The Intelligence Cycle
So how does this whole process work? How do we decide what we need to know before going out and trying to get information on everything? And once we do get whatever relevant information, what do we do with it? How do we know if it’s good enough, after all, there’s no professor to give us a grade; is there?
Well, there’s an order to the chaos. It’s called the Intelligence Cycle. This is the continuous process that determines what we need to know, the acquisition of information, assimilation of data into existing information, and a reassessment of the situation.
The first step of the process is Planning and Direction . This is the tasking phase. Think of it as being assigned a research paper in college. This is where we figure out what we do know, what we need to know and how to go about filling in the gaps. This is where you might decide between going to the library, using Google, or interviewing a person knowledgeable on a subject before you started actually doing your research.
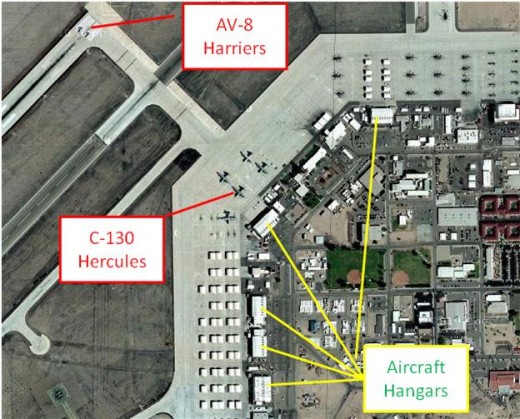
Collection is the second phase. It’s where different intelligence collection platforms are tasked with requirements. Below you’ll see a satellite photograph of a U.S. military base that has an airstrip. Pretend for a while that this is an enemy base. Imagery will use satellites to observe an area of interest and report what is visible. In this case, there are a number of aircraft and an airstrip capable of supporting large aircraft that require a longer runway for takeoff. Imagery analysts will be able to identify the C-130s outside the hangars and the AV-8s (an aircraft unique to the U.S. Marines) on the runway. However, there are rows of parking spaces are covered with tents that prevent overhead observation. HUMINT may be tasked to figure out how many of those spaces are occupied by aircraft and how many pilots are available to operate them. Meanwhile, SIGINT can intercept radio traffic between the air traffic control tower and see who they are talking to and what they’re saying. MASINT (which is essentially an electronic version of All-Source Intelligence) will pick up on the aircraft IFF (identification: Friend/Foe) beacon and can pick up on things such as their forward looking infrared radar (FLIR) when it’s active further revealing individual aircraft capabilities. Open source would look for any public information about the area of interest. In this case, the map was acquired from open source and included number of links that provide more information about the base. This particular base has a webpage identifying the units stationed on the base offering insight into the amount of force that can be projected from this location. For your reference, they are below the image.
Satellite Imagery
Open source links
http://www.3maw.usmc.mil/external/3dmaw/
Official Page for the 3rd Marine Aircraft Wing
http://www.globalsecurity.org/military/facility/yuma.htm
Provides some history and current mission & capabilities
http://themilitaryzone.com/bases/mcas_yuma.html
Provides history and contemporary information on base size and logistics
As the name says, Processing is where the collected information is processed and organized. This includes things like translating all those tapes Bin Laden likes to send. Also translation of news broadcasts or magazine articles and other open source which will include things beyond the literal translation and include such details as connotations of such as the guy who threw his shows at Bush. It wasn’t just a simple assault as it would have been if it were an American, it was a political and cultural insult as well. The same applied to Iraqis slapping statues of Saddam with their sandals. For SIGINT, saying that certain frequencies were in use doesn’t tell the layperson as much as saying that those frequencies are typically associated with certain equipment used by a specific group that has. And if they intercept messages a transcript may be included. HUMINT may find that the word “watermelon” means bomb and “market” refers to an arms dealer’s house. This location will be depicted on a map or satellite photograph provided by IMINT.
Analysis and production is the heart of the cycle. It’s where all the information is compiled and pieced together. So at the tactical level, when SIGINT intercepts a snippet saying take the watermelons to the market , the analysts will know that there is a weapons delivery taking place. At the operational level, it’s more of looking for trends in everything that we’ve acquired and try to figure out how worried we need to be and how long before we find out right we were. We’ll take a look at what’s causing the situation that we’re looking at, what possible alternate futures may occur and the impact of each of them. At the operational and strategic level you’re more likely to see PMESII analysis. It assesses and analyzes the political, military economic, social, infrastructure and information aspects of an area and can be used as a starting point to project the impact after a given course of action or hypothetical alternate future.
Dissemination is the final stage in which the requested information is reported to the customer who initiated the request. Basically the research paper is turned in. Once they get this they will have a clearer picture of what’s going on. Moving forward from that point, they develop additional intelligence requirements and the cycle starts all over again. In this case, they may want to know more about the base itself such as where the fuel depot is located if they want to keep the aircraft from being able to fly without completely destroying them. Or perhaps they may want to look into the effect of destroying the runway. They’d find that since most of the aircraft on this base are VSTOL capability, it wouldn’t stop combat operations. After this, the cycle would continue until they found all the information they wanted and were able to develop a course of action to achieve their objective.
Was this hub helpful to you? If so, Please Click here
Analysis is possibly the most important part of the Intelligence Cycle









