Clean Your Computer of Ransomware.

What is Ransomware?
Remember back in the 80's when you weren't too concerned about contracting a virus on the WWW? It wasn't so much of a concern as it is now. Most everything was freeware and it was basically a pleasant experience.
However, today people are having a tough time making ends meet and apparently so are the hackers. This economy has hit us all one way or another and programmers / hackers have become diabolically more creative. With that said, they've created a malware called ransomware a/k/a scareware.
I've cleaned computers for family and friends from this malware called ransomware. This type of malware restricts the user from launching security programs, such as your anti-virus software or Malwarebytes. It takes hold of all .EXE (executable file ending) programs and informs you that they are infected. The programmer which created this threat insists you purchase the software and then it will clean your computer of all the viruses it detected.
It will inform you and display hundreds of bogus viruses on your computer system that do NOT exist. It will block the computer from launching Windows system restore utility, including anti-virus programs. They're good. At this point your computer system is locked down. Mind you there's no guarantee once purchased it will clean your computer. As a matter of fact once you've provided them with your information what's to say they won't leave you hanging.
This is their ploy to scare you in to entering your sensitive information, such as your credit card information to rid you of the problem it created. Once they have your information they will use it to commit identity theft and / or place charges which will be your responsibility.
Criminals Trick You Into Installing Ransomware:
Ransomware can be installed in a few ways, such as by an email attachment, a malicious link on a website, your social network, and even using instant messaging.
As I mentioned earlier it's a conflict of the criminal's best interest to enable you to launch executable files especially those to that will clean your computer. Therefore, Microsoft offers a security utility called Windows Defender Offline which counters the criminal’s malware.
Windows Defender Offline Minimum Requirements:
Windows - 8 (already built in)
Windows 7, Windows 7 w/ SP1, or higher
Windows Vista w/ SP2 or higher
Windows XP w/ SP3 (Legacy system)
Video Resolution - 800 x 600 or higher
Hard Disk space - 500MB
Where to Download Windows Defender Offline:
Windows Defender Offline is available for 32 bit or 64 bit systems and can be downloaded at http://blogs.microsoft.com/cybertrust/2012/09/19/microsofts-free-security-tools-windows-defender-offline.
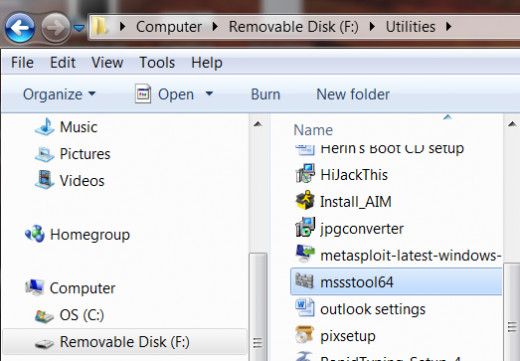
Download and Install Instructions:
Download the setup file to a CD, DVD or Flash drive. It looks something like this. As you can see I've downloaded it to my removable drive F. Click the file to launch the installation.
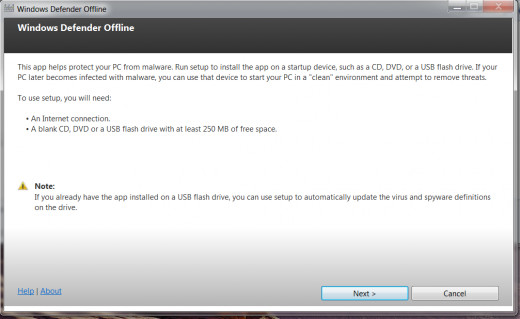
Tools Required for the Installation:
As you can see these are tools you already have in you computing arsenal. If you don't have a USB they're actually cheaper now around $7.00 for 32GB. That's AWESOME! Click Next. Accept the License Agreement. Click Next.
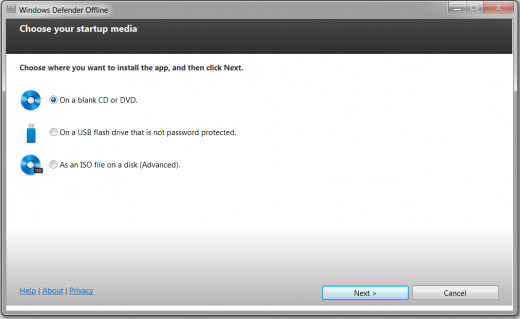
Select a Location for Installation:
Isn't it great to have choices? Yea! Select either a CD, DVD, or USB radio dial and for those who are advance it enables you to create an ISO file. Click Next.
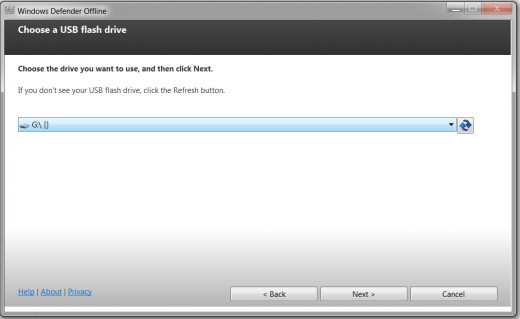
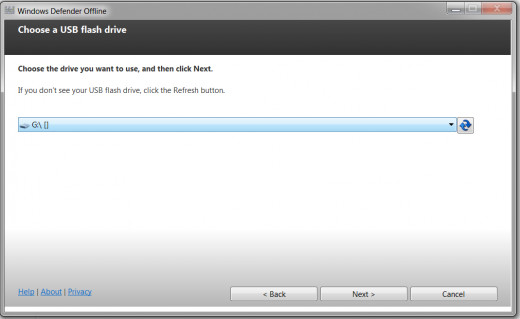
Select the Drive Letter:
Select the drive letter where your installation disk is by clicking the drop down menu button. Click Next.
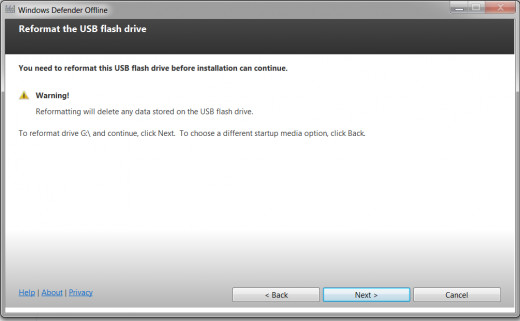
Format Selected Installation Disk:
WARNING! If you weren’t aware of this before please evaluate if you want to use that particular disk. Meaning if you have any data on the disk that you will need later switch to another.
In order to create a startup disk it must be formatted or reformatted and that means it must be blank. The data on the disk will be deleted / erased forever. Click Next.
Progress Bar: Loading Startup Disk:
You are seconds away from the completion of your startup disk. How secure does this make you feel. I'm so excited for you.
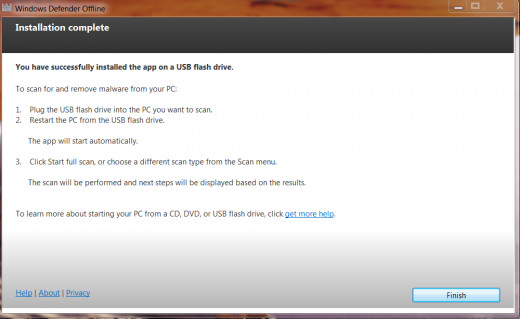
You're Done!
Congratulations! You've completed the installation and now have a source to rid your computer of Ransomware a/k/a Scareware. This is the last step. Click Finish. Now store this disk or flash drive in a safe place. I hope a situation never arises, but it's reassuring to have it just in case. Click Finish.
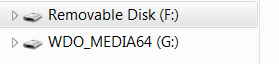
Defender Renamed My USB
After the installation Windows Defender Offline will rename your USB to WDO_ MEDIA64. The 64 signifies that I downloaded the 64 bit version.
To Use Windows Defender Offline Software:
If the situation ever arises and you identified that your computer is compromised insert the startup CD, DVD, or USB you created into the appropriate drive. Reboot the system and follow the instructions to remove the malicious and other potentially unwanted viruses.
Not One Entity on the Internet is 100% Secure:
It's definitely common knowledge by now that no entity on the Internet is 100% secure from cyber criminals. Major companies, such as Facebook (2012), Microsoft (2012)Twitter (2013) and Sony movie studio (2014) have all been struck by the back door villain.
You know they have the best security available. So, that leaves me to believe that I, we, are easy pickings!
But there are some strategies to maintain security. I mean that 's all anyone or any organization can do or promise is to put forth best effort.
- Scan your computer with your anti-virus software regularly.
- Ensure the anti-virus software definitions (files updated to the latest encyclopedia of threats) are up-to-date.
- Never turn off the firewall.
- Never open email attachments from unknown senders.
- Scrutinize downloads w/ piggyback adware attached.
- Be on alert for Social Engineering tactics.
- Update your software applications when prompted (patches old/new vulnerabilities).
- Automate Windows updates (notify you first if applicable, but stay on point).
- Only download from trusted websites.
- Don't connect to unsecure public Wi-Fi.
Do what you can to prevent your personal information and systems from being compromised.
Windows Registry Keys
- http://windowsregistrykeys.com
This is the site where you learn detailed information about computers, laptops, tablets, all-in-one.desktops, and other digital devices. Get familiar with computer specs and how they work..