59
59- 0
Application and System Software
The terms "applications software" and "system software" are used a lot but the terms are often confused. Here are my definitions. Application software is responsible for the business requirements of an organisation. Often, application software is...
- 0
Software Testing - Error Guessing
When testing software Error Guessing can detect some faults that the more systematic approaches can miss. Error guessing involves the tester using their experience to uncover errors. The tester uses their insight and experience to decide where...
- 1
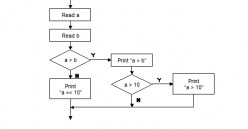
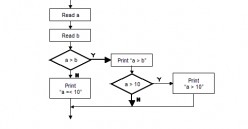
Software Testing - Branch/Decision Testing
Branch testing and decision testing are closely related. We will treat them same. When 100% coverage is concerned, the two techniques are the same. Branch and decision testing require examination of the source code and the creation of tests that...
- 3
Software Testing - Statement Testing
Statement testing is a whitebox, dynamic testing technique. It requires examination of the source code and the creation of tests that will exercise individual statements. The project plan should indicate the proportion of statements that should be...
- 3
Finding Your HubPages Referral Code
If you refer new Hubbers to HubPages then HubPages will reward you with a proportion of their earnings. To benefit from this, you will need to direct them to the HubPages web-site using a URL containing a referral code which identifies you. ...
- 0
Software Testing Hubs
In 2003 I was awarded the ISEB Foundation Certificate in Software Testing. This required me to learn about several topics and I have made quite a lot of notes on these. I am transcribing these note into HubPages which I hope you will find useful. ...
- 1
Software Testing - Dynamic Techniques
Dynamic testing describes those test techniques that operate on software when the software is running. The techniques are often divided into two classes, Whitebox techniques and Blackbox techniques. The Whitebox techniques are confined to...
- 1
Software Testing by Boundary Value Analysis
Boundary Value Analysis is a Blackbox Testing Technique. It makes use of the fact that the inputs and outputs of the component under test can be partitioned into ordered sets with identifiable boundaries. Values in the same set will be treated in...
- 0
Software Testing by Equivalence Partitioning
Equivalence Partitioning is a Blackbox Testing Technique. It makes use of the fact that the inputs and outputs of a component under test can be partitioned into classes. Values in the same class will be treated in the same way. So, the result of...
- 0
ACID
Here we discuss database updates known as Transactions. A Database Transaction can be made up of several operations. However, a transaction is considered to be a single logical operation on a database. For example, a funds transfer transaction...
- 0
Web Services - Procedures.
On this page, we show how the web services are used in order to discover, describe and use a web service. As an example, we use the Delayed Stock Quote service provided by XMethods. Discovery Web service clients use web service registries to...
- 0
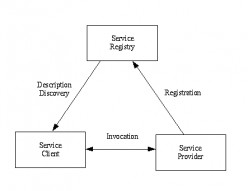
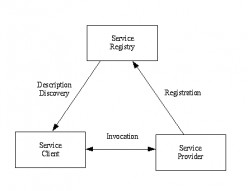
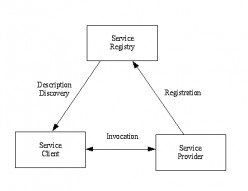
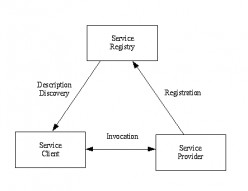
Web Services - Components.
Web service architecture identifies three types of component, the service provider, service client and service registry. Communications between components is based on XML messaging. The web service components are described in the following...
- 0
Web Services - Summary.
Web service standards are used to develop client/server applications on the Internet. The standards recognise the service provider and client components central to the client/server model. They also identify additional servers. Registry...
- 1
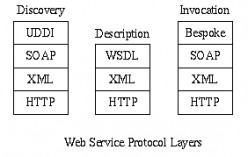
Web Services - Protocols.
Communications between the web service components is based on messaging. XML formatted messages are exchanged between components. Typically, delivery is by HTTP but other protocols may be used. SOAP allows methods to be invoked remotely. UDDI...
- 0
Web Services - Introduction.
The popular view of the Internet is the worldwide web. People sit at their computers using a browser to view static web pages stored on a distant server, or view dynamic pages generated by those servers. This use of the Internet is people-centric. ...
- 2
V, V and T
Verification, Validation and Testing (V,V & T) is a commonly used model for software testing. Here we will give a brief introduction. The following terms are defined in BS7925-1: Verification The process of evaluating a system or component to...
- 1
Software Test Plan
IEEE 829 describes a set of software test documentation. For test plans it describes a document containing the following sections: Test Plan Identifier. Specify a string that uniquely identifies the test plan within the organisation. ...
- 7
Software Testing - How much is required?
Errors and how they occur By definition, errors are made by human beings. All of us make mistakes at some time and in some environments mistakes are more likely to happen. During the development of software, errors are introduced for several...
- 0
Software Testing - Some Definitions
The following terms are defined in BS7925-1. They are the basic definitions about software bugs: Error A human action that produces an incorrect result. Fault A manifestation of an error in software. The terms ‘defect’ or...
- 4
Cyclic Redundancy Checks (CRC)
Introduction Cyclic Redundancy Checks (CRCs) are used to detect errors in transmitted data. A CRC is calculated from the message contents and transmitted with the message. On receipt, a further calculation is performed on the message and CRC to...
- 13
Modulo 2 Arithmetic
Introduction These notes describe how to go about modulo 2 addition, subtraction and division. Modulo 2 Arithmetic Modulo 2 arithmetic is performed digit by digit on binary numbers. Each digit is considered independently from its neighbours....
- 0
Message Digests
A message digest function is an algorithm that converts variable messages to a unique fixed length value. The same input always produces the same output from any particular algorithm. For example, the MD5 algorithm reduces any message to a 128-bit...