Mobile Apps - Advantages and Disadvantages
Early mobile apps
You may recall the early days of accessing the internet from mobiles – awkwardly rendered desktop web-pages on the mobile made it difficult to navigate the content and it seemed absurd to try to fit web content into such a small form factor. Over time, the web-pages were created in two versions – based on the type of device, you would get a customized web-page that rendered passably well on your device.
Research in Motion (RIM) pioneered pagers that provided access to email towards the end of the last century. But, they really rose to fame at the turn of the century, giving enterprise users the convenience of accessing mail and other office applications over the mobile network using Blackberry. The decade until 2010 could be called the decade of the Blackberry – although the Apple smart-phone and subsequently the Android phone made its appearance in the latter part of the decade, the Blackberry was a status symbol for enterprise users all through the decade. Seamless integration with Microsoft Exchange was one of the main features of Blackberry. I also fondly recall the classic non-touch Blackberry phone model, where the screen took up two thirds of the phone area and the keys (with all keys like a standard keyboard) the bottom one third (was half and half in early models).

As per Wikipedia, there were many known celebrity users of Blackberry – including the previous US President, Barack Obama and interestingly, Eric Schmidt of Google who professed that he preferred using the Blackberry keyboard to a touch screen.
What RIM did not, probably, recognize at that time was the fact that enterprise users, although a strong segment to target were only a small percentage of the consumer user segment. Apple and Google were quick to pick up on the needs of the consumer segment and started creating standard “apps” or applications for the familiar activities on a smart-phone – accessing mail, storing and using media etc. It turned out that enterprise users were just one use-case among the universe of possibilities.
This universe expands to infinity when anyone is allowed to build an app for the mobile platform.
Smart-phone Platform Architecture
The arrival of smart-phones offering a layered architecture, heralded a new age in application programming.
Android, having its roots in the public domain Linux OS (Operating System), gave the technical community the first feel of an open mobile operating system. With clearly defined libraries and a published Application Program Interface (API) layer, it now became easy to port some of the well-known web applications onto the Android platform. Eventually, this has resulted in the paradigm shift today, where there are apps exclusively written for the mobile platform.
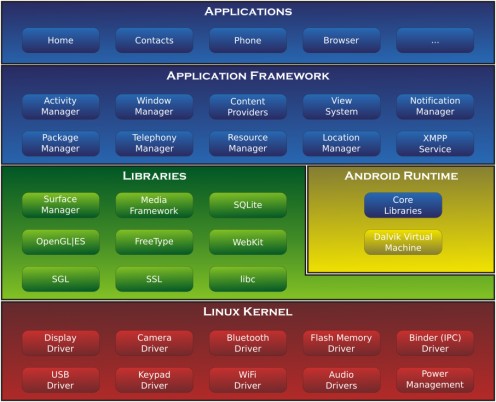
The Android developer community demonstrates a strong engagement between the Android developers and the third party app builders. New Android features and how to use them are explained, discussed and success stories of apps shared.
The Apple mobile OS (iOS) also has distinguished roots – it is based on the "Linux-like" Darwin OS. The focus of iOS as with all Apple products, is on a cutting-edge user interface. Initially, Apple never intended opening up the platform to the technical community of developers, however, with the floodgates opening on Android, Apple has been forced to accept the model of third party apps being made available on their platforms. iOS also has a layered architecture similar to the diagram above for Android:
-
The cocoa touch layer – where the applications reside
-
The media layer – which offers the development frameworks and APIs
-
The core services layer – being the underlying basis of the media layer where the standard OS functions reside
-
The core OS layer – comprises the device drivers, networking functions and all low-level hardware oriented activities
Apple has also mobilized a strong developer program which provides support to the app development community.
A Vibrant Ecosystem is Good News for the User
The average app user never had it better – any kind of action that you would like to do on the internet has an app defined, actually even some kinds of actions that you never envisaged, have apps. If the user does not want to spend money on the premium versions of the apps, there are alternate advertisement supported versions that give partial functionality. Everyone recommends apps to their contacts – also via a mobile app. Whatsapp has probably achieved a distinction of providing a messaging function on steroids, that has permeated our world to such an extent that most users cannot dream of ignoring it even for a few hours.

So What is the Catch?
As with any good thing, “familiarity breeds contempt”. Users have got used to these ubiquitous apps and think nothing of going into the Google Play store or Apple App store and downloading an app. There are the pesky startup screens that one tends to chafe about – sometimes providing information about data privacy and sometimes informing about the permissions that the app requires. This is just information for the user – there is no actual option available at this point to refuse a permission that an app wants.
Android was historically known to be lax in this area, and it has been somewhat rectified in newer versions by allowing the user a subsequent point (when the app starts up) to allow or deny specific permissions to the app.
Note: The rest of the discussion speaks more of the Android perspective, simply because I have more information available personally on this platform. It is also a known fact that Android usage is more prevalent all over the globe.
Nobody can hurt me without my permission.
— Mahatma GandhiThe New Take on Permissions
Gandhi's wisdom quoted above is fully applicable in the app context - the app user has the ultimate control of choosing not to use an an app whose permission-list looks strange. But first, what are these permissions?
At its simplest level, a permission allows an app to use a functionality present on the phone (like camera) or allows access to data (like your contacts). The Android official listing of permissions is significantly large. As a user, you require a basic understanding of the more “severe” permissions, what could be a legal usage scenario and what could be a repercussion of improper usage.
Have you Downloaded Apps Without Reviewing Permissions?
Permission
| Legal Usage
| Improper Usage
|
|---|---|---|
Location (precise location, GPS and Network)
| A mapping app that is giving you directions or a mall based app that gives you offers
| Logging your locations and building a map of where you have been
|
Photos/media/files (read/modify/delete from your USB storage)
| A photo beautifier app that helps improve your photos, could be attached to social media sites
| Copying all available information and using inappropriately – monetizing, analytics, publishing etc
|
Camera – take pictures and videos
| A mapping app that is giving you directions
| Spying and transmitting the pictures/videos
|
Disable screen lock
| Video viewers
| Compromise privacy unintentionally
|
SMS/MMS – read/send
| App using SMS info (retreive OTP from SMS and use in app)
| Copying all SMS data and building information on your SMS usage pattern Sending illegal SMS/MMS
|
Calendar – read/modify/update calendar
| Scheduler apps or apps that drop event reminders to calendar
| Logging your calendar and building historical information on your day, adding unintended appointments
|
Contacts – read/modify/update
| Specialized contact management apps
| Illegal use of contact info (you can be sent malware from a contact email address, all contacts could be phished/spammed)
|
Personal information
| Authenticating using known parameters set on mobile
| Illegal use of personal info (even IMEI: the hardware identifier of the mobile phone) can be retreived
|
From the subset listed in the table, it is clear that there are both legal and illegal usage scenarios for each type of permission. However, as a user, you have no control on what type of usage is being done by the specified app.
A significantly higher risk is associated with apps that run off social networks – it is possible that an innocuous game or quiz accesses your historical personal data available in the social network (where you may have voiced opinions, demonstrated personality traits and affiliations). This has been evidenced by numerous high-profile cases that have been in the press in recent times.
The underlying issue is that the average user is not technically qualified to understand the potential impact of permissions. At the same time, there is a novelty value of a new app or a sense of peer pressure when someone in your network is using the latest/greatest app, which you have not yet downloaded. This is a heaven sent opportunity for malicious hackers – they can directly burrow into your most personal device, that you retain at all hours of the day or night. They can retrieve any and all information based on the permissions that they have stated.
Can I Protect Myself?
The biggest weapon for the user is education. While you can be technologically averse, the world today is beyond a stage where you can hide behind this statement and open yourself to risk. Before installing any app the user can do some background checks:
-
Is the app developer familiar – apps from well known organizations can usually be trusted
-
Review the app description and check for any ratings/third party reviews on the internet
-
Review the permission list – does it give an intuitive feel of being in-line with the app description? If not, you can use your favorite search engine to look up the details of any permission that seems strange to you. Within the top ten hits you are likely to get an explanation of the permission and usually even information about app types that use that permission.
-
In case you are unhappy with some permission, you can email the app developer and request for information about the permission. Some app developers give a clear explanation, but cases of no response or a vague response can get you stuck.
Some people consider number of downloads as a parameter to check, but I am not convinced of the usefulness – if the app has a problem, the users are affected whether it is two users or two million users. On the other hand, if there was a problem, one of two million users is likely to sound an alarm rather than one of two users.
Any point in the background check, where you feel a lack of comfort, you should exercise your option to not download and install the app. The problem comes from apps that look okay mostly, but ends up listing one permission that looks nasty – here, it is a call that the user has to take balancing the benefits of the app against the risk of misuse of that permission. For instance, some of the cab hailing apps seem to ask for permissions that seem unrelated to the app – the company reputation can be a factor in overriding the risk of lax permission.
Newer versions of Android (6.0 and up) allow more fine-grained control on permissions.
. The user is provided an allow/deny pop-up the first time an app tries to access a permission. Also permissions can be configured via the settings – some of the older apps may not run without some specific permissions and you will get a pop-up window explaining the situation if that happens. You can also review app permissions from the "Settings" app and decide to revoke some of them.
Enjoy Your Apps!
As a user, you have the abilities to keep yourself informed and exercise your discretion while using apps. The profligacy of apps simply puts choice in the hands of the user - exercise it, and enjoy all the apps that you like!
© 2018 Saisree Subramanian








