What is a Denial of Service (DOS) / DDOS Attack?
Early Denial of Service (DOS) attacks were considered games played by programmers to disable opponent’s memory. Today, DOS attacks are used to disable and disrupt services and cause company network outages. DOS and Distributed Denial of Service (DDOS) attacks are typically malicious in nature.
The purpose of DOS and DDOS attacks is simple: “to force a target system to become overloaded with activities that reduce its capacity to process legitimate tasks” (Janczewski & Colarik, 2005, p. 86). An example of a DOS attack is the 1987 Christmas Tree Exec worm (actually a Trojan horse) (Lilley, 2002). The Christmas Tree worm’s intent was not malicious. The Christmas Tree worm was used to draw a Christmas tree picture and email the picture to everyone in the user’s address book (Lilley, 2002). The Christmas Tree worm inadvertently used too many resources and forced many computers to shut down. This overutilization of resources prevented legitimate work from being performed on the computers infected by the Christmas Tree worm.

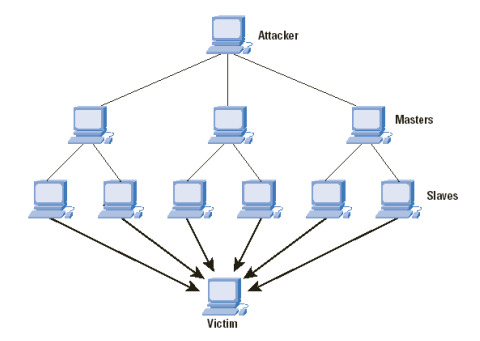
For large corporations with super computers, a DOS attack is often ineffective and a DDOS attack is the preferred denial of service attack. A DDOS attack has several stages. The first stage involves finding and prepping zombie computers. Zombie computers are computers used to carry out tasks. These zombie computers must first be compromised by the attacker. A compromised zombie computer can either be remotely controlled by the attacker or may be configured to perform a task at a specific date and time. Once the attacker has enough zombie computers under his control, he can use the zombie machines to simultaneously launch a DDOS attack against a specific target. This may result in thousands of zombies sending requests to a single web server, hence overwhelming the web server and rendering it unable to support normal traffic.
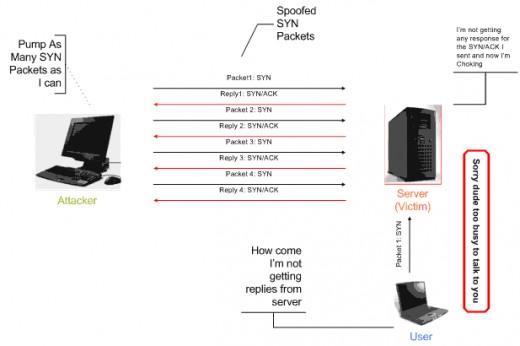
One of the most commonly used DOS and DDOS attacks is a SYN (Synchronize) Flood attack (Russell, 2000). The SYN Flood utilizes the TCP (Transmission Control Protocol) handshake mechanism. In computer network communications, TCP requires the client first send a SYN packet. The server then returns a SYN and ACK (Acknowledgement) packet. The server expects a return ACK packet from the client. The server leaves a socket open and reserves resources waiting for the client to send the ACK packet to complete the three part handshake. A SYN Flood attack takes advantage of the TCP handshake mechanism by sending a server thousands of SYN packets with a spoofed source address and never returning any ACK packets (Russell, 2000). This causes the server to tie up all resources by leaving thousands of sockets open waiting for ACK packets from clients. The utilization of zombie computers for a SYN Flood attack turns the attack into a DDOS and can easily overwhelm most servers.
SYN Flood
DOS and DDOS attacks are difficult to detect and are easy for attackers to use. Many tools are available via the Internet that help attackers setup DOS and DDOS attacks. One of the only effective mechanisms for detecting DOS and DDOS attacks is anomaly-based intrusion detection systems. Anomaly-based detection systems can detect unusual network activity, such as a flood of SYN packets and either alert a system administrator or automatically take action to prevent the attack.
Please check out one of my other articles on information security:
References
Janczewski, L., & Colarik, A. (2005). Managerial guide for handling cyber-terrorism and information warfare. Hershey, PA: Idea Group, Inc.
Lilley, P. (2002). Hacked, attacked and abused: digital crime exposed. Milford, CT: Kogan Page, Limited.
Russell, R. (2000). Hack proofing your e-commerce site: the only way to stop a hacker is to think like one. Rockland, MA: Syngress Publishing.









