How to Protect Your Computer From viruses and Online Scams
Evil raises its ugly head!
Time Traval Saves The Day
When it comes to computers, I have not had a good year, with one problem after another.The latest catastrophe was a very nasty malware that slipped past my security system by camouflaging itself inside of a download. It pretended to be a security program that tries to get its victims to cough up a credit card Number. The “program” takes over the computer to the point that you can not turn off your computer without taking out the battery.
I finally defeated the little demon by rebooting in safe mode and then going back to a time before the problem even happened. This method is a simple way to remove any type of spyware or other annoying program.
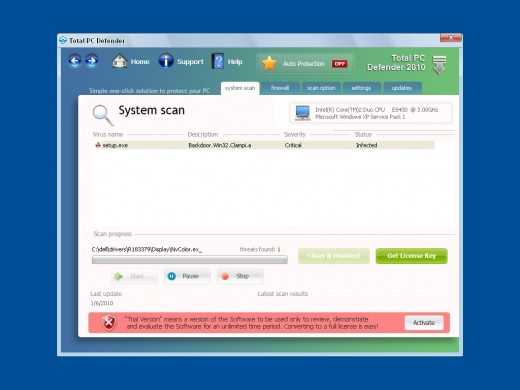
This problem all started when I let a friend who is not very computer savvy check his email and next thing I know is, he was going download crazy! I log back on and was greeted by a abomination pretending to be security program! The name of the Beast? Total PC Defender 2010. I knew that it was some kind of scam program so I did not take the bait. However it cost me a lot of downtime. This rogue security application is spread with the help of sneaky Trojans.
When I at long last I was able to regain control of my machine, I went to Google to find out more about this cyber thorn in my side. All together Google found 1,250,000 sites that had information on dealing with this particular scam. I read forms with the laments of many victims, some who succumbed to the scam and submitted their credit card numbers!
In my search, I did find some very useful websites that will take you step by step though the same methods I used. They also offer free software that they say will supply a remedy. I guess I have gotten paranoid from my experience, for I am little hesitant to download anything. Here is the point I want to make about all the ways presented to deal with this problem...it is not necessary to buy more software to resolve the situation. One site I found useful is one called Bleeping Computer.com This site has software called “Spyware Doctor” that they claim will resolve most malware problems.
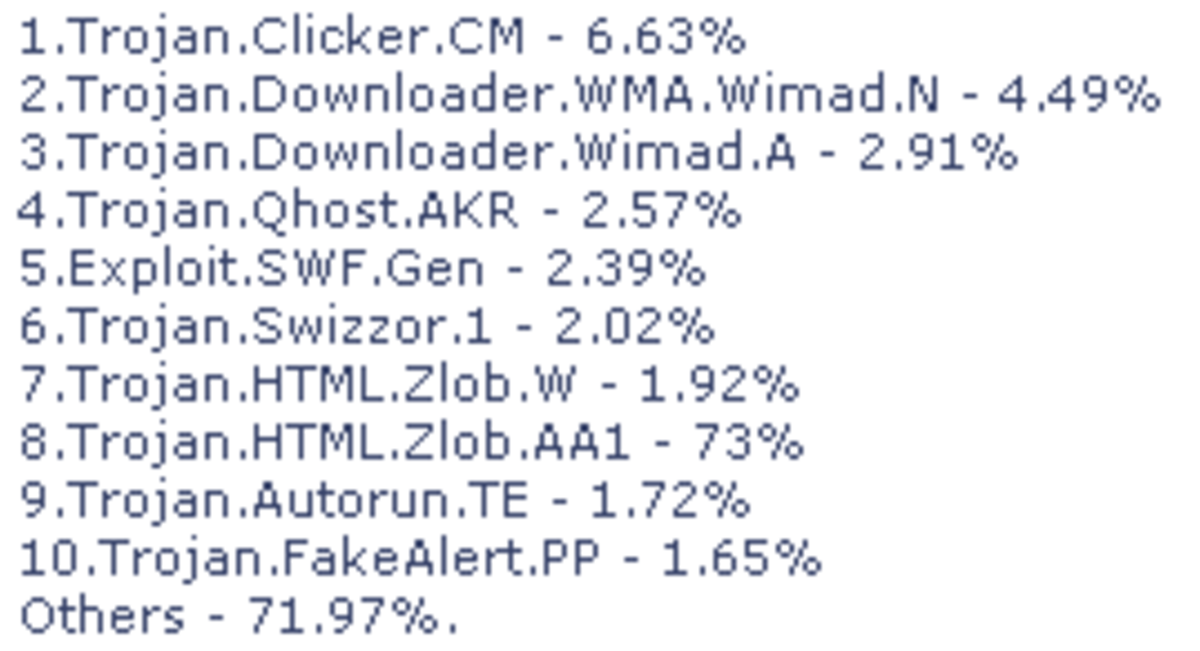
The word “malware”is actually short for malicious software. Another term for programs like Total PC Defender 2010, is scareware for it is meant to scare the victim in devolving there credit card number. Malware is a catch all term that could include any type of malicious software, including spyware, worms Trojan Horses and any other software created to do harm or control a computer.
This whole computer virus nightmare started somewhat innocently as an experiment and/or computer nerd pranks. Then came the age of broadband Internet and our brave new world became even more sinister! Now a lot of Black market software is being designed to allow profit in one form or another. cyber-crime is bigger than ever.
Tthe reality of our times
Here a Scam there a Scam...Everywere a Scam!
I am now on mission to not only help those who are dealing with this particular menace, but to hunt down what other electronic scams are controlling the masses. I already knew there was a lot of scams out there, for every time I peek inside my spam folder I find that I have won millions of dollars in some far off country! However, what I discovered was somewhat alarming, for the problem is much greater than I even anticipated.
These high-tech criminals have become very sophisticated and ruthless and use any means necessary to either rip off, harm or control as many computers as they can. In fact Social Networking sites like Twitter, MySpace and Facebook are major targets of hackers, phishers and other cyberage outlaws. Here is just one example of a MySpace scam: A phishing scam is targeting the popular social networking site, MySpace. Scam artists are accessing account and posting status updates that invite people to make some cash.
If a person clicks on this status update, then he or she will be asked to re-enter their account information. As a result, the cyber criminal will use this information to log in to another person's account to post the same status update. This is why it is important that when you log-in to a social networking site, make sure to type the site's URL.
Another scam has target Being's search engine and it has been reported that 90% of those pharmacy adds will take the person who clicks on the add to phishing site to obtain credit card numbers.These scams goes on and on and to find out more, you can visit slam the Online Scam.com. They have frequent up dates on the latest online scams.
On to the next scary issue and that is, something know as Click Jacking. The following video will give a demonstration that will explain things clearer. The basics of the scam is gain control or manipulate the users mouse to serve the hacker.
It is now is the age of the "invisible scam!"
"walk this Way"...Be on the lookout for the computer Zombies!
Beware of Computer Zombies!
Has your computer been running slower than normal? It may be that it is in the clutches of hacker performing digital Voodoo on your beloved PC! They can use it for what ever they desire, be it spreading spam...attacking government agencies or overrunning sites like FaceBook! Far fetched you say? Not according to the New York Times article written as far back as June 23, 2005. I quote from that article:
“Experts say hundreds of thousands of computers each week are being added to the ranks of zombies, infected with software that makes them susceptible to remote deployment for a variety of illicit purposes, from overwhelming a Web site with traffic - a so-called denial-of-service attack - to cracking complicated security codes. In most instances, the user of a zombie computer is never aware that it has been commandeered.”
The BBC News reports as recently as May 6th 2009 that this problem as increased 50% since 2008. The article also states that the U.SA leads the way with as much as18% percent of the effected computers.
So what can be done to combat these technical nightmares? A lot of simple practical things like..
-
Scan your computer often: Be diligent and do what you can to detect anything that may become a problem. Make sure your computer is fully protected by updated security programs.
-
Do not leave your computer on all the time: This is just what the “bad guys” want, a machine left on and unattended to do their bidding!
-
Be careful of were you click: If you run across adds that promise outrageous giveaways or whatever, avoid them like the plague! The old rule is so true...if it sounds to good to be true it probably is!
-
Be careful of what you down load: Scan when every you can!
-
Never give out credit card numbers to sites you are not certain about: For my self, I never use a credit card on the Internet. If I need to have a credit card to buy something on the Internet-I look for another way to obtain it. I refuse to use credit cards on line.
This is just a few examples of what scams are out there and what can be done about them. This is, as they say, is just the tip of iceberg...
Other sites with usefull information.
- Antivirus & Anti Spyware Security Software for Home & Business | Webroot
Antivirus and antispyware security software for your home or business. Remove spyware, viruses, and malware with internet security software for home and business services from Webroot. - Remove Spyware & Malware with SpyHunter
ESG's SpyHunter scans and removes malware and other malicious components. Read more on other PC security software and information on removal instructions, tips, and alerts on new threats plaguing the Web.