Apple versus the FBI and soon the world

In the world of technology, security of data is one of the most challenging and important tasks at every level. From the individual to the IT executives at multinational firms, data-security can be the difference between success and failure. Data security mitigates risk, enables effective collaboration between peers, guards against theft of proprietary processes, products, and strategies, and provides an assurance against piracy, alteration, or sabotage of confidential files. With handheld devices leapfrogging into a dominant role as the most preferred piece of technology to transfer and store data, an effective security strategy must begin with your choice of handheld device. One of the most sought after handheld devices is the iPhone by Apple for its security as well as many other features.
Apple
Apple has committed to users of its iPhone products, “The most personal technology must also be the most private.” This statement is boldly presented front and center on Apple’s website. They’ve created a system that is highly secure and they regularly update protocols to insure they stay current and effective. Owners of Apple products are loyal and many cite this level of privacy as a big reason why they stay with Apple products. Apple also states, again in big bold letters that, “We believe security shouldn’t come at the expense of individual privacy.” Apple also shares its policies on how requests for information are handled and their adherence to the law. On Apple devices running iOS 8 and later versions, the user’s personal data is placed under the protection of their passcode which is not stored anywhere at Apple. This means that Apple cannot perform data extraction in response to government search warrants because the files to be extracted are protected by an encryption key tied to that passcode. Apple seems to be quite transparent in what the can, cannot, and will do, which includes never allowing government access to Apple servers and the flat out refusal to “hack” their own technology to create a backdoor to break into their products.

The FBI angle
The public fight between Apple and the United States Government started when the FBI approached Apple about cracking the security on an iPhone which was previously owned by an Islamic terrorist who had been killed after executing 14 and wounding 22 at a California public benefit corporation. Apple does not have an unlock protocol for its products nor would they “hack” their own security to allow the government to have access to the phone’s memory. Senior leadership at Apple said any such attempt would undermine security and privacy for all customers. The FBI on the other hand says Apple is just protecting its brand and should be compelled to meet their request and proceeded to get a court order to force Apple’s hand.

All Writ's Act
The FBI is basing their case on a 227 year old law which was signed by none other than George Washington called the All Writ’s Act which is a Federal Stature which states that:
(a) The Supreme Court and all courts established by Act of Congress may issue all writs necessary or appropriate in aid of their respective jurisdictions and agreeable to the usages and principles of law.
(b) An alternative writ or rule nisi may be issued by a justice or judge of a court which has jurisdiction.
Application of the All Writs Act requires the fulfillment of four conditions:
The absence of alternative remedies—the act is only applicable when other judicial tools are not available.
An independent basis for jurisdiction—the act authorizes writs in aid of jurisdiction, but does not in itself create any federal subject-matter jurisdiction.
Necessary or appropriate in aid of jurisdiction—the writ must be necessary or appropriate to the particular case.
Usages and principles of law—the statute requires courts to issue writs "agreeable to the usages and principles of law."
Since everyone isn’t a legal scholar, it’s necessary to translate this into terms that can be understood by all. Specifically, this law gives power to the Federal Government to force people or companies to do something as long as it’s not in violation of the law. A Writ is an older term that means a formal order. This vague law certainly had an impact in the early days of the nation but currently seems contradictory to our basic freedoms. Yet it has been used often by the Federal Government, albeit quietly to engage in spying on the American public. In 1977 it was used to force phone companies to help set up devices that record all numbers called from a specific phone line. In 1999, the Wireless Communications and Public Safety Act also utilized it to require all cellphone providers to be able to geolocate their customers’ phones. In 2005 a federal judge ruled against it being used to force a phone company to allow real-time tracking of a phone without a warrant.

Apple Cooperation doesn't satisfy FBI
Despite the fact that Apple was working with the FBI and quickly provided them with everything they had backed up in their cloud data storage, the agency wanted more. They demanded that Apple crack the phone itself so they can see what else is on it even though there is no evidence that anything else is on the phone. The court order specifically asks Apple to create a new, custom version of their operating system that will run only on that iPhone, but one that will make three changes to the software. Collectively the first two would disable the auto-wipe function and the delay the time limits on how quickly new passcodes can be entered. The court also asks Apple to add a way to attach a cable or wirelessly connect to the iPhone so the FBI can automatically enter passcodes so they can use a supercomputer to bombard the phone with passcode guesses until it finds the right one. The iPhone has security protocols built in which automatically erase the phone after 10 failed password attempts plus entering a wrong code activates a delay in how soon you can try to re-enter it.
Engineers at Apple could potentially do the requested task with a huge outlay of time and manpower, however that's not the point, says Apple's CEO Tim Cook. He argues that Apple can't just bypass their protections for a single phone and still expect all other phones to stay safe and secure. "Once created, the technique could be used over and over again, on any number of devices," Cook wrote in an open letter to customers earlier this week. "In the physical world, it would be the equivalent of a master key, capable of opening hundreds of millions of locks." To those of us on the outside observing, it seems like another government overreach to spy on citizens.

Enter the French
The fight has escalated and spread across the Atlantic, with French lawmakers working on a policy that will impose prison time and hefty penalties on IT executives who refuse to give them access to encrypted data during a terrorist investigation. Their version of the rule would force technology manufacturers to provide the information at any cost by any means necessary. This forced cooperation is a disgraceful display of strong arm tactics and government overreach. At the moment there are no confirmed sources that tie the actions in France with the actions taken by the FBI, but many are already speculating that global governmental cooperation is just emerging that will try to get the upper hand on manufacturers who produce secure products.

Globalists and Questionable Polling
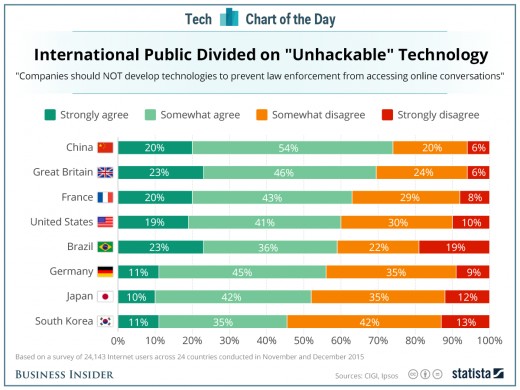
In another emerging story, a recent report is being used as a tool to support the overreach being demonstrated. According to a survey conducted by the Center for International Governance Innovation, the majority of people in several big countries believe that companies should not develop technologies to prevent law enforcement from accessing online conversations. This group is a think tank for global governance with a core belief that global governance will benefit everyone. It sounds an awful lot like a “New World Order” group trying to wrest control of the planet from individual countries and grant those powers to its own membership. Understanding this fact is importance for how the so-called survey results are to be interpreted. Notice that the report doesn’t say data security but online conversations, which suggest e-mail, phone, or text messages.
It would appear that in order to win over public support that these globalists are creating and spinning favorable polling to support the case of the FBI and now with France joining in will push even harder to get what they want. Yet, the opposition is also heating up with activist groups taking the side of Apple and the right to privacy. Many minority groups who have felt they were under illegal surveillance for years are making their voices heard. The hashtag #DontHackApple is prevalent on Twitter in support of privacy. Protesters who own iPhones have had them seized by police who were unable to access their private information without a warrant are supporting Apple. If Apple were to capitulate, then would be criminals and terrorists would simply switch to another product, rendering the entire series of events moot.
Summary
This battle is sure to go on until it reaches the highest courts in the land, and early odds are that Apple will emerge victorious. There is more at stake than just the iPhone battle. Are we as American’s going to allow our government to force any company or citizen to do whatever they feel is needed, just because they say so? Where do our freedoms end and tyranny begin? Does freedom of speech also apply to data? At this point in time, no one can say where the case will end up, only that it will be highly visible and many more factions will weigh in.









