How to Install Windows® Operating System
Overview of Operating Systems
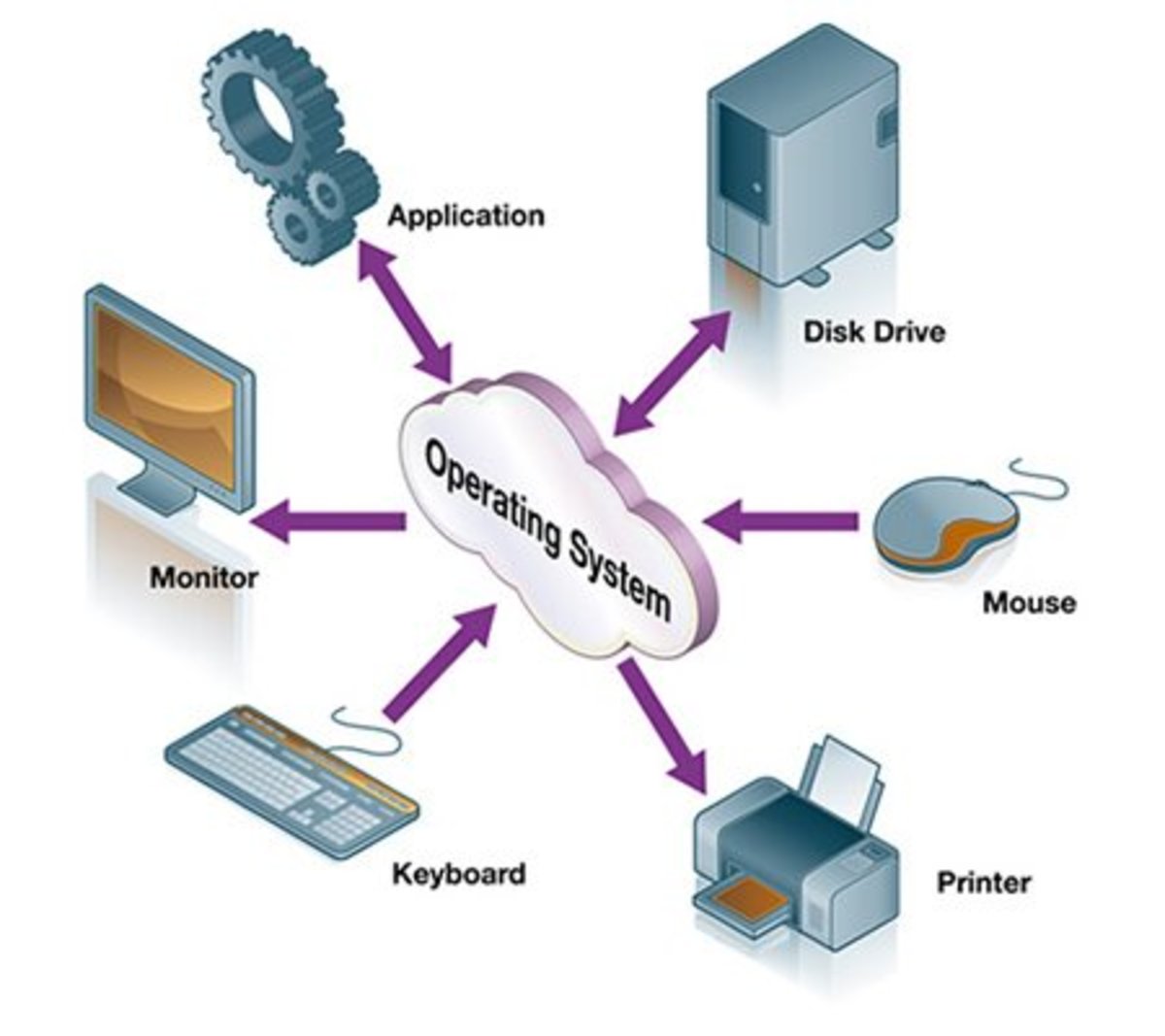
An operating system is an interface between users and hardware that allows convenient usage of the computer. It also protects information and gives each user a part of the resources by acting as a control program.
Components and Functions of Operating System
It is a program that is able to schedule jobs or processes and can use complex rules to deal with a running process. It can execute the CPU and IO handling simultaneously including off board processing. This function helps in memory management, deadlock protection and resource scheduling. Interrupts are able to transfer the control of the operating system to the interrupt service routine. A trap is a software- generated interrupt is mainly caused by a user’s request or an error. The operating a system has different layers of storage devices ranging from the fastest to slowest making efficient use of resources. Much effort is directed towards support caching which is performed at many levels in a computer including at the hardware, software and operating system levels.
Different Versions of Windows® Operating Systems
Some of the most common Windows operating systems versions include Windows 2000, Windows Vista,Windows XP, Windows 7 and Windows 8. serviced for bugs. In the near future
Installation of Windows® Operating System
Windows can be installed by clean install where one wipes out the existing operating system and then install Windows, or does the installation on a new partition. In-place upgrade deals with an existing Windows installation and upgrades it to a new one. Widows can also be installed through migration. Here, one installation becomes the source while the other is the destination. User files and settings are transferred from the source to the destination installation. It is done by either using the Side-by-side or Wipe and Load strategies. The last method is the dual boot which is done with a computer that has more than one operating system. Each operating system is used at different times and not at the same time. A dual-boot can be done between a Windows XP and Windows 7, or between Windows XP, Windows Vista and Windows 7.
Procedure to Install Windows 7 and 8 Operating Systems
Windows 7 is the easiest to install. One has only to answer some questions when installing the system and majority of the setup process occurs automatically. On the other hand, Windows 8 is installed using a method identified as clean install. This involves removal of the extant operating systems that had been previously installed and then installing the new system from scratch.
Methods of Supporting Operating Systems
There are various methods that one can use to support the operating system of a computer. These methods are done for the safety and security of the computer. One can should always endeavor to keep the operating system up to date and secure at all times to avoid problems associated with computer speed and freezes. Automatic updates should be setup to ensure round the clock protection and security. Strong antivirus software should be installed including the application of a firewall which will always keep malicious malware and viruses at bay.
Possible Concerns When Installing and Maintaining Operating Systems
When installing and maintaining operating systems it is advisable to always ensure that it is properly installed and it is in good order. Do not forget to back up the computer daily. Common symptoms in error messages will give you a hint as to what is ailing the computer. Always know the best corrective steps to undertake and install updates to the software and driver updates for your hardware. Rebooting is also useful in fixing most system crashes or uninstalling the software causing the problem.
Troubleshooting and Preventative Maintenance
Troubleshooting your computer system is not an easy task because of its complexity and time consuming procedure. You can make it easier by employing a systematic and logical approach to any problem. Many faults occur repeatedly and it is easy to identify them and handle them appropriately. One should place much emphasis on preventative maintenance to spot and correct problems before they become serious. It is good to use a CHKDSK or scandisk utility built into the system.
Troubleshooting Techniques for Operating-System-Related Problem
The two most commonly used troubleshooting techniques are the "trial-and-error method" and the "systematic method". You can use one or both but make sure you follow the right procedure. Trial-and-error troubleshooting can be done when one has an error, but does not have sufficient information to start..On the other hand systematic troubleshooting involves breaking down the error problem into small manageable pieces.
Maintenance Issues for Operating Systems
To maintain your computer you must perform a few tasks and that includes regular maintenance to rid your computer of problems. These tasks may include deleting temporary files, cleaning the disk, using an anti virus, and defragging the hard drive. Regular maintenance will help keep your computer up to speed and free of annoying problems.
Upgrading an operating system compared to a clean installation
Windows Vista contains upgrade paths for Windows XP Professional, Windows Vista and Windows 2000 Professional. If you are using Windows 3.x, Windows 95, Windows 98, or another operating system a clean install is required.
Networking in Operating Systems
This is an operating system that is specifically designed to support personal computers, workstations and older terminals which are connected to a local area network or LAN. Examples of network operating systems include Banyan VINES, Novell's NetWare and Microsoft's LAN Manager. Some multipurpose operating systems have features which enable them to be termed as network operating systems.
Configuring Windows
Windows should be configured to enable a computer start correctly. The process in configuring windows entails the following steps: click the start button to open the system configuration, go to control panel, click security and system, go to administrative tools and the double click system configuration icon. If you are requested to provide password, you can do so or provide confirmation.
Windows Administrative Tools
Windows administrative tools refers to a folder availed in the Control Panel which harbors tools for users who are at advanced level and system administrators. The type of tools in this folder depends on the version of windows. In accessing the tools, these steps should be followed
Click the start button and go to administrative tools and then to control panel. In the search book, type the word “administrative tools” and then click on the administrative tools icon which emerges.
These tools include component services, Data sources, computer management, and Event viewer, Local Security Policy, Print Management, Performance Monitor, System Configuration, Task Scheduler, Services and Windows Firewall. There is also Windows Memory Diagnostic and iSCSI Initiator.
Common Network Problems
Problems are bound to occur in a network on a consistent basis. The most common ones include Bandwidth saturation, which in this case is a literal saturation of the network when it is overworked or reaches a limit. Other problems include disconnection(unreliability of wireless networks, physical interruptions, bad or defective hardware or wiring, mechanical problems, cable problems, network collisions, software problems, Duplicate IP Addressing, and issues to do with connectivity.
Preventive Solutions for These Problems
For cable problems one can use cable testers in finding out different types of problems that may be existing. These problems may include incorrectly connected cables, cut or dislodged cables, connector problem or interference level. Wiring and cables should be done in such a way that there is minimal if any interference. Concerning software configuration, it is important to ensure that the configuration is done properly and aligns with the specific network. For bandwidth problems, it is recommended to use less of it, buy more of it if there is need for enhanced network and get advice on your ISP provider on the limitation. If you experience constant problems with wireless problems, it is advised to use a wired network.
Security Issues of Operating Systems
Operating systems also encounter a number of security issues on a regular basis. Some of these security risks and breaches are so risky to an extent that if they are not addressed amicably, they can destroy the whole operating systems. These security issues include breach of confidentiality, breach of availability, denial of service (DOS), breach of integrity, and virus and worms attacks.
Preventing Solutions for These Problems
There are a number of ways that can be used in preventing security problems in operating systems. Among these is ensuring that the operating systems one uses has a password to prevent unauthorized access, and vital information, installation of a firewall solution to prevent the network and computer from malicious attacks, and installation of antivirus software on computers. Other means include running systems scans on a regular basis and understand how to handle email including how to avoid phishing and how to attach files.
Standardized Computer Security Practices and their benefits
Standardized computer security practices provide a basis to establish a repeatable processes and procedures in information security. Further, the use of standard computer security practices makes it easy to analyze and plan the activities of security staff in advance, improve on the management of system information security and foster a consistent cycle of institutional learning through ought the firm. Moreover, undertaking security practices in a consistent manner ensures that errors are minimized as much as possible while speeding response time. Furthermore, it also offers a way of measuring performance for consistent improvement. What is more, adherence to these standards raises network control capability as well as network visibility.
Key Elements that should be Included in These Practices
Key elements that should be included in computer security practices include 1) the use of an anti virus program because a zero-day vulnerability can cause harm to your system 2) enabling your Firewall and make sure it is correctly configured 3) enabling you user account control always because it is an important layer of protection from malicious software and prevents them from modifying your system without permission.
Common Security Problems
The three most common security problems to a computer are viruses, spam and phishing. Viruses have a high danger level. They are transmitted via a network or through portable storage devices. Spam is also another threat to your computer which has an extremely high prevalence but with a lower danger level. They are electronic junk mail and sent through messaging systems like yahoo and the rest. Phishing is also another threat and is an attack in which a program behaves like another, for example a website or an URL. It had a high danger level and whose prevalence is extremely high.