- HubPages»
- Technology»
- Computers & Software»
- Computer Software
New Method to Check for Surveillance Software on Your Windows-based PC
Level of Security
The Problem
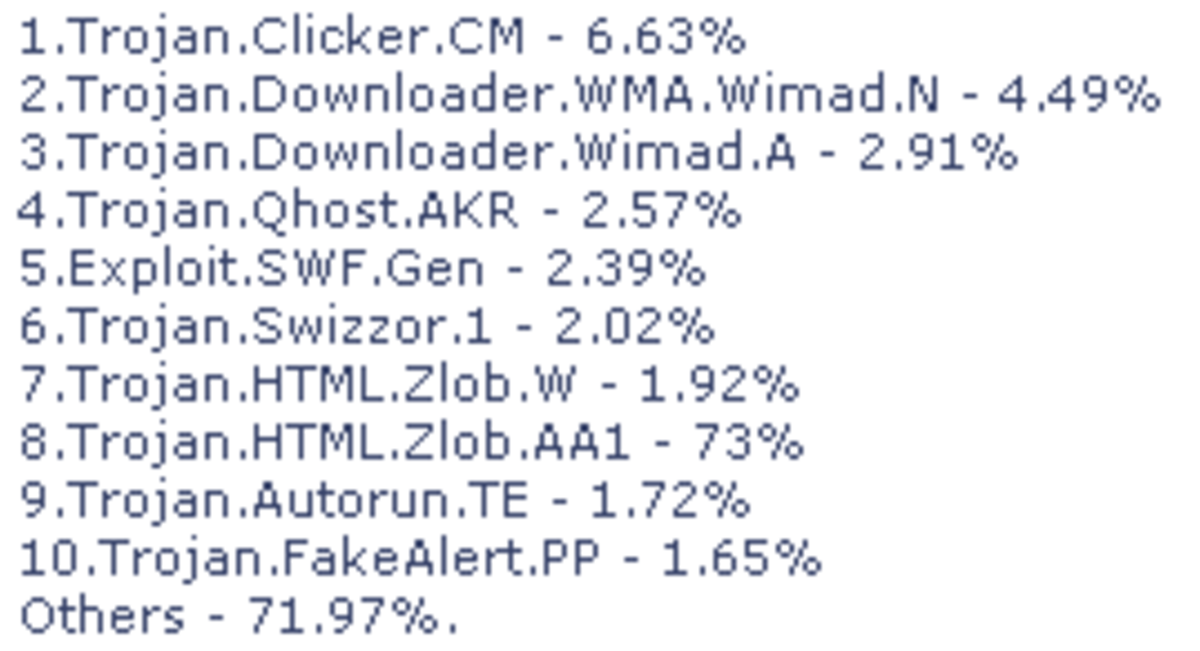
In an age where journalists are being jailed, killed, and being forced to either comply or quit their jobs due to government oversight of the subject matter they are or are not allowed to report, various tools are arriving on the scene to help out. When Egypt hit the Internet Kill-switch, Google and Twitter joined forces to help people armed with only a basic cellular feature phone get word out about what was going in. Anonymous DNS servers such as TOR and others are becoming more widely used and have actually earned the name, "The Dark 'Net" by law enforcement agencies because of the trouble they are having tracking down offending citizens.
It's been long known as well, and been the stuff of novels and movies, that governments use surveillance software to track the computer/network usage of employees. Such software is available to parents to track their kids' usage, and to employers wanting to be sure employees are not using company hardware to waste time on adult-only content (which quite frankly can do just as much harm to your computer as to your physical brain!). The reasons for using such software are all well and good on the surface and have been used to protect company and government assets for quite some time.
The changing landscape of political and religious monitoring when it comes to human rights abuses around the world however, is creating an entirely new scenario where previously above-board software is now being used to target and harm those it is monitoring.
The Solution?
Amnesty International has partnered with several other human rights organizations to create a program that can detect if your computer has ended up with tracking code installed on it. Computer techs know this kind of software has a rootkit, a trojan, or a piece of spyware that calls home. They consist of cookie trackers, key loggers, and backdoors that give remote control to a user elsewhere online who typically has malicious intent. Malicious intent up to this point has usually been for monetary and identity theft reasons, but with governments entering the mix in countries where human rights groups, journalists, religious groups and others are being targeted for death or harassment, malicious intent is now taking on very deadly connotations.

Introducing "Detekt"
The program that scans your system for such surreptitious surveillance is called "Detekt". It must be stated from the outset that "Detekt" does exactly as it's name implies, it locates and informs you of any potential software that could be used against you. It doesn't remove it, it merely alerts you to it's presence. The makers of the software also have a very lengthy waiver stating that in the hours between release and installation of their program on your computer, governments and other agencies may be updating their code so that Detekt can't detect their presence. They strongly advise that users who have a strong suspicion of being tracked, should disconnect their PC or laptop from it's current network source and seek professional support from a computer repair technician. They also state that their software might detect legitimate programs that you want on your computer, so again, having the Detekt log reviewed by a technician can ensure your legitimate software is not affected. Cases where such false positives might occur may include remote management software solutions either in-house or through third-party tech-support companies. This tech-author installs such software on her own clients' computers. In my own test of the program however, it did not detect my remote access software running as a service in memory.
Speaking of memory, that is the primary, and apparently only place Detekt scans for such malware. As a result, the scan is remarkably quick. Detekt does not scan files or folders on the hard drive, it only scans what is running in memory. It also detects your connection to the Internet and suggests you disconnect before beginning your scan. This is good advice considering that if you did have surveillance software running, it would report back to it's server that you were using Detekt at the time.
FCS has added this downloadable executable to the software toolbox and did a test run on WinXP SP3 32bit with 3gb of RAM and a 3ghz processor. Current tests of this software on Win8x 64bit are coming in as non-operational. So although the Detekt readme file states that it will run on OS's from WinXP to Win8x in both 32bit and 64bit configurations, the Detekt authors state that Detekt will only run in the Win8x environment on the 32bit configuration. Hopefully in the future they will release a version that runs on 64bit. It also appears to be Windows-based as opposed to cross-platform. With the increasing popularity of OSX, iOS, Android and Linux, this human rights advocacy consortium would be wise to consider compiling their code to run across all currently known OS platforms.

Where to Get These Tools
- Malwarebytes | Free Anti-Malware & Internet Security Software
Malwarebytes builds industry-leading anti-malware and internet security software to keep you safe from today's online threats. - CCleaner - Download
Piriform - Authors of the hugely popular software CCleaner, Defraggler, Recuva and Speccy. - Spybot © ™ – Search & Destroy | Safer-Networking Ltd.
- AVG | FREE Antivirus Protection for All Your Devices
Download FREE antivirus software with anti-spyware and anti-malware protection for your PC, Mac, Android phone or tablet.
A Toolkit for the Home User
As usual, the average home user's anti-malware installed toolkit should include AVG Free edition, Spybot Search and Destroy, and MalwareBytes Free Edition. Be aware that AVG and MalwareBytes do want you to buy their paid versions, so installation of each must be done with care and attention. AVG should be set to scan once per day. Spybot S&D should be manually run at least once a month on computers active online, users who are not online very often can get away with scans less often. MalwareBytes is there to remove what AVG can't deal with, and many times catching more deeply-hidden threats in the process. Non-profit and educational institutions can use the free version of this trio as well, but businesses and corporations are encouraged to pay for their respective software needs, as enterprise situations often require more measures than the home user to stay safe. This trio can catch most of what is out there and if kept up to date, will continue to do so for the foreseeable future. Your technician will have additional software tools to aid in rooting out rootkits, boot-viruses and other harder-to-reach malware. So talk to them about securing your system, if you haven't already.
If you know someone who is suspicious that their behaviour online is being unnecessarily tracked, have them run the above trio in combination with another tool called C-Cleaner, with all options carefully gone through to get the deepest, cleanest scan possible without upsetting typical user work flows (for example, C-Cleaner can clean history lists in Office, removing the most recently used file information from Word, this will cause users who think files are stored in Word to freak out accusing you of just deleted their files - you didn't, but C-cleaner cleaned the recent pointers to them). After running those four programs, if your friend still suspects being tracked, it's time to bring in Detekt and see what it sees.
Do you consider yourself to be calm, wary, safe, paranoid, or none of the above?
Disclaimer!
One more thing to note about Detekt. The authors state that just because it doesn't find anything, doesn't mean your suspicious friend is clear. This sounds like a recipe for paranoia, but it is a necessary disclaimer. Detekt is not the end-all to this problem, this tool is merely meant to aid you in uncovering the suspicious activity so that a technician can assist you in removing the threat.
Does everyone need to run this tool? No! If you have never suspected tracking behaviour, there is no need to run this tool. However, if you are involved in questionable activity that could cause you to land on a government's watch list, you may consider running this tool to be on the safer side. The days of the Wild West have hit the Internet in a big way now, and it helps to have a few tools at your side.
© 2014 Marilynn Dawson