Hack Report: Target Department Stores
Update: 7/8/2014
This article has been updated with events which took place on July 8, 2014. The update appears at the end of this hub.
Data Breach

Target Department Stores
Date of Breach:
Between November 27, 2013 and December 15, 2013
Date of Report:
December 18, 2013
Number of People Affected:
40 million debit and credit cards. This number was revised in January 2014 to over 110 million people
Source of the Hack
On January 19, 2014, a full month after the hack, Target stores finally announced that they had discovered where the breach occurred which leaked personal and financial information about more than 110 million customers. They said it was malicious software that infected point-of-sale credit card terminals at Target's checkout counters.
They were amazed that none of their over 40 anti-virus tools caught the malware. There's a good reason for that and it is what I've been telling all of you for quite some time.
Almost all anti-virus programs look for viruses, not malware.
Anti-malware programs look for malware, but occasionally it will find a virus. However, it won't be able to remove it. It can only notify you of its presence, but at least that is helpful.
Most anti-virus programs looks for viruses.
Usually anti-virus programs can't tell you anything about the presence of malware; they aren't set up that way.
Still, with the calibre of malware that is being created to hack networks these days, even some of the best malware programs can't detect all of the intrusions.
Sometimes the malware code (bad guy) is so very close to the code that is on the commercial malware detection programs (good guy). These hackers are just getting too good at it.
~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*
Target's Initial Statement
Right after it happened, Target assured their customers that they had protected all customer payment information with "encryption" and that the "keys" to unlock the encryption were stored on a separate system that was not breached.
But that wasn't exactly true, because it had been breached. The encryption algorithm that Target uses (triple DES or 3DES) is very vulnerable to brute force attacks.
Brute Force is when hackers use many computers for high-speed guessing in order to penetrate the network.
I hope now that they know the encryption algorithm is useless that they have employed better system before the Christmas holiday season - a notoriously high theft time.
~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*
First Announcements of Target Data Breach Before They Knew The Extent of It
Here's how it can happen
The way it works is like this:
- The implanted malware grabs the card data off the magnetic strip on the back of the card immediately as it is swiped at the point of sale terminal.
- The data stays in the system's memory so the merchant can be paid.
- Hackers access the network, grab the data so they can create duplicate cards to be sold (usually it is just the numbers they sell, not a real card), and the new users go on spending sprees to buy big ticket items.
- They'll never have to pay a bill because the bill goes to the real card holder. This is usually when the cardholder first becomes aware of a problem, unless a merchant acts responsibly and notifies each customer or in a media release to all customers.
After the hacker gets the information off the magnetic strip, everything moves very fast from that point.
- They have only a small window of time to get the duplicates ready to sell and use, because once the merchant reports the breach, the numbers on the cards are cancelled making them useless.
Hackers must have someplace to fence (sell) the cards before they even hack the networks.
- For that, there are online card shops - underground black market websites - who are clearinghouses that will sell the duplicate cards.
- It is in the hacker's best interests to get rid of the cards as fast as possible for whatever amount they feel they can sell them for, so they don't get caught and so their customers can get a few charges on the card before it gets flagged at a point of service.
They put the cards in batches of about 100, then they test them with sample purchases.
- If the sale goes through, the cards are still good to use.
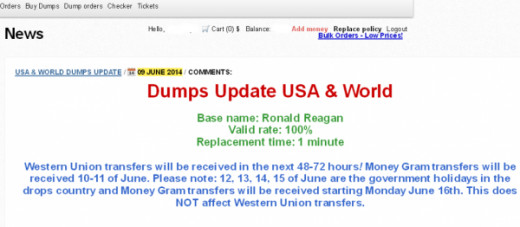
- Generally, they name the batch (for example: Desert Strike, Ronald Reagan), so they can keep it straight what merchant they hacked them from, separating denominations, and the Platinum from Gold, American Express, Debit, Credit, etc.
- Naming the batches also helps customers keep it straight what batch they bought their cards because many buy in bulk - 50 or more cards at a time.
By testing the batch of 100 cards, maybe 2 cards are no good because they have already been flagged to the credit card company for some reason - either by merchant or credit card holder. The rest of the batch is still good to sell.
- So the hacker is able to brag that his batch has 98 percent validity rate, meaning only 2 cards out of every 100 they sell will not be usable.
- That is important info for buyers to know - how many cards in the batch are expected to be usable. 98 percent validity rate is more preferable than a 75 percent validity rate where 25 cards out of 100 wouldn't be usable.
- No one is going to pay $25 to $100 per card if they can only use 75 percent of them.
- The batches are sold in groups of 100 but sometimes when the time crunch is on, because the breach has been caught, they sell them in larger batches of 500 or more for a few thousand dollars less than the individual cards would have sold.
By checking the cards first, by verifying they have a high validity rate, and by giving a money back guarantee (usually just a credit toward another purchase), the hacker builds up his reputation so that more and more people buy from him.
- One such online card shop is called Rescator and its admin goes by the same name.
- I'll be mentioning him a few times in other breaches on future hubs. He is the head honcho of the Russian and English language crime forum "Lampeduza dot la."
- He operates multiple online stores that sell stolen card data, including "Rescator dot la" and several other websites.
- Rescator dot la is responsible for Target, Sally Beauty Shops, P F Chang and a few others I'm featuring in my hubs.
- The site made themselves suspicious by the timing of their sale vs the close timing of the breach.
There are security analysts who watch these card shops in their underground websites for huge influxes of cards advertised for sale. They can almost immediately pinpoint where the breaches have occurred by accessing a few cards and running a history on them to see what the common denominator is of their last uses.
I subscribe to websites of several white hat security heroes so I can study how to protect personal information and learn about data breaches so I can write about them to educate my readers.
If it wasn't for these heroes who watch for the batches of cards for sale, I think the US Secret Service and other agencies would be twiddling their thumbs a lot longer than they already do.
~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*
Example of hacker's sale without prices
~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*
The Far Reaching Bigger Picture
Hemu Nigam, founder of SSP Blue, a security and privacy consulting firm says:
"This will impact many Target business partners — Visa, MasterCard and the host of banks and credit agencies that now have to keep an eye on the 110 million customers now vulnerable to identity theft. It affects more than Target customers. It affects mortgage lenders and car sales. It affects the entire economic infrastructure.”
Target Stores Solution
It took almost two weeks, and I consider this closing the barn door after the horse ran away, but Target finally decided to offer free credit reports for one year to all their customers as well as giving everyone a ten percent (10%) discount on purchases in their stores on two days only - December 21 and December 22, 2013.
In my opinion, the damage was done and they obviously didn't learn much from the experience because they didn't announce any better security measures that were put in place to protect the data of their customers. Let's see what happens this year between Thanksgiving and Christmas 2014.
Offering free credit reports for a year (for monitoring purposes mostly), and offering a store discount of 10% is not a big deal, especially when the 10% is only on two mediocre sale days just before Christmas.
How could they have made me happier?
Offer 25% off on another day where it could be added to another promotion offering at least 15% or with higher discounts. Yeah, I like a good sale. But they can afford it.
Ten percent is a drop in the bucket with you figure most stores have 100% to 200% markup.
About Target's Offer of Credit Report Monitoring
In January, Target offered one year of ProtectMyID which is a service offered by Experian, one of the three largest credit reporting companies in use in the United States.
Customers had to enroll right away, but had up until April 30, 2014 to do so, then request an activation code, then register for the ProtectMyID service before April 30, 2014 in order for Target to pay Experian for the monitoring.
Now, they did say they notified ALL their customers by mail that they were offering this service. However, I know a lot of people who never heard about it at all. Yes, I was one of the ones who didn't hear about it or I would have written about this long before now.
This was one of the best kept secrets - even more than a data breach! - because it was in Target's favor not to take out full page advertisements to announce it to the millions of people concerned.
For each person who signed up, Target had to pay Experian their annual fee. For all those who didn't sign up for the free credit report monitoring, Target got off scot-free.
Now, for all those who did not sign up, there is a slightly twisted silver lining.....
Experian got hacked themselves in late March 2014 and gained access to over 200 million social security numbers. In other words, you have saved yourself a lot of trouble because you would have updated certain information with them, which the hackers would have tapped in the hack.
I have a hub in the works for the Experian Hack which will be available tomorrow.
~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*
Warning
Several incidents of spoof emails have been reported.
If you used a credit card at any store - not just Target - chances are your email address is also on file.
Do not - under any circumstances - answer an email from any company when they are asking you to go to their site to update your information.
Do not type anything in the reply box to these emails. Just replying to them gives them a wealth of information about your location via IP address giving them an opportunity to get the information they are looking for straight from your computer when they hack it.
Even if the email looks like it came from Target, PayPal, Ebay, Your Bank, The IRS, Social Security, or any other well known entity, if they are asking you to update or provide them with any information like your mother's maiden name, your password on the store account or credit card account, your Social Security number, your birthdate, your PIN or any information that identifies you:
- NEVER respond
- NEVER click their link
- NEVER confirm or deny
- NEVER go directly to the website after you got their email.
This is how hackers attempt to get information in order to use for identity theft, to take your credentials and use them for all kinds of cyber criminal activities.
Update July 8, 2014
More than 140 lawsuits, including 29 brought on behalf of banks and credit unions against Target Corporation, were consolidated before U.S. District Judge Paul Magnuson on May 14, 2014, according to http://www.bankinfosecurity.com.
On July 8, 2014, Target requested that a U.S. district court halt the discovery process for all class action lawsuits filed regarding their December 2013 data breach until Target can file motions which they are sure will dismiss most of the lawsuits.
"The experiences of courts and litigants with similar motions to dismiss in data breach related class actions instruct that Target has a substantial likelihood of succeeding in seeking dismissal of all or most of the claims anticipated in the consolidated complaints," attorneys for Target said.
"Given the burden that discovery regarding potentially moot questions would impose on the parties and this court, good cause exists for continuing the discovery stay for a few months until the motions to dismiss can be resolved."
- Quoted from court documents
At the close of business today, there was no reply from the court. Stay tuned.
~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*~~*
Further Reading
This content is accurate and true to the best of the author’s knowledge and is not meant to substitute for formal and individualized advice from a qualified professional.
© 2014 Rachael O'Halloran