more
Although encryption is a necessity in today's business world, there are different methods that can get the job done. For organizations using the mainframe, PGP encryption is the best option IMO. PGP offers more security than other methods and there are many added benefits as well. A highlight of PGP is that it uses public-key cryptography.
What is public-key cryptography?
Each user that encrypts or decrypts data within PGP must have their own public and private key pair. Public-key cryptography is based on an cryptographic algorithm that mathematically links the public and private keys of each user. While there's a link between each user's key pair, it's essentially impossible (termed computationally infeasible) to derive the private key from the public key in any properly generated key pair. The strength of public-key cryptography and PGP lies in the private key because it never needs to be sent or available anywhere except in the specific user's possession. Other encryption methods use the same key to both encrypt and decrypt (symmetric-key cryptography) - the same process of encryption used in PGP before public-key cryptography is utilized. This gives PGP an added level of security over other encryption methods.
How does PGP encryption work?
In PGP encryption, the recipient's (whoever is going to decrypt the data) public key is used to encrypt a random key after that random key was used to encrypt the data. This process is shown in the diagram below and the result is an encrypted random key along with the encrypted data and this can either be sent or stored. No matter what happens, the only person able to decrypt the data and get it back to its readable state is the person attached to the public key used during encryption. It will also be known exactly who encrypted the data as they use their private key to create a digital signature.
PGP Encryption: A Layman's Guide to How It Works
PGP encryption affords excellent data security and many added benefits like confidentiality, authentication and compatibility. It's important to note that the version and features of PGP must be the same for both encryption and decryption. Some large organizations require companies that either receive data from them and send data to them to not only use the same PGP encryption method but the same encryption software to eliminate any potential troubles during the data transfer.
There are many PGP encryption software options available today and some will work for the mainframe while one in particular will thrive on the z/OS mainframe. E-Business Server utilizes PGP encryption on System z and unlike many solutions, it will play nice with existing components and it won't require much work to get on with encrypting data using PGP!
PGP Encryption Diagram
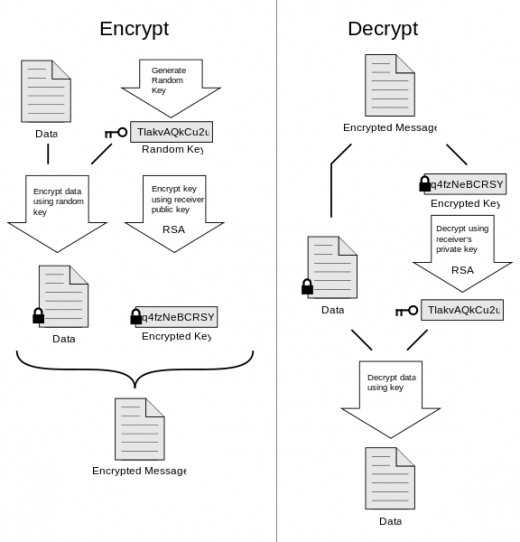
By xaedes & jfreax & Acdx (Own work) [CC-BY-SA-3.0], via Wikimedia Commons



