Apple IOS Security Versus Android Mobile Security

When in October 2013, Google executive Chairman Eric Schmidt claimed that Android operating system trounced Apple mobile security, a degree of excitement swept across the tech industry and once again the question of mobile security was top of the news. The excitement was soon forgotten and only peaked at the beginning of 2014.
This time around it was Apple’s own Phil Schiller, who tweeted a Cisco 2014 mobile Security report on 21st January 2014, highlighting security glitches in Google’s Android operating system.
According to the CISCO mobile security report, over 99% of mobile malware attacks were targeted towards Android operating system.
2014 promised to deliver even more in the world of mobile phones, phablets, tablets and a host of wearable devices. The huge numbers meant that as years rolled by mobile security was paramount again, as malware coders were at work figuring ways to penetrate security loopholes in Google Android, Apple IOS, Microsoft Windows and other mobile operating systems.
Is Apple IOS More Secure than Google Android?
This brings us back to the initial question: Is Apple IOS more secure than Android OS or is it all empty talk? The correct answer is actually YES and NO, but in more ways than one, user indulgence rather than operating system fault contributes to vulnerabilities in Android variants.
In order to fight security breaches, Google’s Android operates in a sandbox environment, an example of a secluded layer where very little of the system can be tampered with. Still, the user, through app installation, knowingly or unknowingly, can violate sand box integrity by enabling access to system files.
Unlike Google, desktop security has always been paramount for Apple and it is no wonder that IOS mobile security too has been taken seriously at Cupertino. Mac operating system is known for its resistance against malware, though much of it owes to the limited number of Mac users, in comparison to windows operating system, for example, which is literally everywhere.
On the other hand, Google’s minimal know-how in the field of traditional desktop operating systems should be the contributing factor to the apparent vulnerabilities that haunt Android OS. But it is safe to assume that Google is going through the learning process fairly, a process that should take more than only one day!
It is no surprise then that Google is willing to reward individuals who identify and forward Android security flaws to its technical team. And to be fair to the tech firm, its operating system has is receiving massive adoption by cell phone manufacturers around the world, and it is next to impossible to harmonize OS perfection in such glaring diversity.
5 Reasons Why Apple IOS Could Be More Secure
Below I illustrate five paramount but definitely not all reasons which make Apple IOS much more secure than Google's Android.
1. Apple Makes and Owns Both Hardware and Software
Unlike most of its competitors, Apple is privileged to make both hardware and software for its devices. This gives the company comparative advantage over competitors when it comes to ensuring particular levels of mobile security.
Harmonization of hardware and software allows for strict control of operability across layers and resources of hardware and software.
Right from the initial iDevice boot, baseband verification, in-house and third party apps validation, Apple is capable of analysing and ensuring that only permitted software run in IOS devices, and certain privileges are possible while others are not.
File encryption in iPhones and iPads are handled by specialized software and hardware engines called AES and SHA-1. In Addition, AES works closely with iPhone unique ID(UID) and device group ID(GID) to make software encryption efficient. Thus, snoop attempts from without, to read encrypted iPhone data directly is next to impossible.
To complement this, Apple invests the highest attention in the IOS kernel and overall IOS security architecture in order to avail users trusted security while the iPhone or iPad is in use.
Unfortunately for Android operating system, hardware manufacturer teams are a little detached from the software departments, and attempts to ensure high level compatibility guidelines may not always be achieved.
2. Apple IOS Is Not Open Source
IOS is not open source while Android is. Android accepts feature and security contributions from enthusiasts which permit upgrades and all sorts of betterment to the initial operating system.
It is important to emphasise that some of these contributions are amazing and is what makes every new version of Android even exciting. And some or most of these source code enhancements in Android actually find their way into Apple IOS as jailbreak features.
The biggest drawback with community based coding contributions is that they do not always follow all the stringent ‘vetting’ that is the hallmark on non open applications.
On the other hand skilled contributors tend to code pre-root software which may give third party app access to system software, lending them ready for various modifications.
Therefore, with or without intending, multi user codes can easily get exploited by hackers and thus become source of system vulnerabilities.
3. IOS App Installation Is "Only" Possible Via iTunes
Apple also controls the manner in which apps can be installed in iPhone and iPads. Of course apps can be installed through third party applications and on jailbroken iPhones, but then you always jailbreak your iPhone at your own risk!
As a rule, apps can only get installed via iTunes in the computer and within the App Store app in the iPhone or iPad.
Android actually makes it possible to install third party apps right from within the operating system. The process may involve or not rooting, which of course grants user and apps direct access to system files. This is possible within the official Android firmware.
Direct installation of third party apps is particularly tempting even to the ordinary user owing to availability and ease of use.
Of course Google continues to apply strict measures, including rigorous in house scanning in order to root out rogue apps. But not all malicious apps will see the exit.
Aside, file transfer between an IOS device and the computer can only be done via iTunes. Of course third party also makes this possible particularly on jailbroken iPhones. Android meanwhile, allows for direct transfer between the cell phone and the computer. The chance that malware can move between the two devices increases significantly.
Aside from app installation, Apple ensures strict guidelines for app development making it hard for rogue apps to feature on App Store. Stringent minimum requirements apply before any app is even considered to feature.
4. Android Fragmentation Vs Massive Adoption of New Apple IOS Firmware
The nightmare of operating system fragmentation continues to bedevil Google Android. According to Google’s own Android stats of January 2014, Android 4.1.x aka Jelly Bean still remain the most popular OS, for it is installed in about 40% of all Android based smartphones.
Now this is security nightmare for Google which has tried all in its power to make users upgrade to new operating systems and versions. Every other upgrade and new OS is an attempt not only to introduce improvements but also to patch security vulnerabilities that progressively arise due to age.
On the other hand, new Apple IOS 7x continue to garner massive adoption in the shorten time. By January 2014, over 80% of active IOS users had upgraded to IOS 7x firmware. Massive adoption of new operating system is good for Apple since it means the company can always trust that security patches receive massive adoption right away.
Apple IOS
| Year of release
| Users as of Jan 2014
| Google Android
| Year of release
| Users as of Jan 2014
|
|---|---|---|---|---|---|
IOS 5
| June 2009
| Less than 3%
| |||
Gingerbread
| December 2010
| 21.1%
| |||
Sandwich
| October 20111
| 16.9%
| |||
IOS 6
| September 2012
| 17%
| Jelly Bean
| July 2012
| 35.9%
|
IOS 7
| September 2013
| 80%
| Kit Kat
| October 2013
| 1.4%
|
Illustration of user adoption of IOS and Android upgrades as of January 2014
Another factor that enables immediate adoption of new IOS firmware owes to Apple not signing old IOS firmware only 24 hours after a new firmware is launched.
This page illustrates Apple signing of old and new IOS firmware for old and new IOS devices.
5. Apple Activation Lock and Remote Wipe
In January 2014, the password management company Dashlane released via ArseTechnica a comprehensive study of password security behaviour of 100 e-commerce companies and awarded Apple 100% mark for exemplary password management.
In line with its improving security policies, Apple released IOS 7 with strict authentication requirements to secure iPhone data and protect against theft.
Activation Lock:
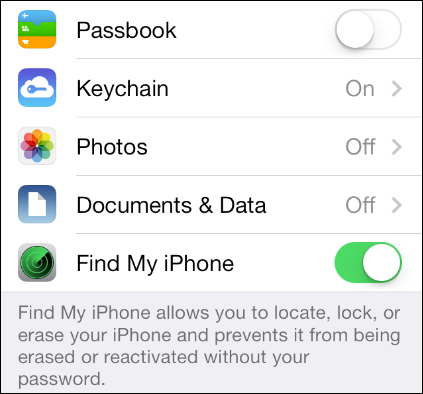
With IOS 7, Apple implemented a security feature called Activation Lock. Linked closely with Find My iPhone, Activation Lock makes it next to impossible to steal and use an iPhone or iPad running IOS 7x. Once Find My iPhone is activated in iCloud, only the authenticated Apple ID password can be used to restore or re-activate the IOS 7 device.
This means that a stolen IOS 7 device usually becomes a worthless piece of electronic, if initially locked with a lock screen pass-code\TouchID and has Find My iPhone activated.
In addition, the iPhone owner can as well implement the nuke option to remotely erase iPhone data. This option is particularly important if the iPhone does not have a lock screen pass-code installed.
Apple security Vs Android security: Which is better?
© 2014 Alfred Amuno