Security for "The Internet of Things"
How does it work now?
The Internet of Things is here and it’s growing rapidly. It's popular among ordinary people who want to automate their home but also to the IT experts.
The phenomenon known as IoT is not a new concept. This coin was used for the first time in 1999 to describe the network to which all things will be connected. Originally conceived, it used Radio-frequency identification technology - RFID. So by applying this concept, your water heater would be connected to the network (Internet). Based on your movement pattern, it would be able to decide when you need more or less hot water. This 'smart' water heater could be controlled via Android application if you decide to go back from vacation sooner. It's smart, isn't it? Ingenious.
But what about the security of this devices and a way of accessing them? Well, you'll say: "Everything is locked in the apartment. The electricity bill can be a bit bigger. When I come back from a vacation I will reset the password." What about having independent central heating attached to this network? When you go to the vacation, malicious neighbor turns on the heating in the mid of August. This would raise the temperature and led the heating system in a disaster. Such a situation provokes an unavoidably higher cost of repairing.
Imagine the situation in which you have a refrigerator, which would be able to make a conclusion about what food you need and to buy it instead of you. You go travel and realize that you do not have the funds on the card because your refrigerator bought the used car. This kind of a fridge is already available to buy in every country. Not to mention that a lot of houses already have video surveillance that is set for accessing the mobile phone applications. If you do not change the default passwords and protocols, you will make hackers to know when you are not at home.
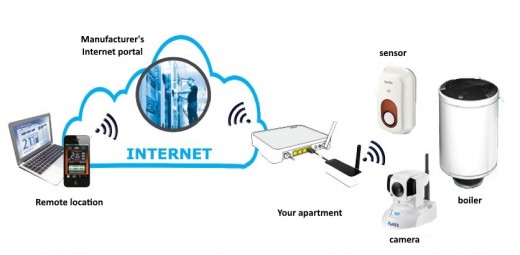
The examples are to attract the reader's attention. They are related to the use of 'smart' devices in the households. The far more serious area of application of the IoT devices is their implementation in the production process automation, agriculture, traffic management, etc. The security of such systems is equally important, both from the aspect of human and process vulnerability in these areas, as well as from the vulnerability of data due to the availability of sensitive systems and servers on the Internet.
Security experts appeal to manufacturers for raising the level of security to their products, given the fact that the network of 'smart' devices is growing more and more. Given the prevalence of these devices in and outside corporate networks, it is important not only to be ready to protect your own organization, but it is vital that you realize how far the risk of smart devices can rise.
What about the researches?
Let's deal with the research. According to the fact that AT&T IoT Cybersecurity Alliance's last year white paper, the 'Mirai' malware was the main risk for unsecured smart devices. Exposing personal information is a major threat to compromise your device. However, according to the report, your 'smart' devices can be used in a widespread attack. In this case your organization's reputation may be affected. The worse situation for your organization is to be the victim of a compromised 'smart' device of your business partner.
One research predicts that by 2020, more than 20 billion 'smart' devices will be in use (look at the table below). This number will increase from 8.4 billion in 2017. The largest percentage, about 63%, represents 5.2 billion devices of consumer devices (for households and individuals). The remaining 3.1 billion devices are in function with business users. In consumer's environment, 'smart' devices are most represented in cars, then in smart TVs and digital set-top boxes, while in the organizations and businesses there are a large number of 'smart' devices with the function of smart sensors and security cameras.
Gartner's research in 2017
Category
| 2016
| 2017
| 2018
| 2020
|
|---|---|---|---|---|
Consumer
| 3,963.0
| 5,244.3
| 7,036.3
| 12,863.0
|
Business: Cross-Industry
| 1,102.1
| 1,501.0
| 2,132.6
| 4,381.4
|
Business: Vertical-Specific
| 1,316.6
| 1,635.4
| 2,027.7
| 3,171.0
|
Grand Total
| 6,381.8
| 8,380.6
| 11,196.6
| 20,415.4
|
Gartner engaged in a serious research in 2017
AT&T IoT Cyber-security Alliance's research
- Demystifying IoT Cybersecurity
Mirai and similar malware also demonstrate how IoT risk extends beyond your own organization.
The implications of security
Like any type of cyber attack, the implications of the attack on 'smart' devices are far-reaching. That is why IT security experts must approach the security problem of the 'smart' device just like to the computer network, cloud systems, workstations, and other endpoint devices. A comprehensive strategy is essential as a necessary procedure for securing your organization and preventing cyber attacks.
The level of investment in the Internet of Things security is different. Some companies invest a lot of money into the development of security mechanisms for their IoT devices. Others focus on faster production, while security comes later with updates or newer OS versions of the device. IT security specialists have to consider this when making a risk analysis, as well as in the implementation of security procedures and mechanisms to protect the system. There has to be done a lot for securing the next step towards 'smart' devices security.
Good practice in four steps
Well, every CSO would ask the same question: "If you can give me an advice on IoT security, what would that be?" The answer is, "Get to know your system!" Initially, you must maintain visibility before implementing any protection - You cannot protect what you do not see. What should that mean? Each organization must have an inventory of its online assets, including services (not just devices).
Risk analysis and security implementation are based on the answer to the question: "If my service breaks down, how much would that cost my company in money and what would be the damage to our brand?" With that starting point, you should be prepared for each IoT-devices security challenge. Do that by defining risks and taking steps to preempt unwanted situations and be prepared to recover in case the attack still occurs.
There are four steps you must follow to establish a secure IoT system:
- Install the patches
- Backup
- Focus on visibility
- Link your defense
1 - Install the patches
First of all, the key thing is installing patches. For example, WannaCry has exploited the failure of organizations that did not install security patches at the time when they appeared and were available for download. Organizations not affected by this attack had strong security procedures that, of course, implied the application of the patch as soon as they emerged. Of course, WannaCry did not target IoT. Imagine having something similar rather than data encryption. For example, your device is being exploited for a mining cryptocurrency or DDoS attack, although the manufacturer has published all patches and installation procedures for months. Installing the patch is fine. But what should you do if the manufacturer does not release security patches? There are billions of devices running, without the support of the manufacturer, or the company that produced the device no longer exists. In this case, an IPS (Intrusion Prevention System) must be applied. The IPS system is a device - a security system that enables a preventative network security approach, that is, a system used to identify potential threats and which responds very quickly to them, or prevents the system from being infiltrated.
2 - Backup
Next, pay attention to making your backup copies. Particular attention should be paid to scanning of backups in order to eliminate the suspicion that they are infected. Backup needs to be subdivided (segmented), that will protect you from service-to-service attacks, which is expected to increase this year.

3 - Focus on visibility
Thirdly, focus on the visibility of data and parts of the system. Setting up a defense perimeter (IPS, firewall, etc.) is not enough. Once the perimeter is breached, due to the visibility of the whole system, the company can easily identify what the attacker is doing (for example, the entire network behind the router is in one VLAN). Just by carefully considering and studying the attacker's technique, you can understand their goals and motives, so make the segmentation of your device's network (different VLANs). Likewise, you can use different communication protocols. For example, you do not have to use the TCP/IP protocol on the whole network. Also, you should start removing your devices from accessing the internet. If the complex system can not be effectively protected, then it must be isolated from any external access.
4 - Link your defence
Linking security systems is an unavoidable measure in establishing the security. Proactive security solutions have to be linked, so they all work together. You need to follow the security solutions from manufacturer's website, looking for ways to integrate devices provided by different manufacturers. By reducing the complexity of the security system and the automation of interoperability between different security systems, you will gain in efficiency and faster defense. Everything that is good - is simple, right? Yes and no, but you do not have to make it complicated by accumulating firewalls, routers, and various settings on them.
Security of 'smart' home devices
The above-mentioned recommendations - techniques are related to larger systems or IoT business networks. Of course, they are also applicable to IoT of customer's network. On the other hand, it is very unlikely that you will buy Intrusion Prevention System to protect the network in the apartment because it costs as much as the apartment you want to secure. Therefore, a few modified procedures and recommendations should be followed.
- Study your 'smart' devices - and what they are doing or what functionalities they have.
- Disable remote access if not necessary.
- Install patches, whenever they appear, on all the mobile devices that you control your 'smart' devices, including the 'smart' devices themselves. If an attacker can access your door-opening system or a smart thermostat through a malicious application embedded in your mobile device, there will be a disaster.
- Install the security software (antivirus) on your mobile device from which you are controlling your IoT devices.
- Protect your WiFi network using advanced protocols (WPA2) and strong, complex passwords. Do not make any relevant ports open for external access to the router. If the manufacturer's web service for controlling your 'smart' device offers the configuration of these ports - that is a very good option. Disable SSID advertising for your wireless network. Make two different WiFi networks if your router can work with multiple SSIDs (if not, get one).
- Use one network for computers, phones, and other web activity, and another for smart devices.
- Use strong passwords. Most users leave default passwords, both on routers and on devices in the network.
- Also, pay attention to the access credentials you use to access the manufacturer's portal through which you access your 'smart' devices.
- Most important, determine the 'visibility' of your 'smart' devices yourself. Do neighbors and friends have to know that you monitor your camera over the mobile phone?
Would you buy a smart refrigerator?
Things will get better
Companies involved in the production of security systems are aware of threats to which 'smart' devices are exposed. They are developing products that include functionality for secure remote access and authentication, as well as protection against malware and viruses. According to Fortinet's survey, over 61% of respondents in the USA say they will do some kind of automation through 'smart' devices in their homes for the next 5 years. Hackers will be prepared to take advantage of every failure. You should not be pessimistic, no technology has been invented for taking advantage of its bad side. The battle is just at the beginning. The customers will come to those manufacturers that offer the highest functionality and security.