- HubPages»
- Technology»
- Computers & Software»
- Computer Science & Programming
Internet of Things: A Comprehensive Review of Architecture, Elements, Protocols, and Security Challenges
Main Article
Abstract
Internet of Things (IoT) has enabled connected things via the internet to facilitate humans, machines, and objects in a contemporary environment. IoT has potential applications in every field of life mainly smart cities, smart homes, smart grids, smart retail and healthcare management systems. At the same time, the IoT network poses some security challenges while adopting it. This paper provides an overview of IoT basics including its applications in various fields, architecture and basic elements and protocols of IoT. However, it also describes some security challenges faced by the implementation of IoT architecture. Furthermore, some futures directions are suggested also.
Keywords: Internet of Things, Automation, layered architecture, security, protocols, elements
1. Introduction
The Internet is being used by millions of people in their daily life tasks to make life better. The internet has revolutionized the lives of people in terms of entertainment, knowledge and information and various other tasks. An estimation says that 48 percent population of all over the world use internet technology. It has many potential benefits for the user such as it connects and synchronizes with other users all over the world [1], [2]. With the popularity and benefits of internet technology, another emerging technology named the Internet of Things (IoT) has come into being which connects objects and devices to connect and transfer information to the other devices via the internet [3]. This technology can make life easier by connecting and automating the various objects of daily life and provides comfort and improved efficiency of users in their daily tasks. IoT has a combination of different types of sensors and actuators attached to the real-life objects to get information from them. The sensors and devices then connected to cloud storage with the help of various methods such as cellular, WiFi, Bluetooth, low-power-wide-area networks or directly can be connected with the Ethernet connection in case of a small area [4]. Every method has different power consumption, range and bandwidth and these methods are selected according to the IoT application needs. When data reaches the cloud, data processing is performed by some software and then the useful information response is sent back to end-users.
IoT as an emerging technology has its various applications in various domains to make them smarter and efficient than ever. The tasks over the internet are performed robotically and efficiently in no time. The brief depiction of applied domains of IoT is presented in Figure 1. The research is undertaken on the elder people in [5]. In the context of their adoption of smart home products related to healthcare. The result has shown a positive result regarding variables like adoption, reliability, and expert advice but negative for variables like anxiety and cost. A platform for monitoring stroke patients during their daily life activities through a smart cup SyPATHy is presented in [6]. SyMPATHy uses Raspberry Pi Zero and sensors to retrieve and process data. 9-DoF Inertial Movement Unit (IMU) MPU-9150 is used for detection. Force Sensing Resistors (FSR) are used for monitoring hand force while grasping the cup. Another application for home automation is presented in [7] using a smart voice-based automation system for home appliances using IoT, AI, and NLP techniques. The appliances (Fan, lights, door lock and coffee maker) are automated by voice commands using NLP to the mobile devices which acts as a central console and these appliances are connected through Arduino Board which response to the mobile inputs.
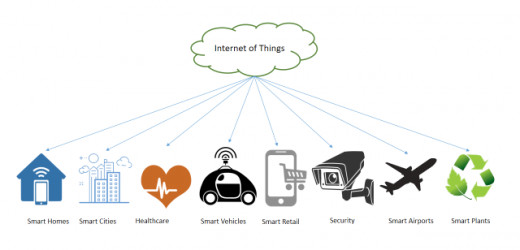
Figure 1: IoT Applications
Smart cities [8] are the most prominent application domain of IoT technology where smart city covers many functions of the city such as smart homes [9], smart healthcare applications [10], smart water management system [11], smart waste management system [12], grocery management system [13], smart grids [14], and smart plant system [15] etc. A smart waste collection and management system [16] is on real-time data with an IOT prototyping using sensors is presented in [17]. The nearest-neighbor shortest path algorithm is used for checking the nearest optimized routes. The shortest path spanning tree algorithm is used for finding the distance of wastebins and work areas. Then the wastebin sensing algorithm is used for checking the level of waste bins. Intelligent analysis is performed for the prediction of future wastebins load. Real-time data of India's city Pune is taken for the system's implementation. A grocery management system is proposed in [18] where the system used IoT and cloud computing technologies in a way to manage products. Sensors are used to quantify the product listings. This provides a new revolution in the e-commerce system. Smart Plant System (SPS) is proposed in [19] where the system basically uses the concept of the notification system, used in different smart devices. When plants need water notification is sent to the owner about it. Moreover, IoT has potential applications in all fields in the smart world.
IoT has its various application domains with a different number of users, different suitable communication technologies, network size, different bandwidth and their relevant testbed applications such as for smart home implementation, Radio Frequency Identification (RFID) [20] and Wireless Sensor Networks (WSN) [21] communication technologies with small bandwidth are required. Whereas for smart city implementation, RFID and WSN with large bandwidth and many users are required to efficiently test the results. The number of IoT sensors and devices is rapidly increasing and people are adopting this technology to perform their work in a better way. An estimation said that the number of connected IoT devices will increase by up to 50 billion devices. In short IoT technology refers to a virtual and wireless connection of sensors and devices with real-time things such as processes, people, vehicles, animals, homes, and industry which provides automatic communication among devices without human intervention. Besides all these benefits this technology as being an emerging one poses some challenges at its initial phases such as poor energy, poor management, security and privacy issues [22]. Security and privacy is the main concern in the IoT network and this is the most considerable issue as the devices are connected through the internet and have confidential information stored which cannot be compromised at any cost. There are many attacks that can steal critical information of participants stored in the IoT cloud storage and the lost information can be used for illegal purposes by attackers. So the privacy of the participants must be considered for preventing unauthorized access to the user’s data and to make it secure and reliable.
The objective of this paper is to describe and overview the IoT architecture with its basic concepts, elements, protocols, and some recent security challenges. The paper is organized as follows: Section 2 describes the architecture of IoT and section 3 describes the basic IoT elements with brief details. Section 4 represents some standard protocols of IoT. Section 5 represents some security challenges of IoT architecture. Section 6 proposes some future directions for securing IoT architecture. Section 7 concludes the paper with concluding remarks.
2. Architecture of IoT
The IoT network solution provides outstanding opportunities to individuals and organizations and its architecture consists of numerous sensors and devices, communication protocols, cloud storage services, and different layers. There is no single consensus and agreement which is approved universally. Different researchers have been proposed different architectures according to perception and demands. The most common and appropriate architecture described in [23], [24], and [25] is a three-layer architecture.
3. Three Layer Architecture
Three-layer architecture is the most basic architecture of conventional IoT infrastructure. These layers are the perception layer, network layer, and application layer. This three-layer architecture provides the main idea of IoT with these three basic layers.
-
The perception layer is also referred to as the physical/sensor layer. It works as a replacement of real-world objects perception and is responsible for the identification of the information and data, collection of data from objects in real-time. These sensors and devices include RFID, WSNs [26], and different types of surveillance cameras that are selected according to the requirements of the application scenarios [27].
-
The network layer develops a connection between the perception layer and the application layer. It takes data from the perception layer and transmits the received information with some network technologies such as Zigbee, Bluetooth, WiFi, routers, and gateways to the application layer for further processing [28].
-
The application or presentation layer of IoT architecture includes cloud storage and servers to save the coming information from the perception layer via the network layer and it defines and delivers specific service to the end-users. These services vary according to the collected information coming from the perception layer.
4. Four Layer Architecture
The three-layer architecture of IoT is the most basic architecture and is considered as outdated with the rapid increase in the development of IoT technologies and applications. It was difficult for the developers to make any change in the application with flexibility and ease. This architecture was not suitable for scalable applications as the scalability in the architectures has come into being in recent years [29]. Therefore, a four-layer architecture was proposed by researchers to overcome the issues of three-layer architecture [30]. It includes four layers with an additional layer that is a support layer/ platform layer. The other three layers are the same as three-layer architecture and the support layer comes between the network layer and application layer. Figure 2 depicts and differentiates these described two architectures of IoT.
-
The support layer is added for improving the security of data storage in the IoT network. In conventional three-layer architecture data from the perception layer sent directly to the network layer. But in four-layer architecture, the data and information gathered from the perception layer is sent to the support layer first. This layer is responsible for checking the data authenticity and it transmits data to the network layer after approving data with some authentication methods.
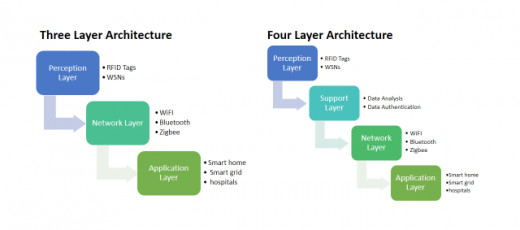
Figure 2: Architectures of IoT
5. Elements of IoT
The IoT network is comprised of various connected devices over the internet where data is collected from the real-time environment and processed information to generate the results according to the application. In order to perform all operations over the network in a proper way, there are some basic elements of IoT infrastructure that are important to be overviewed and understood. These elements describe the basic functionality of the IoT network and the way it works. Figure 3 depicts the hierarchy of the elements.
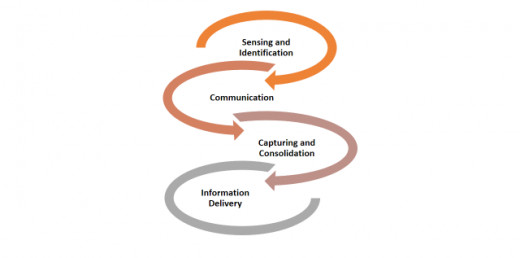
Figure 3: Elements of IoT
6. Sensing/Identification
The very first operation of the IoT network is to identify and gather data and information from the target point. This information is obtained with the specific sensing technologies according to the application [31]. The sensed data may be captured from an appliance such as cameras, RFID tags, wearable devices or some other devices. To identify each device in the network, unique addresses are assigned such as IPV4 and IPV6 [32] and IPV6 provides better addressing as compared to IPV4 addressing [33].
7. Communication
Communication is the fundamental element of the IoT network as devices require a means of communication for transmitting the obtained data to the cloud storage for further processing. Communication among devices may be wired or wireless as it depends on the nature of the network. Different communication networking technologies such as WiFi [34] (Local Area Network) LAN [35] or (Wide Area Network) WAN [36] can be used. For short-distance communications, Bluetooth [37] or Zigbee [38] communication protocols are used.
8. Capturing and Consolidation
This element of IoT network works as an actual processor of data as the gathered data from previous layers is transmitted to the cloud-based storage [39] where the information is aggregated according to the request and to provide useful information to the end-users. The consolidation of data may come from many similar IoT devices or any other internet sources
9. Information Delivery
The last element is the final delivery process of information to the end-users. These end users may be individuals (commercial or industrial) or organizations connected in the IoT network. The main objective of this element is to provide simple and transparent information and it requires the execution of all previous steps and operations with optimality across multiple platforms such as tablets, desktop and smartphone with multiple compatible OS such as IOS, Android and Windows, etc.
10. Standard Protocols
IoT protocols are basically divided into two categories such as network protocols and data protocols. Here we briefly explain some specifications of these standard protocols.
Bluetooth: The most broadly used wireless technology for short-range coverage is Bluetooth. Bluetooth protocol for IoT is Bluetooth Low Energy (BLE) protocol.
WiFi: It provides quick communication and transfer of information with efficient control over the large volume of data. The WiFi standard 802.11 presents the ability to transfer higher megabits per second.
Zigbee: It is a standard protocol for industrial area and usually operates at a frequency speed of 2.4GHZ. It provides small rates of transferred data among homes and buildings. It is popular for providing security in the IoT network with low power and high node counts.
MQTT: It is a message protocol and abbreviated as Message Queue Telemetry Transport. This is usually considered in the remote areas in the IoT network. MQTT takes data from many electrical devices and transmits this information to the IT infrastructure.
CoAP: Constrained Application Protocol is a utility protocol and its main task is to restrict smart gadgets. This protocol is used in an identical and restricted environment. It includes various general devices and different restrained networks joined on the internet.
NFC: Near Field Communication allows the participants in the network to communicate with electronic devices and to use the contents with contactless payment transactions. It covers the 4cm area between devices for accessing and sharing information.
RFID: Radio Frequency Identification protocol works with wireless technology. It uses electromagnetic waves to identify objects and devices. The range of RFID is from 10cm-up to 200 mm.
AMQP: Advanced Message Queuing Protocol is a protocol for the application layer in the IoT network. It is based on message-oriented architecture and is usually used for middleware infrastructure. It is an international standard protocol.
11. Security Challenges and Possible Solutions
IoT has revolutionized the modern world with connected devices and connected people with smart devices, but there are still some open security challenges exist in the field that is important to consider. In the past few years [40].
-
The botnets are increased in the IoT devices in which hackers control the connected devices remotely and use the confidential data of connected users without knowing them. This becomes more severe in organizations where real-time security checks cannot detect and track these botnets [41]. Real-time security solutions must be installed at every level of the IoT network and must be operated frequently to avoid any sudden attacks.
-
With the proliferation of IoT edge devices and objects in the network, security is being compromised and this becomes a challenging task for security professionals [42]. This issue can be overcome by building more IoT networks instead of scaling the existing network.
-
Encryption is one of the best security solutions to be secure in the network. But because of the low storage and processing power of the network, the encryption algorithms can be easily manipulated by hackers [43]. There is a need for more powerful encryption algorithms which cannot be compromised easily.
-
Phishing [44] is a huge security threat across all enterprises and it is the most common type of all attacks. The hacker sends a corrupted signal to an IoT device and it disturbs the working of that device by triggering various complications. This threat must be taken into account by training participants with different common symptoms of this attack.
-
User privacy is the main concern of any network or organization. Many participants are using IoT devices. Private data of users can be compromised by breaching [45]. The participants must be able to restrict any kind of interference in their personal and confidential data by knowing them first.
12. Conclusion
IoT has played a significant role in human life by developing a more efficient and interconnected ecosystem by connecting physical objects via the internet to work smartly. In this paper, we discussed and reviewed basic three-layer architecture and enhanced four-layer architecture. Some of the basic application domains of IoT are briefly explained. The key elements and standard protocols are also overviewed with a brief description. As the IoT network is an emerging area of research and implementation, some security issues are still there. Some current security challenges and their possible solutions are suggested for future research work.
13. References
[1] A. E. Schlosser, S. Shavitt, and A. Kanfer, “Survey of Internet users’ attitudes toward Internet advertising,” J. Interact. Mark., vol. 13, no. 3, pp. 34–54, 1999, DOI: 10.1002/(SICI)1520-6653(199922)13:3<34::AID-DIR3>3.0.CO;2-R.
[2] “Internet - Our World in Data.” [Online]. Available: https://ourworldindata.org/internet. [Accessed: 11-Feb-2020].
[3] M. Oppitz and P. Tomsu, “Internet of Things,” in Inventing the Cloud Century: How Cloudiness Keeps Changing Our Life, Economy and Technology, M. Oppitz and P. Tomsu, Eds. Cham: Springer International Publishing, 2018, pp. 435–469.
[4] A. Al-Fuqaha, M. Guizani, M. Mohammadi, M. Aledhari, and M. Ayyash, “Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications,” IEEE Commun. Surv. Tutor., vol. 17, no. 4, pp. 2347–2376, Fourth quarter 2015, DOI: 10.1109/COMST.2015.2444095.
[5] D. Pal, S. Funilkul, N. Charoenkitkarn, and P. Kanthamanon, “8-Internet-of-Things and Smart Homes for Elderly Healthcare: An End User Perspective,” IEEE Access, vol. 6, pp. 10483–10496, 2018, doi: 10.1109/ACCESS.2018.2808472.
[6] M. Bobin, M. Boukallel, M. Anastassova, and M. Ammi, “9-Study of a Smart Cup for Home Monitoring of the Arm andHand of Stroke Patients,” in Proceedings of the 18th International ACM SIGACCESS Conference on Computers and Accessibility - ASSETS ’16, Reno, Nevada, USA, 2016, pp. 305–306, doi: 10.1145/2982142.2982188.
[7] P. J. Rani, J. Bakthakumar, B. P. Kumaar, U. P. Kumaar, and S. Kumar, “11-Voice controlled home automation system using Natural Language Processing (NLP) and Internet of Things (IoT),” in 2017 Third International Conference on Science Technology Engineering & Management (ICONSTEM), Chennai, India, 2017, pp. 368–373, doi: 10.1109/ICONSTEM.2017.8261311.
[8] M. Naphade, G. Banavar, C. Harrison, J. Paraszczak, and R. Morris, “Smarter Cities and Their Innovation Challenges,” Computer, vol. 44, no. 6, pp. 32–39, Jun. 2011, doi: 10.1109/MC.2011.187.
[9] E. Park, Y. Cho, J. Han, and S. J. Kwon, “4-Comprehensive Approaches to User Acceptance of Internet of Things in a Smart Home Environment,” IEEE Internet Things J., vol. 4, no. 6, pp. 2342–2350, Dec. 2017, doi: 10.1109/JIOT.2017.2750765.
[10] K.-H. Yeh, “A Secure IoT-Based Healthcare System With Body Sensor Networks,” IEEE Access, vol. 4, pp. 10288–10299, 2016, doi: 10.1109/ACCESS.2016.2638038.
[11] C. Kamienski et al., “11-Smart Water Management Platform: IoT-Based Precision Irrigation for Agriculture,” Sensors, vol. 19, no. 2, p. 276, Jan. 2019, doi: 10.3390/s19020276.
[12] M. Adam and M. E. Okasha, “3-Waste Management System Using IoT,” p. 4.
[13] “Security in RFID based smart retail system - IEEE Conference Publication.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/7724331. [Accessed: 11-Feb-2020].
[14] “Internet of Things Based Smart Grids Supported by Intelligent Edge Computing - IEEE Journals & Magazine.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/8727940. [Accessed: 11-Feb-2020].
[15] A. Çaylı, “Internet of Things and Agricultural Applications,” p. 9, 2019.
[16] R. K. Borah, “1-IoT based smart garbage collection system,” p. 4, 2018.
[17] G. K. Shyam, S. S. Manvi, and P. Bharti, “18-Smart waste management using Internet-of-Things (IoT),” in 2017 2nd International Conference on Computing and Communications Technologies (ICCCT), Chennai, India, 2017, pp. 199–203, doi: 10.1109/ICCCT2.2017.7972276.
[18] J. Kaur and P. D. Kaur, “19-CE-GMS: A cloud IoT-enabled grocery management system,” Electron. Commer. Res. Appl., vol. 28, pp. 63–72, Mar. 2018, doi: 10.1016/j.elerap.2018.01.005.
[19] A. Voit, M. O. Salm, M. Beljaars, S. Kohn, and S. Schneegass, “7-Demo of a smart plant system as an exemplary smart home application supporting non-urgent notifications,” in Proceedings of the 10th Nordic Conference on Human-Computer Interaction - NordiCHI ’18, Oslo, Norway, 2018, pp. 936–939, doi: 10.1145/3240167.3240231.
[20] “RFID technology and its applications in Internet of Things (IoT) - IEEE Conference Publication.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/6201508. [Accessed: 04-Feb-2020].
[21] “Convergence of MANET and WSN in IoT Urban Scenarios - IEEE Journals & Magazine.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/6552998. [Accessed: 04-Feb-2020].
[22] I. Yaqoob et al., “Internet of Things Architecture: Recent Advances, Taxonomy, Requirements, and Open Challenges,” IEEE Wirel. Commun., vol. 24, no. 3, pp. 10–16, Jun. 2017, doi: 10.1109/MWC.2017.1600421.
[23] I. Mashal, O. Alsaryrah, T.-Y. Chung, C.-Z. Yang, W.-H. Kuo, and D. P. Agrawal, “Choices for interaction with things on Internet and underlying issues,” Ad Hoc Netw., vol. 28, pp. 68–90, May 2015, doi: 10.1016/j.adhoc.2014.12.006.
[24] S. Leminen, M. Westerlund, M. Rajahonka, and R. Siuruainen, “Towards IOT Ecosystems and Business Models,” in Internet of Things, Smart Spaces, and Next Generation Networking, vol. 7469, S. Andreev, S. Balandin, and Y. Koucheryavy, Eds. Berlin, Heidelberg: Springer Berlin Heidelberg, 2012, pp. 15–26.
[25] “Research on the architecture of Internet of Things - IEEE Conference Publication.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/5579493. [Accessed: 11-Feb-2020].
[26] N. Khalil, M. R. Abid, D. Benhaddou, and M. Gerndt, “Wireless sensors networks for Internet of Things,” in 2014 IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), 2014, pp. 1–6, doi: 10.1109/ISSNIP.2014.6827681.
[27] N. Ye, Y. Zhu, R. Wang, R. Malekian, and Q. Lin, “An efficient authentication and access control scheme for perception layer of Internet of Things,” Jul. 2014, doi: 10.12785/amis/080416.
[28] O. Bello, S. Zeadally, and M. Badra, “Network layer inter-operation of Device-to-Device communication technologies in Internet of Things (IoT),” Ad Hoc Netw., vol. 57, pp. 52–62, Mar. 2017, doi: 10.1016/j.adhoc.2016.06.010.
[29] C. Zhong, Z. Zhu, and R.-G. Huang, “Study on the IOT Architecture and Access Technology,” in 2017 16th International Symposium on Distributed Computing and Applications to Business, Engineering and Science (DCABES), 2017, pp. 113–116, doi: 10.1109/DCABES.2017.32.
[30] “Smart gateway based communication for cloud of things - IEEE Conference Publication.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/6827673. [Accessed: 11-Feb-2020].
[31] D. C. Bogatinoska, R. Malekian, J. Trengoska, and W. A. Nyako, “Advanced sensing and internet of things in smart cities,” in 2016 39th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), 2016, pp. 632–637, doi: 10.1109/MIPRO.2016.7522218.
[32] T. Savolainen, J. Soininen, and B. Silverajan, “IPv6 Addressing Strategies for IoT,” IEEE Sens. J., vol. 13, no. 10, pp. 3511–3519, Oct. 2013, doi: 10.1109/JSEN.2013.2259691.
[33] I. Grønbæk, “Architecture for the Internet of Things (IoT): API and Interconnect,” in 2008 Second International Conference on Sensor Technologies and Applications (sensorcomm 2008), 2008, pp. 802–807, doi: 10.1109/SENSORCOMM.2008.20.
[34] “Implementation of WiFi-based single phase smart meter for Internet of Things (IoT) - IEEE Conference Publication.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/8075793. [Accessed: 11-Feb-2020].
[35] “US7289472B2 - Handoff method of wireless local area network (LAN) - Google Patents.” [Online]. Available: https://patents.google.com/patent/US7289472B2/en. [Accessed: 11-Feb-2020].
[36] “US6339594B1 - Wan-based gateway - Google Patents.” [Online]. Available: https://patents.google.com/patent/US6339594B1/en. [Accessed: 11-Feb-2020].
[37] “Bluetooth: a viable solution for IoT? [Industry Perspectives] - IEEE Journals & Magazine.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/7000963. [Accessed: 11-Feb-2020].
[38] “A connectivity-increasing mechanism of ZigBee-based IoT devices for wireless multimedia sensor networks | SpringerLink.” [Online]. Available: https://link.springer.com/article/10.1007/s11042-017-4584-2. [Accessed: 11-Feb-2020].
[39] “Bringing IoT and Cloud Computing towards Pervasive Healthcare - IEEE Conference Publication.” [Online]. Available: https://ieeexplore.ieee.org/abstract/document/6296978. [Accessed: 11-Feb-2020].
[40] B. L. Risteska Stojkoska and K. V. Trivodaliev, “A review of Internet of Things for smart home: Challenges and solutions,” J. Clean. Prod., vol. 140, pp. 1454–1464, Jan. 2017, doi: 10.1016/j.jclepro.2016.10.006.
[41] E. Bertino and N. Islam, “Botnets and Internet of Things Security,” Computer, vol. 50, no. 2, pp. 76–79, Feb. 2017, doi: 10.1109/MC.2017.62.
[42] V. Adat and B. B. Gupta, “Security in Internet of Things: issues, challenges, taxonomy, and architecture,” Telecommun. Syst., vol. 67, no. 3, pp. 423–441, Mar. 2018, doi: 10.1007/s11235-017-0345-9.
[43] “Security of the Internet of Things: perspectives and challenges | SpringerLink.” [Online]. Available: https://link.springer.com/article/10.1007/s11276-014-0761-7. [Accessed: 11-Feb-2020].
[44] B. B. Gupta, N. A. G. Arachchilage, and K. E. Psannis, “Defending against phishing attacks: taxonomy of methods, current issues and future directions,” Telecommun. Syst., vol. 67, no. 2, pp. 247–267, Feb. 2018, doi: 10.1007/s11235-017-0334-z.
[45] S. Li, L. D. Xu, and S. Zhao, “5G Internet of Things: A survey,” J. Ind. Inf. Integr., vol. 10, pp. 1–9, Jun. 2018, doi: 10.1016/j.jii.2018.01.005.
This article is accurate and true to the best of the author’s knowledge. It is not meant to substitute for diagnosis, prognosis, treatment, prescription, or formal and individualized advice from a veterinary medical professional. Animals exhibiting signs and symptoms of distress should be seen by a veterinarian immediately.
© 2020 Hamza Sami Ullah