- HubPages»
- Technology»
- Computers & Software»
- Computer How-Tos & Tutorials
Concerned About Security After Lenovo's Superfish Scandal? Build Your Own Computer
What is the Superfish? It sounds Super, right? Well, it's not...
"Superfish" is an American company that leaves glaring, gaping, soul-crushing holes in your personal security on-line - holes so wide, anyone with even half an interest in stealing all your personal information and a few months of coding experience can waltz into from anywhere in the world. This is an unfathomable security hole, like buying a wallet that has a giant hole in the bottom that also cuts out from the bottom of the pants' pocket, so anyone who is even half-decent as a pickpocket could steal your wallet. Superfish pretends to be a shopping customizer that will "recommend" - a.k.a. redirect - you to things that you might like to buy. This is problematic even if it works. That a major computer manufacturer put this user experience nightmare into one machine at all would be cause for concern. That they put it into every laptop they sold is enough to make some computer security experts want to place Lenovo on permanent ban, and destroy everything they ever made due to security concerns. That last point is not hyperbole.
Lenovo is only the tip of the crud iceberg! Bloatware and spam are ubiquitous!
Lenovo's Superfish scandal is bad enough. Actually, it's far and away the worst thing that has ever come out of the pre-installed software system that plagues our computers with useless junk. What is bad enough is any bloatware, at all. Famous not only for making amazing machines, Sony is notorious for completely ruining them with epic bloatware and spamware that renders their technology almost useless without a tech-savvy overhaul. It is almost impossible for anyone to walk into a store and purchase a computer that does not come pre-loaded with a series of software tools and kits that are not present on the box. Computers really should come with a software list, with everything that is included on the list, so consumers can make informed choices about which services they desire, and which they do not.
Where are the honest labeling laws that, at a minimum, would allow consumers to choose the computers with the software they actually want pre-installed, among the options present?
Well, honestly, because any pre-built machine is going to be loaded with garbage. Companies pay other companies to put garbage on machines that are bought by you. Ultimately, you, the consumer, is paying for the garbage that computer companies put on the machines, and the cost of the machine is not adjusted to reflect the profits the computer companies reap on these arrangements.
Hate buying useless things? Well, there's a simple solution. Make your own computer.
You Can Build This. It Isn't That Hard. Promise.

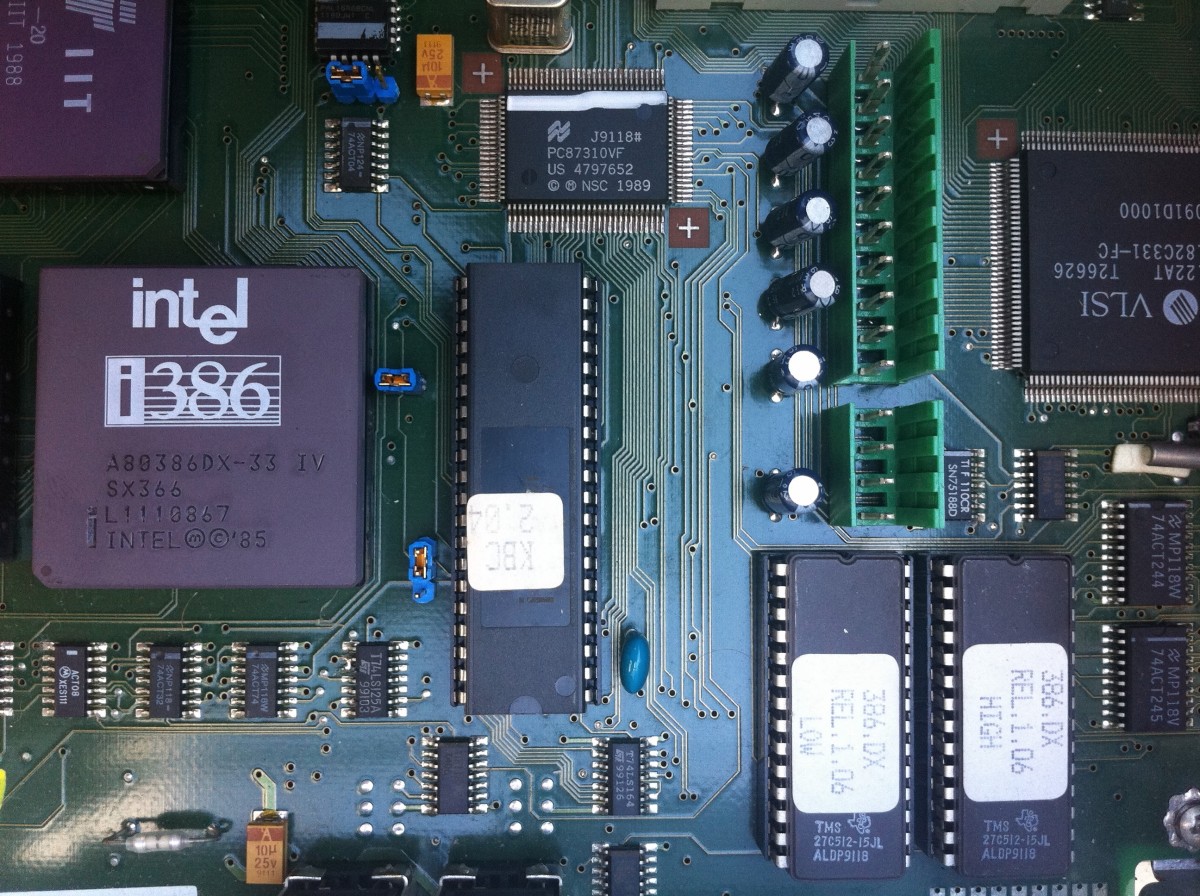
Building a Common Computer Tower
For first-time builders, towers are highly recommended. They are larger, require simple tools that are probably already in the garage, and are easier to modify in the future, if any mistakes are made or upgrades are needed. With off-the-shelf parts, a crafty builder can gather parts from a list at their local technology store, and put it all together in a weekend. Less-experienced builders will probably need a couple trips to the store.
Remember: Keep your receipts in case you need to return something. Make sure you shop at a technology store that will accept returns!
Computer towers can be built at all levels, quite easily. From the epic, heavily heatsunk gaming towers designed for maximum CPU power, to the simple, $99 easy-bake-oven-equivalent introducing the building concept to kids, computer towers can be built readily, and often at a price that is competitive with their pre-built equivalent.
The advantage here is that not only can the consumer avoid bloatware, adware, and all sorts of known and unknown problems associated with the suite of useless junk that clutters up computers, but also users can be in complete control of what kind of computer they actually want or need. For instance, I don't do a lot of video graphics stuff on my tower. I'm mostly a writer. I don't need the latest and greatest video card on my work tower. I do need a lot of memory, however, and really good audio, because I do listen to music while I work. Imagine a computer with excellent audio cards, but average video cards? I don't need to buy both to get one, if I am building my own. I can save money on the video card, and get a very good audio system. By building my own tool, I get to choose what I need and what I do not; I get to choose when I go for the best and when I do not need to do so.
Laptops can be more challenging, but are worth it
Towers, let's admit it, are passe. Everything is shrinking. Laptops are the new desktop. Tablets are the new laptops. Lenovo's impacted computers were laptops.
Building a laptop may require more technical knowledge, and tools that are specific to computers. We have long moved past the time when someone with a screwdriver could casually install TCP/IP cards into their own laptop. But, it is not hard to purchase an off-the-shelf hard-drive for a laptop and have someone install it on a perfectly functional machine for a few dollars, if one is unwilling to go to the trouble of learning how to work on the smaller scale of our shrunken laptops.
In my experience, one of the biggest surprises new potential builders will have with computers is the tightness of the case versus the desired things inside of that case. I recommend newcomers to find larger cases, like the excellent Sony Toughbooks, that are more forgiving to slipped screwdrivers and more fun to pull apart and put back together, over anything slim and small and dainty. Toughbooks are often used by contractors and first responders, and, as a result, are not hard to find on the used computer market.
Again, these are still generally harder to work with than towers.
For anyone without a lot of experience or tools interested in laptops, my suggestion is to pay an experienced computer repairman to install a new, blank hard drive on the machine of your choice. Then software can be installed with some level of safety.
The world is changing fast, and unfortunately, the consumer is not powerful enough to protect themselves from the many issues of personal information in the digital age. It is only a matter of time until we see bloatware even on the blank replacement hard drives, in my opinion.