A Guide to Sidestep the Most Common Cryptocurrency Scams

News websites and social media feeds are once again abuzz with the word Cryptocurrency. And this time it is all for good reasons. Majority of Crypto enthusiasts, traders, analysts, and holders believe that the whole cryptocurrency market has risen from the slump, often dubbed as the Crypto winter, which extended for more than one year.
As always, Bitcoin paved the way for recovery and has since risen to values only seen during August 2018. This shift of momentum in the market is sure to bring a lot of new investors, of which a majority would be entering the space for the "get rich quick" property of Crypto. And such an attitude doesn't often go well with Crypto or any investments for that matter.
In comparison to conventional investment schemes, Cryptocurrencies are an entirely different ballgame. Though it had garnered immense popularity (and equal notoriety), the whole Crypto market is only just over ten years old. And some of the best things like the volatility in price (at times the worst thing) and the worst things like the lack of regulations are all due to this immaturity.
Thus a person lured into Crypto on the back of such lucrative gains in short periods can easily fall prey to fraudsters. And in such cases due to the lack of proper regulation in the Crypto space, a legal struggle to retrieve the lost money may not often go in favor of the victim. Hence it is essential to know some of the most common scams that plague the Cryptocurrency space.
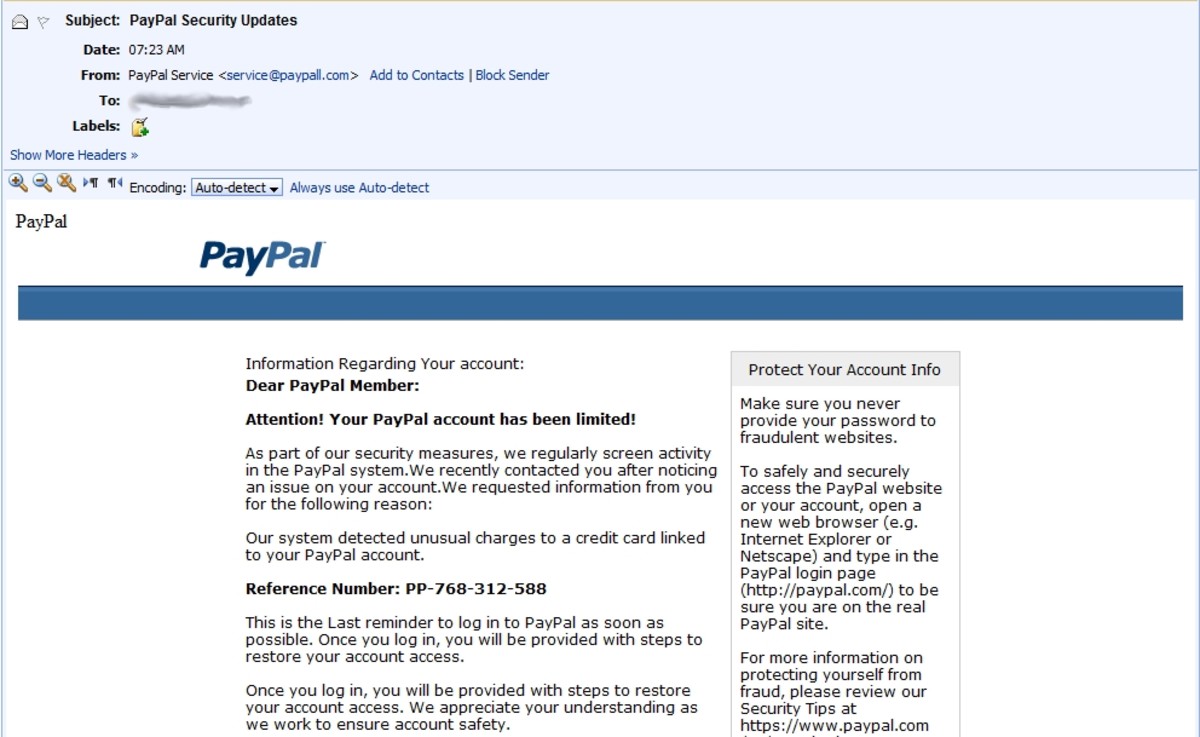
Phishing
Phishing is a common technique that is prevalent among hackers, and anyone who uses a mailbox would receive at least a dozen spam emails which leads them to a Phishing website. A person who is careless enough to type the login details in these websites will directly send them to a hacker.
One of the techniques used by hackers while phishing is devising a webpage which looks similar to another webpage where one would insert the sensitive details to access a website and this website would look exactly like a Cryptocurrency exchange login page or even an Internet Bank account login page only the website address would differ.
Thus to avoid such mishaps one should exercise due caution whenever dealing with sensitive information that puts their investment at risk. Another safer option that improves security is by adding a Two - Factor authentication method to the Exchange account. However, more advanced techniques like sim swapping are being employed by hackers to counter these.
Exchange Hack
An exchange that deals with cryptocurrencies are prone to a hack like any other website on the Internet, and probably in such a scam, a user cannot be explicitly blamed. However, a user can ensure that they would not be affected by such a hack by moving their coins to a local wallet of their control (Hardware or Software) and only move it back to an exchange if they intend to sell it soon. Moreover, exchange hacks are one of the real deal breakers of the Crypto world as it has affected numerous prominent exchanges in the past.
Exchange Scam
An exchange getting hacked is the wrongdoing of hackers, whereas an exchange itself may be a scam. There are several hundred Exchanges that offer the trade of digital assets, however many of these exchanges are too shady and untrustworthy. The prime reason is that most of these Exchanges can cease to exist at any point of time due to the lack of regulatory measures that govern the creation of an exchange. Initially, these trading exchanges will have the look and feel of a credible Exchange. However, once there are enough user coins at their exchange wallets, they exit without a trace. There have been several reported incidents of such exit scams, and as a user, the precautionary measures one can take is to thoroughly research about an Exchange to make sure it is reliable and also moving the coins to a local wallet whenever a withdrawal is possible.
High Yield Investment Programs (HYIP)
Probably one of the oldest means of scams, HYIP scams were in existence way before Cryptocurrencies, so much so there are sites that monitor HYIP schemes. However, for people who are not familiar with HYIP, an explanation would go like this: A website or a "firm" which assures its client to double, triple or even quadruple their investment in a matter of days.
HYIP scams are not necessarily Crypto related, however, after the Cryptocurrency price surges, the HYIP scammers have started to focus more on Cryptocurrencies rather than Fiat Currency. Multiplying a person's investment in a short period through different trading technique is what an HYIP claims to do, thus exploiting an investor's lack of knowledge in Crypto trading. But proper research about Crypto even for a few hours would give a person enough insight to understand that Crypto doesn't work that way and thus the best possible action against HYIP scams is not to invest in them.
The "Get Rich Quick" Coins
Arguably the most common technique to scam in a Cryptocurrency space is to develop a practically useless Coin. A Coin thus developed only serve the purpose of securing enough funds for its developers. Though one can argue that developing such a coin itself is not a scam as no one is forcing the investor to invest in the Coin, however, the ethics of such an action is in question here. Moreover, this scamming technique is the most difficult one to counter for an investor as one is not sure a coin is a scam or whether one is losing out on some cheap Crypto just because of being over cautious. However, when it comes to an investment, it never hurts to be a little over cautious.
That is why there is no one way to find out whether a coin is a scam coin or not, but one can use the following tips to make a decision:
- It would be safe not to invest in a Coin or Token just because it has increased in value for some days. Moreover, the primary step before investing money in Cryptocurrency is to do thorough research of a project. Research carried out through google searches, social media pages of the Coin or direct interaction with the Coin developer can be handy.
- It would be wise to keep a distance from all those projects which only talk about the price of the Coin and not about the utility.
- The volatility of Crypto can be cruel even to the best of the projects thus investing large amounts that can affect a person financially in case the Coin's value diminishes, is not a recommended option.
Summary
The Cryptocurrency market is still a maturing space, and there are regulatory steps that are steadily being employed to safeguard the interests of an investor. However, as a legally gray area of investment, scammers are aplenty in the space. Though over time the Crypto market will mature and might be free of all such scams until then exercise great caution as fraudsters are out there devising newer techniques every day to steal that hard-earned money.
This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters.