DDos protected VPS
Any individual or business with a computer that utilizes the internet is subject to Distribution Denial of Service (DDoS) attacks. These attacks occur for many reasons and are so subtle, that users may not even be aware that it is happening. In fact, in recent news, the entertainment giant, Sony, was a victim of multiple DDoS attacks.
Individuals experiencing disruptions to service such as unavailability of certain websites, unable to access any website or a dramatic increase of spam in your account, could possibly be under a DDos Attack.
What is a DDoS attack?
A DDoS attack is a well-timed, coordinated, distributed remote attack that deliberately prevents one or many computers or networks from accessing a network of sites including certain websites, emails, online accounts, applications and more.
Once the attacker gains access to the target computer, the computer becomes too busy responding to the attackers commands, that it doesn't have time to respond to legitimate commands. This flood in the system can cause the computer to delay, stop responding altogether, or create an outage.
How and Why DDoS Attacks Happen
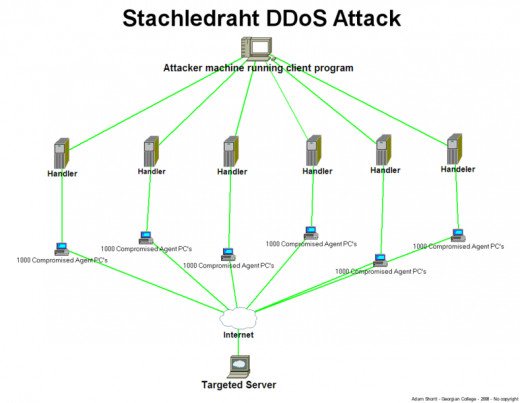
The aim of a DDoS attack is to recruit as many bots, or infected computers, as it can. DDoS attackers develop specialized malware programs, which they spread to as many vulnerable computers as possible, either through websites, email attachments or an organization's network.
Once a user is tricked into running the malware, the infected computer will be turned into a bot, providing an access point for the attacker to control the computer. Once the attacker gains control of the computer, it will then respond to the attackers command and control servers, which will be transmitted through the centralized machines.
These commands include directions for launching attacks from the computer's malware to a specific target utilizing selected attacks methods. It is the attacker's goal to infect as many computers as possible, potentially building an army of botnets, which generally consists of thousands of bots. Once an attacker has a botnet, anytime they want to launch an attack, they simply send a message through their botnets command of control servers with specific instructions to launch an attack on a specific target.
The infected machines in the botnet will comply by launching, a coordinated, well-timed distributed attack, or a DDoS attack. An average DDoS attack lasts about 24 hours. Sometimes an attacker will forego the botnet system altogether, and simply hire a DDoS service to launch attacks, which costs anywhere from $5-$200. There are various types of DDoS attacks.
Each attack targets a different component including ISP, routers, appliances, firewalls, applications and data centers. There are also various methods of attack, which advanced DDoS protection companies are equipped to handle. Some of the most common methods of DDoS attacks include:
- Layer 7 Attacks-this is the newest level of attacks. This attack focuses on the specific application area that creates bottlenecks, like the Slow Read attack, which utilizes Apache's continual connection, and the fact that it opens a new thread for each new connection to send packets slowly over various connections, quickly overwhelming its web server.
- Layer 3/4 Attacks-these attacks originate from a variety of sources and are designed to overwhelm the computer's resources in order to deny it the ability to respond to legitimate traffic.
- DNS Amplification Attacks-during a DNS amplification attack, the attacker sends a request for a large DNS zone file, using the intended victim's IP address, to a large number of open DNS resolvers. The resolvers then respond by sending a large DNS zone answer to the IP of the intended victim, allowing the attackers to amplify their attacks to the many times the size of the bandwidth resources they control.
- SMURF Attacks-During a SMURF attack, the attacker relays ICMP requests to the network broadcast announced from the router configured to relay ICMP to all devices on the router, disguising the source of the ICMP request to the address of the intended victim. Once the router receives the request, it passes it on to all the devices utilizing the router. These devices then respond back to the ping. The more devices linked to the router, the more the attacker is able to amplify the attack.
- ACK Attacks-During an ACK attack, the server initiating the attack, sends a synchronization request to the receiving server. Once the receiving server acknowledges the request, the attacker sends lots of SYN packets to the intended victim, using a disguised IP address pointing to the intended victim. The server responds to the victim's IP with an ACK, thereby, launching an attack.
Who Is Behind DDoS Attacks?
A DDoS attack can occur for many reasons including to cripple a business competitor or simply to gain instant internet notoriety.
Why Some Organizations and Websites are Constant Targets of DDoS Gaming sites, have long been a victim of cyber attacks because they are often targeted by unsuccessful players seeking revenge for their losses. However, any site can be a target, such as e commerce sites, political sites and even an organization's web server etc.
Historically, sites whose servers do not support HTTP, sites with a continual need for connectivity and sites where users have an emotional investment in the site, such as gaming sites, have been popular targets of attack. Sites sensitive to latency and availability are also ideal DDoS attack targets.
In other cases, it is estimated that most businesses are targeted as a result of activism, competitor saboteurs, extortion driven attacks or just for fun.
Consequences of DDoS Attacks
DDoS attacks can create legal repercussions, reputational damage, financial losses and costumer agitation, therefore, a potential DDoS attack should never be taken lightly.
How To Defend Against A DDoS Attack
There are a few basic ways to protect your computer from a DDoS attack including:
- Install a firewall with restrictions on traffic flow
- Install Anti-virus software
- Use email filters to help manage unwanted traffic
- to name a few
Protecting Your Websites and Online Business Against DDOS Attacks
DDoS attacks are ever evolving as new ways to combat against such attacks are constantly being developed. Most DDoS attacks target the network and transport in layers, which may prove too sophisticated for traditional modes of protection. Therefore, many individuals and businesses are turning to more advanced protection services for help. Advanced DDoS protection services provide an extra level of protection for organizations both large and small, including protection against layer 7 attacks. Some companies that specialize in Advanced DDoS protection include:
- Incapsula-Incapsula's Global CND includes 16 scrubbing centers with a network capacity exceeding 600 Gbps and automatic activation and triggering of DDoS protection.
- Akamai Kona-the Amkamai Kona Site advanced technology stands between your network and DDoS attackers and is always on.
- CloudFlare- CloudFlare's Enterprise level DDoS mitigation services utilizes a global network with caching to provide a superior network infrastructure to absorb attacks.
- RadWare- Radware's DefensePipe absorbs volumetric attacks from your website, whether BGP or DNS, by redirecting it from your website to scrubbing in the Cloud.
- Defense.net-the founder of Defense.net created the distributed denial of service attack mitigation service industry, more than 10 years ago, which means their protection techniques are backed by decades of experience in DDos attacks.
How a DDOS Protected VPS can Protect Websites or Limit the Damage Suffered.
In short, by utilizing a DDoS protected virtual private server (VPS), it helps buffer against attacks by providing an outside network infrastructure that stands between your network and the attack. And, in the event a business finds themselves being attacked, many services provide emergency services that immediately directs the company's DNS to their service, so they can scrub the attack traffic, limiting damage to the system, so businesses can rest assure knowing, they are protected even, during, a DDoS attack.








