- HubPages»
- Technology»
- Computers & Software»
- Computer Software
Steganography

Data security has been a cat-and-mouse game between those for whom data hiding is the ultimate goal, and for those who would prefer being capable of deciphering hidden data. The history of this quest goes back centuries as substitution cipher was practiced in ancient battlefronts. Such schemes are called encryption in which useful information is transformed in such a way that only authorised persons can decrypt information.
But the problem is that even this encrypted or scrambled form of information is a tell-tale sign that something fishy is going on. For example, there are security firms specialising in protecting companies' data, so that unruly employees do not subvert policies of data disclosure. Encryption poses a risk for the business to be successful, which is why they try to identify and restrict any encrypted data that attempts to travel in or out of defined security parametre.But here comes the real twist in the story: what about the situation when it becomes very difficult to actually to identify the presence of encrypted data?Origins and the concept
The study of steganography explains this as the events of heads shaved off to write engraved messages on the skin, and then sneaking the informer after hairs had grown again are common in old-aged espionage tales. Or hiding valuables in fridge or other unsuspecting places to ward off robber's attention are among the examples of steganogrpahy applied in the real world.
The same notion applies in the digital world as well, where an apparently normal file, say an image, a document or a sound file is used as a host to hide information in it. As these files are exchanged very frequently over the internet and other communication channels, it becomes very time consuming to scan each and every file to detect the presence of hidden communication in them. Nonetheless, there also exist techniques that apply checks to detect steganography in ostensibly innocent data files.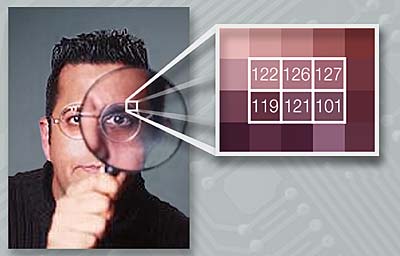
How does it work?
How does steganography actually work and what are its practical uses in today's world? The first question is really simple to answer if we just recall how data is stored in a computer. At a lower level, the units of data storage are bits and bytes, and in some formats, there are header and footer information that ‘read' these bits and bytes to construct the information that we see, say in word processors and image editors. To see this in action, open an image file in Notepad and watch a junk of special characters appear.
There have been instance of cheat codes for games that relied on opening up an EXE file and altering the bits that governed licensing, or applying other cheats by by-passing the instruction code responsible for executing a particular part of whole programme. Same logic applies in steganography but in a much simpler way since it mostly deals with multimedia content in which bits and bytes represents colours. If pixel information is contained in an eight digit number, altering the least significant bit would create alteration in colour which may not be detectable to a human eye. That is, such small changes would not introduce noticeable ‘noise' in image or sound file, where there could be a natural noise present already.
For example, where two colours get separated in an image, a slight blurring of line may be taken as natural photography phenomenon rather than insertion of a few extra bits of information in the file. Similarly, slightly darker or lighter shades may not be noticeable at all as colour depth has gone up to staggering 16.7 million since a very long time now.

Uses
There are several industrial uses of steganography. Firstly, it can be used as a way of introducing bookmark information to thwart copyright infringement. The hidden information can be used as a proof of ownership of digital content - say videos, MP3s and even PDF files. In an event of dispute, the real owner can use the same tool he used initially to hide information in the file to reveal it, thus proving his right on the content.
Another use of this technology is exchanging confidential data over insecure protocols. One of the tools available for USB disk protection is called ‘True Crypt', this also has an option that accomplishes same result by creating a hidden partition inside another but whose presence can not be identified - they call it ‘plausible deniability'.
This is needed in cases of ATM robberies where a person is asked on a gun-point to show his real balance and take it out. If there would be some other secret PIN, the ATM could automatically show ‘service is down' or some other message to prevent the real balance being shown.
Yet another use is private communication in a way that other members of the group do not get to know about it. For instance, if a group of students in a class has to share a report with everyone else, the grade can be hidden in the report and password could be provided to the group members to access this information. So, only the group members can be notified about the grade obtained.
Tools
There are plenty of steganography tools available for free over the internet, or if you happen to be a little more interested, you can write your own. It takes nominal programming knowledge - C or Java preferably - and familiarity with file format in which information is to be contained. All the tools available ask for a host file (like an image file), the information to be hidden (for example, a text file) and a password for encrypting the data. The output is the same host file but now containing the secret information. Size of the file may be a little larger than before, and there could be a limit to the max size of information that can be contained in a particular format. Some common tools are Hide in Picture, Stego and S-Tools. Such Windows based programmes offer standard encryption along with steganography.