Systematic Approach for Investigation
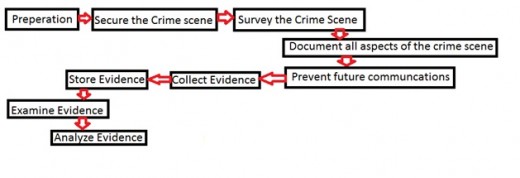
For every investigation, the team of investigators must proceed in a systematic manner. Before an investigation takes place, the team goes through a phase known as the "preparation phase." This phase involves a briefing of the crime and what activities took place, as well as what is at the crime scene. During the preparation phase, an investigator gathers materials that will be necessary to perform a thorough investigation of the crime scene. If a search warrant is necessary, the investigator will obtain one during this phase detailing what they are looking for at the scene of the crime as well as what will be examined. Developing a strategic plan for investigation is also necessary in this phase before the actual investigation occurs. (FBI website, 2000)
Next, the team will arrive at the crime scene and secure the area. The investigators enclose the crime scene perimeter with crime scene tape and guards. Securing the area also involves noting each investigator who enters into the crime scene as an attempt to eliminate the contamination of evidence which may occur. The arriving team must also determine if the area is safe for examination. (FBI website, 2000; pp. 22-23)
Next, the investigators will survey the area and determine what evidence will be collected and viewed during the investigation. The investigators evaluate the crime scene and create a plan to search all of the evidence on the scene. They then evaluate all of the electronics found at the scene including computers, cameras, mobile phones, and other devices to determine what equipment is needed to examine the devices. They will collect the names and statements from all individuals at the scene of the crime. (FBI website, 2000; pp. 22)
Before a thorough investigation takes place, the team of investigators must document all items found at the scene. They most take photographs of the crime scene which cover all areas of the perimeter, and create a hand drawn map of the crime scene indicating where each piece of evidence was placed at the crime scene. When taking each photograph, the investigators must document all items found within each photograph. Every visible aspect of the crime scene should be noted for future evaluations. Recording everything at the crime scene is extremely important for future evaluations including reexamining the crime scene as well as testimony in court. Once the scene is thoroughly documented, the investigation can begin. (FBI website, 2000; pp. 22-23)
Shut down all devices which may interfere with the crime scene investigation. Turn off devices such Bluetooth and the investigators personal radios, mobile devices, and disable all communication on running devices. This is done to prevent future communication actions from recording over the information currently on the device. (USDOJ, 2008; pp. 8-10)
Once all communication is disabled, it is time to collect the evidence at the scene. Because the scenario given is one where the computer is on, it is recommended to create a digital copy of the computer to prevent losing valuable information once the computer is turned off. During the collection process, it is important to continue documenting every piece of evidence as it is collected in order to pick it out in the future for investigation or presentation purposes. If a device is turned off, it can be collected in an evidence container and brought to a secured workshop for evaluation. If an investigator determines it is important to bring the information back to the workshop to evaluate, they must check the device for any malicious software before securing it for evidence. Small storage media devices should be logged and collected for investigation in a work shop. Once all evidence is placed in secure evidence containers, it must be transported to the headquarters location and placed in evidence storage. Some evidence collected may be easily-damaged, so it is important to take every measure possible to secure each piece of evidence and handle each piece with care. (USDOJ, 2008; pp. 8-10)
After all evidence is collected and preserved, it must be examined. This is the point where forensic investigators go through all of the evidence and extract appropriate information for the case. During the phase of examination, it is important to document thoroughly each step taken and all programs and procedures used throughout the process. The analysis of the examination will then take place as thorough review of the technical information. This includes an analysis of the hidden data, extracted files analysis; analyze the timeframe of each file installation, access and use as well as an analysis of the applications used on the device. The analysis report should be so thorough that any investigator can open up the report and perform the exact same process completed and uncover all of the same data and information. (National Institute of Justice, 2004)
References
FBI website. (2000) Crime Scene Investigation: A Guide for Law Enforcement. Retrieved Feb.
11, 2012 from http://www.fbi.gov/about-us/lab/forensic-science-communications/fsc/april2000/twgcsi.pdf
U.S. Department of Justice (2008) Electronic Crime Scene Investigation. Retrieved Feb. 11,
2012 from https://www.ncjrs.gov/pdffiles1/nij/219941.pdf







