Surfing the net anonymously
Why surf anonymously ?
Following the recent 'outing' of three members of MoneySavingExpert by a company against who they were posting defamatory threads, the question has arisen as to whether it is indeed possible to surf the internet without leaving a trace behind.
There are many reasons for wanting to hide your I.D. when surfing the net, from hiding from a violent ex, to running a political campaign in a restricted Country. With impending UK legislation allowing the Govt. to snoop on your data, surfing without fear will soon become common-place.
Every time you visit a website and login to buy goods, leave a thread posting or update a blog, you leave behind a unique identifying number known as an 'IPAddress'. This is issued to you by your ISP each time you turn on your ADSL/Cable Modem and lasts for as long as the connection is live (the box is 'on'). Your ISP will keep records of who was allocated that particular IPA on any particular date and time. It is this info that leads the Authorities to your front-door if you are naughty and post libelous stuff on the net, or spend all your time researching how to make explosives.
Cloaked surfing for beginners.
There are three main elements to cloaked-surfing
- An untraceable IPAddress..
- A throw-away email address.
- An unconnected connection.
An untraceable IPAddress
The first one is easy to achieve using a program called 'Tor' (short for 'The onion ring'). This 'moves' your IPAddress away from your actual one by routing your connection to the www via a system known as a 'Proxy Server'. What you need to understand is that when you fire-up your Router/Modem, it will be given a unique IPAddress (the internet equivalent of a phone number) that will identify you to the world.This number remains linked to your Modem's connection to the www until you power-off the modem for 3 minutes or so, then when you switch it on again, you will be allocated the next available IPA.
As ISP-provided IPA's are so unique that only once such address can exist at any one moment in time on a network, this is the first thing that the Authorities request from the ISP as, as long as they are provided with the date & time, they can search their logs and find-out just who the IPA was allocated to on that date at that time.
With a program such as 'Tor', your connection to the www is re-routed via another server (sometimes even located in another country), this is then seen as your IPA, thus masking your real one. The clever bit is that depending on your settings, you may be routed through several of these servers.
Tor does have a good number of legal uses, such as protecting your network from direct attack, or to watch TV channels not normally available in their Country (i.e. U.S. citizens watching content streamed from BBC iPlayer (which is not usually available outside the UK due to licensing issues)). It also has other more 'covert' uses such as spying on business competitors or organising civil unrest.
Tor is available for Windows, Linux and Mac OSX. There is also a version available that installs on a USB thumb-drive to leave no trace of your actions on the computer being used. It also integrates with all the popular browsers..
A throw-away email address.
When you sign-up to an ISP, you get given an email address. This is linked to your account so when used to set up thinks such as blogs, or accounts on forum sites.
If you do suffer the loss of your throw-away address, just go and sign up for another. There are plenty of email providers out there.
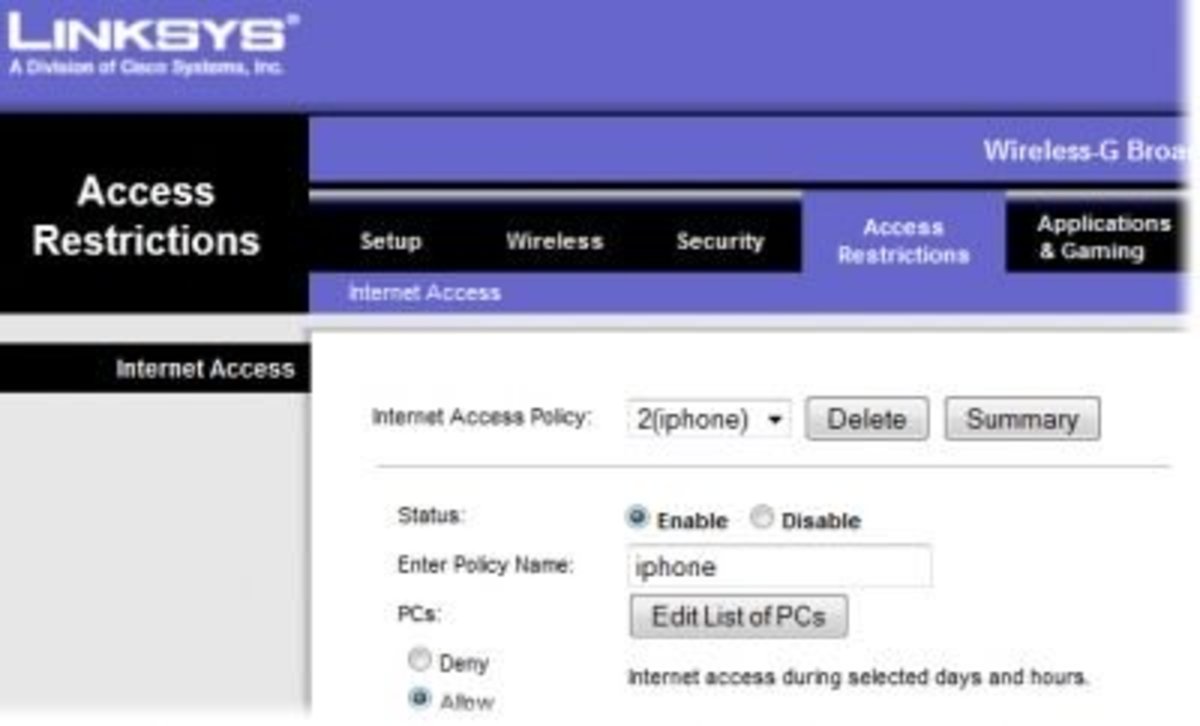
If you want to remain anonymous, then such you need a throw-away email address. These are readily available from such sources as Yahoo and Google. Just remember not to set-up a throw-away account until you have read the whole of this article.
An unconnected connection.
It may sound like gobbledy-gook, but basically, this is a connection to the www that is not linked to you or your address.
A vast majority of pubs, fast food joints and coffee shops have free WiFi available to their customers. These are ideal for the anonymous surfer so long as you follow the rules.
- Never buy any food or drink using payments other than cash.
- Steer clear of venues where you are well-known.
- Use only venues that appear to have a good number of people already surfing. As they say, safety in numbers.
- Circulate. Don't stick to one hotspot. The more you 'roam' the harder you will be to 'hit'.
By following the rules, you can surf using a free publicly-useable WiFi hotspot. If you are one of many, then you will be harder to identify should the Authorities try to detect you.
When setting-up a throw-away email account, do so from a public WiFi hotspot so there is no record of your real IPAddress.
Links
- Tor
The onion ring. The best piece of software for hiding your real IPA. - Tails - Privacy for anyone anywhere
The USB Thumbdrive version of Tor.