Sample Master's Thesis - Chapter 4: Project Completion and Recommendations
Published: January 23, 2012

The preceding chapters have detailed the organizational structure of Dayton College, the need for the Virtual IT Lab project, and the implementation strategy of the project. This final chapter documents the project implementation; including the design of the lab, roadblocks along the way, organizational impact, recommendations, and research suggestions to improve the overall security posture of the college.
Preliminary implementation tasks included performing a cost benefit analysis, performing a risk analysis, developing a mitigation strategy for the identified risks, and gathering functional requirements for the lab. These steps have been completed and approved. The Virtual IT Lab project moved into implementation following a directive issued by the Director of Education.
Procurement activities began immediately following the above mentioned directive; which was issued in response to incidents involving the Trojan infections of an assortment of PCs used by students in various shared PC labs.
The number of new PCs for the virtual lab has been cut in half to fall in line with the current enrollment in the Computer Service Technician (CST) Program for which the lab is intended. Twelve PCs have been ordered and delivered. A new file server could not be justified so one of the new PCs was re-provisioned to act as a file server in the lab environment. The PC meets the requirements to provide file and print services under Windows Server 2003.
Functional Requirements
Designing the lab would be a difficult task without first defining exactly what would be expected from the lab. The instructors and program chair participated in a brain storming session to determine what those expectations are. These expectations were compiled into a list and titled the functional requirements. That list of functional requirements follows:
- Isolate the Virtual IT Lab from the production environment
- Highly restrict or eliminate student access to the Internet from the lab
- Provide an environment where students may obtain hands-on experience working on the lab requirements of the curriculum
- Provide platform flexibility to experiment with isolated threats and troubleshooting procedures
- Support the Microsoft Windows XP, Windows Server 2003, and Red Hat Fedora operating systems
Lab Design
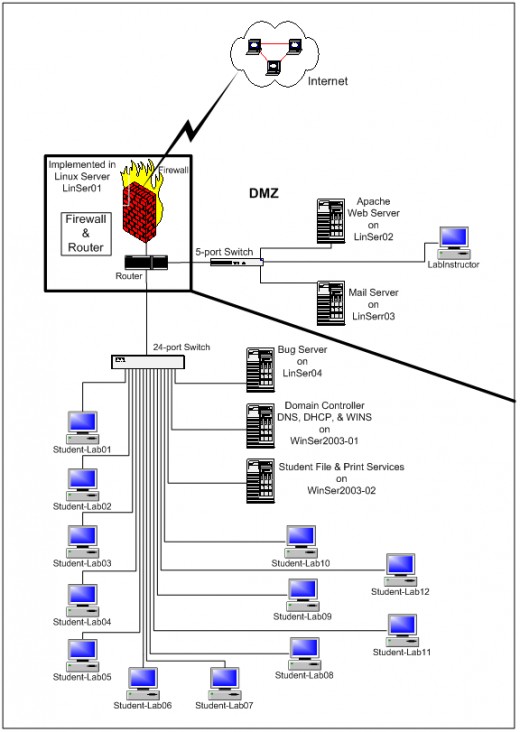
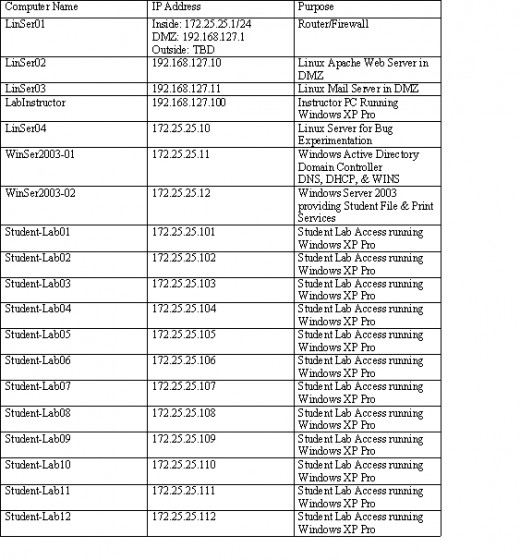
The physical lab design provides for the students to work in an environment that provides the necessary functionality to complete lab assignments and experiment with test scenarios. There will be no physical connections to the campus network; which presents an isolated environment from the production network architecture of the college. Refer to Figure2: Virtual IT Lab Proposed Network Diagram and Table 6: Virtual Lab Logical Design and Addressing; which follow this section for an illustration of the logical design of the lab.
A hardware firewall and router were not approved so one of the donated workstations will be configured as a Linux server and dedicated to the routing and firewall functions. This server is identified as LinSer01 in Figure 2: Virtual IT Lab Proposed Network Diagram.
A dedicated Internet connection has been approved and will serve to provide software updates and driver downloads for the students. Only communication to the web sites containing the necessary drivers and updates will normally be permitted through the firewall; however, instructors will also have the ability to open and close Internet access at will to provide for experimentation by students working on scenarios in various workshops that will be held.
The original specification for the lab called for two 24-port switches to separate the Windows and Linux environments in the lab. However, only one switch was approved by management. This 24-port switch connects all the servers and student computers together in the internal network portion of the lab. Separating the Windows and Linux environments is not absolutely necessary but dedicated DHCP scopes will be used to logically identify hosts as running particular operating systems.
Work-benches have been built around the perimeter of the room and 24 network connections have been placed in strategic locations along the benches to provide the connections to the switch. The Internet connection and computers located in the Demilitarized Zone (DMZ) will interface through the Linux server previously identified as LinSer01. A 5-port mini Ethernet switch will connect directly to the router and the computers in the DMZ will in turn connect to the switch.
Firewall and Router
As stated earlier, a Linux server will be used to fill the firewall and router roles. Most Linux configuration tasks can be accomplished by downloading and installing the appropriate packages. To set up the Linux firewall one of the recycled PCs will be re-provisioned as a Linux server with very basic services. Two additional Network Interface Cards (NIC) s will be installed and configured on three different subnets to create the internal, external, and Demilitarized Zone (DMZ) interfaces. According to Netfilter (2008) the Linux 2.4.x and 2.6.x kernel series contain a framework for firewall services called netfilter. The LutelWall package will be downloaded and installed to aid in the configuration of netfilter.
LutelWall is high-level Linux firewall configuration tool. It uses human-readable and easy to understand configuration to set up Netfilter in the most secure way. The flexibility of LutelWall allows firewall administrators build very simple, single-homed firewalls, and most complex ones - with multiple subnets, DMZ's and traffic redirections. (TopBits.com, 2010).
This configuration will permit a single platform to act as a router and firewall providing filtering services and DMZ isolation for the web-facing servers.
Table 6
Internal Network
The internal network comprises the 12 student computers connected to the 24-port Ethernet switch along with three file servers. Two of the file servers will run the Windows Server 2003 operating system and the third will run Red Hat Linux. One of the Windows servers will act as the domain Controller (DC) for an Active Directory domain and this server will run the Domain Name System (DNS), Dynamic Host Control Protocol (DHCP), and the Windows Internet Name Service (WINS) services. These services are necessary to control the communication within the Virtual IT Lab domain. A second server will host file and print sharing services for the students. This server will also run the Windows Server 2003 operating system. All unnecessary services for both the Windows servers will be disabled so only file and print sharing services will be available on this server.
A third server in the internal network will run a Red Hat Fedora distribution of the Linux operating system and this server will be used as a host computer for instructors to implant bugs that will inject anomalies into the internal network for student experimentation and troubleshooting.
DMZ
The DMZ will act as a buffer area between the Internet and the internal networks. This network segment will contain a web server, a mail server, and an instructor PC. The web server will be used to simulate Internet access while the live Internet is unavailable. Instructors will place the necessary configuration and update files on the web server for students to download. A student web site may also be developed as a part of the coursework; which students would develop and maintain. The instructor PC would be used as a utility computer in the DMZ by instructors and could be configured as a honey-pot, or a system to act as a diversion for intrusion detection research.
Internet
The proposed design of the Virtual IT Lab includes a dedicated connection to the Internet that would only be active when the connection is enabled by the instructors. This connection would serve a very specific purpose and could be simulated by changing the configuration of the DMZ while the live connection is not present.
Organizational Impact
The organizational impact of implementing the Virtual IT Lab environment has been good and the capabilities have been well received by the students. Students are beginning to use the lab to complete project requirements for their IT lab assignments and are gaining real hands-on experience. Participating in workshops presented by the IT instructors in the lab are aimed at helping the students achieve certification goals.
Students working in the lab are not tempted to surf the web so the emerging threats that the project was intended to mitigate have in fact reduced in probability.
Goals Met
Two of the three strategic goals for this project have already been met; specifically, providing an isolated environment for IT students and reducing risk to the college. Student access in the lab is isolated from the world of the public Internet and from the college’ production network as well. The risks associated with the IT students retaining unrestricted Internet access have been virtually eliminated and the risks greatly reduced.
The goal that has not as yet materialized is the reduction in cost of the simulators. The simulators are still in use by most students in the CST Program and the college will evaluate the effectiveness of the virtual IT lab environment before making the decision to continue or discontinue the simulators.
Recommendations
While performing the research for this project, numerous deficiencies in the current security posture of the college surfaced. The recommendations which follow are intended to address those deficiencies.
Unique User Accounts and Strong Passwords
Although unique user accounts require some time and effort to administer, the benefits of providing a more secure environment and the ability to monitor user activities greatly outweigh the time and effort considerations. The practice of permitting all students to log on to the network using a generic student account with the equally generic password of password should be replaced by assigning unique usernames to students and requiring strong passwords. This practice alone could potentially reduce much of the risk exposure to the college’s production network.
Monitoring Facilities
Faculty members should take action to know what activities students are participating in while using computer systems located in the lab environments. Thin-client workstations with mirroring capabilities could be used for monitoring activities. The Virtual IT Lab environment demonstrates that students are able to perform the tasks necessary for program completion in a controlled environment.
The college’s Acceptable Use Policy, see Appendix B, states that the college’s computers are to be used only for college business and academic purposes so no privacy should be assumed by any user. User activities should be monitored to ensure that policy is being adhered to. There are a number of commercially available content filters that also provide monitoring capability.
Incident Reporting
Tracking the incidents as part of the incident response and problem resolution procedures ensures that incidents are responded to and resolved in a timely manner but provides little capability in tracking the types of security incidents that occur, there frequency, or magnitude. Maintaining a simple database, such as the one detailed in a GAO (1998) report would provide such a capability. The number and types of reported information security incidents were collected and analyzed along with the resolutions and disciplinary actions involved, if any.
Collecting and maintaining the above mentioned data would allow generating reports that would allow the college’ security personnel the ability to perform the following compliance related tasks:
- identify emerging problems
- assess the effectiveness of current policies and awareness efforts
- determine the need for stepped up education or new controls to address problem areas
- monitor the status of investigative and disciplinary actions to help ensure that no individual violation was inadvertently forgotten and that violations were handled consistently
(GAO, 1998)
User Awareness Training
User awareness training should be an ongoing activity for student and faculty users alike. The college should publish the acceptable usage and privacy policies to increase awareness of what actions are acceptable, what actions are not acceptable, and what actions will be taken when violations are discovered. The privacy policy should protect PII of both students and faculty while concurrently providing awareness that activities conducted on the college’s computer systems are not private and are subject to monitoring.
Membership in Security Organizations
Membership in professional organizations adds credibility to the opinions of individuals involved in the professions represented by those organizations. This is especially true for instructors who rely on their credibility in order for their opinions to be either accepted or challenged by critically thinking students.
Membership in security organizations would help the individuals involved with maintaining the security posture of the college stay informed about new security threats and countermeasures. Some organizations of interest include the following: (1) the SANS Institute, (2) the Computer Security Institute, and (3) the Information Systems Security Association.
Conclusion
Every organization faces some amount of risk directed toward their information assets, even educational institutions like colleges and universities face risk. The greatest risk may at times come from within the organization; from the very individuals that the organization was formed to serve. This was the case at Dayton College and the reason to implement a Virtual IT Lab environment for a select group of IT students.
The project to implement the lab completed successfully as demonstrated by the elimination of certain threats and meeting the goals set forth for the project. There were, however, certain roadblocks that necessitated creative thinking to resolve. Equipment needed to be repurposed to meet the constraints placed on the project regarding new equipment procurement and scheduled tasks needed to be moved ahead in time to meet an organizational directive. Solutions to the problems were developed and the project was completed ahead of schedule and under the proposed budget. Overall, the project would be classified as a success.
Research Topics
To further increase the value of technology solutions for the college and increase the effectiveness of the security posture, further research should be completed toward the motivations of younger “Generation We” students and the effectiveness of security awareness training on those individuals. Specific questions needing research include the following:
- Does the attitude of younger students toward authority increase the likelihood that those students will attempt to bypass security controls?
- Is security awareness training an effective deterrent to computer abuse for the younger generation?
- Should more stringent control mechanisms be put in place?
Research should also be conducted to develop ways that the Virtual IT Lab environment could aid in increasing the overall security effectiveness of the college. Could effective technical controls be developed that would permit merging the production and student environments without degrading the security posture of the production domain?
Thesis Navigation
References
Accrediting Commission of Career Schools and Colleges. (2010). The Accreditation Process.Available from http://www.accsc.org
Broadstairs, K. (2000). 01-2-2 Quantifying Risk. In K. Broadstairs, R. King, & D. O'Conor (Eds.), Risk Management (p. 39). GBR: Scitech Educational.
Dragoon, A. (2003). Governance: Deciding factors. CIO. Retrieved February 18, 2010 from http://www.cio.com/article/29619/Governance_Deciding_Factors?page=1
Eckert, J. W., & Schitka, M. J. (2006). The hacker culture. Linux+ Guide to Linux Certification (2nd Ed.) (pp. 17-18). Boston, MA: Course Technology
GAO. (1998). Executive guide: Information security management--learning from leading organizations: AIMD-98-68. GAO Reports, 1., Government Accounting Office
Georgia Institute of Technoloogy. (2008). Emerging cyber threats for 2009. CU360 , 34 (21), 4-5.
ISO 17799 Portol. (2007). What is ISO 17799? Available from http://17799.denialinfo.com/index.htm
Moteff, J. (2004). Computer Security: A Summary of Selected Federal Laws, ExecutiveOrders,and Presidential Directives. Library of Congress, Congressional Research Service
Panel on Confidentiality Issues Arising from the Integration of Remotely Sensed and SelfIdentifying, & National Research Council. (2007). Putting people on the map: Protecting Confidentiality with linked social-spatial data. Washington, DC: National Academies Press.
Rainer, R., Snyder, C., & Carr, H. (1991). Risk Analysis for information technology. Journal of Management Information Systems , 8 (1), 134-135.
Schiller, C. (2007). Botnets. Network and Systems Professionals Association. Available from http://www.naspa.com/
Schniederjans, ,. M. (2004). Information Technology: Decision-Making Methodology (p. 140).Singapore: World Scientific Publishing Company.
Spammer-X. (2004). Inside the SPAM Cartel: Trade Secrets from the Dark Side. Rockland, MA: Syngress Publishing
Treviano, L. K., & Weaver, G. R. (2003). Managing Ethics in Organizations : A Social ScientificPerspective on Business Ethics. Palo Alto, CA: Stanford University Press.
U.S. Senate. (2009). Safe Internet act: S 1047 IS. Library of Congress.