How Safe And Strong Are Your Passwords?
Don't use the same password twice

Password Guessing
Published 3/23/2014 by Rachael O'Halloran - This is Part One in a series.
So how safe are your passwords?
Do you feel like yours are so unique that no one would ever guess them?
Maybe. Maybe not.
If any of your passwords are the name of person, place or thing in your life, guess what? Your passwords are not really safe at all.
People who use the names of their pets, children, maiden names, married names, street names, city or state names, honeymoon destinations, nicknames and even names of their long lost love have passwords that are the easiest to hack.
If you have a series of numbers after the names, it makes it a little harder to be guessed, but not by much, especially if the numbers are birth dates, birth years, anniversaries, address numbers, present or former phone numbers or any other momentous date.
Common Passwords

Password Strength
The stronger your password, the less likely it will be guessed by a human or a computer program.
So, make it long and make it strong.
A strong password would be a combination of numbers, symbols, and upper and lowercase letters that are in no sequential order.
Question: With that in mind, is this an example a good password choice?
AbCd1234
Answer: No, because it is an alpha numeric sequence following a certain order, even though the usage of the upper and lower case letters is random. Completely guessable.
Question: Is this an example of a good password choice?
Y$9b6#_m2%P&4
Answer: Yes, because this is a totally random mixture of letters, numbers and symbols and not easy to remember. Don't use it, it is just an example.
Your email password
Never use the password you use to sign onto your email on any other sites. If you have one password that you are using for everything, change it now so each site has its own password.
Write them down (on paper) because good passwords are the ones you can't remember. Remember, make it long and make it strong. The longer the better. The more mixture of numbers and letters and symbols, the better.
If the passwords you use now in any way resemble those on the lists located in the sidebar of this hub, change your passwords on every account to something stronger. Once a thief has figured out a pattern to a couple of your passwords, he has access to your life.
If you think you don’t have anything worth stealing from your computer or your accounts, think again. Your identity is just as important to a thief as your Facebook game credits, bank balance or your Paypal account.
Choosing a Password
Your password should never be the name a person, place or thing that is familiar to you or can be associated with you. Even by adding numbers to it, most people still choose numbers that mean something to them, like a birthdate, address, or phone number.
Lots of hackers use "bots" or programs
Did your password make any of these lists?
The Ingenuity of the Password Thief
Passwords were first implemented so that you can be identified as the rightful person to have access to a certain account. In no way is it a foolproof system, but it is the only system we have at the moment.
That is why it is so important to keep your passwords to yourself and not share them. However, it is advisable to leave them in a safe place for your loved ones to access your accounts if you should happen to die or in some way become incapacitated. I cite that because of what happened with awordlover's account which I also moderate.
Just like there are car thieves who can hot wire your car to steal it, there are thieves who can hot wire your computer to get to your passwords and other information.
Ok, not really, but how they get your information is a similar process.
The thieves who want your password have several ways they can get it and they don’t even have to know who you are, where you are, or when you are online.
Personal Information
It will always be a human who benefits from stealing from you, but it may not always be a human who did the actual stealing.
Primarily this is because "there's an app for that!" There are many computer programs that are specifically made to hack or guess passwords. They need very little personal information for the process to be successful. I feel that these 'bots' should be outlawed; unfortunately they are legal. However, I fail to see their value or worth in a legitimate way.
Guard your personal information just like Fort Knox is guarded.
When you think about what people can do with your name - just your name - it can be devastating. Most of the time, we are responsible for sharing some details of our life appearing online. When we are talking to our friends online, especially on Facebook and other real time sites, we often will mention something about our daily lives, be it the name of our children, where we used to live, where we work, naming an upcoming event at our kid's school, or even what our favorite recipe might be.
How many times have you clicked "Share" on a Facebook post?
It is inevitable to share information on a social site. Something as innocent as sharing a photo for a charity, child or pet abuse, or a disease like breast cancer, adding your own message to pray for someone, or that so and so is recovering from breast cancer - all these things can give a thief valuable information about you, your location and your online habits.
Google yourself often to see what shows up in the results.
You might even be surprised to find one of your Hubpages articles is listed on someone else's website - possibly with their name replacing yours as the author! That is how I found many of awordlover's articles were being copied to other sites.
Look your Google results over and see how easy it would be for someone to locate you.
The results might show site that have your present and past home addresses, the names of your children, their ages, that you have X number of grandchildren who live in (name) state. That you are married XX years to (name) and that you were married in (city). Regarding your activities and what you talk about online, don't give the search engine any more information to add to their database.
Tips & Safety: Choosing Passwords
The Best Passwords
The best passwords make no sense.
Alternate -- using random numbers, letters and symbols with upper and lower case. Write them down and change them often, at least once every three to six months or when you see suspicious activity on your accounts.
If you ever hear news reports that a certain company's database has been hacked or they leaked email address/account numbers, and you have an account there, change your password immediately.
If you get suspicious emails stating that you have to update your account information, do not click. If the email contains any personal information about you, change your password by going putting the URL into a separate browser window/tab, and take care of it from there.
Don't click any links in emails because they will most likely re-direct you to a bogus site (clone) that looks like the company, but it is not.
Passwords are your one single line of defense against internet predators trying to get your information.
Deter a password thief today. Go long.
Write Down Your Passwords & Sign On Information ...
A password thief can change your passwords so that you lose access to your accounts (it happened to me with a blog) and it won't be long before he attempts to divert your direct deposits to a new destination. It happened to me with my Social Security checks.
With my blog, all the thief had to do was go hack the blog's password to get to the Dashboard, kick me out as admin, put himself in as admin, change the password. I tried to get it back via "password recovery" steps to get the password to get onto the Dashboard, but the link Google sends went to his email because mine was already off the blog by that time. He then cleared out every post I made over the 3 years life of the blog. I have copies of my posts and the cache copies are still in search results, but Google wouldn't remove him as admin because I couldn't prove ownership. I asked for the blog to be closed down for stealing my content, and the answer was no because there was no content to steal. The reason it was not showing on the blog was because he deleted it. I asked for blog to be closed down because he impersonating me. The blog had my name in the title. And they agreed. The whole blog is gone but now neither of us have access to it. My family wants me to start another blog soon, but I doubt it. With Hubpages theft being so high on the internet, it is becoming the Wild West of the 21st century. I don't know if I want to add one more thing to be constantly on my guard about.
But, my Social Security check was a different matter.
Like most people, my Social Security check goes direct deposit to my bank account. There was no option to have it mailed to me. I was told that direct deposit was a requirement. My husband and I keep one joint bank account for paying mortgage, car payments, etc. We keep separate "his and her" personal accounts. My account pays most of the frills (decorating, shopping, online purchases), his account pays for all the thrills (vacations, our hobbies, Saturday night dates).
As smart as I thought I was, I kept a Word document of all my passwords on a file in my computer, instead of on paper in my house.
It listed my secret questions, passwords, screen names, anything I had trouble remembering was in that Word file. I even emailed passwords to myself every time I changed one, so I would be able to find them easier and to copy paste them onto the list to update it.
Emailing passwords to yourself is the worst thing you can do. Think about that for a second and you'll see why.
The thief was able to get most of what he needed from the emails I had sent to myself and my husband. But he was also able to get the Word document I kept in a file because I emailed it to my husband as an attachment to an email so he would have the info in case he ever needed it to get into our online credit cards and bank accounts.
This was after I took over awordlover's accounts last year; I thought it was a great idea that she left all her info behind in a notebook for her husband and sons for when her time came. I just skipped her notebook advice and made the Word document instead.
It was a very bad idea.
The thief had everything he needed - the answers to my security questions, my bank account number, my social security number from the bank account info. Using the online form, he notified Social Security to change the direct deposit of my check to a bank in Miami, Florida, he put a change of address in with the US Post Office for a drop address (a physical address that is an abandoned lot that has a street address assigned to it), so only the mail that came to our house that had MY name on it was changed from my present address in California to Miami, Florida. He also cleaned my personal bank account out to put the funds in the Miami bank and then he closed my California bank account. All this happened within 5 days.
It took me over 6 months to get my Social Security check straightened out. In that 6 months, the thief had all the mail in the Miami forwarded to another drop address in St. Thomas Virgin Islands. It skipped around the islands for a few months until it landed in Bangor, Maine.
My accounts went to more destinations that my husband and I ever went when we traveled across the country. The initial process was all done while I was working a 8 hour shift. It took me 5 days to realize the extent of what had happened.
After the 6 months, the hacker abandoned the account in Bangor Maine and emptied it out by wire transfer. The horror of it all, he was never caught.
Thieves never leave a trail for anyone to trace activity directly back to them. The guy who did this bounced off so many IP addresses and servers, that he is in the wind and the authorities said they know they will never catch him. After they told me he was untouchable, they told me it was all my own fault because of the Word document.
When I say write it all down, I mean on paper, to keep in your house, office, or safe. Not on a PC, not in email.
Write down your passwords and secret questions on paper, along with your sign on names, screen names and account numbers, DO NOT store them on a Word Document on your computer.
As with me, all a thief has to do is access your email, and it will be no time at all before he has access to every part of your life.
Suspicious emails?

Security Questions
Do you have the same security questions on every account? Yes?
The problem with security questions is that people choose something they themselves (or immediate family) will remember so they don't have to play hit and miss to guess what the answer is.
What city were you born in?
All a thief has to remember is "Oh, she has it listed on her Facebook profile. It's Detroit."
The security questions you choose to remind yourself of your password or to verify your identity could be your undoing.
Try changing them (questions and answers) every few months so that the same questions are not on the same account forever. Also, try giving the wrong answer for what city you live in or other questions. Choose something you will never remember.
What's your mother's middle name?
Pick a male name that is not familiar to your family. For example: If no one is named Sebastian, you could choose Sebastian but then add a series of non-sequential numbers after it, if the space allows numerical input.
On your bank information for example, one of the primary questions they almost always ask is what city were you born or what city were you married in as a security question. You can pick a fantasy destination you always wanted to travel to, and use lower and uppercase letters to type it out. If the field allows you to insert numbers or symbols, add them. If the city has a slang name, write that down instead of the city's actual name.
Example: Windy city, Mardi Gras, Philly, Tinseltown, Motor City, Chocolate Town, etc. If you grew up in a section of a city, try using that. Example: Flatbush, Kensington, East side, Jackson Heights, Prospect Park, etc.
Sometimes one of the choices is for your middle name or maiden name or that of your mother or grandmother or sister. You'd be amazed at how much information about yourself is available online. Did you list your relatives in the family boxes on Facebook? Mother, father, sister, brother, etc. Also, if you ever wrote a personal hub, mentioned family members by name, their illness, their new home, the honeymoon, your children, their birthdays - a clever password thief can get all of that info if he enters your name in a search on Google.
If a site allows you to pick your own security questions, be creative. Pick something more obscure. What was my Uncle Harry's second born son's name? Or, What personal nickname does my hubby have for me?
Picking the name of the street you lived on as a kid is popular and not a good question to choose. Here is a good example. Enter your name in the Public Records box of Peoplefinders.com
All anyone has to know is what city you lived in at that time and they can Google it with your name and get more information. If you still have family living there, the phone book is their best friend.
Here are the results using my name and California in the search boxes: You will see that the results give you a list of alternate names that might be in use, an approximate age so you can tell which person might match the Rachael O'Halloran you are looking for, a list of former city and states, and possible relatives who live or have lived with me.
On peoplesmart.com, privacy protection doesn't get much better. The link shows all the names for Rachael O'Halloran, aliases or former names, and former addresses. For a 3 day trial price of 95 cents, someone can do as many searches as they want for 3 days (or $25 a month) and do serious damage to a lot of people with the information on that site and many others like it. And it is all public record.
Due to what happened to me with my bank account, one of my security questions is "What am I going to do to the bastard who ever steals my passwords again?" The answer allows me 26 characters and unless the thief has had nightmares about someone doing these things to him, he won't get the answer. I change the answer every month.
If your bank requires you to use your account number (instead of a screen name) to sign in to their website, then it is triple important that your password and security questions be the most difficult ones to guess. Because most people bank in their own neighborhood, your bank and bank account number can be located very easily. By knowing your birth city, your maiden name, (as per the public record links above), your favorite color or your favorite flavor ice cream, (from sharing that on Facebook or other social networks), the answers to your security questions can be guessed with little effort.
If you are easy to find, getting into your accounts won't be hard at all.
WiFi

Cybercafe Safety

Wifi, Library and cybercafes
If you use computer libraries or cybercafes, these are not secure computers. Only use them if you absolutely must. Never look up your credit card or bank information. You don't know if there is a keystroke logger or malware that monitors the activity of every person who uses the computers. It could have been placed by the owner or anyone else and you can't see it.
If you are accessing your email, take a look at your login activity since your last access and make sure it is only the places you have logged in.
When you are leaving that computer, clear the cache - totally wipe out your browsing history so the next person sitting down cannot see what you were doing, or try to access those sites with any saved information (cookies, etc.). If you must write anything down, use your own paper and not post-it note pads that are sometimes available. What you write can be seen through to the next paper.
Completely log out of every page you opened. Never save passwords on the screen prompts.
After you leave, change your password as soon as possible. Don't change it on their computers.
When I had to use library computers or cybercafes because we were on the road traveling from east coast to west coast, I changed my password as soon as I got back in the car by using the browser on my cellphone. I didn't use my cellphone for answering emails because of the volume, airtime cost, and the fact that my fingers couldn't handle the volume of email that needed responses.
If you are surfing for hotel availability for the next stop in your travels, do not put in credit card information to hold the reservation. If they insist, tell them you are on a public computer, tell them your arrival time and you will supply the information at that time.
If you use WiFi, which is often available at hotel destinations, cybercafes and restaurants, you need to do routine maintenance on your computer as soon as possible. Here is a link with more tips.
Safety Tips: Bank

PIN number joke

Disclaimer
While I am fully aware the information in this article can be used in the wrong way, this author advises all readers to use the information responsibly.
Tips for Offline Safety
I require my bank to call me on the phone every time a major change is being done on my account.
Even if I am on vacation, and I've used my bank credit card or wrote a check a minimum of two times at the vacation spot, they have to call my cell to see if it was me. If I write a check from the vacation place, they call me saying that a certain merchant or establishment is trying to cash a check I wrote for $XXX.XX and did I write it? Also, if any changes are made to the account logistics (change of password, my address, redirecting my direct deposits, etc.). they call me even if I did it myself. I also get an email notification as part of a two step verification. Any time a company offers a two step verification, take it!
Establish a Purchase Limit.
This is not how much your line of credit it. This is a limit you decide that you want to bank or credit card to notify you about if someone spent this much or more for one purchase with one merchant. It is a red flag to you. If you never spend above $1000 at one time for a purchase, then that would be a good Purchase Limit to put on your account. Since I rarely buy any one item that cost $1000 or over from one merchant, I informed my bank and my credit card companies that any purchases that exceed $1005 should follow the two step verification.
Get your bank and all your credit cards to do the same for you.
Tell them you want a "STOP" put on the account any time your credit card is used a minimum of two times in a state (or zip code) that is not your own. This means that the third time the card is being used, the merchant will decline the card at the point of purchase (and hopefully get someone on camera!). If the bank or credit card company is able to locate you to verify it ahead of time (in case it is truly you doing the transactions), then the third merchant won't decline the card. The good thing about this is when my husband and I are on vacation, I almost always forget to call the credit card companies to tell them there will be new activity in a place other than home state. It is just something I don't remember to do. By the time I get to the third merchant who declined my card, I remember, so I have to call them to let them know it was me making the transactions and that it is all ok.
PIN Numbers.
I have separate pin numbers on all my credit and debit cards and I am required to enter them even to make a purchase in Walmart. Whomever steals my credit cards (or steals just the number) has to have the PIN for that particular card to be able to use it - online or offline. If you have a debit card, chances are you've had the same PIN number forever. Change it every 3 to 6 months and write it on your list of passwords and security information.
If this seems like a lot of trouble for you to go through, you only have to have someone invade your privacy one time, and you won't think it is a lot of trouble anymore.
- Write everything down so your family members have a "go to" list in case anything ever happens to you.
- Keep a small notebook just for your passwords.
- Assign one page for each site listing the passwords and the security questions with the answers that you chose for that site.
- Change it up every few months.
If you can remember your password and the security answers, you are not operating in a secure environment.
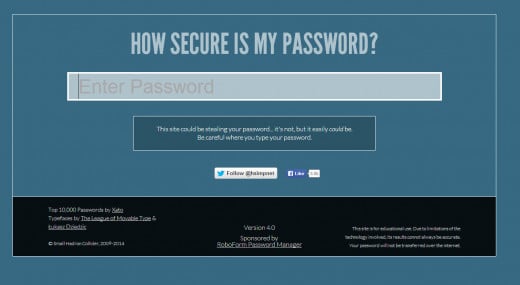
Cool Site: Try This Password Checker!
Go to this link - How Secure is My Password. Enter ONE password (repeat for each password you have, one by one for each account.)
The result will tell you how long it will take someone with a Desktop PC to crack your password.
However, because I'm suggesting this as an educational tool for you to see how good your passwords are, I do not recommend using the Password Manager Form that is also offered on that page.
I prefer you to do it long hand, in a small notebook from the dollar store, and keep it safely in your house, not online.
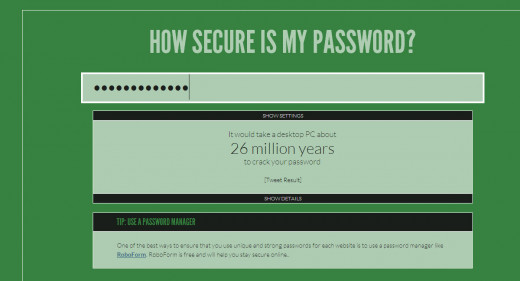
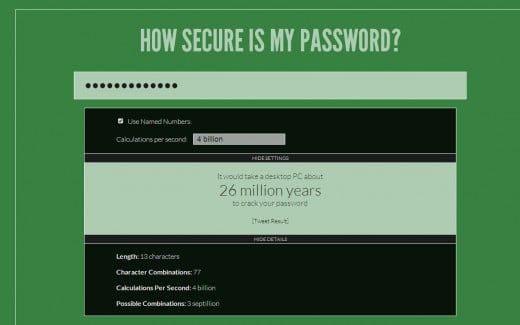
Below this paragraph are 3 screen shots to show you what to expect and what my results were using the "Good" password from the example above: Y$9b6#_m2%P&4
1st is the landing screen for you to enter each of your passwords one by one.
2nd is a screen shot of my results.
The 3rd screen shot shows what you will see when you unhide the results to see the number of possible combinations. You want to see VERY HIGH numbers on that part.
These are screenshots. To test your password strength, click link under screenshot
Making Good Password Choices By Google
© 2014 Rachael O'Halloran