- HubPages»
- Technology»
- Internet & the Web»
- Viruses, Spyware & Internet Security
Network Security and Some Hot Research Topics in Network Security
Network Security


Network Security and Some Hot research in Network Security
NETWORK SECURITY:
The three primary goals of network security which are confidentiality, integrity and availability can be achieved by using firewalls. Firewalls provide security by applying a security policy to arriving packets. A policy is a list of rules which define an action to perform on matching packets, such as accept or deny. Determining the appropriate action is typically done in a first-match fashion, dictated by the first matching rule appearing in the policy and the time required to process packets increases as policies grow larger and more complex So Network firewalls must continually improve their performance to meet increasing network speeds, traffic volumes, and Quality of Service (QoS) demands. Unfortunately, firewalls often have more capabilities than standard networking devices, and as a result the performance of these security devices lags behind. Furthermore, computer networks grow not only in speed, but also in size, resulting in convoluted security policies that take longer to apply to each packet.
When a security solution cannot keep pace with the speed of incoming data, it either allows packets through without inspection or places incoming packets into a growing queue, thus becoming vulnerable to Denial of Service (DoS) attacks. With either of these possibilities, even a network with a perfect firewall policy (short in length and optimally ordered is susceptible to attacks resulting in prolonged delays, data loss, or both, and it is for this reason that a new firewall architecture is necessary. Parallel firewall designs provide a low latency solution, scale-able to increasing network speeds. Unlike a traditional single firewall, the parallel design consists of an array of firewalls, each performing a portion of the work that a single firewall performed. As network speeds increase, the additional load is distributed across the array, providing a solution that can be implemented using standard hardware. The firewall that will be discussed is Microsoft firewall which called Internet Security and Acceleration firewall (ISA). In this paper a standalone (ISA) and parallel (ISA) will be discussed and tested in different scenarios and their effect on network performance will be calculated. In this paper integrations will be applied with firewalls like integrate an antivirus with firewall to work as a gateway antivirus to scan every traffic which pass through the firewall another monitor program will be added to monitor the sessions that are established through the firewall, an integrated program which split or distribute the bandwidth to users will be added also and here the Microsoft firewall will have the responsibility to establish VPN connections. Therefore lots of test will be done to examine the performance of Microsoft firewall when it is in standalone and when using parallel Microsoft firewalls and a proposal will be presented to enhance the Microsoft firewall performance and this will happen by integration between Cisco and Microsoft products.
-Microsoft Parallel Firewall
Microsoft parallel firewall has another name called Microsoft Internet Security and Acceleration (ISA) integrated with Network Load Balance (NLB) here in this thesis ISA 2006 integrated with NLB will be used. Network Load Balancing (NLB) enables all cluster hosts on a single subnet to concurrently detect incoming network traffic for the cluster Internet Protocol (IP) addresses. On each cluster host, the NLB driver acts as a filter between the network adapter driver and the TCP/IP stack to distribute the traffic across the hosts. ISA Server takes over at this point, enabling NLB in complex deployment scenarios, including virtual private networking, Cache Array Routing Protocol (CARP), and Firewall Client. By enabling integrated NLB on an array of ISA Server firewalls, the framework will be established for NLB configuration at the network level. That is, ISA Server load balances traffic on a per-network basis. After enable NLB on the specific networks that wanted to be load balanced, ISA Server determines the network adapter that will be used for that network. If there is more than one network adapter available, ISA Server selects the network adapter based on name in alphabetical order. ISA Server performs stateful inspection on all traffic. For this reason, ISA Server works with Windows NLB to ensure that incoming and outgoing traffic for each session is handled by the same array member. This is important, because this enables ISA Server to perform state-ful inspection on the traffic.
When NLB is configured for a network, at least one virtual IP address must be specified for the network. With NLB integration enabled, ISA Server modifies both the network properties and the TCP/IP properties of the network adapter. Using ISA Server Management, more than one virtual IP address can be configured for each load balanced network. In some scenarios, such as NLB publishing scenarios, multiple virtual IP addresses may be used and all the traffic will pass through firewalls using this virtual IP (VIP).
-Extra Functions for Microsoft Firewall
Many integrated software will be added to Microsoft firewall (ISA) like Virtual Private Network (VPN), antivirus software to examine the incoming traffic before being downloaded, bandwidth splitter software to distribute the bandwidth to all of authenticated users. After those integrations the test will be done by using different scenarios and topologies to examine the performance of Microsoft firewalls.
-Some Experimental Technique
The test will be done by using Microsoft firewall standalone and parallel all of the firewall will have constant number of 3000 firewall policy and all of them have Antivirus integration, monitor integration and bandwidth splitter integration. Many scenarios will be tested as following:-
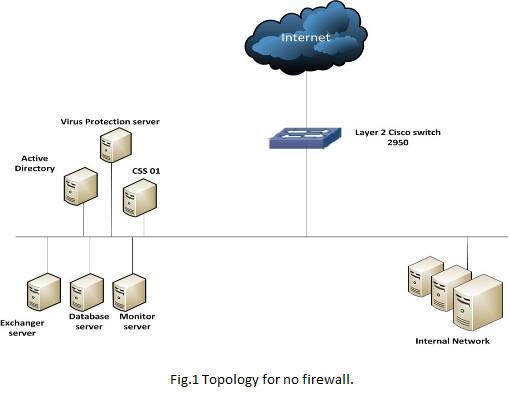
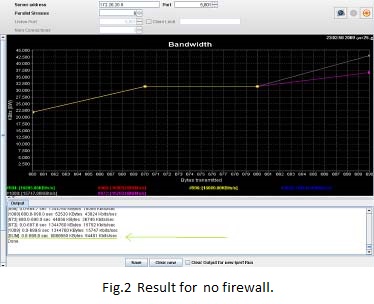
1. Without Firewall
There is no firewall on network, so there is only 2950 switch to connect servers, then generation of the traffic directly from source to destination will be done. Fig 1 shows transmissions of ( 8068560 Kbytes ) In ( 699.6 sec ) are done and the bandwidth usage is 94481 Kbits/sec.
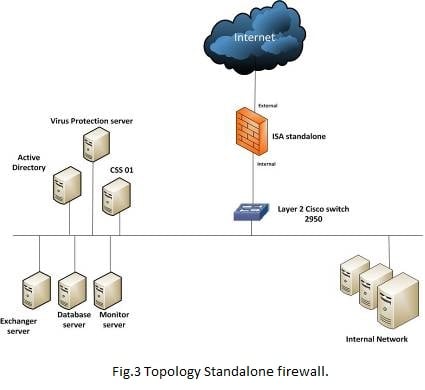
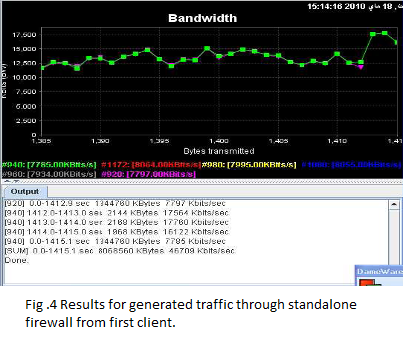
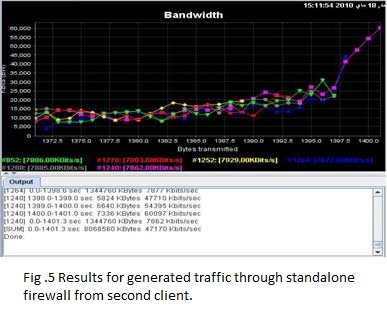
2. Standalone Firewall without VPN
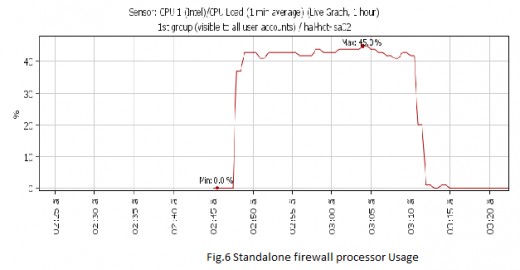
Using only one single firewall without VPN and generate the same traffic but here it will pass first through the firewall going to the receiver servers and then the results will be as Fig 4 shows Results for generated traffic through standalone firewall from first client, transmissions of ( 8068560 Kbytes ) In ( 1415.1 sec ) are done, the bandwidth usage is 48121 Kbits/sec and Fig 5 shows Results for generated traffic through standalone firewall from second client, transmissions of ( 8068560 Kbytes ) In ( 1401.3 sec) are done, the bandwidth usage is 48121 Kbits/sec. Fig 6 shows processor Usage for Standalone firewall which equal 45%.
3. Standalone firewall With VPN
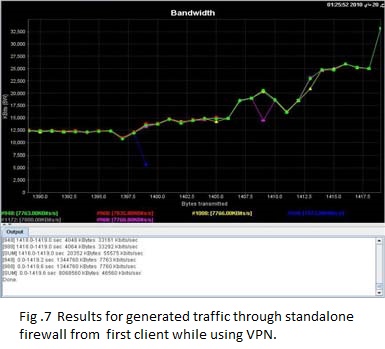
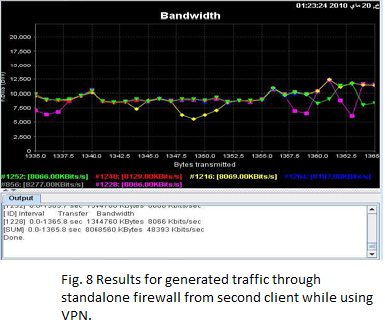
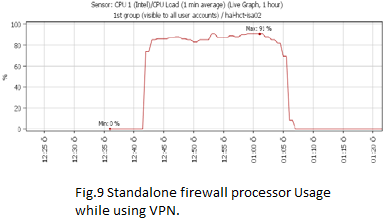
Using only one single firewall with VPN and generate the same traffic. Fig 7 shows Results for generated traffic through standalone firewall from first client, transmissions of ( 8068560 Kbytes ) In ( 1419.6 sec ) are done, the bandwidth usage is 46560 Kbits/sec and Fig 8 shows Results for generated traffic through standalone firewall from second client, transmissions of ( 8068560 Kbytes ) In ( 1365.8 sec ) are done, the bandwidth usage is 48393 Kbits/sec. Fig 9 shows processor Usage for Standalone firewall with VPN which equal 91% and this is a huge number which will lead to hang the system up and thus becoming vulnerable to Denial of Service (DoS) attacks.
-Some Extra Hot Research about Network Security:
Nowadays, some of the trending topics in Network Security are:
-Pervasive security / Security of the internet enabled host devices:
With Nest thermostats, Tesla cars and Microsoft's Hololens - Internet of the things (IOT) seems to be geared up for a good run. IPv6 protocols add another dimension to the problem space.
-Privacy compliance in big data / distributed / cloud systems:
With more and more enterprises uploading sensitive data across data centers, ensuring privacy and integrity (traditionally resource intensive) for huge amount of data is a bottleneck.
-Anonymous traffic networks:
Recent NSA stings have brought the focus back on possibilities of packets being being tempered with. Networks like ToR are being prototyped to prevent tempering.
-Software Defined Network (SDN) vulnerabilities:
SDN world has to deal with control plane attacks which try to DoS the central control system and data plan attacks which are similar to traditional network protocols attacks.
For a more wholesome picture of the research scenario, I have listed below some of the top notch conference programs of 2014.
1. IEEE Symposium on Security and Privacy 2014
2. ACM CCS 2014
3. USENIX 2014 Technical Sessions
4. IEEE NCA Page on ieee-nca.org
Hope this give you a starting point and on overview of the research directions !
Some extra knowledge:
I’m not quite sure if you’re asking about specific technology in network security or trends that cause an increased risk of hacks etc. Nevertheless, I will try to answer as best I can !
A few of the most recent research trends in technology that effect the security of your network include, artificial intelligence, Internet of things, big data and machine learning. Each of these technologies requires additional research in terms of danger to your network security. Simply put, as new technologies are created, new security risks are also created. Just look at the past year for example - security incidents grew 66% CAGR, and the majority of users (58%) operated on 3-4 devices on a daily basis. That’s crazy – the expanded use of technology has opened us up to an increase in security risks and network security has to continue evolving and the research must continue to be done.
The latest trends specifically in network security technology include next generation firewalls and multi-layer protection. This includes, advanced detection, including the ability to detect patterns in suspect activity as well as an increase in advanced data loss prevention measures.
This content is accurate and true to the best of the author’s knowledge and is not meant to substitute for formal and individualized advice from a qualified professional.
© 2019 Kashif Inam Paracha