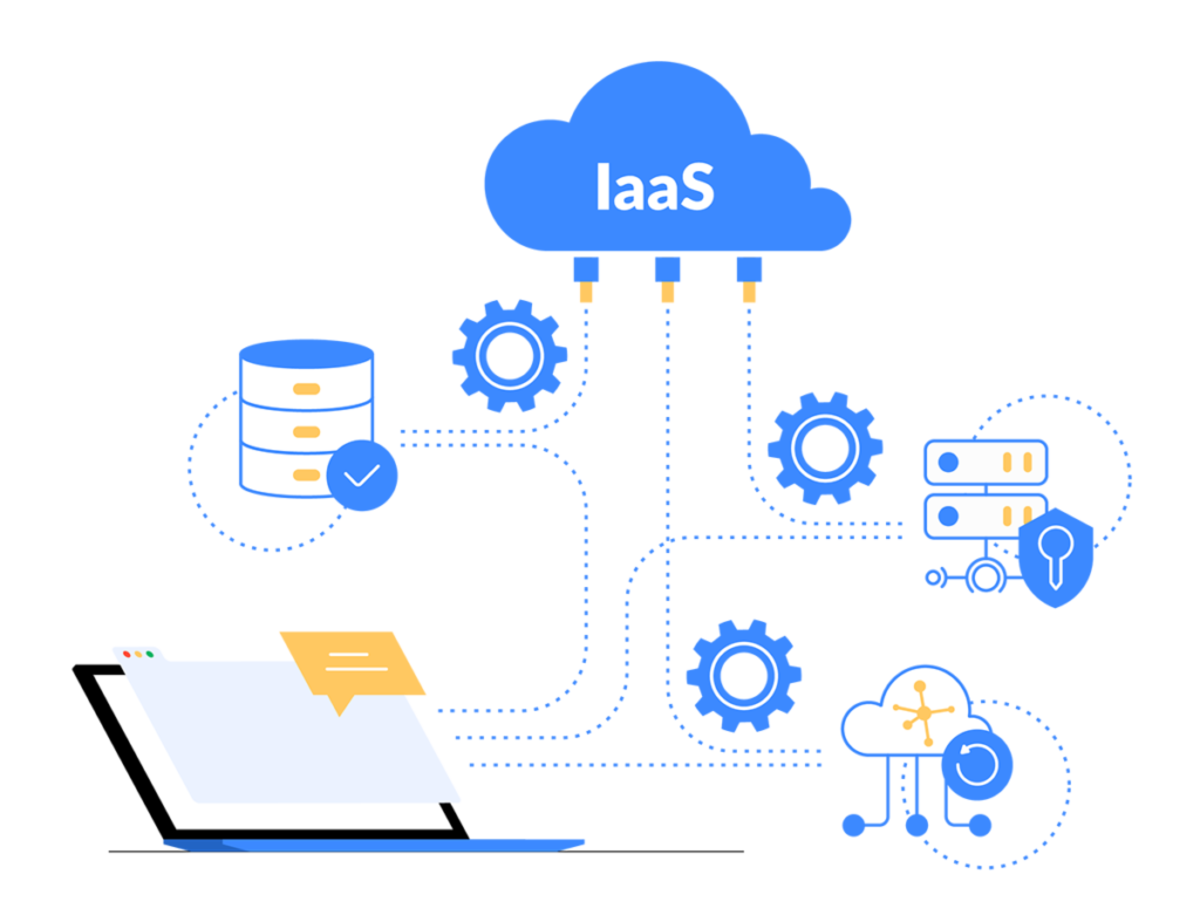
What's a Public Key Infrastructure?

An overview of a PKI
The benefits of a public key infrastructure are plentiful; a PKI can increase privacy, whilst reducing the risk of online communications being tampered with and ensuring transactions are secure everytime you buy something online, send a confidential email or do a bit of internet banking.
Building an argument for using a PKI is easy then, yet there are several ways you can go about creating a public key infrastructure if you are involved in online retail. The first thing you need to do is decide whether you should outsource it or handle it in-house. This overview will give you the information you need to make an informed choice.
Companies that wish to have the most control over their public key infrastructure often favour the in-house approach. Nevertheless, this will require a lot of your time and money, especially if you or your employees do not have any IT security knowledge in-house. You will also need to invest in software licencing too and you will have to fund any maintenance that is required. So there are large costs in the beginning, but also continual expenses whilst supporting the infrastructure. Many companies think that this is worth it, so they can have ultimate control. Nevertheless, the sheer level of investment involved often prohibits many small businesses.
One thing you do not want to do is start building a PKI in-house only to discover half way through that you do not have the capacity to do so. Therefore, you need to assess your operational capacity before making a decision. Your business will need to have 24 x 7 support capability - again not necessarily easy for smaller businesses. It is also advisable to make sure you have security policy expertise in-house, as well as staff that are qualified in running a public certification authority (CA).
If this all sounds like a lot of expense and bother, it is better to outsource to a company with the right expertise
But it's not just about expense, risk and having the right expertise - you need to consider whether your company wil gain a strategic advantage by maintaining control over this service by building it in-house. Especially if you are a growing tech company and want to benefit from the best public key infrastructure setup as possible to secure not only you online communications but also you growing reputation.
But you will need to be sure that you are equipped to handle user registration to the required standard. Also, can integrity and security of root signing keys be guaranteed and are physical security measures sufficient? This pretty much covers the main areas you need to take into account when determining whether you have the operational capacity to handle PKI in-house.
If you decide that you would be better off outsourcing then make sure the liability of the supplier is stated clearly from the outset and that the supplier is adequately and continuously insured. It is also important to make sure you are not forced into a one-size fits all model. Your public key infrastructure model will need to be adapted as your business grows.
There is no right or wrong answer on whether in-house PKI or outsourcing is the best option for your business– it all depends on your company, your resources and your requirements. What is clear is that security on the internet is frequently compromised as hackers become more sophisticated so don't leave you reputation for security of information to chance.

The security of computing in the cloud
More and more businesses in all parts of the world are adopting cloud computing as companies seek to improve their agility and reduce costs. While cloud computing presents many benefits; it has also brought the need for greater levels of security. Specialist training of employees is required to ensure that appropriate security controls are in place and that cloud computing is being implemented responsibly.
Employees need to be aware of all of the theory and the best practises surrounding cloud computing and have real-world experience in implementing security controls in a cloud computing environment. Increasingly sophisticated hacker techniques to gain confidential information either to make money or compromise your company reputation mean you just can't leave internet security to chance.
There is a straightforward training course that IT employees can attend to gain a Certificate of Cloud Security Knowledge (CCSK) which is recognised all over the world and backed by the European Network and Information Security Agency and supported by the Cloud Security Alliance. These two organisations have a leading role to play in cloud security research on a global basis so if your staff need some training then this accredited CCSK course is one worth considering.
CCSK has been designed for a wide assortment of professionals that are involved in the IT industry, as cloud computing impacts a huge number of people nowadays due to its deployment all over the world. From data security, to compliance, to architecture, to governance – this course covers a large number of topics, which is another reason it is suitable for so many IT professionals.
Basic Cloud Security Issues
Cloud computing is still an evolving area but looks set to continue growing so there is no getting away from the facts that every company - no matter how small - needs to have some basic understanding of all the security issues surrounding it:
- virtualisation
- traditional security
- portability
- interoperability
- legal and electronic discovery
- information lifecycle management
- incident response
- identity and access management
- governance and enterprise risk
- encryption and key management
- data centre operations
- compliance
- audit
- cloud architecture
- application security
Phew - who knew underneath that fluffy name that there was so much to know...