Embattled WikiLeaks Founder - Rape or American Counterstrike?
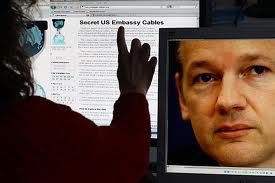
It's probably a safe guess that growing up during the technology revolution was exciting for a young Australian entrepreneur whose early computer hacking abilities have brought him infamy. Julian Assange's name has been splashed across newspapers, blogs, and internet news sites around the globe for the last several years. Whether he's a hero for democracy or a dangerous threat to a government's continued power over the citizenry depends upon who is doing the talking.
1987 brought the world the first portable computer (laptop). That same year Julian was honing his hacking skills with two other hackers, forming the group they named the International Subversives. Julian Assange, born July 3, 1971, grew up in Townsville, Queensland. He spent much of his youth with his mother and half-brother in hiding from one of his mother's boyfriends.
“Don't damage computer systems you break into (including crashing them); don't change the information in those systems (except for altering logs to cover your tracks); and share information,” he wrote, mandating the rules of operation for the hacker's group.
Eventually, Assange was caught in the act. In 1991 he was discovered hacking into the Melbourne master computer terminal of the Canadian telecommunications company of Nortel. As a result, his phone lines were tapped and the Australian Federal Police raided his home. Three years later he plead guilty to 25 charges of hacking though he was originally charged with 31. Besides Nortel, it was reported that he had also hacked into the USAF 7th Command Group in the Pentagon, and several other organizations, including an Australian University.
The judge released him for good conduct and fined him $2,100. Nortel claimed Assange had cost them more than $100,000, but the judge said “there is no evidence that there was anything other than sort of intelligent inquisitiveness and the pleasure of being able to ...surf through these various computers,” then reminded him that he could have been sent to jail for ten years.
Collateral Murder video
Sorry!!! The video of Collateral Murder has been removed from Youtube. Please remember...we're only allowed to know and witness ONE side of the issues that affect our lives and pocketbooks. After all, the average American citizens that make up the masses are no longer considered necessary by our government when it comes to making the rules we are forced to live by.
Andy Greenberg is a reporter for Forbes magazine. In an interview conducted November 29, 2010, he spoke with Julian Assange about his activities with the whistle-blowing internet site, WikiLeaks. When asked, “What do you think WikiLeaks mean for business? How do businesses need to adjust to a world where WikiLeaks exists?” Julian answered, “WikiLeaks means it's easier to run a good business and harder to run a bad business.” He went on to explain that the threat of being exposed on illegal or unethical practices may have a positive impact for consumers and others affected by bad practices. “There's a threat of regulation that produces self-regulation.”
For those who are unfamiliar with the site WikiLeaks, it may sound illegal in, and of itself. One might ask the question, “Isn't it illegal to publicly expose State secrets?” The answer is maybe....sometimes...depending on who is doing the exposing and by what method one might come into possession of those secrets.
Julian Assange is one of the founding members of the organization which had its start in 2006. He considers himself the editor-in-chief of the website, the purpose of which he says is for creating open governments. WikiLeaks doesn't engage in computer hacking, though the organization is often accused of doing so, because of Assange's open admission about his past. What actually takes place requires the efforts of many people spread around the globe. Like Assange, they hold a belief that “the more secretive or unjust an organization is, the more leaks induce fear and paranoia in its leadership and planning coterie...Since unjust systems, by their nature, induce opponents, and in many places barely have the upper hand, mass leaking leaves them exquisitely vulnerable to those who seek to replace them with more open forms of governance.”
When asked about the beginning idea of the site, Julian goes back to 1993 when he started the first ISP in Australia called Suburbia. He says that from the beginning, he recognized the importance of bringing information to the people. Suburbia felt the nudge from companies and individuals pushing for published information. These same groups submitted information for that purpose, with many groups represented such as activist groups, lawyers, and even corporate employees.
They (Suburbia) was considered the “free speech ISP” in Australia and people were flocking to it, all in the interest of exposing unethical or illegal persons, actions, or companies. Other ISP's without the guidance of techno wizard, Assange, were folding under legal threats. He realized very early on that creating a conduit for such information would lead many more people to actively participate in uncovering the secrets, lies, and disinformation used and published by unethical and/or illegal entities.
WikiLeaks is a more expansive and advanced Suburbia designed for the purpose of supplying a forum for leaked information about activities and practices which the common public has a right to know. Assange and his colleagues collect documents that world governments and other organizations may regard as confidential. Once the documents are collected, the information is subjected to scrutinization, authentication and then analysis, before being posted or “leaked”.
WikiLeaks doesn't have a stable, stationary location. There's no staff to pay, no office equipment, in deed, no office, but rather constantly changing headquarters designed to keep the intelligence agencies so often leaked about, scrambling to play catch up. Around the world, hundreds of volunteers help to maintain the website that is critical to outing the doers of evil deeds. The site's content is maintained on about two dozen servers around the world, as well as hundreds of domain names. All expenses are paid by donations in addition to over 1,000 independent individuals who run “mirror sites”. All content is received anonymously through individuals who upload to the site. Their identities are completely protected due to the technological dexterity of Assange. According to him, even he doesn't know the name or location of the informants who provide information.
Assange has stated that the site is “an uncensorable system for untraceable mass document leaking and public analysis.” Any country or corporation wishing to remove the published content from WikiLeaks, would have to practically dismantle the entire Internet. To date, even thought the site has received more than 100 legal threats, almost no one has bothered to actually file the suit.
While Julian doesn't seem particular about what country, corporation, or individual on which he is perpetrating the “crime”, he does seem to have in his possession, a vast amount of secret US documents, which he hasn't hesitated to publish. Based on the structure of the organization, a logical deduction would tell us that the US has many people who believe in freedom of speech and the right to know about affairs which affect our well-being. While it may be true that some of these “whistle-blowers” are simply disgruntled employees, or dissenters in general, or possibly even criminals engaging in treason (as it is now understood in the new millennium), if those whose names are listed as the perpetrators, or the enablers, or the diversion from truth creators (outright liars protecting self-interests) were not engaging in unethical practices, or committing illegal acts, there would be nothing to leak. There would be no reasons for an organization such as WikiLeaks to grow and thrive on the internet. There would also be no reason for the ruthless, calculating efforts to discredit anyone since there would be no documents to cause embarrassment or threaten positions.
The undeniable truth is that unless those with the power and authority to affect the conditions of the population are checked, and monitored, and called upon to explain activities, they will continue to operate in any manner they choose, mistakenly believing it is their right to do what they do.
It is irresponsible for any true patriot to sit quietly without active participation in protecting democracy, even at the lowest levels of operation, for that is where fascism gains its first toehold. Left unfettered, it grows in strength and becomes a force more difficult to reign in. A fascist government will begin by creating the problem while pretending to be addressing it. They will feed those to be subdued with false statements and scenarios designed to induce emotional distress. Then they will point an accusing finger at a target of their choosing, whose demise will be backed by the people they are misleading. The target will inevitably be something or someone that blocks the activities of the fascist movement, such as freedom of speech, freedom from search and seizure, etc.
While presenting their target, they will use the rights to selected freedoms as an example of how the target is creating the problem and suggest a removal of those rights in the interest of protecting the nation. We have but to think of the craziness at US airports. We began with agreeing to extra precaution about what can be brought onto an airliner, no matter the inconvenience. In our minds, it was a small price to pay. We didn't mind having our shoes removed and checked for hidden box cutters. We decided we could live without many of our toiletries, purchasing them once we reached our destinations. Again, a small price to pay for ensuring safety to all air travelers. Now, only ten years later, we are subjected to full body scans that can see beneath our clothing. If we exercise our rights to refuse the scan, then we must submit to an “enhanced” full body pat-down, which includes TSA officials touching genital areas.
Finding ways to limit, curb, or completely halt freedom of speech has always been an important agenda of fascists. Currently the citizens of the United States are being bombarded with misleading statements and arguments about the importance of the government controlling the internet. There have been several failed legislative attempts at passing the right to control into the President's hands. Another one is in the works. Eventually, it will come to pass if every citizen doesn't take action and oppose the very idea.
The transparency of our government at work, diligently dismantling our constitutional rights is outrageous, and it gives a clear indication of how extensively they believe in our gullibility. With the outcry and demands for explanations originating with the 9/11 “terrorist” attacks, there have been many who have gained an audience to their views and ideas via the internet. Without a doubt, the internet has left communicating news as well as leaking potential scandals, vastly improved. Whereas only local viewers and readers of a news agency could be reached by the release of information prior to the internet, since then, a single story can now grab the attention of millions of people within mere seconds to minutes. It is has become much more difficult to control potentially damaging news stories. How do you go about monitoring and scanning all the copied and forwarded documents and emails of millions of people simultaneously?
Julian Assange has been a bone of contention for officials since he began releasing sensitive information originated by the US government and military. The release of the video titled “Collateral Murder” was leaked in April of last year. It was a video recorded from the cockpit of an Apache helicopter who opened fire on a group of people they mistakenly believed to be insurgents. Among those killed were two Reuters journalists.
After opening deadly fire on the group, the occupants of the helicopter noted a van moving down the road and stopping at the scene. One of the injured men was struggling to crawl across the pavement when the occupants of the van got out to offer help. This was interpreted by the military as aiding the enemy. They opened fire on those helping, showering the van with gun fire. Everyone outside of the van was killed. The two children, visible through the windshield, were seriously injured. Their father was driving them to school when the US military opened fire.
WikiLeaks posted a diary of the Afghanistan war logs in July, followed by a diary of the Iraqi war logs in October. The second contained almost 400,000 documents beginning January 1, 2004 through December 31, 2009 though March and May of that year are missing.
There have been many who have maintained that releasing the war logs was illegal and placed intelligence operatives and military personnel in jeopardy. This is untrue. The logs were scanned and specific names of individuals removed, as well as some locations of which enemy knowledge could be dangerous. WikiLeaks doesn't intend to add to the body count by being irresponsible with what is being posted. Assange believes the overview of the war, a broader picture can be seen by those who read the documents. Contained within are the rumblings of a government bent on self-promotion and world domination. Not exactly the reasons Americans were fed as the purpose of the war.
Now it would seem that Assange and WikiLeaks is under attack by the US government and other big business whose illegal and unethical practices have landed them in the “WikiSpot” (spotlight brought about by a WikiLeaks related post). According to documents posted and leaked through WikiLeaks last December, the law firm Hunton and Williams approached Palantir, HB Gary Federal, and Berico Technologies to draw up a report analyzing the potential threat brought by WikiLeaks. All three companies are related to computer, software, and internet security.
Recommendations contained in the report include personal attack of the constitutional lawyer Glenn Greenwald for his support of WikiLeaks. One of the statements referring to Greenwald said, “These are established professionals that have a liberal bend, but ultimately most of them if pushed, will choose professional preservation over cause, such is the mentality of most business professionals.” Are they saying that business professionals are likely to throw away principles and ethics if faced with a smear campaign instigated by agents of our government, when it means all credibility will be destroyed?
Another recommended action is listed on the page subtitled Potential Proactive Tactics. Verbatim, it says, “Feed the fuel between the feuding groups. Disinformation. Create messages around actions to sabotage or discredit the opposing organization. Submit fake documents and then call out the error.”
An attack of a different kind was launched in August 2010. Two women met and slept with Julian Assange within a four day period during his stay in Sweden. Both posted Twitter boastings about their “conquests”, both admit they were fascinated with him prior to meeting him, and both had contrived chances to meet him. Both admit to having consensual sex with him. Both are claiming rape. While with one woman, a condom had broken and the woman had become upset, believing that he had damaged it on purpose, though he denied it, the other woman claims that she woke up to Assange in the act of penetration without a condom, but allowed him to continue without it, even though the previous night she had insisted he was to use one. She then got out of bed and went shopping for items with which to cook him breakfast.
Interestingly, both women met Assange at the same conference. It wasn't until Assange failed to make the expected follow-up call requesting another “date”, that the two woman became less infatuated with him. After meeting each other to discuss him, both women suddenly lodged complaints to authorities that he had raped them. It would seem his playboy attitude was viewed by them as “cheating” with another woman. The only way to make him pay was through the allegations of rape, as it is illegal to have sex without a condom in Sweden and doing so without the woman's permission can be construed as rape.
After an initial investigation into the complaints, prosecutors for Sweden dismissed the charges and nothing more was heard about it. However, in December, Assange learned Sweden had issued a European Arrest Warrant to extradite him to Sweden for the purpose of questioning. Not surprising to any of us who have noticed the timing, the decision to give credence to the allegations came directly on the heals of the November 28th WikiLeaks release of 251,000 American diplomatic cables. In relation to the cables, Assange told London reporters that they showed how the US ordered ambassadors around the world to “engage in espionage behavior”. He also stated that the order represented how the US was “gradually shifting to a lack of rule of law which needed to be exposed....”
While the ridiculous rape allegations will probably not amount to any real legal action against Assange, the damage intended has already taken place. His credibility has been compromised. Any search of his name comes up repeatedly linked to rape. There are questions everyone should be asking before forming an opinion regarding his real or imagined crime. Why were the two women so intent on meeting him? Why had they turned to each other, collaborating their stories, asking the police for assistance but refusing to file an official report of their complaints? One other fact, both women had political connections to the Embassies and their events. It would appear to anyone with even half a brain, that this was just another attempt by the American government to discredit a person with perceived where withal and power, to tumble their aristocracy.
If you find this information helpful or interesting, why not pass it on by clicking the Tweet, Like, or +1 buttons provided at the top of the page?
- The New World Order: Not Just Another Conspiracy Theory
- The CIA: A Nazi Network
- 9/11: The New Pearl Harbor?
This year marks 10 years since terror proved it had grown roots in American soil. Much has been written and rewritten about the events of 9/11, as well as some of the blunders in handling a growing concern with terrorism. The author gives a chronolog - Sharia Law In America
Our insistence on being politically correct has led us down the merry path extreme Islamists have always intended, that of becoming a country divided on how we should be treating Muslims and their religion. There can be no division if we are to prese









