How to Protect Your Computer From Malware
A Hacker

Secure Your Computer To Secure Your Data
Your personal computer is a valued device, your data is much more important than your computer. Both must be protected at all costs.
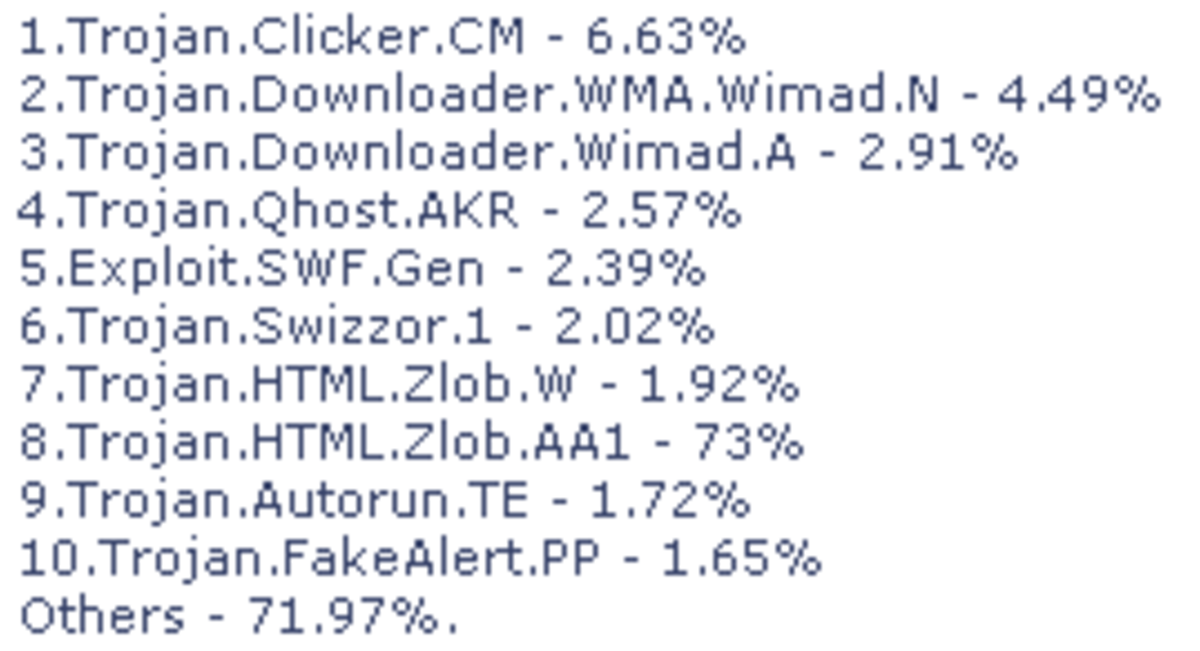
The issue of computer malware confuses a lot of people.
The term malware is actually a shortened form of malicious software. Malware is software created or developed to damage or perform unwanted actions on your computer.
Malware is also capable of disrupting your computer operations and gathering your sensitive information without your knowledge.
Examples of Malware are:
- Computer virus
- Computer worms
- Spyware
- Trojan horses
- Rogue security software
A Computer Virus
A computer virus is a software program designed to interfere with the normal operations of your computer.
It can corrupt or worse delete data on a computer making it impossible for you to access your documents.
They spread rapidly from an infected computer to other uninfected computers.
They can also be infected to systems that are already infected making you end up with a mixed grill of viruses.
They are easily spread via removable devices like USB flash drives, through the Internet by downloading infected software or through email programs especially attachments.
A Computer Worm
A worm is a malicious software that propagates itself by replicating without the user's interaction.
Usually, it uses a computer network to pass from one computer to another.
In most cases, worms will originate from email attachments where they spread to the computer when the attachment is opened.
They also send themselves as infected email messages to other computers.
Worms are not as harmful as viruses but they end up consuming the bandwidth of your network.
Malware Scan
Spyware
This is a software package that secretly gathers information from your computer. It does so through the Internet connection without your authority or knowledge.
In most cases, this is done for advertising purposes. They are capable of collecting sensitive information like bank or credit information, user logins, and browsing habits.
Having acquired your browsing habits, you can then be bombarded with advertisements related to your surfing habits.
Others can also install additional software, change your computer settings, and slow down your Internet connection speeds.
A Trojan Horse
A Trojan horse is a malicious program that masquerades as a normal program inside other programs.
It gains access to the computer by hiding itself in a legitimate program, for instance, a screensaver, free applications, and games from the Internet.
Then, once inside your computer, it will put a code into the operating system and from there on you are at the mercy of a hacker.
Rogue Security Software
This is a software program that tricks you to think that your computer has a virus attack.
Thus it prompts you to buy or download a program that will clean your computer.
These messages usually appear as pop-ups which should be closed using the Alt + F4 key combinations.
Always be extra careful before downloading any software from the Internet.
Why You Need An Anti-Malware In Your Computer
Many people will install an antivirus program in their system and think that they are 100% protected.
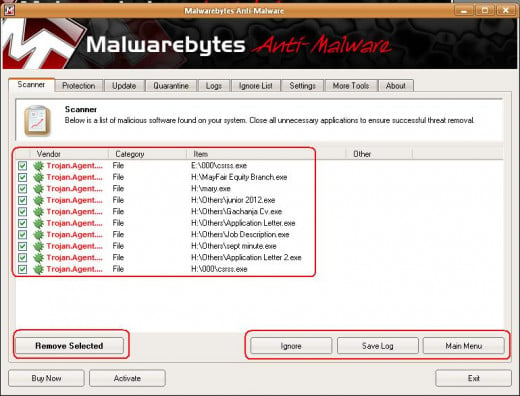
That is what I have been doing until my computer was attacked by a Csrss.exe Trojan horse.
Checking from the processes running, the csrss for windows service was having lower case letters while the Trojan had a capital C.
The antivirus I was using could not detect it. The Trojan was turning word documents to have the .exe (executable) extension.
So, it is only after opening such documents that I was getting a warning about an attempt to open a suspicious file.
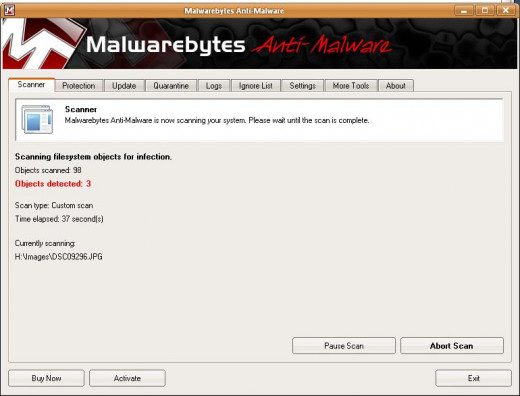
Turning to the Internet, I decided to download Malwarebytes, a free anti-malware, though you can also get a paid version.
I used the free version which managed to detect and delete all the Trojan horses I had on my computer.
Trojan Horse Detected
How To Protect Your Computer Against Malware
- Install an antivirus program on your computer. The antivirus you use should be able to detect a wide range of virus including the current ones because viruses are created daily. We have a lot of free antiviruses that are good and capable of protecting your computer just like the paid versions.
- Install an anti-malware. You should also go for reliable malware that will be able to detect malware and destroy them.
- Keep on updating your antivirus and anti-malware regularly.
- Scan removable devices like USB flash drives after attaching them to your computer.
- Scan software and other documents you download for malicious software.
- Be extra cautious when opening attachments especially from dubious sources.
- Regularly scan your computer.
Is your computer secured?
This content is accurate and true to the best of the author’s knowledge and is not meant to substitute for formal and individualized advice from a qualified professional.
© 2012 Patrick Kamau