61
61- 1
Taxonomy of Malicious Software and Detection Tools
The amount of malicious software is growing at an exorbitant rate and overwhelming security vendors. Identifying and disinfecting systems of that software remains in the realm of antivirus software.
- 0
Reducing the Effects of Blended Attacks
This article will help you understand what blended attacks are and how to prevent them.
- 0
The Threat of Fraud on Social Networking Sites
Several publications note a rise in cybercrime using banking Trojans linked to social networking sites. These instances demonstrate risks in using the internet.
- 0
Computer Worm Characteristics
Laymen tend to classify all malware as viruses. However, viruses are only one type of the myriad of nasty programs that infect computers. Along with viruses, hackers write Trojans and worms that inf
- 10
Recyclers Recover Gold from E-scrap Gold Fingers
The bulk of gold content within escrap computers resides within the gold fingers or the edge connectors that connect printed circuit boards together. Recyclers recover this gold from the escrap computers to earn a home income.
- 0
CPUs: The Gold Mine for the Escrap Recycler
Much of the gold contained in escrap computers resides in the CPU chips. The CPU chips often contain gold plated pins because of the high frequencies involved in computer clocking. Gold may also connect the CPU chip to the package and some older CPUs were manufactured using gold plated heat...
- 7
Recycling Palladium from Monolithic Ceramic Capacitors
One often overlooked source for the precious metal Palladium is the monolithic ceramic capacitors that reside on printed circuit boards. Am e-scrap recycler who collects a large quantity of these capacitors could send them to a processor or extract the metal in a home lab.
- 0
Sample Risk Management Plan: Part 2: Charter, Scope, and WBS
This is the second element of the Risk Management Plan for the fictitious company A&D Manufacturing. This element highlights the project charter, scope, and WBS.
- 9
How to Create a Loan Amortization Calculator Using HTML and JavaScript
This final installment of JavaScript tutorials combines disciplines learned in many of the other tutorials and leads an aspiring programmer on the quest to develop a functioning amortization calculator.
- 2
How to Retrieve HTML Form Data Using JavaScript
Once you create a form in HTML you may like to act on the data at the client level before sending the data to a server.
- 0
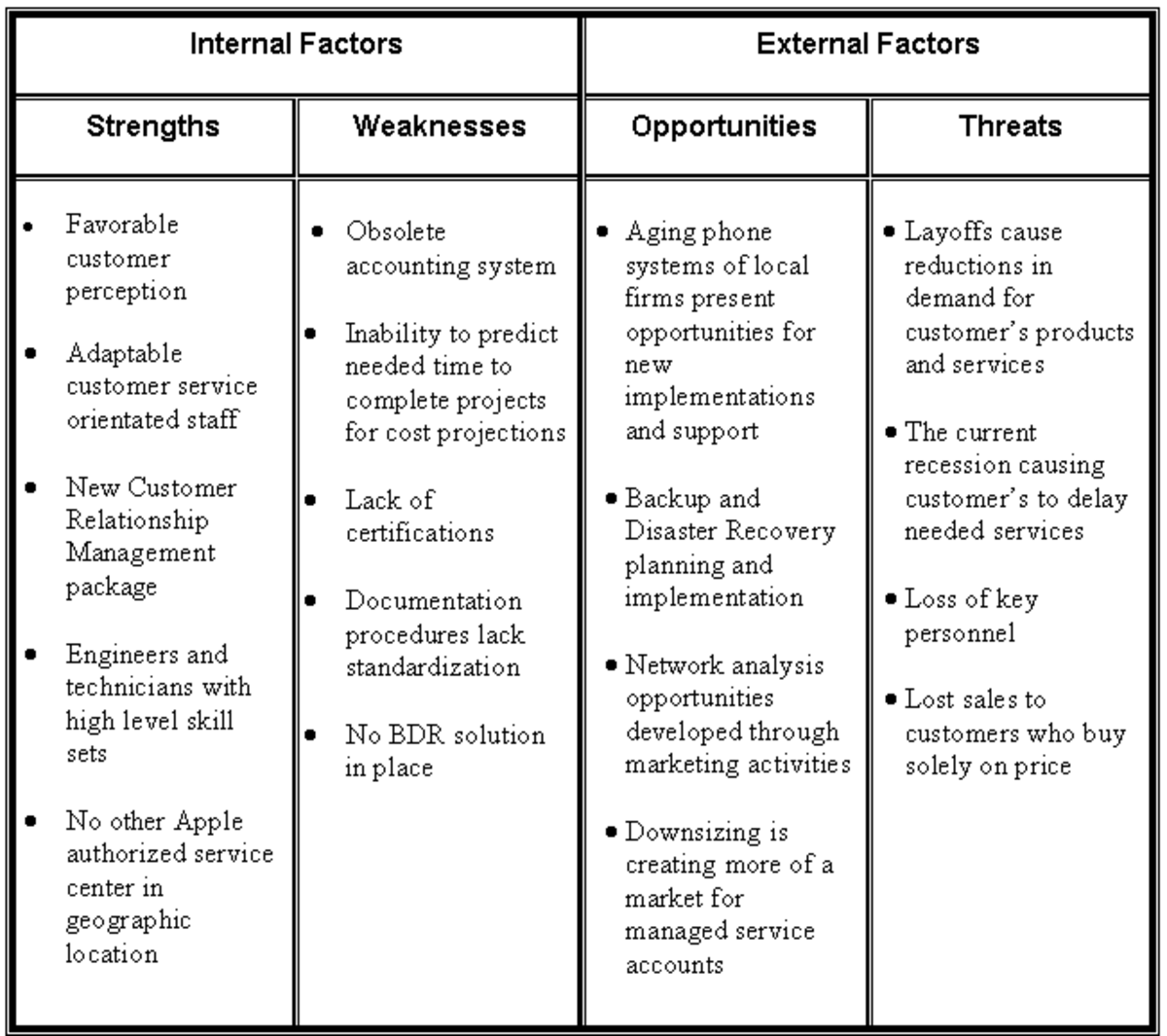
Term Paper: Organization Strategy Analysis Using SWOT
Learning to perform a proper analysis of Strengths, Weaknesses, Opportunities, and Threats (SWOT) is a necessary task to plan an organization's strategic direction. This sample term paper explores the construction of a prpoper SWOT analysis.
- 13
Term Paper: Atomatic Teller Machine (ATM) Project System Functional Requirements Document
This sample term paper was written to cover the topic of gathering requirements for a class in system development and design.
- 7
Microsoft's Tool to Restore a Windows Live OneCare Backup
If you backed up your system using Microsoft Live OneCare Backup and restored your OS, you may have trouble restoring your data - Live OneCare no longer exists. However, there is a solution.