IDENTITY THEFT ON THE INTERNET: HOW AND WHY IT OCCURS
MEANING OF IDENTITY THEFT
Identity theft on the internet happens when an unauthorized person gains access into any of your online account and perform any activity (both legal and illegal). It is a fraudulent act that is punishable under various laws in different parts of the world. There are various kinds of identity theft e.g. medical identity theft and financial identity theft.
Identity theft on the internet is a threat to the teeming population that joins the internet community on a daily basis. People need to be educated on the modus operandi of these online scammers. Hence, this hub is given birth to.
BUY IDENTITY THEFT BOOKS
HOW IDENTITY THEFT ON THE INTERNET IS PERPETRATED
Online scammers or thieves can employ any of the following techniques to collect your online identity:
PHISHING AND PHARMING
Phishing and pharming are examples of social engineering. Social engineering in the context of internet or online security is the use of social skills (persuasion) to convince people to unwittingly disclose their internet credentials. A lot of people have lost access to their online account by simply supplying their login information to the wrong people (online identity thieves) thinking they are verifying their accounts. You will be provided with a form to fill. And once the form is filled, the perpetrators of this scam will grab your login details and bingo- your login details will be changed. You will be bewildered in your next login attempt when you are told that your password is incorrect. Below is a shot screen shot of a mail purportedly coming from yahoo.
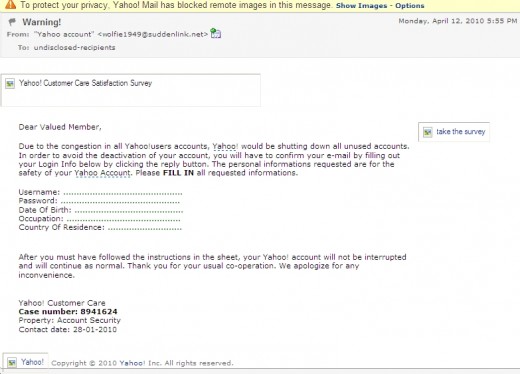
Notice the urgency in the last line of the content of this mail. Also notice that the recipient is undisclosed, meaning that the sender of this email didn’t particularly target you but so many people. To instill fear in you and to create sense of urgency are the main aim of phishers and pharmers. They will start by telling you that your account is in danger of being deactivated if you don’t take action before certain time. Your best protection here is to ignore them. You can read up a true life story of a fellow hubber who had been phished in the past titled phishing and me for more insight. Edit: the link was removed because it no longer exist.
SPOOFING
Spoofing in the context of internet identity theft is a technique employed by online identity thieves to gain unauthorized access into the database of a website that contains the login details of its members. This is a form of hacking where the hacker spoofs an IP (internet protocol) address of a trusted host or within the network. The login detail of every member of hubpages can be collected through this means if hubpages does not have adequate security on their website. You however don’t need to worry yourself much about this as it principally falls into the jurisdiction of site administrators to take care of this threat by deploying and installing latest website and network protection technologies as they are released. At the basic, websites administrators should have IDS (intrusion detection system) and firewall security technology. Again, your best protection here is to vary your passwords from site to site.
HACKING AND VIRUS ATTACK
Hacking can either be positive or negative. It is positive when a program that enhances life is written and it becomes negative when access is illegally gained into a system. Hacking can take various forms which include: spoofing as explained above, brute force, DOS or DDOS (denial of service or distributed denial of service), password crack, dictionary, malicious code, sniffing, hoaxes, spam, man-in-the-middle, mail bombing, buffer overflow, cross scripting, timing attack, social engineering, etc.
Most of these hacking methods are no longer feasible in today’s advanced world of technology but, you still need to know about their existence.
Special note of man-in-the-middle Trojan should be taken as this still cause havoc on the internet especially “internet banking”. Man-in-the-middle Trojan is a newer version of Trojans that is deadlier than its predecessors. It is a high level virus that does not cause any harm to your computer or the host. But stays dormant and silently gather and transmit information from the host to a remote computer. This virus is so intelligent that it can mimic any webpage just to fool the end users. Any online form you open will be mimicked by this virus once your system is infested by it. Man-in-the-middle Trojan is so intelligently programmed to gather your online login data, send them to a remote site and return a “cannot find server” message to you on first attempt after which it goes back to its dormant status and allow you to complete your online form. This will give you an insight into what antivirus companies go through. Your best protection in this regard is to have strong and constantly updated antivirus software installed on your computer.
WHY INTERNET IDENTITY THEFT IS PERPETRATED
The main motive behind the activities of online scammers is to get financial benefits. A lot of people tend to resort to stealing people’s online identity just to cushion the effect(s) (both present and potential) of the crunch in the financial sector. Lazy people that are relieved of their appointments see online scamming as the nearest viable opportunity of making easy money. Fear of the unknown push those that are still working into perpetrating identity theft on the internet.
Greed on the part of the victim is one of the reasons why online scammers succeed. Or how can you explain the wisdom behind someone supplying his financial data online to an unknown destination with the hope of getting one form of financial incentive or the other? knowing fully well that he/she has not done anything in the past to warrant this kind of benefit. Ignorance is another ‘why’ online identity thieves succeed. The probability that you will fall for any of these social engineering techniques is low if you are well informed of the activities of these online and internet miscreants.
The best security measure you can take in order to be free from internet identity theft is to be constantly educated on the activities of these online scammers. Note also that your online data or information can easily leak through people that are close to you. So, take proactive measure today by sharing this hub with them. You can do that by clicking on the ‘share this’ link at the bottom of this hub. Identity theft on the internet is real and ever increasing as more people embrace the internet world of opportunities.
To your internet and online security!
OTHER INFORMATION SECURITY RESOURCES
- Information Security SWOT Analysis
Information securities are those well articulated actions taken to make sure our information is secure. We secure our information to preserve its basic characteristics which are: availability, accuracy,... - WAYS TO PREVENT DATA LOSS, THEFT AND DATA LEAKAGE FROM YOUR LAPTOP AND OTHER PORTABLE DEVICES
In this digitalized age, where almost everything has been reduced to zeros and ones (0s & 1s), the success of all ventures largely depend on its ability to gather data and process such data into information...









