Torrent Dangers Everyone Should Know to Keep Botnets off Your Network
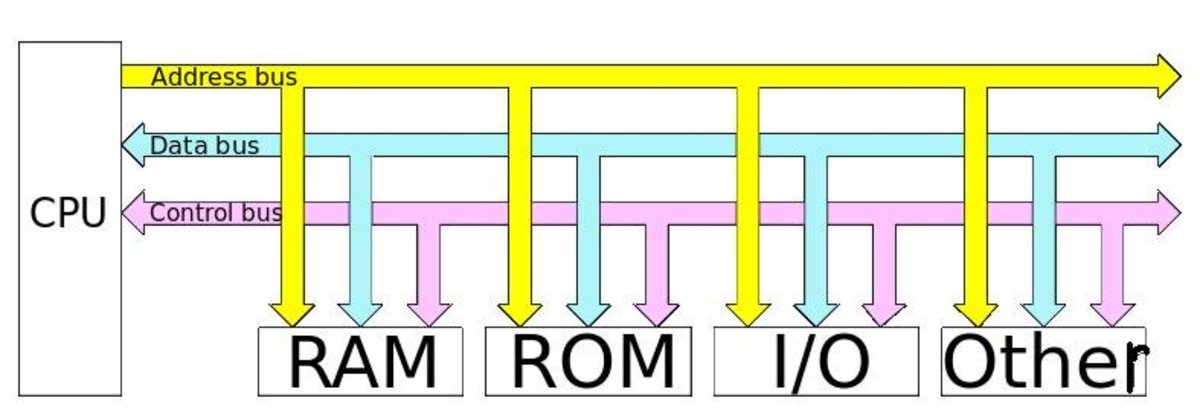
A Model of Network Vulnerability
Torrents are a Great Technology for Downloading Large Files But Heavy Usage for Pirating Content Makes Torrent Use Extremely Unsafe
Most teens today use media sharing websites that utilize torrents or peer to peer technology without understanding the high degree of risk involved.
Torrenting websites require a user to open ports to their network that leave it highly susceptible to infiltration by hackers. They are exceedingly dangerous to both network and computer security yet many people are completely unaware of their existance. This is despite the fact that torrenting is frequently being utilized on their own networks by younger generations to acquire virtually any type of media they desire.
We knew nothing of their existence back in 2009 when we first encountered problems with our home network...sadly we learned about them the hard way. Our network was taken over by a botnet that didnt like sharing our own resources with us. So for the better part of 2 years my family went without internet most of the time, which was exceedlingly frustrating because 2 family members were HS seniors who were trying to get through the college application process and internet usage was mandatory. Those were just a small percentage of the problems we faced during the 2 years in which our network was hacked.
I hope that by sharing what I've learned, I can prevent others from having all of the network problems that our family struggled with.
I originally wrote this in 2012. Every year I review the state of torrenting activity again to both update this and keep it current and with the hope that torrenting use has finally died away. Every year I'm disappointed to learn it hasn't...although it does appear in 2018 that torrenting usage is finally beginning to see a bit of a downturn.
While in the process of updating this article again I also happened to be simultaneously writing a series of post about Firewalls on my main website which I'm not sure I'm allowed to link to here. However I think its alright to say that my site is vsatips.com. My Firewall series is important because there will finally a good way for home networks to better secured. The advent of home firewall security appliances is just beginning, and it's a welcomed innovation be cyber security specialists worldwide. This new class of devices offers a lot of promise for future network security at very affordable prices.
The timing couldn't be better since I recently discovered that botnet threats are increasing both in number and in size because of another relatively new technology...the Internet of Things (aka IoT.)
My Family's Story Began in 2009 and Endured for Over 2 Years
My family's home computer network was hacked around 2009. I've written a more detailed version of what the outcome of that was, which was that our network was entrapped into a Botnet, and we lost our use of it, which you can read here. Here, I focus on what occurred within our home that made our network vulnerable to outside hackers. It opened up a world my husband and I never knew even existed, and led to a frightening 2 year ordeal which changed all of our lives profoundly.
Our story began when our 2 (then) teen-aged sons...who were pretty typical kids all around, learned from friends what most teens today already know. How to find television and movie media online to view for free. They were fairly advanced about tech-related subjects...definitely much more tech-savvy than we were. Which at the time was necessary to employ the techniques required to take advantage of free media resources. Today, that kind of technical knowledge isn't really required anymore. I'd be willing to wager that almost any teenager today, if motivated, could quite readily connect to these resources with much less effort than was needed back then.
I'll also tell you about how we, as parents, got up to speed and learned to protect our computers and home network from hackers after our 2 year ordeal was finally behind us.
The one thing that may have made us a little bit unique was that I have always loved computers...although strictly from a user standpoint back then. I had worked in the computer industry way back in the early '80's which was when I worked for a living. This was long before we had kids. I continue to love computers & related technology today, which is one reason I write a blog on security and technology tips now. Apparently I'm not allowed to link to my own website here but if you Google 'What Hacker's Don't Want You to Know About Firewalls' you can see the first in my most recent series of security articles. Because of my strong interests I probably had a somewhat higher level of understanding about computers in general than most stay at home moms did in the 1980's (although that might not be as true today!) We probably had more computers than the average household did too, and it's quite possible that we had a better network too.
In order to understand how our network was attacked its essential that I go back to the very beginning to provide you with a brief history of how our home network evolved prior to being attacked.

Chronology of our Home Computer Network
Back in the days of dial-up, as our kids grew and our use of technology grew, we progressed from sharing one desktop to each person having their own computer. Since internet access was required for some of their school work, even back then, we went from one phone line to 2, then we added a third.
When broadband became available in our area, we jumped on the band wagon, and were thrilled with the faster speeds, but kept the phone lines too, so that several people could be online simultaneously. But as our phone line costs increased, and arguing ensued over who got to connect to the faster broadband connection, I researched alternatives, and educated myself on routers and WiFis.
We only knew one family that had implemented a home network, but the husband was happy to teach us how to set one up. I purchased the hardware we needed, and he spent an evening with me teaching me how to install the wireless cards in each Windows computer, find a good central location for our router, and how to link everything together. He taught me how to access the router online, using the default username and password, but back then, no one really worried about changing those default settings, and we didn't setup any kind of security to prevent access to the network.
As networking became more popular, our cable company began to offer networking as a service, but this was a year or two before they did. Everything worked great for a while, but over time, more devices entered our home that utilized radio waves, which is the technology that wireless networks use, and interference issues sometimes cropped up, generally from cordless phones or our microwave oven back then.
We also added an addition on to our house, and moved some things around in the process, so our network was adapted to accommodate those changes. I still was able to handle the logistics of all this, but we ultimately reached a point in time when a problem arose that I couldn't fix. We found a local consultant who helped us install a signal amplifier, which was great for a while.
That technology was rapidly improving, and over a period of several years, we upgraded the 'amplifying' types of devices several times, migrated to newer wireless standards, added access point technology, hard wired more areas in our home, and most importantly learned to change the default router settings along with adding WEP encryption to secure access to our network.
My 2nd Monitor

Changing the Default Router Settings and Enabling an Encryption key for Network Access
This is a really important aspect that everyone should know how to do, and I'm going to assume that most everyone either does know how, or has that setup by their ISP or whoever setup their wireless network. If anyone has questions about this, and my assumption isn't correct, let me know in the comments section below, and I'll add a section on how to do this.
Description of the Likely Scenario that Created Vulnerabilities in our Network
Over time our boy's knowledge of, and usage of technology far surpassed our own. We also seemed to have less time than when they were younger, and our computer usage was primarily aimed at getting things done, whereas their usage had a much broader scope. Not only did they rely on it for school work, applications and administrative things, but it became the hub for most of their social interaction, as well as their primary source for media of any kind.
As everyone's usage grew, we began to have more and more problems with network speeds, and network outages. As our boy's knowledge grew, and ours sort of stagnated, they began helping us out with technical problems with both our computers and our network. In an earnest effort to improve the overall network throughput and address our escalating problems, one of the boys upgraded our standard Linksys Router's software to dd-wrt, which was actually a really smart move, because the software is pretty amazing. It really gave our old router a facelift, but since we didn't involve ourselves in the process we didn't realize that the security that had been in place was affected, and we didn't think to check on this aspect for a long time.
It was only when we began to have some really significant problems that it dawned on us that the encryption we had originally setup on the Linksys router was no longer in place. It was around this time that we also really delved into the dd-wrt application and found out both how amazing it was (more surprising because its open source software) and the powerful reporting capabilities it offered, which were better than my husband's commercial setup for his business. The reports depicted some extremely unusual patterns of high usage, some of them occurring when no one was here, which was really hard to understand. But they also showed us patterns for problems that we'd been experiencing, and which we ultimately learned was that our network had been commandeered by a Botnet. That meant that it was no longer under our control...but was being controlled by someone known as a bot master. In my article about how our network was hacked by a Botnet, I talked about the specific Botnet I believe we were part of.

Introduction to Torrent Programs
The Network Reports Pointed Towards Torrent Program Usage
The information from the reports, along with several network consultants who worked with us during different points in our ordeal, led us to learning about the type of technology that's used so routinely by teenagers today, and was a complete mystery to us, and our friends. As we learned more about how the technology works, we began to understand how the course of events made it fairly easy for a hacker to get into our network, maybe more than one for all we know...they are difficult to track and identify, unless you catch some of the activity as it's happening.
My Family's Network is Once Again Safe & Secure

How We Removed the Botnet & Regained Control of Our Network
It took 100's of hours of time to research and diagnose the problems, for us to get up to speed with the technologies, and finally to isolate what specifically was attacking our network, our computers and all our devices.
After several failed attempts to correct the situation...attempts which involved reinstalling or upgrading operating systems and (or) replacing entire computers with newer technology, we finally figured out that our problems were primarily virus based and so well hidden that some of them were virtually impossible to detect or remove in the piecemeal fashion we'd been using.
The only remedy that would work was to wipe every single device on the network simultaneously, and to start from scratch. By doing it this way each machine would essentially be in new fresh state with a clean factory version of their operating system. Once this was accomplished we reinstalled everyone's data which had previously been removed and run through many filters to make sure it was clean before it was reinstalled. Ultimately this was the only approach that worked to finally solve our network issues and to keep our network safe going forward.

The Prevalence of Bit-Torrents
If anyone doubts the prevalent use of torrenting technology, here's an excerpt from Wikipedia regarding the popularity of torrenting back in 2012:
"BitTorrent has 150 million active users according to BitTorrent, Inc. Based on this the total number of monthly BitTorrent users can be estimated at more than a quarter billion. At any given moment BitTorrent has, on average, more active users than YouTube and Facebook combined. (This refers to the number of active users at any instant and not to the total number of unique users. BitTorrent is widely used to transfer Files. More than 200,000 people have been sued since 2010 for transferring copyrighted materials on the BitTorrent network."
We, like most parents that I've talked to since, had no idea what torrenting was. It was only after many months of experiencing huge problems with our home network that we became cognizant of this technology and it’s use within our own network. Upon researching and logging the many network issues it became evident that our network had been hijacked, leaving very little of its resources for our own computing needs.
Overtime we began to suspect that torrenting might be at the root of our problems. But simply making that connection took a lot time and resources. It was never entirely clear while events were unfolding what exactly was responsible. The problems we experienced and logged manually and via reports from dd-wrt, the open source router software that our modem was running under, helped us to see that connection, but that knowledge really came to light after the fact...after our network and all our devices were restored for the last time.

A More Thorough Discussion of Torrenting: It's Prevalence and Dangers
Just So I Don't Confuse Readers, in the Industry and For Purposes of This Discussion, Torrents, Bit Torrents, P2P (Peer to Peer) and File Sharing are All Terms Describing the Same Technology
Typical Example of How Someone Encounters & Interacts with a Torrenting Website
In order to appreciate the danger, you need to understand the technology behind torrent programs,. Torrenting is a way that kids, or anyone for that matter, can have access to free media through the Internet. This is a very attractive way for kids to be able to get music, watch TV shows, watch movies, and download video games, for free. The way torrenting works is through what's called what's often referred to as peer-to-peer (p2p) file sharing.
When a person wants to access media without having to pay for it, they can do a Google search. They may, for example, use the title of a movie. Included in the search results will be sites that say they can watch this movie for free. So they click on a site, and perhaps they even check out a couple of the sites found in their search results. In the end they decide that one of these sites looks most promising to them.
That's the site that they decide to join as a member, because virtually any site offering the media they seek will require registering first. It's easy to join and become a member of a torrenting site. The site may or may not disclose the terms of agreement. More than likely they will ask you to check some sort of box that says that you agree to all of the terms and conditions of the website.
This is where the problems can begin, especially with the older file sharing sites which were less technologically advanced than today. Very few adults actually read those pages and pages of terms and conditions, and even fewer teens do. I myself do try to, (especially after having raised teenagers), but even if one does read everything, and does understand everything...which is a huge "if" right there, there isn't really any alternative to agreeing to the terms of a website if reciept of the content or service in question is at stake.
Usually this crops up after having put a lot of time into searching for something specific. Under those circumstances who would want to start from scratch? So I suspect even the most savvy of users don't usually bother to read through all of the terms and conditions. Generally they just check the box to agree to the terms and move on to begin downloading the media!
What you are agreeing to in this instance, is sharing media with other members of the site. The implications of the way this sharing is conducted is really important because ultimately it was this unique sharing technology that was responsible for opening our network to allow the Botnet in and gain its foothold.

A Closer Look at What Sharing is in a Peer to Peer Framework
The whole concept of torrenting involves a large group of users who generally have each downloaded lots of media to their hard drives. When a user initiates a new download, instead of receiving the entire file from one server, they are actually downloading many different pieces or 'bits' of a particular file, from many other members' hard drives.
It's important for me to note that this process is less automatic now than it was several years ago when our network was hacked. Today, users usually have to make some modifications to their network ports essentially opening them to allow other users to access their own hard drive. Sometimes this may even be all of the hard drives on their network. In the 'all automatic' scenario we probably fell under this happens without any outward signs of what's occurring.
Today teens usually seem to know enough about their own networks to accomplish this with just a few steps. In either scenario remembering to mention this to their parents after the fact usually doesn’t happen (for one or more reasons.) Giving the average teenager today the benefit of doubt, this most likely occurs because they don't recognize the danger of their actions.
The torrenting site that provides the software and their user network is designed for all of their users to share 'bits' of their files with each other. The end result for the user in my 'Typical Case scenario' is that they will personally 'own' a complete version of the (usually pirated) content on their own computer. But they are now a member of that bit torrent community. That makes their computer part of the Peer network which provides many bits of their own media to other users who are doing the same thing.
Peer to Peer file sharing is really a pretty amazing innovation!
There are a lot of polished, seemingly safe and secure sites out there offering this technology. The technology in and of itself, is not a threat.
What creates the threats, as I understand it, and I'm sure I don't understand the entire concept all that well, are twofold.
First are the modifications to your network that must be made in order to allow many other users onto your network, so that they can access your hard drive. I'm sure there are different scenarios for how this actually happens, with varying degrees of knowledge on the user's part regarding the types of permissions they are granting to the torrent site. I also suspect that there are varying degrees of compulsory sharing between the various sites offering these services. Some may limit the actual time your computer spends sharing bits with others to the time-frame required for you to accomplish your download. But others my keep your network and computer open 24/7. Based on the network traffic reports I found on our own network, our network appeared to be open and available for sharing 24/7.
The 2nd reason threats arise I've really already addressed above too. It’s the aspect pertaining to how cognizant a user may be of what they are really agreeing to up front. Personally I know at the time this occurred I wouldn’t have understood all the terms I was being asked to agree to. It’s clear that the teenagers living in our household at that time also didn’t fully understand the implications. They also didn't understand the impact of opening ports to your network. That involved removing the WEP encryption I'd added to keep our WiFi safe too. I think it’s hard for most people to recognize or even believe that hackers may be near enough to take advantage of the laxity of security many WiFi's exhibit. I know that in our case these risks were considered and ultimately weren't believed to be real enough to warrent concern.
Mac Security Blog's July 2017 Article "Why BitTorrent Sites are a Malware Cesspool."
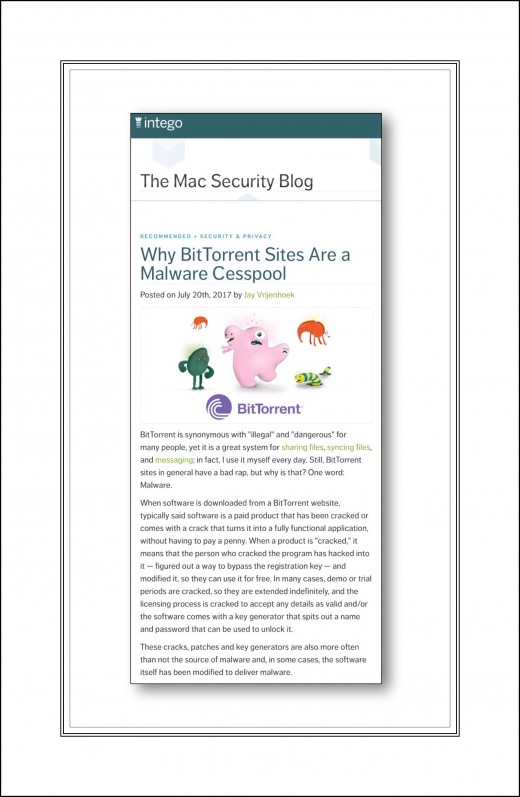
Mac Security Blog's July 2017 Article "Why BitTorrent Sites are a Malware Cesspool."
Evidence for My Conclusion
Every year I review the state of torrenting technology to determine if it still presents an extreme risk. Each time I undertake this exercise I'm surprised to see that it still does. Because of the genius behind the whole Peer to Peer sharing concept I've come to the realization that this technology may remain with us for the long haul.
In July 2017 Jay Vrijenhoek writing for Intego.com, the Mac Security Blog, decided to see for himself just how much of a danger BitTorrent sites, which are one popular torrenting platform, really present. You can read his shocking conclusion in this article he calls "Why BitTorrent Sites are a Malware Cesspool."

A Summary of the Greatest Threats
The main threats are:
1. Pirated media is illegal and subject to huge fines. Authorities are actively pursuing stopping users, and imposing financial and even criminal penalties on "innocent" users, many of whom are teenagers just following their friends advice. Even more alarming is the fact that all of these activities are traceable and provable, and the existence of illegal copyrighted media, if found on a device, or to have been routed through a router, are punishable to the owner of the hardware whether or not they had any knowledge of the actions.
2. Allowing websites or many users to access files on your computer is risky business...and can lead to a multitude of problems including viruses and identity theft.
3. If the computer that is torrenting is on a network of any kind, any device on the network is also susceptible to the same attacks.
4. One of the biggest threats in 2017 is to IoT Devices. Most Botnets today target things like smart light bulbs, Amazon Echo, Google Home and the many smart-home products so popular today.
5. One significant reason Botnets continue to thrive in 2018 is because manufacturers of internet connected hardware don't build good security measures into their products. This means that users need to be extra vigilant and find ways to safeguard these devices through the use of security enabled routers, hardware firewalls, and even subscription based services which are beginning to become quite popular...kind of like how Cloud backup services were at one time.
These threats are real and frequent! They aren't just continuing at the same rate but moving far beyond the level that my family experienced several years ago. They are increasing in number and kind almost exponentially!
All the safety precautions in the world won't be enough without user education. Computers that have been well maintained, with the proper security measures, and networks that have been secured with good firewalls won't be protected in the event that someone on the network opens up a portal to the outside world for purposes of torrenting.

Some Useful Resources to Better Understand Torrents and Their Dangers
If you Google 'the dangers of Torrents' (or torrenting) you'll find lots of information which discuss the legalities of downloading pirated content. You may also find advice on the least problematic ways to go about it. This post at the Creative Digest is very typical of the kind of things you'll find. What you won't often find are warnings about the real dangers to your computers, and what you'll almost never find are warnings about the dangers these activates pose to entire networks of computers and devices.
That was true in 2009 and unfortunately it's equally true today in 2018.
That is my main reason for writing this very long description of what occurred with our network. Because, although you don't often hear about it often or maybe even never, we learned that its not really all that unusual. In fact Brian Krebs a well respected cyber security specialist got into his line of work specifically because of his encounters with similar types of threats during roughly the same time frame that we were battling our botnet foes.
This huge oversight by the press is one thing I just don't get. In 2018 botnets are steadily increasing in numbers yet the vast majority of people have no idea what a botnet even is! You rarely hear about them in news articles yet they are responsible for a huge portion of the malicious hacking that goes on in the world today.
Thankfully there are a few notable exceptions to this frustrating state of affairs. The first is this 2016 article by iafrikan.com in which I highlighted some of the best warnings in the screenshot below. The second is a short but really informative segment by a television show called The Morning Blend in which I even learned about one danger that I was unaware of. The segment is called BitTorrent Networks - a Parent's Primer.
The last is a wonderfully illustrative YouTube video which appears below the screenshot I mention above. In it the host from The Verge explains in detail how torrenting works using an easy to understand approach that's entertaining as well.
iafrikan.com Highlights Dangers Most Others Tend to Ignore

The Verge's Excellent Description of How Torresnt Work
A Few More Tips
Here are a few more things we learned through experience:
- Even non-tech-savvy kids today have the resources and where-with-all to figure out how to get past any security measures you may have implemented on your computers or your home network.
- The torrenting sites are so widely used and 'polished' (for lack of a better word) that even adults who are relatively tech-savvy, can innocently become involved with them. This is especially because there is a very large "gray area" when it comes to media that is free.
Because torrenting sites and software are not illegal per se, and there are legitimate sites that use the technology to share free public domain types of media. Thus there aren't easy answers for parents to address this subject with their kids. But here are a few suggestions:
- Talk about torrenting or peer-to-peer (p2p) sites with your family and make sure that everyone knows about them, the risks involved, and to approach free media of any kind cautiously.
- If you think you might have torrenting software on a computer you can search for files that end with: .torr or .torrent.
- Even after you have this conversation with your kids, don't assume that they entirely understand both the technology and the dangers the way you do. We were pretty shocked to find after having the kids on board with wanting to fix things, that they still had files on their computers and they were still using sites that were dangerous, primarily because this technology is so ingrained in their generations' media habits that sites they thought were safe and legal, really weren't.
- If you have kids going away to college, it's important to revisit the topic periodically when they come home, since torrenting is so completely ingrained in their generation's culture. It's very likely that pretty much any device they come home with will have torrent apps running on them continuously in the background that they forget about stopping when they are home visiting. It's not easy to enforce a 'no torrent' mandate, but in my experience, it's not only advised, but necessary, since internet threats continue to flourish.
- One thing I've noticed more recently is that many colleges today have technology that blocks torrenting completely. This can be both good and bad. If your child's college is using this technology, then your child might be even more motivated when they come home to get the content they want.

How File Sharing Technology Began & Evolved
A Little Bit of History
Napster was the first widely popular website to use the peer-to-peer model of file sharing on a wide scale. Some of you may remember Napster...I do, although I never actually tried it, I was curious. In it's heyday, it was especially popular with teenagers who downloaded music files to store and play on their MP3 players. It predated Apple's iTunes Store, which, when it was released, probably played a large role in Napster's demise.
What played a greater role however, was the whole drm controversy. When artist's began seeing some of their work showing up online before they had even actually published it, it sent chills up their collective spine...and rightly so, I should add.
The other early file sharing sites like Kazaa and Limewire, met with similar fates eventually (although I still find colleges are warning students of the dangers of their use so maybe they still operate in some form today). But while those were file sharing sites, they weren't actually torrent sites, which was a newer technology that was created in part to sort of skirt the issues that created all of the legal problems for Napster. The early file sharing sites used a central server that coordinated the sharing process. Torrent technology works a little differently. The torrent host site still administers some the the transactional stuff, but the actual file sharing activities occur on a true peer to peer basis. This distinction means, that not only is it more difficult to gather evidence of wrongdoing, since all the little 'bits' of data are pretty impossible to track, (that was actually true of the earlier technology too, but even more true with the newer model), but the hosting site (I made up that name for it, there's probably a better definition for the actual site that brings all the users together), doesn't carry any (or at the very least only a negligible amount) of legal responsibility, so they are less likely to be sued.
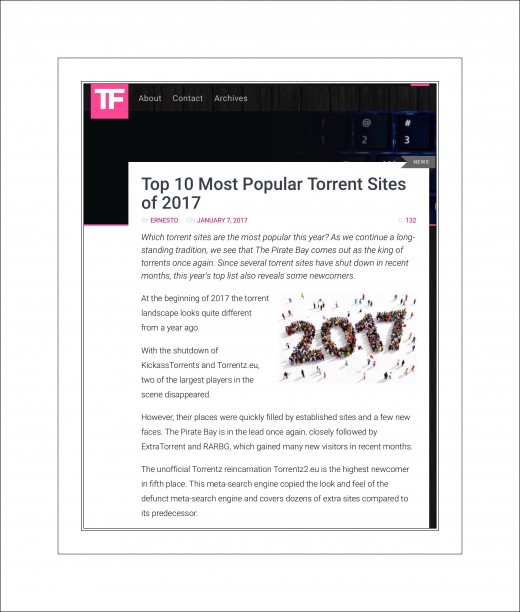
Torrent Freak's 2017 List | Most Popular Torrent Sites
Torrent Freak is a website dedicated to covering news surrounding all aspects of torrenting and file sharing. The website has lots of articles about the best technologies for people to use today to safely download pirated media.
Here's a link to one of their recent articles about the top 10 torrenting sites in 2017.
I ran across their website today while trying to update many of the links and information in this article, which I originally wrote in 2012. (Because it's such a long article it's taken me a few days to get everything up-to-date.) I was more than a little disturbed to discover such detailed and reliable information within just a few moments of search time. It's helped me to recognize that the torrenting community continues to thrive today, which of course goes to the heart of why file sharing technology works and why it's difficult for lawmakers to prevail.
Again a similar search in 2018 immediately found this article 'The Best Torrent Search Engines in 2018 (Working.)’ reminding me that torrenting is still going strong and that sadly it still seems to be something that the vast majority of Americans have never even heard of!
A list of the Top Torrent Sites At the Time Our Network Was Hacked
Tixati
uTorrent
Transmission Bittorrent
Vuze
BitComet
TurboBT
Deluge Torrent
ABC (Another Bittorrent Client)
2 Important Concepts to Remember
There are two things that I thought of after finishing this the first time that I wanted to make sure were very clear and not lost within all of the information given above:
1. How do you know if you have torrent files on your computer?
Most torrent files have one of 2 file extensions, .torr and .torrent.
If you search your hard drive using a wildcard * modifier in your search like this:
*.torr
or
*.torrent
and you find files with these extensions, then your machine has been downloading torrent media.
2. Unlike in the earlier days of the internet, it's not likely today that a child could inadvertently download torrent files without knowing what they are doing.
With today's technology, you need to have a fairly good understanding of the steps involved in setting up your computer and network to participate on torrent sites...in fact you need to open a port or two on your router to be listening for this type of information. Thus the security breach...but at least it's reassuring to know that you can't do it accidentally very easily anymore.
The only reason I say this is because I recall in the early days actually visiting sites when I was looking for obscure media, and seriously considering using one of them to download something. What scared my away were the disclaimers and legal stuff I needed to agree to beforehand. At the time I knew nothing about file sharing sites, but in retrospect, this was probably one of them, and I could have easily gone the other way and downloaded something not realizing the ramifications!!!!
3. I just remembered that another good way to check if teens are visiting torrenting sites is by looking at the browsing history on their computers.
You can also do this on mobile devices, but that's a little trickier since they usually have the devices themselves which are locked with passcodes, and you need to be knowledgeable about each type of device's browsing technology and how to use the app to check it's history.
One thing my friends have asked me is...
How can you know if a website uses torrent or peer-to-peer technology? There isn't an easy answer for this if you're attempting to download free media. But if you take the time to examine the file types you'd be downloading, and avoiding any with the following extensions, you'll eliminate some really obvious threats:
.exe
.rar
.tar
.ace
The title of the article is: How to Tell If a Movie Torrent File Is Fake
A lot of information is written for people who are using torrenting sites, to help them avoid dangerous sites. About.com's Internet for Beginners site has a great guide for this.
- This is the link to the article 'How to Tell If a Movie Torrent File Is Fake'
Although this article is intended for people to 'safely' torrent (an oxymoron at best), it's still good information for anyone to avoid obvious threats.
Great Information About Torrenting Dangers I 2017
- The Dangers of Using Torrents
Trevor Murimba, a Certified Ethical Hacker has written some good advice for everyone on the dangers of using torrenting sites in current times...specifically in 2016. Sadly, torrents are still here and still dangerous!

A few of the sites I found that provide educational and helpful resources parents and users
- FBI Publications - A Parent's Guide to Internet Safety
About the Federal Bureau of Investigation - Parental Control Software Torrent Freeware Downloads: Verity Parental Control Software, Win Parental
Freeware parental control software torrent downloads. Verity Child Monitoring and Parental Control Software. Win Parental Control Software is an comprehensive Web Filtering Software with Parental Controls. - Parental Control for Windows - Free downloads and reviews - CNET Download.com
The Best Free Parental Control app downloads for Windows: Anti-Porn HomeGuard (32-bit) Spyrix Free Keylogger Porn-Blocker LightLogger Keylogger Golden - If you steal films and music, copyright companies 'will have your IP address within three hours' | D
There is a little bit of helpful information for parent's in this September 2012 article entitled: File-sharers' details logged with copyright companies 'within three hours.' - Talking Torrents: Frequently Asked Questions About Bittorrent Litigation | Philly Law Blog
One afternoon you check your mailbox and notice that your internet service provider has overnighted you a letter. You open the letter and find it says you've been named in a lawsuit for downloading porn, movies, or music on the internet. Your interne
Available Online Resources for Parents to Learn About Networking, Torrenting and Cyber Safety
There's a plethora of information providing advice on how to utilize torrent technology but...
What alarmed and saddened me as I was researching for this, was just how readily available clear and concise instructions are for virtually every aspect of learning how to download content using torrent technology.
There are articles which guide users, step-by-step through the setup process for their computer and network, articles on sites to use, detailed information on the nomenclature and inner workings of the process, warnings about the illegalities, and advice on how to avoid getting viruses, as well as getting scammed or 'caught'. There are sites designed to allow users to find out how much of their download activity has been tracked publicly. And there are historical essays on how the technology developed and changed over time.
What is clearly lacking is advice for parents informing them of the wide-spread use of these practices, and educating them about how to protect their networks, their home computers, and their kids. I did find a few sites that discussed some of these things, but they were few and far between. They also aren't easy to spot hidden among all of the 'how to' guides
Graphical Representation of a Botnet & Bot Master

Homeland Security's Cyber Safety Website is Huge!
- They've Dedicated October to Learning About Cyber Security Too!
Being online exposes us to cyber criminals and others who commit identity theft, fraud, and harassment. Every time we connect to the Internet—at home, at school, at work, or on our mobile devices—we make decisions that affect our cybersecurity.
Epilogue
One unanticipated personal outcome of this horrendous event
It propelled me back into the industry I'd worked in long before starting a family. Had it not been for our Botnet invasion I doubt that I would have taken the time necessary to get back 'up to speed' with the current state of computing technology, which in turn means I never would have begun writing online. I've come to realize that writing the kinds of content that I do, which teaches others about safety or about how to use technology or solve annoying little problems with it, is something that I really love.
So there was at least this one silver lining that came from the most perplexing, angst-invoking and longstanding loss that together we'be ever faced as a family unit.
I've written many more resource focused articles about protecting your network at my main personal website, vsatips, which is dedicated primarily to 'how to' types of articles about cyber safety and mobile technology. Originally I included a link here, but Hubpages frowns upon self promotion, I've removed the link. If you're interested in learning about some of the great new technology that's just now, in 2018 becoming available to home users for network protection, you can ask me in the comments section below, and I'll try to figure out a way to share it here.
The Overall Impact Upon My Family
An additional happy outcome is that my kids, now young men with their own careers, as well as my husband, who was never all that concerned about data safety previously, all have developed a very healthy respect for safety matters of all kinds regarding technology.
I'd be extremely shocked if any one of us were ever to succumb to anything even remotely suspect in the future. After almost 2 solid years of dealing with the problems that we did it seems to have given is all a sort of innate ability to know how to handle matters of digital security...which given our current scary climate is something to be appreciated!
A Poll of the Hubpages Community's Awareness of Torrenting Technology
Are you personally familiar with torrenting technology?
© 2017 vsajewel