- HubPages»
- Technology»
- Communications»
- Smartphones»
- iPhone
How to Use Find My iPhone to Protect Your iPhone
When the little known doulCi team got the better of iCloud Activation Lock in May 2014, privacy questions were raised again, and we wondered if Apple was capable of staying ahead of the game. It was early Christmas for hackers and the same old story for Apple.
The Christmas was short lived though as Apple worked around the clock to zip up lingering exploits in IOS firmware.
Despite doulCi and other security hacks though, you can still use Find My iPhone and other security features to protect against iPhone theft data compromise.
1. Use Passcode or Touch ID
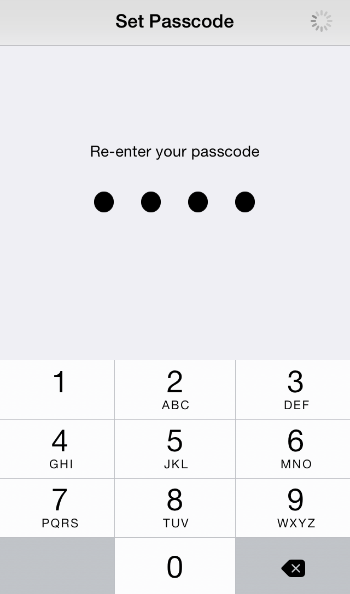
Your first line of defense against iPhone and data theft is the passcode lock. It is a security feature which requires enabling and thereafter inputting a passcode in order to access the iPhone homescreen. It is integrated within all IOS versions.
Touch ID fingerprint sensor is an additional line of defense for owners of iPhone 5S and iPhone 6 and 6 Plus.
One example of the value of the passcode was illustrated when in May 2014, in Australia, a cracker remotely took control of a handful iPhones and demanded a fee from their owners before he could unlock their devices.
Affected users that had enabled passcode lock were able to access their devices once they keyed in the passwords. Those without passcode security remained locked.
A passcode enabled iPhone will also give you plenty of time to report a lost iPhone to Police and just in case Find My iPhone is enabled, it will also give you extra time to track it down before someone turns it off.
In addition to other security features, the passcode makes it hard for the iPhone thief to read through your data and flip through your photos.
Is passcode security enabled in your iPhone?
2. Activate Find My iPhone – Activation Lock
Find My iPhone has been part of iPhone operating system since 2010 but took center stage in 2011 following reports of increasing iPhone theft.
2011 was also the year that Apple launched iCloud and besides the storage services it provided, iCloud made it possible for Apple device owners to send notifications to lost devices.
The Activation Lock feature was bundled in IOS 7 as a bonus to Find My iPhone.
The activation lock requires that you type the Apple ID credentials anytime you wish to turn off Find My iPhone, sign out of iCloud or erase your iPhone. This applies to the bad guys as well. Because they want to turn off Find My iPhone, they will have to fill in your Apple ID which they probably don't have.
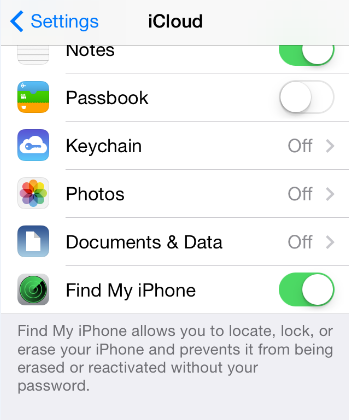
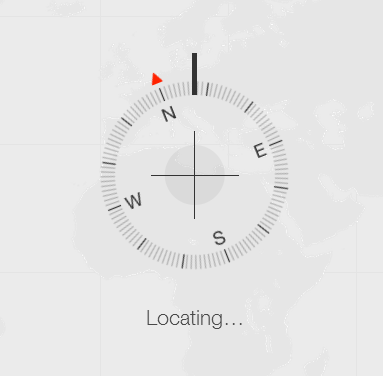
When Find My iPhone is enabled in your device, you can use your iCloud account via a desktop browser, or the Find My iPhone app in another Apple device to track a missing iPhone.
iCloud account and Find My iPhone app will send a custom message or sound to alert the person with your iPhone that it is lost.
Perhaps the most reassuring thought even in the aftermath of doulCi hack, is that your data will remain safe after the activation bypass. Most times the activation notice will pop up after an iPhone has been erased or restored by you and the thief respectively.
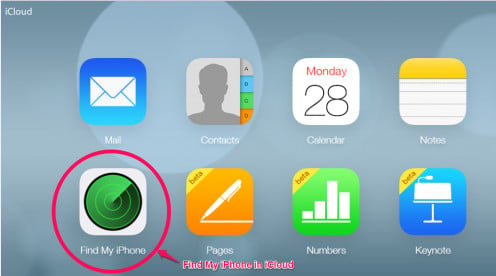
To activate Find My iPhone or Activation Lock, simply log into iCloud in your device and the rest will be taken care of.
To log in to iCloud, tap Settings>iCloud
- How To Download And Install Old Version IOS Apps For...
In order to download and install old IOS version apps for iPhone 3G and 3GS which usually run IOS 4X and lower, you need to fiddle around with a few tweaks in order to get the job done. You must have a jailbroken iPhone, install Appsync ...
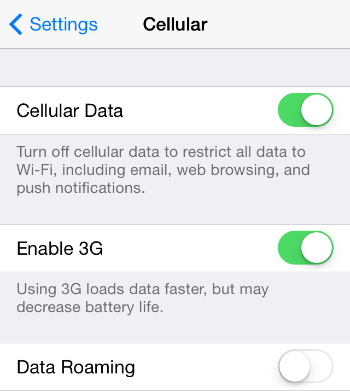
3. Enable Data Connection When Outdoors
We all disable data connection once in a while because we want to preserve the draining battery in the iPhone. Intensive data use leads to excessive heat and thus lessening battery hours, and weakening battery over time.
For the same reason, you may actually enable data connectivity only when you need it.
For security reasons however, make it a point to leave data connection enabled most of the time, especially when you are out of the house. At least disable 3G or 4G connectivity. I am imaging this is when thieves are bound to strike, or you are most likely to misplace your iPhone for one reason or another.
A running data connection in addition to enabled Find My iPhone feature should be the starting point for you to track your iPhone.
By remote use of another Apple device or iCloud in the browser, you should be able to see where your iPhone is before it is turned off.
Never mind about data bundle itself, for you should be able to activate additional data remotely. Most service providers around the world permit remote data activation.
4. Install and Use Security Apps to Track a Lost iPhone
Aside from the tracking capabilities installed in the iPhone and IOS, i.e. Find My iPhone, you may want to take advantage of third party apps to help track a missing iPhone.
Third party apps can be downloaded from App Store and Google Play.
Prey Anti Theft for Android
Besides using your laptop or desktop computer to track a lost iPhone, you can track it using Prey Anti Theft Android app. This app uses geo-location to track location, and front and rear camera to take pictures of whoever is using your iPhone.
Of course you will need an Android device to do this. If you own an Android device or a friend of yours does, why not help track each other in case your devices get misplaced?
Prey Anti Theft is also available for iPhone and can as well track Android devices.
Prey Anti Theft is available for free from App Store and Google Play.
Find My Friends
Find My Friends is a social app that is meant to locate friends and family for social purposes.
Find My Friends is a sneaky app I must add, but again if you find it socially acceptable to track each other for pleasure then an additional feature to track misplaced and stolen devices should be a bonus.
Once installed in your IOS or Android device, you can add friends or get added in friends’ circles so as to locate each other for not only social activities but cell phone tracking as well.
Find My Friends is available for free from App Store and Google Play.
A Word Of Warning
If you think you have successfully tracked down a thief in possession of your iPhone, exercise wisdom when deciding to approach him or her. Avoid superman sentimentalities and seek the services of law enforcement officers to effect arrest.
5. Do Not 'Trust This Computer'
The Trust This Computer feature Was introduced with IOS 7. It will pop up every now and then whenever you connect your iPhone to a new computer. You can choose to Trust or Don’t Trust a computer depending on what you want to do with it.
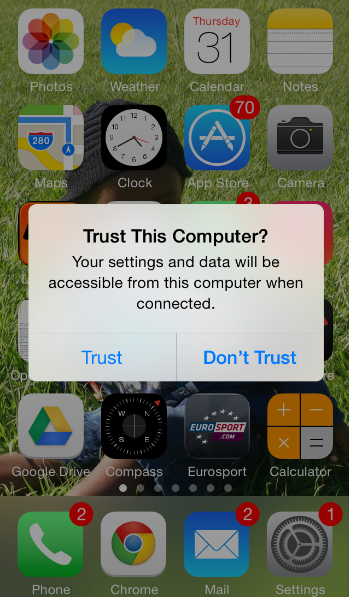
The warning will pop up when you connect your iPhone without a passcode to a computer. It will also pop up when you punch in access passcode in an iPhone that is connected to a computer.
If you trust a computer,
- The data in your iPhone will sync with that computer if iTunes is installed and running.
- Your files, especially photos will be accessed using that computer if your iPhone is not passcode protected
If you don’t trust a computer, none of the above will happen.
You do not want to trust any computer except yours.
The warning will pop up when you connect your iPhone without a passcode to a computer. It will also pop up when you punch in access passcode in an iPhone that is connected to a computer.
6. Do Not Jailbreak Your iPhone
As much as iPhone jailbreak is a pleasurable hactivity, it also creates a back door for crackers and mad men to access your iPhone.
Jailbreaking an iPhone practically opens up the IOS sandbox environment which is a hallmark of iPhone security.
Your enemies are not only the phone pickpockets in the alleys, but also data snippers that prowl the internet.
A jailbroken iPhone allows cracker developers to,
- Have root access to your iPhone
- Track your location
- Install malware
- Install keyloggers
Just in case jailbreaking is your bread and butter, ensure to install apps you are sure of, in order to be safe.
© 2014 Alfred Amuno








