Protect Your Retina Macbook Pro - MacBook Air From Theft: Part 2 - Data Protection & Tracing A Stolen Computer
In case you missed the first part, which looked into the hardware option for protecting your Retina Macbook Pro or MacBook Air, you can still read it here.
Come back to continue with this part.
Data protection
You can do only so much to protect your MacBook from being stolen.
So, it is a good idea to prepare for the case it happens, despite all the measures you have taken to prevent it.
But even if nobody wants to steal your hardware, your content on your computer could be just as interesting for somebody. And I am sure you don’t want to see a stranger prying on your documents, bank data, photos and so on.
Apple knows that and offers within OS X a broad range of features to protect your data.
Unfortunately a lot of people are lazy and don’t want to enter passwords, so the default setting is oriented to convenience.
In order to make our Macintosh's as safe as possible, we need to activate these features, which Apple provides luckily at no extra costs.
You can find everything you need in "System Preferences”.
User account
First of all you need to setup your user account correctly. Beside the obvious - a strong password - you should consider the following.
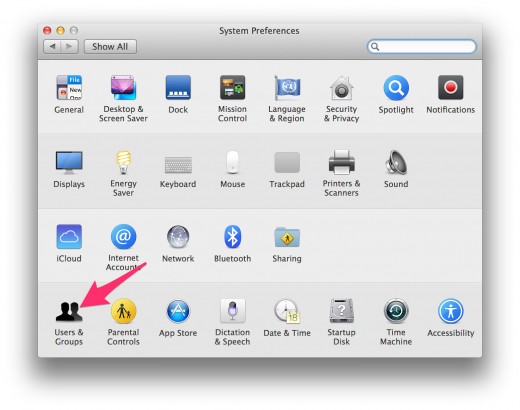
1. Click on “Users & Groups”
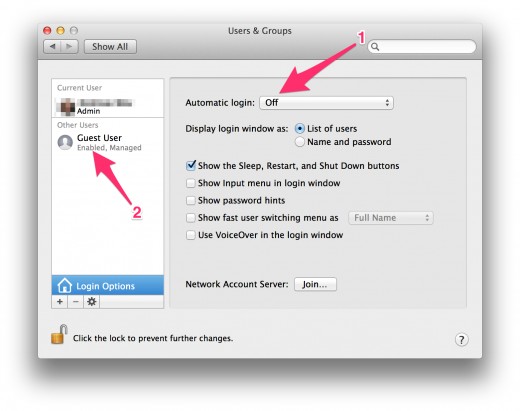
2. Make sure that the “Automatic login” is switched to “Off” (see arrow 1).
If you let this setting on, a potential data thief needs just to start the computer and gets access to everything on it immediately, without even knowing your password. Even a strong password is of no use in this case.
Bonus tip: There is always a guest account pre-set by Apple. But by default it is not active. In preparation for our final step of “Tracing a stolen MacBook”, activate the guest user account (see arrow 2). I’ll explain what for in a few minutes.
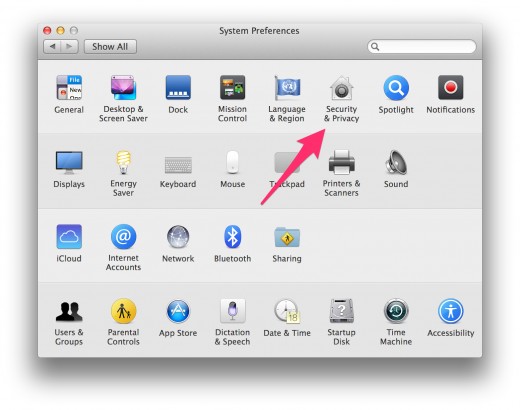
3. Next, go into "Security & Privacy"
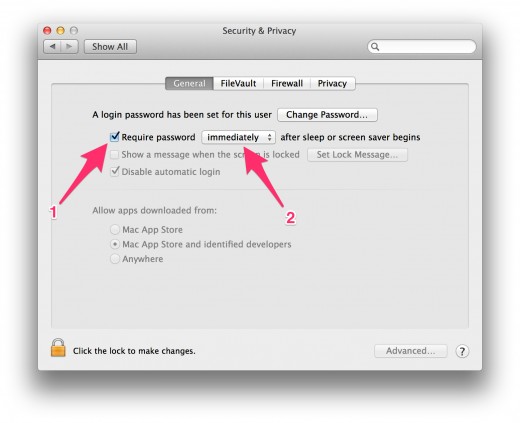
4. Click on the tab “General” and activate the first checkbox (see arrow 1) and choose “immediately” from the dropdown box (see arrow 2).
This way your computer will ask for the password, even if you have been away for just a few seconds, which could be enough time for a bad guy to get to your computer, while you fetch another coffee or talk to a colleague next door.
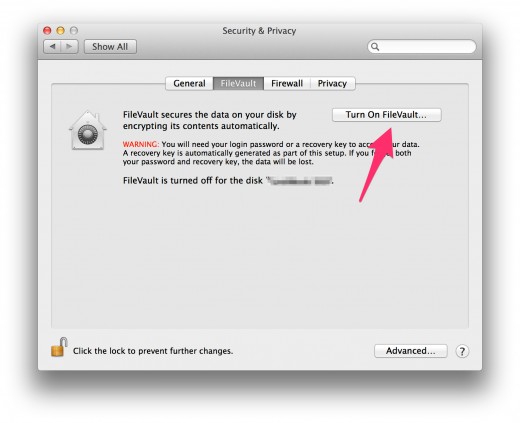
5. Now click on the tab “FileVault” and turn it on.
This will encrypt your entire disk.
Even if a thief would disassemble your computer and re-install the disk in another computer, your data will be safe, as it is not accessible without the password.
But be aware, if you ever loose your password or the recovery key, even you would loose access to your data. Therefor make absolutely sure to safe the password in a secure place!
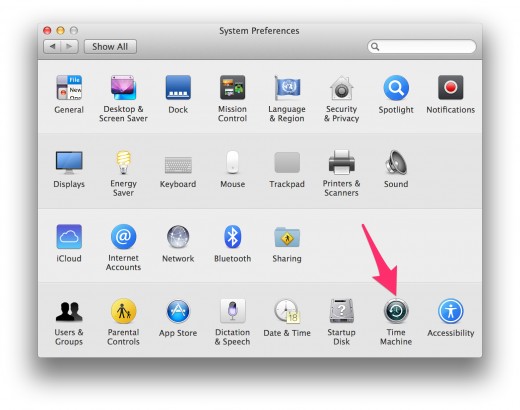
6. Backup
I know nobody likes Backups!
They are a pain in the …. But please consider to use the free backup solution from Apple called "Time Machine”.
It is extremely easy to activate with literally just a click on a button and from there on it will automatically save your data as soon as the backup disk is connected.
In case of theft of your MacBook you have a Backup at home.
If this day ever come, you’ll be so happy you did this one click, believe me!
7. Cloud services
Another option is to consider to save the most important files in a cloud service as - the likely most known one:
Dropbox (Basic accounts are for free. Here with an extra 500MB).
Again, if somebody ever steals your notebook, you’ll be so relieved to know you still have access to your most precious data.
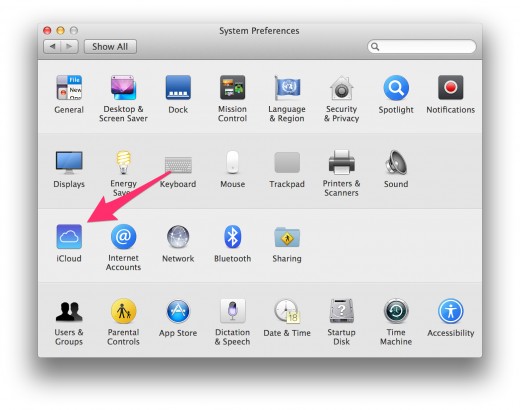
8. Setup “Find my Mac"
Now we come to preparations for the worst case scenario, when your MacBook actually gets stolen.
(I am assuming that you already setup your Apple ID.)
Click on “iCloud” (see arrow).
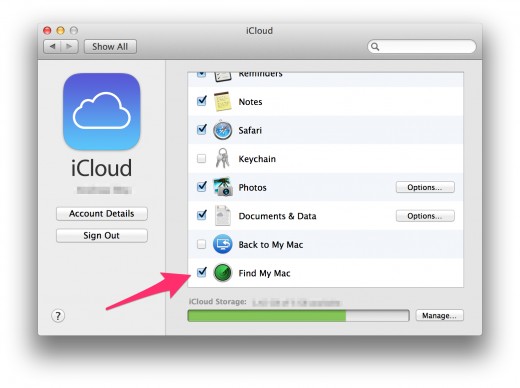
9. Scroll down in the list and activate the checkbox “Find my Mac”.
That’s all there is to do.

Tracing a stolen MacBook
Now we can checkout, how it works, when your precious MacBook has actually been stolen.
- Open a browser on any computer - it doesn’t matter whether it is a Mac or a PC.
- Enter the URL: http://www.icoud.com
- Enter your Apple ID and password

4. Click on “Find my iPhone”
I know, you are looking for your MacBook and maybe even don’t have an iPhone, but you will find your Mac there as well.
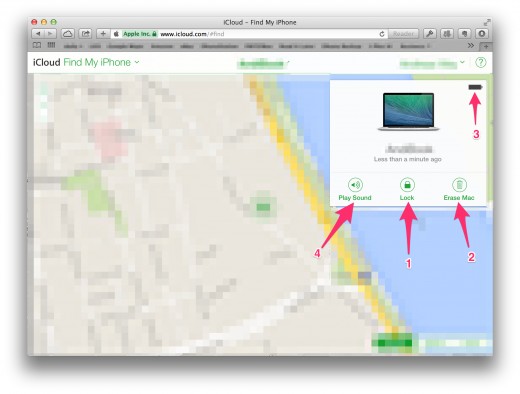
You got two information and three options here.
- The location of your MacBook and how long ago the last active usage was. That is - by the way - why you should activate the guest account. This way your thief will actively use the computer - as the guest account has no password - giving your Mac the possibility to send current location data, telling you where it is taken hostage.
- You will also see the current status of it’s battery (arrow 3), so you know for how much longer it will be able to send it's GPS location data.
But you have also some options to become active.
- For one, you can lock your MacBook remotely (arrow 1), so that nobody can’t access it anymore without knowing the password.
- If you are afraid that you will not get your laptop back or the data on it is so sensible (and providing you have made a backup before) you can delete the entire disk remotely (arrow 2)!
- The last button is not so much for a case of theft, as much more useful if you do not remember where you placed your notebook.
Click the “Play Sound” Button and the MacBook will play a very loud sound, so you can follow the lovely voice of your Mac to find it (maybe under a pile of folders or in dirty clothes).
Third party services
The above features are all part of the standard OS X and come without extra charges from Apple. They cover already quite a large range of functions to protect your data and help you finding your Mac in case of theft.
Nevertheless there are services offered by third parties, that go beyond these functions.
I would like to give you a quick overview, what’s out there and go a little deeper in what I opted for.
Hidden
| Undercover
| Prey
| |
|---|---|---|---|
iSight camera pictures
| X
| X
| X
|
Screenshots
| X
| X
| X
|
Track location
| X
| X
| X
|
Keylogging
| X
| X
| -
|
External IP address
| -
| X
| X
|
Send message
| -
| -
| X
|
Sound alarm
| -
| -
| X
|
Lock Device
| -
| -
| X
|
Price
| $15/year
| $49 one-time fee
| Free (basic account)
|
Basically there are three popular services that cover extended functions that might help you finding the thief of your Macbook.
All three of these businesses offer the following extended feature set:
- iSight camera
The Buildin iSight camera takes periodically pictures of whatever is in front of it. In the case of theft, it is most likely our thief enjoying your Mac. Smile thief, you are on camera! :-) These picture helps the authorities to find that bad guy, maybe he is even already known to them. - Screenshots
Similar to the camera feature, every few minutes a screenshot is taken, which will show sooner or later, the identity of our “new friend”. He/She will likely use Email, Facebook, Twitter, Skype or so on and use his/her accounts for that. - Location tracking
That’s basically the same information as Apple’s “Find my Mac” features. But these services are also meant for Non-Apple users, so it’s a good thing to have it.
Hidden
Hidden does one more thing, though. It logs the keyboard.
This way you might get even passwords from the thief, which gives you even more opportunities to get hold of him/her.
Hidden understand itself literally as a service and charges a monthly fee.
They consider that fee so low that they actually charge you annually. The more computers you sign up, the cheaper it gets for each of them. If you have a large amount of computers to protect, this might a service for you to consider.
Undercover
Undercover covers the same features as Hidden and adds again one more: the external IP address.
The company behind it follows more a licence model, so you need to buy a licence for each computer. It starts at $49 one-time fee for a single computer and gets cheaper the more you buy.
Prey
Prey is an open source project.
Therefor the basic account is for free!
It covers the same features as the others - besides key logging - and adds
- “Send message”,
- “Lock Device” and
- “Sound alarm”.
The latter two are - again - known from Apple, but “Send Message” can be useful, if you think your MacBook is not stolen, but lost. Then there is a chance that there is an honest finder, reading your message, where to return the notebook.
Prey in use
It doesn’t take a genius to guess that I opted for Prey.
For me the extra information from the iSight camera, Screenshots and external IP address are very useful and come in case of Prey for free.
Once you sign up with Prey, you download and install a client app. Which runs invisible in the background (you can’t even see it in the task manager of your Mac) waiting for you to activate it.
It won’t send any data to Prey’s servers before!
For the purpose of showing you what you get, when the worst case scenario actually happens, I pretended to have my MacBook stolen.
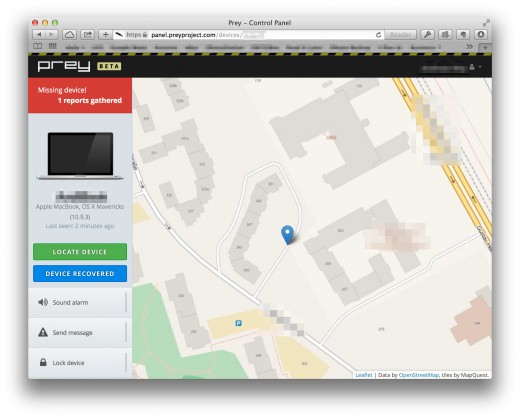
The screenshot above showns you the overview screen of Prey after you logged in.
Very similar to Apple’s “Find my Mac” you see a map with the last known location of your MacBook and a timestamp when this was reported.
In the lower left corner you will find three button for the before mentioned functions “Sound alarm”, “Send message” and “Lock device”.
Once you “reported” your device as stolen, a signal will be send to your Mac and it will start collecting data and sending a complete report every 5 minutes. That is the fast setting within the free account.
Below you can see the details of such a report.
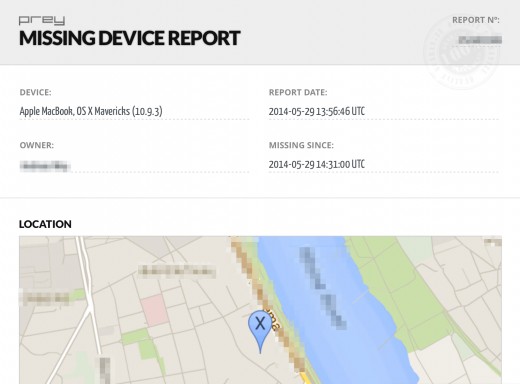
Beside Device and owner name, there is a date for “missing since” and this particular report and a pin on the map, where it was at the time of this report.
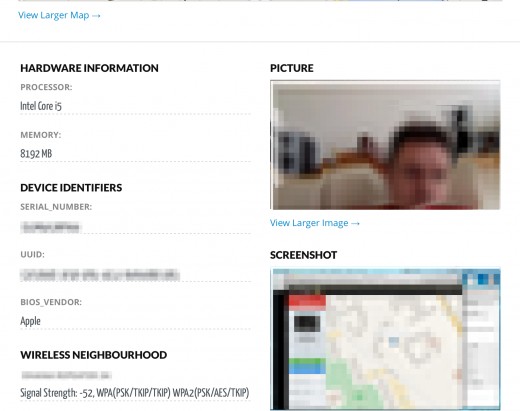
When you scroll down in the report, you will see the Photo taken by the iSight camera and the screenshot and a list of all Wireless networks within reach of the Mac at the time of the report.
The information about signal strength are particular helpful for the police as it allows them to triangulate the exact position very accurate.
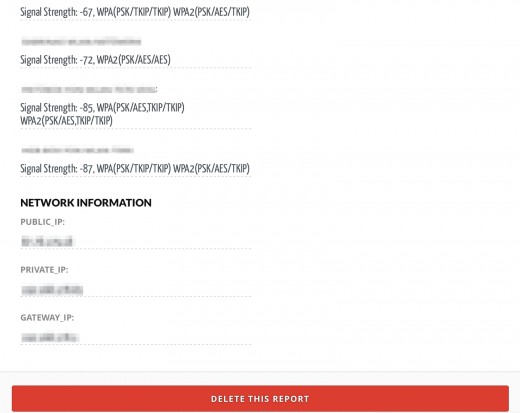
Last but not least the report ends with the IP addresses from the gateway that was used at the time and the private and public address.
Verdict
If you follow all these advices and set your MacBook up accordingly, you only have to get the Kensington Lock Adapter. Everything else is for free.
It will decrease the likelihood of your notebook stolen in the first place, increase the safety of your data and enable yourself and the police to retrieve both if the worst happens to you.
So, there is no excuse!
If you know any other service or tools that could help in this matter, I would love to see them in the comments below.
© 2014 TheAndy

![How to Remove Kaspersky Password Protection? [Easily Recover] How to Remove Kaspersky Password Protection? [Easily Recover]](https://images.saymedia-content.com/.image/t_share/MTc2Mjk3NDcwOTAzNTkyMTI2/how-to-remove-kaspersky-password-protected-easily-recover.png)