- HubPages»
- Technology»
- Computers & Software»
- Computer How-Tos & Tutorials
Security software including Anti-virus and firewalls and security best practices for small business
Due to their reputation for being far less likely to have security software such as anti-virus software and firewalls installed, as well as running out of date security and operating system patches small businesses are often a favoured target of cyber criminals. Additionally, small businesses often do not have dedicated IT resources available to ensure that good security practices are implemented and adhered to.
Small businesses can protect themselves from these outside threats by installing, configuring and regularly updating security software as outlined below as well as regularly patching the company’s computers. In addition, an acceptable usage policy based around some general security best practices should be created, implemented and signed by all employees.
Firewalls
A firewall for a small business is a solution (typically software) that protects the company from any internet traffic that could potentially be harmful to the business.
- Firewalls scan all internet activity to and from the company and if the activity is determined to be harmful or potentially harmful based on the firewalls predefined security rules then it will be blocked.
- Some applications utilise specific ports to communicate other than the normal internet and secure internet ports (http:// and https:// traffic on ports 80 and 443). These applications will typically be blocked by a firewall setup using a default configuration, requiring the specific ports used by the application to be opened or enabled.
- Email communication using SMTP and POP3 will typically require the requisite ports to be opened; similarly FTP will also require a port to be opened to function correctly.
Anti-virus software
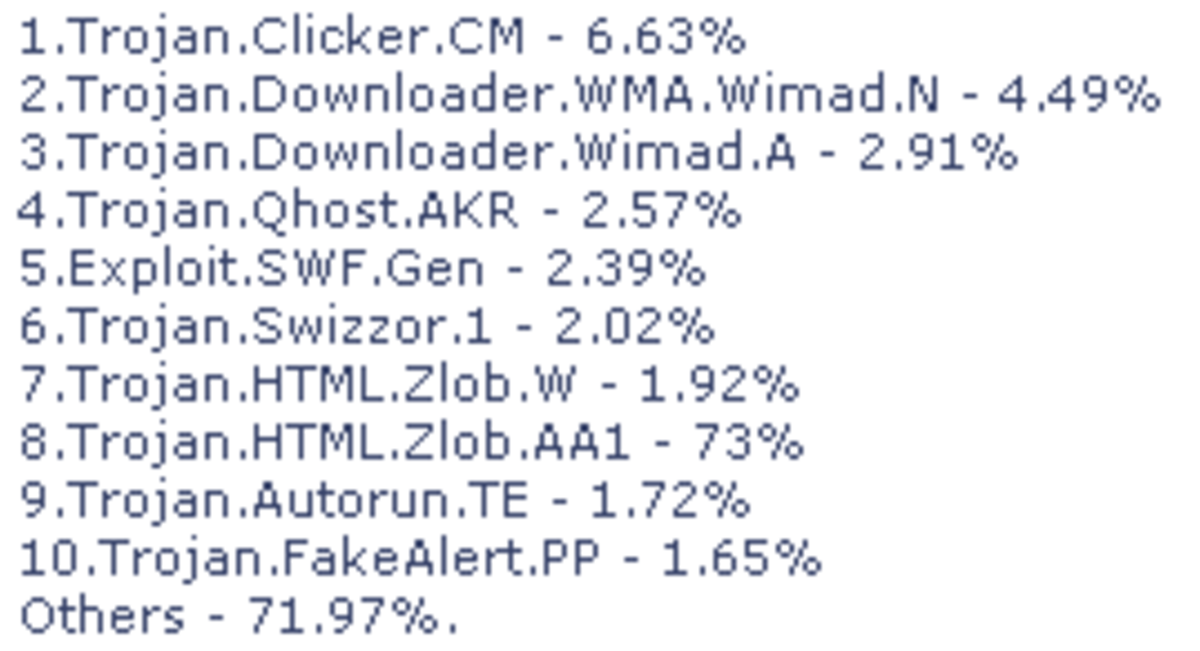
Anti-virus software scans all active files for known viruses using its installed virus definition files, protecting the computer from viruses that have infected active files. In addition, the software can scan all files on the computer to ensure that there are no further infected files.
- Anti-virus software must be installed on all computers and servers in the business and manually configured to scan all files at least once a week.
- Anti-virus scans can be very CPU intensive, so it is best practice to ensure that scans run when the computer is not in use (typically during the night if the computer is left on).
- If there are too many files on a server or a computer for the anti-virus scan to complete before the business day begins, then the software should be configured to scan a section of the data (for example one server volume) each day to ensure that all data is regularly scanned.
Corporate anti-virus software will often come as a suite containing antispyware, firewall, and network intrusion prevention software.
- Antispyware software scans for threats such as malware and other forms of spyware designed to infiltrate or even damager your computers or your network.
- Network intrusion software monitors your network for suspicious activity or unauthorized access attempts and prevents your network from being broached.
It is crucial that Anti-virus software be configured to update automatically, to allow the software to download up to date virus definition files to ensure that the software is able to detect all currently known viruses.
Providers of corporate anti-virus software are also beginning to offer their software suites using Software as a Service (SaaS).
- Software installs using an online deployment (installation links can be distributed via email, eliminating the necessity of localized software installation and configuration by CD).
- Management of the software is centralised to an online console, allowing for reporting, running virus scans and managing security updates to be completed via the internet.
Security Patches
Without an effective patching solution, businesses expose themselves and their data to anyone able to exploit the security weaknesses exposed by out of date or missing security patches.
- Many bug fixes and operating system enhancements are included alongside security patches which will provide a more stable and productive environment.
- Patching should also include any applications installed on computers to ensure that they are also running optimally.
- The simplest and, for many small business, the most effective way of ensuring that all computers are patched is to enable the operating system and any applications configurable to do so to auto-update.
- Computers should be configured to install the patches automatically on a defined schedule preferably when the computers are not being actively used.
- Windows will restart the computer automatically (if required) after the installation of updates is complete. This behaviour can be modified using Group Policy if the computers are members of a domain. All users should ensure that their work is saved when they leave work for the evening.
- Larger firms can use free software solutions such as WSUS (Windows Server Update Services) to automatically deploy patches to their environment.
General security best practice and the creation of an acceptable usage policy
In addition to installing and constantly keeping updated a suite of security software as outlined above, there are a number of additional steps that a small business can take to ensure that the business remains secure and does not inadvertently open itself up to cyber criminals. These security practices include:
- All PCs should require unique usernames with passwords to logon
- Staff should be trained to treat emails with attachments from unknown senders with care. If there is any doubt, delete the email without opening the attachment
- Laptops and mobile devices such as iPhones, CDs, DVDs and USB keys that contain any company data should be encrypted
- Passwords should be kept private
- Passwords should never be written down
- Passwords should be regularly changed (every 90 days is a good practice)
- PCs should be locked when users leave their desks for any extended length of time
- Areas containing servers should be physically secure
- Access codes to restricted areas should be regularly changed
- When an employee leaves the company, the account should be disabled and the password changed immediately
- Employees should be continually trained and empowered to follow good security practices to further reduce any risks both to company infrastructure and company data.
These security practices as well as recommendations on how to handle sensitive information should be combined into an acceptable use policy.
- This policy should outline the security practices above and should also outline the acceptable use of the company’s IT equipment. The policy should include guidelines on acceptable internet usage, application usage and the installation of software.
- It should also outline the punishment for a violation of the policy which should be signed by each employee.
- Someone should be assigned to be the “security expert” unless you have an IT presence. It will be their role to ensure that the policy is adhered to and that the software updates are occurring as scheduled.
Conclusion
With anti-virus software and a firewall solution correctly installed, properly configured and fully patched, as well as regularly scanned computers and an acceptable usage policy in place, small businesses can ensure that they are as secure as their larger counterparts.
Alongside a comprehensive IT security policy, a backup and disaster strategy should be implemented to ensure a company can continue to function in the event of data loss or catastrophe. Setting up such strategies is covered in my hub
Well, I hope you have enjoyed reading this hub as much as I have enjoyed writing it. Please feel free to leave any comments you may have below.




![How to Remove Kaspersky Password Protection? [Easily Recover] How to Remove Kaspersky Password Protection? [Easily Recover]](https://images.saymedia-content.com/.image/t_share/MTc2Mjk3NDcwOTAzNTkyMTI2/how-to-remove-kaspersky-password-protected-easily-recover.png)