- HubPages»
- Technology»
- Computers & Software»
- Computer How-Tos & Tutorials
Malware: What is it and how to deal with it

Virus... Worm... Trojan Horse... No, it's not a biology or history hub, but a technology one. You've probably heard about those terms, and more often than not you were talking about your computer, and not about unseen organisms, slithery animals, or mythological legends. The term "computer virus" has become such a common term in the modern world that we all know about the threat it presents, and most of us prepare against it. But how many of you have heard of the term "malware"? The term "malware" is significantly less used than "virus", and yet, when most people talk about a "virus", they are referring indeed to malware. So what is it?
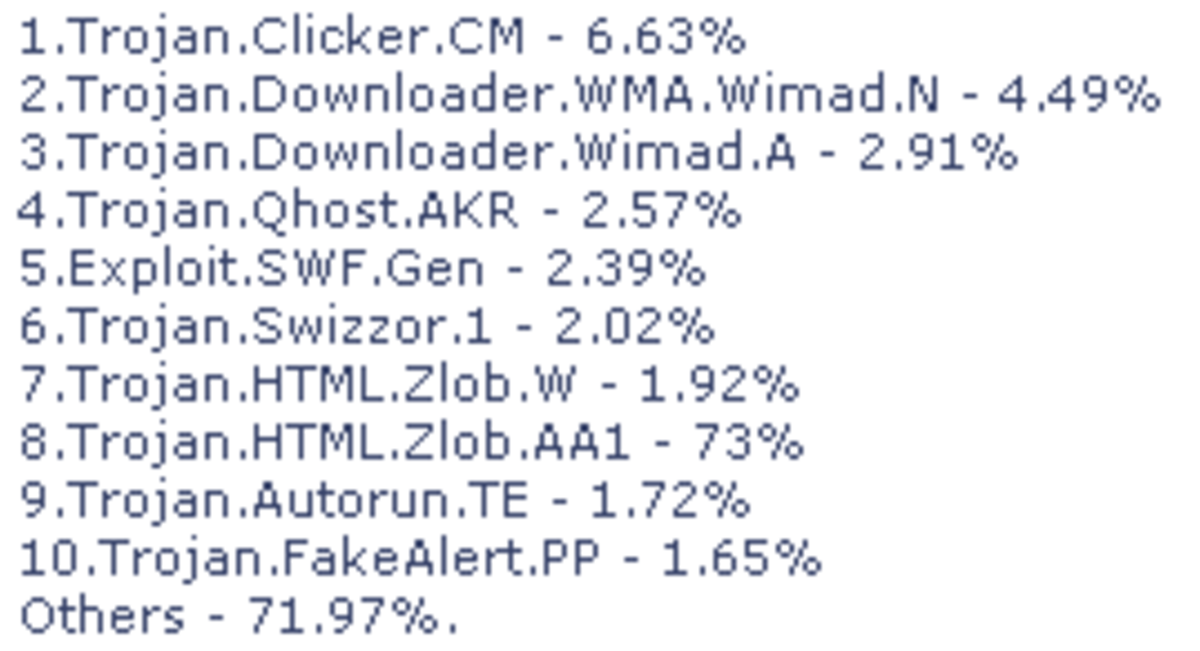
Malware is a portmanteau of the words "malicious software", and refers to any software designed with malicious intentions. Therefore, a computer virus is an example of malware, but not the only one. As a matter of fact, in recent years, computer viruses haven't been the most common malware. So the term malware encompasses a wide array of malicious softwares and threats. Let's talk about some of them.
Types of Malware
Computer Virus: A "computer virus" is simply a malware that spreads itself through your computer files when executed. Like its namesake, a virus needs a host to exist, which is why they attach themselves to executable programs, documents, and files. These files thus become infected, and have to be "cleaned" or "healed" with an antivirus before they infect others. As a result of the virus, the documents might become corrupted and sometimes unusable. Although self-replicating programs appeared as early as 1949, the first computer virus is said to have surfaced in the 70's.
Computer Worms: Worms have some similar traits with computer viruses in the way they spread through the computer. However, worms are standalone malicious programs that don't need to be attached to a certain file or program. Worms can cause significant damage by corrupting files, increasing network traffic or by carrying a damaging payload within themselves. Worms first appeared in the 70's and, unfortunately, have been present in computers ever since.
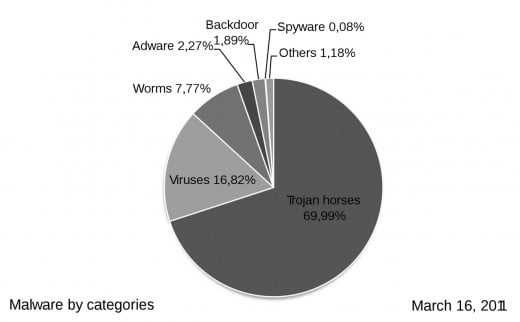
Trojan Horses: Like its legendary namesake, Trojan Horses appear inoffensive at first, but carry a "dangerous" cargo inside. Typically, Trojan Horses disguise themselves as something harmless, like a legitimate software, to lure the user into downloading it, installing it, and executing it. But once the user does so, the Trojan Horse unleashes some dangerous function. Trojan Horses might carry other malwares as well.
Spyware: A spyware is a malware that spies what the user does on the Internet and the computer, and then sends that information to someone. That person can use that information to either target you with unwanted publicity and advertisements, or for other malicious intents.
Key Loggers: Key Loggers are designed to record all the keys pressed by an unsuspecting user. They are surreptitiously installed in a computer, and start recording all the keys that the user presses, thus recording things like usernames and passwords, credit card numbers, account numbers, etc. Key Loggers then send that information in some way to someone that could use the information.
Others:
A backdoor is a malware that allows someone to gain access to your computer without going through the typical authentication process (username and password).
Rootkits are meant to hide other malware. They use various system features to make it unable for the user to see said malware showing among its processes.
A hijack is a type of malware that takes control of your web browser. After that, it redirects your web searches to unwanted pages, or simply alters the way your browser behaves.

What to do?
Want it or not, malware is a reality and we are all exposed. During the 90's, the most common method of infection was through infected floppy disks. But now, with the growth of the Internet and the World Wide Web, malicious websites and harmful e-mails have become the main route for the malware to reach your computer. So, what measures can we take to prevent malware from reaching our computer?
Tips
- Most antivirus allow you to scan files, flash drives, and external disks by just right-click on them and choosing Scan.
- Don't install more than one antivirus! It might affect your computer performance or even prevent it from starting. Make sure you completely uninstall any former antivirus before installing a new one.
- Get used to performing a Full Scan with your antivirus at least every week. Do it when you're not using the computer and let it run while you watch TV or do something else.
- If you receive suspicious e-mails from companies or friends, check the e-mail header to make sure the incoming e-mail address is legitimate.
- If you are not sure if a certain link is legitimate, hover your mouse over it (don't click it!) and look at the bottom of your browser. You'll see a floating text or bar with the exact address the link is pointing at.
- Install an antivirus - The most important and popular method of protection is by installing an antivirus software in your computer. It's almost compulsory to do it if you are going to surf the web. Antivirus have a record of malware definitions and cures, allowing it to detect and "heal" your computer from them. This list is regularly updated so that the antivirus can find new malwares. Although premium antiviruses cost, there are some very good free alternatives like Avast, AVG, and Microsoft Security Essentials, among others.
- Install anti-spyware - Although an antivirus is necessary, sometimes it doesn't protect against all possible malware threats. Typically it has to be complemented with an additional tool to detect malwares like spywares, hijacks, adwares, etc. This softwares are called Anti-spywares and they don't interfere with the antivirus, but rather complement it. Like antiviruses, there are some free alternatives like Lavasoft Ad-Aware, Malwarebytes, and Super Anti-Spyware.
- Make sure your firewall is activated - In most cases, a firewall is a software that monitors incoming and outgoing data in your computer. That way, firewalls can prevent malicious and unwanted access to your computer from hackers, crackers, and digital thiefs. Like antiviruses, firewalls can cost. However, some operating systems like Windows have it included within them. To configure your Windows Firewall, just go to Start - Control Panel - Windows Firewall. In corporate environments, firewalls can be a piece of hardware that monitors what comes in or gets out of the network.
- Be careful of suspicious e-mails (Phishing and Spoofing) - Lots of malware threats nowadays materialize themselves through unwanted e-mails. Trends like phishing and spoofing, where malicious users try to trick and lure people into clicking links or downloading stuff, have increased the spreading of malwares. Whenever you receive unwanted e-mails telling you to click on a link, or download something, be suspicious; even if the e-mail comes from a friend.
- Scan everything - Your antivirus is there for a reason. Use it. Most antivirus are configured to periodically scan the computer, or to even automatically scan flash drives as they are plugged. But still, you can make sure there's no threat by scanning every file that reaches your computer. From a document sent to you on an e-mail, to a picture that you downloaded from a website. Also, run a quick scan on flash drives as soon as you connect them to your computer. Like floppies in the past, they are a very common form to spread malware.
- Know where you surf - Finally, know what sites you frequent. If possible, avoid suspicious and illegal websites since they might be full of tricky links that might download unwanted things to your computer. Don't use obscure sites to download things or buy products, and remember #5: Scan everything.
How to Turn on Firewall on Windows 10
How to Turn on Firewall on Windows 7
To sum it all, malwares are here to stay, and we must be protected. Their symptoms and effects might go from just slowing down your computer, to corrupting and deleting your files, to simply crashing your operating system, or enabling things like identity theft and unwanted publicity. To mitigate the damage of this threat, make sure you follow the tips mentioned above. But most importantly, back-up your important files (work documents, pictures) in an alternate storage like an external hard drive, a DVD-R, or a cloud storage service. This will save you a lot of headaches and suffering in case your computer is damaged beyond recovery because of malware. Good luck and stay safe!
Antivirus Poll
What antivirus do you have installed in your computer?
Other Technology Hubs...
- The Internet or the Web?: Getting the terms right
More often than not, these two terms get confused in the mix. Here is a look at what each of them means as well as a brief history on both. - Vista: The black sheep of the Windows family?
Microsoft's 2007 operating system is bound to ride out in the sunset with a tarnished reputation. But is it warranted? - The Wikipedia Odyssey: 2001 and Beyond
Launched in January 2001, the user-edited encyclopedia has challenged the conventions of how knowledge should be spread, and how people can work together for the same purpose. - Pirates of Silicon Valley: The rise of Steve Jobs an...
TNT's dramatization of the birth of Microsoft and Apple follows the lives of Jobs and Gates as they set to change the world forever while trying to