Intelligence Operations in Darfur, Sudan
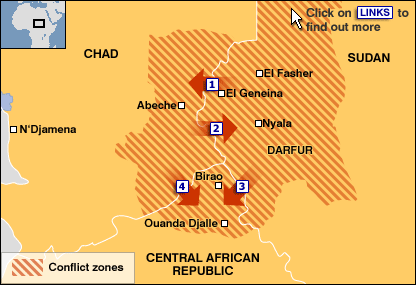
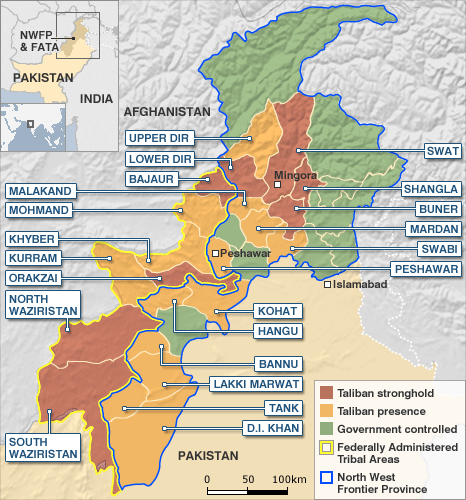
The situation in Darfur bears a striking resemblance to the condition in Afghanistan and Pakistan today. There is an ongoing insurgency and there has been Al Qaeda influence over the years. The border is insufficiently patrolled and locals cross it regularly without resistance. While these are different geographic locations, many of the lessons learned in Afghanistan will apply. This is partially because Al Qaeda can be reasonably expected to involve itself in the area if America becomes too heavily committed. The fact that America is currently planning to pull out of Afghanistan in the near future will already contribute to the image of Al Qaeda and the Taliban as “freedom fighters” that successfully rebelled against the occupation of the Americans just as the Mujihadeen were able to repel the Soviets in the 1980’s. This opportunity for propaganda in Darfur, Sudan would be difficult to pass up considering the minimal risk to the organizations as a whole compared to the amount of public recognition that it stands to gain. Keeping this in mind, throughout this hub, there will be a number of comparisons drawn between the two regions.

So what type of intelligence organizations are needed to support the peacemaking operation? Well, intelligence at the strategic, operational and tactical levels are all important and strategic will be the first priority as it will help determine the best way to go about dealing with the situation by providing an accurate understanding of the region from a political/military perspective. For example, if we go into Darfur forcefully and start another Afghanistan, we’ll need to know where the rebel leaders are physically located and if they are built up and isolated enough, we may be able to just carpet bomb these insurgents—if they’re far enough away from civilization—and provide humanitarian aid to the refugees. The opposite end of this spectrum involves them having their base set up within the refugee camps. This could explain reports of local government aircraft bombing refugee camps since other countries don’t necessarily have the same rules of engagement that we do as Americans. If these reports are true, we can send in fighter aircraft to provide security to the civilians. Although UAVs are capable of remaining on station for considerably longer periods of time than conventional aircraft with a pilot in the cockpit. A thorough understanding of what’s going on will be necessary to determine priority targets and how to coordinate their targeting and destruction. This usually starts with maps and imagery so National Geospatial Agency (NGA) which is responsible for satellite imagery, (Ford, 2007) would be the first contributors. CIA has a solid HUMINT element and handles such things overseas, so they’d be the first ones sent in to see what we’ll be dealing with, if they aren’t already there (Ford, 2007). Cellular and satellite phone usage is pretty common; National Security Agency (NSA) specializes in exploiting enemy communications (Ford, 2007). Insurgency and terrorism are often very difficult to distinguish from one another and with Bin Laden’s history in the area, it’s only safe to conclude that Al Qaeda will be in the neighborhood and likely to fight America in much the same way that they are in Afghanistan. FBI is the U.S. anti-terrorism authority, so they’d definitely have a hand in the intelligence collection and the ensuing counterterrorism operations that would be going on. Should we decide to resort to military action, the entire DOD intelligence community would become involved in support of battle field commanders. Of course, DIA would be right alongside them.
Let’s take a moment to consider how national intelligence organizations would support multinational operations. Historically speaking, human intelligence provided tactical leaders an early warning regarding enemy plans. When imagery or even overhead reconnaissance (from mountains, cliffs, or even treetops and hot air balloons and today’s spy satellites overlooking the battlefield) became available, it provided an extra element to confirm observations and perceptions as they had been reported to battlefield commanders. HUMINT offers an extra benefit of extracting the enemy’s intended course of action from the infinite scenarios available based on the enemy’s capabilities. In the type of environment posed by Darfur, HUMINT will again be the primary collection platform, just as it is in Afghanistan.

Multinational Intelligence
There would be a degree of collaboration between the U.S. and the other countries involved, most notably the “Big Five” (the United States, United Kingdom, Canada, Australia and New Zealand) that we are allied with. Sharing of information will depend strongly on how the areas of operation are divided. For example, different regions of Afghanistan are occupied by different countries and different branches of their militaries. For the U.S. alone, within just the Department of Defense, the U.S. Navy which tends to head joint operations would have to provide intelligence support for Marines, Army and Air Force, all of which go about combat in different ways. For a multinational operation, the intelligence elements would need to share information and processed intelligence. Also there would need to be a way to share as much information as possible without compromising sources (HUMINT) or ways and means or capabilities (IMINT, SIGINT, etc…). One real-world anecdote that illustrates where this can become problematic occurred in Afghanistan in 2009. The 4th Brigade of the U.S. Army’s 101 Airborne Division had HUMINT collectors working in the same battle space with the Polish HUMINT Collectors. One of the issues encountered was that at times the Polish ran the same sources as the Americans without realizing it. The problem with this is called “circular reporting” in which a single source self-validates because multiple human intelligence collectors talk to him without talking to each other. While the American Operational Management Teams (OMT) could de-conflict sources within the American HUMINT network, there was no oversight for international HUMINT. One would think that the least complicated solution would be to simply approach the Polish HUMINT collectors and ask them directly. The U.S. Soldiers involved did this and found that like the Americans, the Polish wanted to protect their sources. Using a sources name or the town in which he operates can essentially become a death sentence for the source. So it took a long round about real-life version of Milton Bradley’s board game, “Guess Who” to identify each other’s sources and resolve the source of circular reports. There will need to be an international version of American OMTs that provide oversight for international HUMINT operations to prevent this sort of thing from occurring again. On the subject of information sharing; a communication network will need to be established that is compatible across the board, between not only the branches of the U.S. military, but also across the communications platforms used by other government agencies. On top of that, communications between America and other coalition forces as well as the African Union, which has expressed an inadequacy of its communication capabilities (Hillard, 2009).
Combined Intelligence
During different eras in the nation’s past, various intelligence collection platforms, or “-INTs” as they’re colloquially known, have served as the crux of collections. Early in our nation’s history, George Washington was an accomplished source handler and utilized much of the tradecraft that is still in use today (Knott, 1996). It should also be noted that Washington was an insurgent commander during the Revolutionary War and America came into existence thanks to the failed British COIN operation. Later, during the Civil War, hot air balloons where used to photograph the battle field, laying the groundwork for IMINT (Central Intelligence Agency, 2007). During the post World War II and Cold War era, MASINT was used to locate communist command centers (Air Force Institute of Technology, <2009) and SIGINT was used to intercept communications providing valuable insight into the intended enemy courses of action.
In today’s conflict, insurgents utilize civilian infrastructures and blend into crowds so there isn’t the massing of forces in the traditional sense where large numbers of uniformed troops gather in preparation for one big attack on a known target such as a city or some other strategic terrain that serves as a center of gravity which would be extremely obvious (Rotzien, 2007). This type of chameleon-like concealment renders static IMINT such as satellite photography insignificant beyond terrain familiarization and mapping and completely ineffective in tracking enemy movements. Unmanned Arial Vehicles (UAV) fill the gap by providing real-time overhead surveillance.
Insurgent communications are very “low-tech” (Zeytoonian, 2006). Without the Cold War’s volume of electronic emissions and transmissions to intercept; SIGINT, while still important, has ceased to be the workhorse of the intelligence collection effort. Moving forward into this contemporary operating environment, HUMINT is becoming the primary means of collection as the enemy employs decentralized leadership and compartmentalized elements that perform specific missions or roles within the organization. The only connection between cells is the people within them; the same people that, due to security procedures, generally may not even know everyone in their own organization.
Before anyone even sets foot in the region, NGA will have already provided geospatial intelligence in the form of satellite photography and terrain/political maps. CIA would be focused on strategic level intelligence and if Al Qaeda were to renew or otherwise increase its presence and involvement in the region, FBI, the counterterrorism element of America would become involved. DOD of course would need to be involved at the tactical level for joint intelligence operations as troops conducted combat operations. The Department of State has a Bureau of Intelligence and Research. One of their responsibilities is the analysis of geographical and international boundary issues (Ford, 2007) which seems very relevant across the regions of Darfur, Sudan and the FATA in Pakistan with insurgents, refugees and locals moving across the porous borders at will.
Collection Requirements
With all these gears turning to get information, let’s take a look at some of the intelligence collection requirements, collection systems and personnel needed for this type of peacekeeping operation. In this past century, with the numerous technical advances, HUMINT didn’t play as large a role in intelligence collection as it does today. The Cold War ushered in an era of communications interception. In the counterinsurgencies that have developed since then, the enemy doesn’t have all the technical assets normally exploited by military SIGINT. With small numbers, there is no massing of troops that can be detected with satellite imagery. They operate much like an ideological version of U.S. Special Operations, engaging in asymmetric guerrilla warfare with little or no support and improvising to accommodate operational necessity as they choose targets of opportunity that will have the most impact on coalition forces. The low-tech adversary places a disproportionate dependency on HUMINT (Zeytoonian, 2006). While we do have the capability of intercepting personal communications such as text messages and phone calls, the volume of information on any platform makes it very difficult to locate specific targets relevant to the collections effort. HUMINT fills in the gap by getting information on targets such as phone numbers and email addresses that can then be targeted by SIGINT. Furthermore, HUMINT has access to communication platforms such as “word of mouth” or “runners” that carry a message in their head and repeat it directly to the intended recipient.
Traditional order of battle information such as chain of command, strength and numbers, weapons and equipment as well as enemy dispositions (locations) will all be useful. Of course, chain of command will be used to build a personality chart/link diagram of the organizations in play as well as target packages. Tactical SIGINT teams will need to bring in their Prophet (GlobalSecurity.org, 2005) systems among other electronic warfare equipment to collect packet and content data on enemy communications whether by cell phone, handheld radio or even email and any number of other electronic means that will have men in black knocking on our doors. Before putting boots on sand, satellite photos and maps are needed and can be provided by satellites or high altitude aerial photography. Unmanned Arial Vehicles (UAVs) are capable of providing real time imagery of the battle space making them a vital asset to contemporary intelligence collection efforts. However, they have been compromised and insurgents have been able to intercept transmissions from the UAVs to their operators, giving the enemy access to imagery as seen by our cameras (McCullagh, 2009). This real-time “shoulder peeking” at our perspective of the battle field gives them an added advantage and as a result, the exploitation of this vulnerability has most likely also mitigated the capabilities of UAVs to a significant degree. Required personnel will include UAV pilots and maintainers as well as some sort of information technology element to resolve encryption issues. For SIGINT, technicians and operators as well as linguists that can interpret what they intercept. Culturally aware and linguistically proficient HUMINT collectors will have to close the gap with interrogations and Military Source Operations.
Priority Human Intelligence Requirements will include:
- What organizations are operating in the area of responsibility?
- Who are the leaders and key personnel of these organizations?
- What relationships do these organizations have with each other?
- What methods of finance do these organizations have?
- What are the primary targets of these organizations?
- What Techniques, Tactics and Procedures do the organizations use to conduct operations?
- What locations do these organizations use to conduct their operations and planning?
- What locations so these organizations use for stockpiles and caches?
- What training and/or experience do the organizations have?
- What outside organizations provide support to these organizations?
- What methods of recruiting do these organizations use?
- When will these groups conduct their next raid or attack?
- Where do these organizations acquire and store their weapons, equipment and supplies?
- How do members of these organizations identify themselves?

Information Sharing and Challenges
There will be a number of challenges in information sharing with African Union Forces. Much like the ANA, corruption is common in this part of the world and it’s likely that sharing information with the locals will become a counterintelligence risk as they may possibly report to the people we’re after if they don’t moonlight as rebels themselves. Other issues include the language barriers and cultural diversity. There may be people within the force that have been personally or indirectly affected by the conflict and with information that they wouldn’t otherwise have, they may attempt to take matters into their own hands. For example, there was an incident with an interpreter in Iraq who had a personal issue with a detainee’s political and tribal affiliations. With this knowledge, while escorting the detainee to an interrogation room, the interpreter assaulted him, which resulted a severe loss of rapport that the interrogators had managed to establish to that point.
Other issues include communicating the findings across the language barrier to all the African Union Forces which limits the potential for timeliness and availability of intelligence (both characteristics of effective intelligence). According to Lieutenant Colonel Wilson Tembo of the African Union Forces, there is a lack of adequate equipment and personnel (Hillard, 2009).
"We have a good communication plan and architecture that shows how things should be set up but, we do not have the necessary equipment to make it a reality. This is a problem that we see in our mission in Somalia," he said. "We do not have the necessary communications links essential for keeping in touch with our people in order to follow their progress. We came up with a workaround solution, but that is still not sufficient."
LtCol Tembo, Africa Union Forces
Working with the African Union forces can be challenging because increasing our forces in the area since AFRICOM has been recently established. In 2009, there was some mistrust by some of the leaders on the continent who felt that the command would try to find ways to put more U.S. forces on the continent and establish a base in Africa (Hillard, 2009). The perception of being an invading or occupying force is something that Al Qaeda will likely play up and encouraging locals to fight against the Americans as the Taliban successfully did in Afghanistan. Al Qaeda will say that they were successful because the U.S. is planning to withdraw; and in propaganda, perception is more important than reality.
Along with information sharing, there will be challenges in conducting intelligence operations in this type of environment. Besides the challenges of sharing information, the challenges of gaining information are equally daunting. One of the big issues to overcome is the current standard operating procedure where HUMINT, which will be the driver for this type of conflict, requires SIGINT confirmation. Due to the lack of stable government and commercial enterprise, there is a lack of electronic devices such as in-ground phone lines and cell phone towers in use, so that leads to a lack of electronic communication emissions. Necessity drives insurgents in this situation to find another communication platform such as “word-of mouth”. There are satellite phones, but the cost limits the people that can afford them (Woodson, 2005). As a result, there will be less electronic communications for us to intercept. This in turn means that we will have a lot good intelligence from human sources, but not enough validation to act on it. Another issue arises from the fact that with so many refugees in close quarters, once they realize that our sources get food and other benefits, we will encounter peddlers trying to “sell” fabricated information to get food for their families or themselves (Hutton, 2008). The other side of the coin is that with more people around to notice “undue affluence”, there is the increased likelihood of the insurgents identifying and killing our reliable informants. It’s also possible that their murders will be violent to serve as an example for others that they should not help the Coalition Forces.
Conflict of Interest
One big issue is the conflict of interest between the intelligence community and the humanitarian aid community. For example, the Peace Corps prohibits any intelligence veterans into its ranks. While the author was attending a DIA hiring event, there were, what can be described as, strong “anti-Peace Corps” sentiments as it was strongly reiterated that Peace Corps Veterans could not be employed by DIA.
The policy is founded on the premise that it is crucial to the Peace Corps in carrying out its mission that there be a complete and total separation of Peace Corps from the intelligence activities of the United States government, both in reality and appearance. Any semblance of a connection between Peace Corps and the intelligence community would seriously compromise the ability of the Peace Corps to develop and maintain the trust and confidence of the people of the host countries. To insure that there is not the slightest basis for the appearance of any connection between Peace Corps and the intelligence community, the policy contains certain permanent bars. Serious doubts about an applicant's connection with intelligence activities are to be resolved in favor of exclusion.
(Peace Corps, 1984)
This schism makes it difficult to conduct HUMINT operations because the people that establish the most rapport and are in a position to gain the most actionable intelligence are the ones that want to distance themselves as far as possible from this type of activity while the people who live and breathe intelligence are essentially outdone and have to work harder to meet their objectives as they no longer stand out from the rest of the “occupiers” as much as they otherwise would. To put the situation in an economic light, using the principle of supply and demand, having humanitarian aid in the area of operations increases the supply in relation to the demand. Upsetting the ratio deprives the HUMINT element of the monopoly that it would otherwise have over the “human terrain.”
Supporting COIN operations with intelligence requires the analyst to know the indigenous people in a way not required by conventional operations. This human-intelligence dimension involves examining the role that culture, demographics, political support, religion, and ethnicity play. It also necessitates learning about patterns of social networking. (Zeytoonian, 2006) In a counter insurgency, not only the analysts need to understand the people. Every troop on the ground is in a position to make a tactical decision with political ramifications and needs to conduct himself accordingly. This model is best summarized in General Krulak’s concept of the “Strategic Corporal” and the “Three Block War” (Krulak, 1999).
In recent years, the focus on Iraq and now Afghanistan has taken attention away from the conditions in Darfur. Many linguists are being trained in Arabic and now the shift is towards Dari, Pashto and Urdu as we surge in Afghanistan. Arabic will be useful, however, many of these Arabic linguists are finding that they can make considerably more money in the private sector for companies such as Blackwater or KBR and other government agencies like CIA, denying the military access to their skill set. Aside from the fact that we are short on target linguists, in Sudan, there are a number of other languages spoken, to include: Nubian, Ta Bedawie, diverse dialects of Nilotic, Nilo-Hamitic, and Sudanic languages. Chad is no different while French and Arabic are the official languages, Sara is spoken in the south and more than 120 different languages and dialects are spoken throughout the rest of the country. In the Central African Republic, even though French is the official language on paper, the lingua franca and national language is Sangho (Central Intelligence Agency, 2009).
Was this hub helpful to you? If so, Please Click here
REFERENCES
Air Force Institute of Technology. (<2009). Introduction. Retrieved February 10, 2010, from http://www.afit.edu/: http://www.afit.edu/en/docs/CMSR/intelligence_What%20is%20MASINT.pdf
Bhattacharji, P. (2008, April 02). State Sponsors: Sudan . Retrieved January 12, 2010, from Council on Foreign Relations: http://www.cfr.org/publication/9367/state_sponsors.html#p1
Central Intelligence Agency. (2009, December 31). CIA World Factbook. Retrieved January 06, 2010, from https://www.cia.gov/library/publications/the-world-factbook/: https://www.cia.gov/library/publications/the-world-factbook/
Central Intelligence Agency. (2007, October 25). Civil War. Retrieved February 15, 2010, from https://www.cia.gov/kids-page: https://www.cia.gov/kids-page/6-12th-grade/operation-history/civil-war.html
Ford, P. J. (2007). Introduction to Intelligence: A Synthesis of Public Domain Sources. Saverna Park, MD: Erevno Systems Corporation.
GlobalSecurity.org. (2005, April 26). AN/MLQ-40 Prophet. Retrieved June 02, 2010, from GlobalSecurity.org: http://www.globalsecurity.org/intell/systems/prophet.htm
Hanson, S. (2007, January 02). Sudan, Chad, and the Central African Republic . Retrieved January 13, 2010, from Council on Foreign Relations: http://www.cfr.org/publication/12309/
Hillard, E. (2009, January 21). U.S. Africa Command Addresses Africa Union Communication Challenges. Retrieved February 10, 2010, from http://www.army.mil/: http://www.army.mil/-news/2009/01/21/16020-us-africa-command-addresses-africa-union-communications-challenges/
Hutton, L. (2008, December). Spies for hire and information peddlers: A new threat to security in Africa? Retrieved February 12, 2010, from http://www.britannica.com: http://www.britannica.com/bps/additionalcontent/18/35690565/Spies-for-hire-and-information-peddlers-A-new-threat-to-security-in-Africa
Jacobsen, A. (2010, May 05). SIGINT Spy Drone Key to Capturing Shahzad? Retrieved May 05, 2010, from Pajamas Media: http://pajamasmedia.com/blog/sigint-spy-drone-key-to-capturing-shahzad/?singlepage=true
Kilcullen, D. (2006, March 01). Twenty-Eight Articles. Retrieved February 10, 2010, from http://usacac.army.mil: http://usacac.army.mil/cac2/COIN/repository/28_Articles_of_COIN-Kilcullen(Mar06).pdf
Knott, S. (1996). Secret and Sanctioned. New York: Oxford University Press.
Krulak, G. C. (1999, January). The Strategic Corporal: Leadership in the Three Block War. Marines Magazine .
Lefkow, L. (2006, November 09). Eastern Chad: A Spillover of Violence from Darfur. (J. Fowler, Interviewer)
McCullagh, D. (2009, December 17). U.S. was Warned of Predator Drone Hacking. Retrieved February 15, 2010, from http://www.cbsnews.com: http://www.cbsnews.com/blogs/2009/12/17/taking_liberties/entry5988978.shtml
Office of the Coordinator for Counterterrorism. (2007). Country Reports on Terrorism. Washington, D.C. : US Department of State.
Office of the Coordinator for Counterterrorism. (2010, January 19). Foreign Terrorist Organizations . Retrieved January 30, 2010, from http://www.state.gov: http://www.state.gov/s/ct/rls/other/des/123085.htm
Peace Corps. (1984, April 02). MS 611: Eligibility for Peace Corps Employment or Volunteer Service of Applicants with Intelligence Backgrounds. Retrieved February 15, 2010, from http://www.peacecorpsjournals.com: http://www.peacecorpsjournals.com/manual/MS611.html#3.1.--intelligence_activity
Ploch, L. (2008). Africa Command: U.S. Strategic Interests and the Role of the U.S. Military in Africa. Washington, D.C.: Congressional Research Service.
Rotzien, C. (2007). Fighting a Global Insurgency Utilizing Galula’s Counterinsurgency Warfare Theory. Pennsylvania: Army War College.
Stratfor.com. (2008, October 14). Afghanistand-Pakistan Battlespace Border. Retrieved June 15, 2009, from http://www.stratfor.com/analysis/20081014_afghanistan_pakistan_battlespace_border
Woodson, M. S. (2005, October 11). Insurgent Intelligence Gathering. Retrieved February 10, 2010, from Military.com: http://www.military.com/opinion/0,,78499,00.html
Zeytoonian, D. (2006, May 01). INTELLIGENT DESIGN: COIN Operations and Intelligence Collection and Analysis. Retrieved February 10, 2010, from http://www.au.af.mi: http://www.au.af.mil/au/awc/awcgate/milreview/zeytoonian.pdf