Have You Been Socially Engineered? Did You Succumb?
Social Engineering in the internet age
As the internet has become all-pervading, the average person is at the receiving end of a few attempts of social engineering each day to provide some information that they did not intend giving out, or to carry out some actions against their will. However, not all of these are successful. There are guardians on the internet – whether it is the mail provider,the ISP (Internet Services Provider), the cloud storage provider. And these guardians help ward off some these disasters – they find their security reputation essential to maintain to continue in business and are also regulated by most national governments to provide filters and checkpoints for their customers.
Unfortunately, there are the few cases where people actually succumb to these social engineering attempts. Due to massive strides in automation the social engineer is happy to live with the thousands of failures to secure one successful attack.
We primarily have to educate ourselves about the newer types of attacks and be very careful of the information that we publish on the internet. Towards this, I am describing here a few of the recent types of social engineering attacks and suggesting mechanisms of how we can protect ourselves against them.
Social media sites

Quizzes on Facebook and other social media sites
This is a time-tested technique, that appears every now and then. Most quizzes are engineered to:
- provide additional information about individuals for targeting – maybe leading to answering the “what is your mother’s middle name” type of security questions that are used to reset passwords
- provide data on a targeted demographic for marketing – when you told the quizzer that the last five concerts you went to were all Metallica, he gets an understanding of what memorabilia to offer you and also possibly when your house will be empty (when you go to their next concert) in the near future
The Better Business Bureau has put out a recent advisory about quizzes, indicating that this is an extremely current issue. However, this blog from 2015 provides more insight, it includes the perspective of the company that created the quiz. The danger of that particular quiz app under discussion was that it requested disclosure of:
Name, profile picture, age, sex, birthday, and other public info
-
Entire friend list
-
Everything you’ve ever posted on your time-line
-
All of your photos and photos you’re tagged in
-
Education history
-
Hometown and current city
-
Everything you’ve ever liked
-
IP address
-
Info about the device you’re using including browser and language
The list of disclosures was subsequently reduced once the media spotlight came on.
How do I protect myself?
- Check your privacy settings and reduce the level of information available to third parties on your favorite social network – this means that the affiliated websites and applications cannot access your data. This also means that you may not be able to use some of the third party websites/applications, so if was your lifetime ambition to do that quiz, you may have to give up your privacy.
- Get out of lifetime ambitions to answer such quizzes
Are social media quizzes popular?
view quiz statisticsFake online stores
Internet shopping is here to stay. I personally love the fact that I can buy some of my essentials on-line – especially when it is a point purchase that I would have to travel some distance to specific stores for the purchase. A case in point, I recently bought a bathroom appliance off Amazon to replace the previous one which had broken down. The original purchase was done in the last decade at a brick-and-mortar store about ten kilometers away from my home. I actually beamed at the delivery person when the replacement arrived, really happy that I saved the travel time for a good quality item. Now that my appliance is installed, it is what I consider a good buy.
But I’m digressing: the internet abounds in fake stores that either do not deliver anything after an upfront payment, or provide a cheap substitute to the item you ordered. Most country regulators keep warning about such scamsters, this 2017 article from Australia includes a nice graphic reproduced below:
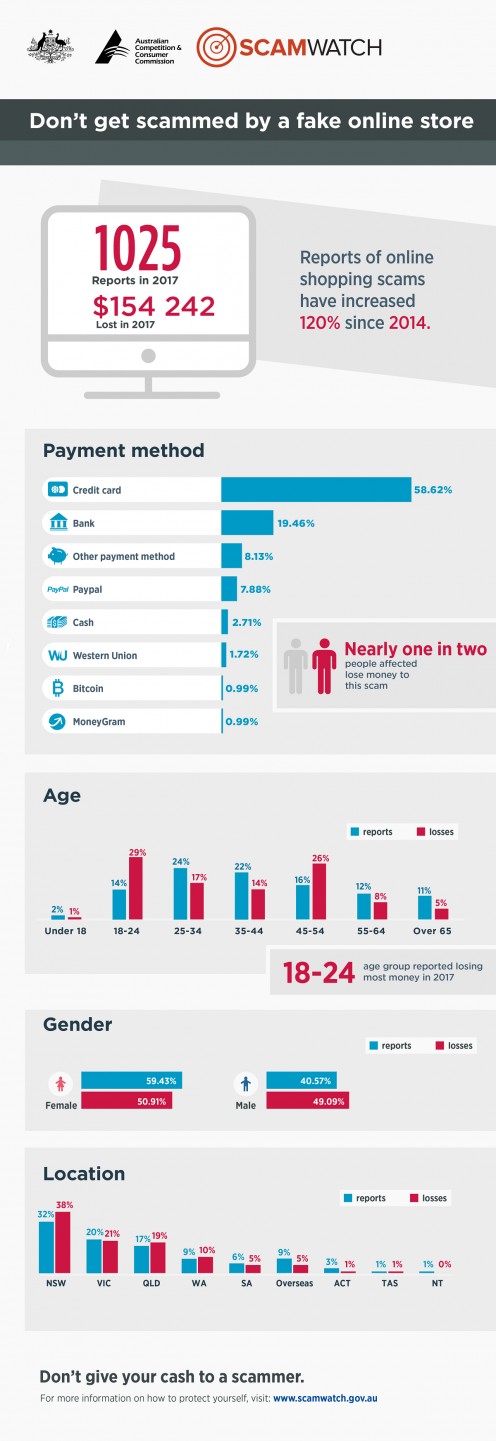
How do I protect myself?
Use only well-known shopping sites. If you are tempted to buy an out-of-the-world product from an unknown site, do the following before you dole out your cash
- Check your local in-country scam watch website – the link for Australia is above, the Better Business Bureau works for some geographies including US. They may have an inquiry process to check if the site is legitimate or they may have a blacklist put out which you can check for the name
- Check for spelling mistakes and other language errors – many scam sites have some kind of errors showing up
- Check if your out-of-the-world product is available via a known site at an acceptable price
Wi-fi Hotspots
Most of us are suckers for free wi-fi – whether it is at the airport or at your favorite coffee shop. It has also become so ubiquitous that almost every business offers it. While the genuine service can be trusted (to a certain extent), there is a possibility of an “evil twin” attack where a scammer provides an additional hot-spot with a similar sounding name and potentially using the same credentials as the business.

What we should be aware of is that w-ifi is a medium unlike the previous wired access networks: it is fairly easy to tap into a wireless network with the right device (nothing too expensive). And in a hot-spot where all users are sharing the same published security credentials, it is quite simple to get access to all data over the network.
Most times we are safe, all legitimate businesses provide encrypted sessions over SSL(Secure Sockets Layer - denoted by the image of the lock on most web browsers). The eavesdropper just gets a bunch of gibberish which is not easy to decrypt. However, some of the apps are just as secure as the writer made them to be, so there could be a security hole that allows access to your data. The OWASP (Open Web Application Security Project) publishes a list of top 10 risks for mobile applications and it lists improper communication and improper authentication at numbers 3 and 4 in its last publication in 2016.
How do I protect myself?
-
Limit your financial transactions done in any public wi-fi network – do you really have to transfer money from your bank account to that third party at this instant? Can it wait until you are safely back home?
-
Be wary of social media updates – can uploading that goofy photo of you at the airport shop be that urgent?
-
Do not set your mobile WLAN (wireless Local Access Network) to auto-connect to open hot-spots
-
If you require your mobile phone to entertain you while you wait, can you do it with downloaded content or games and switch your WLAN off?
-
Read a book
Old-fashioned email phishing
We should be thankful for our spam filters that weed out most of the unwanted stuff these days, but one can become over-zealous in filtering. I operate on the principle that most of the non-personal mail is spam and am quick to filter them out. However, I do have to get into my spam folder on a regular basis and see if I have to declassify some of them. As an example, one of my insurance companies was mailing me regularly to get me to download their new app and when I received their third mail, they earned a place of pride in my spam folder. This resulted in my annual policy update also going into the spam folder and I had to subsequently rescue it.

There are enough websites that provide examples of different phishing scams, however, there is a certain sophistication coming into the attacks to even fool savvy users as was evidenced in 2017 by this Gmail phishing scam. Also, previous scams are being resurrected into “spear phishing” campaigns making them specific to certain subsets of audiences, like a targeted advance fees fraud letter .
How do I protect myself?
-
Check all fields of unexpected mails – there are some suspicious giveaways like the actual sender name, whether the addressee is in BCC or in the To field
-
Never click on a link from an email – assuming that the correspondence is from a personal or business contact, go back to your bookmarks or your favorite search engine and get to your contact’s site in the usual way. If it is not a contact, do you want to reach out to them at all?
Mobile malware

A lot has been written and said about using mobile phones responsibly, talking of avoiding indiscriminate app downloads – especially from unknown sources. Both Apple and Google have screening policies on their app store/play store with Apple having more stringent screening criteria. Both also run bug bounty programs, in the hopes that the intrepid hacker will submit the issue to them allowing fixes to be deployed quickly. However, malware attacks are reported on both platforms, although the volumes on android are higher. Just a sample of recent reports:
However, an alarming trend over the last couple of years is mobiles coming pre-installed with malware which has entered in through the supply chain – the hapless user cannot even be blamed for downloading the malware through an app.
With the mobile internet users increasing exponentially, it is hardly unexpected that the current battlefield between users and hackers is the mobile domain. Also, considering that a reasonable proportion of the mobile users are first time internet users, it makes them vulnerable to social attacks that have far reaching consequences.
How do I protect myself?
-
Build awareness – use your favorite security related website to keep track of attacks. There will be patches released for your mobile OS by the vendor for any serious issues that can be installed.
-
Use a malware detector and scan your device at regular intervals – there are a few free options available. Note that you have update your malware detector as well, and be open to the possibility that the detector may be hacked.
-
Do not download applications indiscriminately. Periodically purge your mobile of unwanted apps.
-
Be aware of “normal” working mechanisms of your mobile – response speed, available memory etc. If you see abnormal behavior, take action – it could be sending a query to a group focused on your mobile platform, talking to a local mobile “expert”. In the worst case, be prepared to reset your mobile to factory defaults and start again – this means that your data backups should be appropriately available for loading.
Whatsapp scams

Of all the apps available on mobile, whatsapp is something that I single out for the simple reason that everyone and their grandmother uses it. It is one of the most effective tools of group communication seen in recent times with the result that the general public vies to cross post what they heard one group into another.
The scamsters are of course, quick to use this and send out messages with included redirects to unsafe websites. They also use ingenuity and contextually make a user feel that the message is genuine – a case in point is a recent message circulated in India that mimics offers made last year by a disruptive ISP. A fairly detailed analysis of the scam demonstrates that the intent seems to be installing a third party app (which could potentially be a bot) and recruiting new victims into the scam.
These scams are similar to the traditional phishing scams, only that the attack vector moves from email to whatsapp. And given the smaller form factor of mobiles, as well as potential naiveté of new users, the scams thrive and multiply. Also, related to the form factor, there are various URL masking techniques that the savvy scam programmer may use in their scripts, which results in you reaching a different website than what you intended. This can be done legally with a URL shortener (seemingly originated to conserve space on web-pages) which redirect users to actual sites, but also intentionally mis-directing via scripts.

How do I protect myself?
-
As with the phishing and mobile scams, do not comply easily with clicking on app downloads or visiting unknown websites.
-
More importantly, do not propagate the scam – any message asking to be forwarded to ten of your best friends does not deserve immediate reposting onto your favorite whatsapp groups.
-
All of the points about protection against mobile scams would apply.
The brave new world – Internet of Things (IOT)
The Internet of Things has been in the making over the last decade and has seen increased deployment in recent times. Unfortunately, this also increases the attack domain for the hacker to anything that can be controlled via the internet through an application.
Recently, a friend demonstrated to me the latest water metering app being used at their apartment complex – with smart water meters installed at all water ingress pipelines for each apartment, the consumption data was being stored and every apartment user could check heir mobile app on a daily basis for real-time consumption amounts and the corresponding charges for that month. The intent was laudable, with graphs available of individual consumption vs average consumption, peer-pressure could drive down usage for the remainder of the month; also it was a pay-as-you-use model as against the flat-rate model that has been used in my tech-averse apartment for years. Imagine if this water meter could be hacked externally to change the records for specific users. Even worse, if there was an actual control from the meter to turn off water (apparently this is common, to eliminate wastage), there is a possibility of a malicious hacker holding the apartment water supply hostage demanding a payment.
Before dismissing the idea as fanciful, if we review this from the perspective of the technology involved, it is not too different from the ransomware attacks that hijacked data in the recent past asking for crypto-currency payments to release data. But imagine the impact of losing your water supply.
IOT and the need for security in IOT networks is recurring theme – the trade-off being that when we want to monitor and control every small device, we want to keep the features on the control software minimal.
Also consider the fact that all of the malware attacks on mobiles can very well be replicated in the IOT domain. Some recent examples include:
Given the fact that IOT security is relatively nascent area, most security vendors are at the forefront and are re-purposing existing solutions to include specifics for IOT, as well.
How do I protect myself?
-
Not much for the individual at this point, the topic is being focused by vendors and standardization bodies
-
Responsible usage of any IOT device (following appropriately published upgrade cycles) and their control application – do you really want to check out the water meter from that insecure open wireless hot-spot?
In conclusion
Social engineering has always been around – from the door to door salesman conning the stay-at-home mom to buy encyclopedias in the last century (and not dispatching said encyclopedias after banking the advance) to the recent IOT and mobile attacks. The attempt is always to get the victim to do something they never intended – provide data, recruit more victims, provide funds.
Educating ourselves, shrouding ourselves in healthy scepticism and responsibly using the tools and networks available to us is key to fighting this menace.
If it sounds too good to be true, it probably is
— The Better Business Bureau, originally attribution from the 1960s.© 2018 Saisree Subramanian







